As parents, grandparents and technically stumped users ask friends for help in getting online, remote desktop access tools, as Sam Grobart from the NY Times points out, are being used as a means of eliminating hours-long, potentially very frustrating conversations.
 As we have observed in past Application Usage and Risk Reports, these applications are powerful business tools that enable IT and support personnel to rectify computer and networking issues remotely. To highlight the common place nature of these tools, remote access is now a feature in the Chrome browser from Google. The ease with which these tools are accessed have made them commonplace for tech savvy employees, as the article aptly points out, to use as a means of helping friends and family address computer problems. The dark side of these altruistic endeavors is that cybercriminals know these tools are used commonly by all manner of user; they know they are often mis-configured; they also know the ports these applications use on the firewall are commonly left open. And because these tools are used commonly by IT, when they are found on the network, they are often "allowed" with little attention paid to who the user is. This knowledge allows the cybercriminal to look for, and use remote access tools as attack vectors.
As we have observed in past Application Usage and Risk Reports, these applications are powerful business tools that enable IT and support personnel to rectify computer and networking issues remotely. To highlight the common place nature of these tools, remote access is now a feature in the Chrome browser from Google. The ease with which these tools are accessed have made them commonplace for tech savvy employees, as the article aptly points out, to use as a means of helping friends and family address computer problems. The dark side of these altruistic endeavors is that cybercriminals know these tools are used commonly by all manner of user; they know they are often mis-configured; they also know the ports these applications use on the firewall are commonly left open. And because these tools are used commonly by IT, when they are found on the network, they are often "allowed" with little attention paid to who the user is. This knowledge allows the cybercriminal to look for, and use remote access tools as attack vectors.
The most recent 2011 Verizon Databreach report analyzed 900 incidents worldwide and found that 320 of the initial penetrations could be tracked back to remote access errors. The report implies that the common use [or misuse] of these tools is such that attackers have built it into their development efforts. From the report:
these tools is such that attackers have built it into their development efforts. From the report:
“As soon as an intruder discovers a particular [remote access] vendor’s authentication method and schema (be it for TCP port 3389 for RDP; or TCP port 5631 and UDP port 5632 for pcAnywhere), he will be able to exploit it across a multitude of that vendor’s partners and customers. Oftentimes, in lieu of conducting a full port scan for these remote service applications, attackers will customize their scripts to exclusively look for these ports and search a broad swath of the Internet.”
In a real world example, $3 million USD was stolen from unsuspecting Subway customers by cyber criminals who gained access to the credit card data by performing a port scan for remote access tools and then cracking the associated passwords.
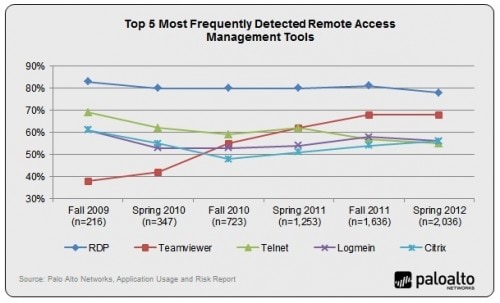
Palo Alto Networks Application Usage and Risk report statistics finds an average of eight different remote-access applications are in use across 96% of the participating organizations. When viewed across the past two years of data collected and analyzed in the Application Usage and Risk Reports, the top five remote access tools have remained consistent in terms of the frequency of usage. The interesting trend seen is the growth in popularity of Teamviewer, an open source tool that supports nearly every client known to exist. So using Teamviewer, a support representative could conceivably help a customer using their Android-based phone. A very powerful business proposition. And therein lies the downfall, at least from a security perspective.
Thanks for reading.