I recently presented about securing government at the 2017 Cyber Defense & Network Security (CDANS) conference in the United Kingdom. As I was preparing remarks for senior U.S. and EMEA military leadership, and as I’ve done in years past for this annual conference, I began pondering 2016 in the context of securing our networks. What could I advocate to these leaders that was different than I have advocated in years past? After all, we’re seeing some of the same issues – made even more urgent by our evolving networks into public clouds, and with our data more widely dispersed than ever before.
Entering 2017 with more electric grid attacks, a year of pervasive and successful ransomware, attack campaigns of years past that succeeded once again, and now our first ever botnet of things, what could I say to encourage these leaders and help us focus not on the past but on lessons for a very positive start to 2017? Well, as it turns out, quite a bit. What follows are my observations and thoughts for using 2017 to course-correct with both the recognizable patterns and greater attention to best practices to ensure our defense in depth strategies are agile.
First, let me pose a question to you: Coming out of 2016, what do you feel is the number one way in which attackers are ahead of our enterprise security efforts? I would posit that it’s automation – with collaboration a close second. As I looked at some of the 2016 cyber malicious activities and events, the automation theme was pervasive and growing:
- Ransomware
- Return and use of macros
- Mirai botnet and the “Botnet of Things” attack
- “OilRig” campaign
- “Shamoon 2” attacks
- Yahoo: biggest breach of one source to date
- Russian gang amass of 1.2B credentials
I won’t use this blog post to repeat the many details we’ve already published from the year. But I do want to reiterate the good news that I repeated to the audience at CDANS, and even more with the latest release of our PAN-OS 8.0: you, too, have automation available to protect your data and your network assets. (More on that later.)
Late in 2016, I commissioned a study of how the U.S. federal government is using automation to improve all aspects of its attack mitigation processes – from external threat intelligence consumption to what security sensors and capabilities are doing to help. The results, published in MeriTalk’s “Pedal to the Metal” report, were in some ways disappointing, yet were informative in where I feel Palo Alto Networks can help.
Here are some highlights:
- Fewer than half of U.S. federal agencies guard against emerging and critical attack vectors, increasingly used as attack entry points.
- Most focus on traditional entry points (mail server, internet gateway, web)
- 55 percent say their agency is currently not automatically correlating threat campaign information from different locations
- 30 percent do so manually, and
- 25 percent don’t do it at all
- When faced with a new (unknown) threat…
- A low 15 percent can create new protections within a few minutes (over a third still take days to take any action)
- Only 17 percent can distribute new protections within a few minutes
- Security operations teams ingest an average of 25 external threat feeds daily
- 47 percent: Still purchase feeds only consumed via email
- 72 percent: Few hours to a few days to assess presence of unique threat and determine whether actionable
- 81 percent: Few hours to a few days to create actionable changes in security posture to protect against a new threat received from external sources
- Security operations teams are allocating skilled and limited resources on tasks that can be automated
Most don’t need more data (or people to review it) but the ability to make faster decisions from the data they have. But do they understand that?
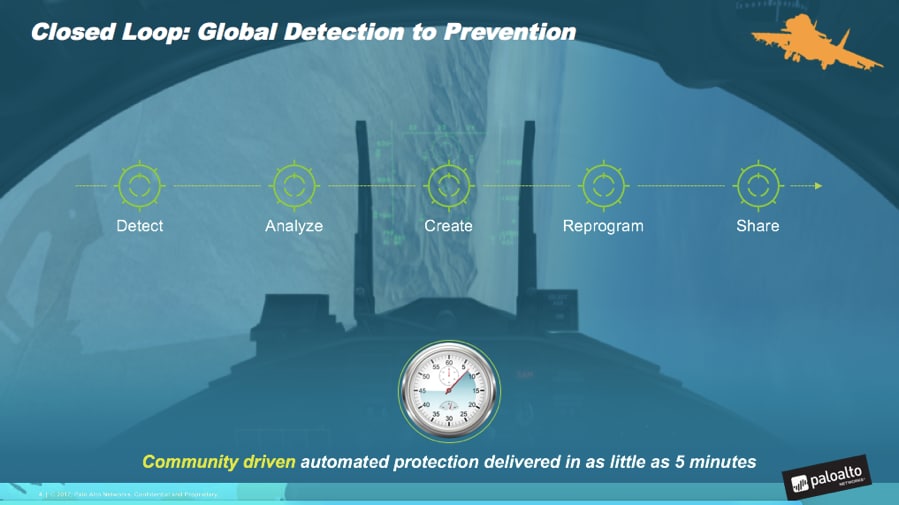
As Einstein said, “We cannot solve our problems with the same thinking we used when we created them.” It’s time to embrace innovations in automation, just as we’re seeing governments now slowly but surely embrace the cloud. Reduce time to act on anything new hitting your networks. Your goal with today’s technology should be under five minutes for new protection to be created and deployed. This could be malware signature creation, detecting and blocking new IP addresses and domains associated with command-and-control infrastructure. When it comes to exploits, they can be stopped immediately – don’t settle for anything less.
For government, these changes may seem like radical departures but keep in mind that you can start with incremental change to a long-term goal. Don’t be overwhelmed. Perhaps start with one aspect of your network with:
- Security focused on one location that’s more vulnerable
- Security focused on one aspect of the threat
- Security focused on one attack vector (internet gateway, north/south into your data center, east/west traffic within your data center, Office 365 and Azure environments, your use of SaaS applications, etc.)
- Preventing phishing: You can detect if a link in an email is malicious, and then block connections to those sites.
- Preventing stolen credentials: Now in PAN-OS 8.0, you can block authenticated lateral movement, using multi-factor authentication within the network, from adversaries trying to compromise a network.
- Reduction of efforts and time to correlate and make actionable use of threat intelligence (from internal and external sources). With our MineMeld tool that’s offered as freeware or supported as part of AutoFocus, you can even do correlation, de-duplication, and can create automatic blocklists from your threat intelligence feeds.
- The people part of the equation. I still hear stories about teams refusing to work together. Resolve to improve teaming between those with security responsibility. Perhaps choose two teams to focus improved communication: start with network and IT security teams, later adding collaboration with DevOps, endpoint and other teams. And don’t forget to include the ICS & SCADA teams, where applicable.
For your OT environments, if your country doesn’t have regulatory guidelines, use NERC CIPv5 as your baseline, and consider the Purdue model.
I used a military analogy to which many can relate – regardless if you were ever part of an airborne mission or are a gamer. Looking out of that cockpit, traversing enemy territory, the timeliness (and accuracy) of the information that you receive is critical. Just as in the physical domain, every second counts in our cyber domain. We don’t have to repeat the mistakes of 2016. It is possible to appropriately secure our data and networks – however we extend them from SaaS to public cloud to remote locations to support our troops, our government operations, and our citizen services. Let’s use 2017 to reclaim control and use automation to our advantage – to reduce the risk to our governments and critical infrastructure and to ensure the resiliency of our digital way of life.
To learn more about our other activities at CDANS 2017 this year, please visit:
- CDANS 2017: Keeping Cybersecurity Skills Sharp With Cyber Range
- Securing Our Networks with Women in Cyber
And if you haven’t had a chance, please read about all of the exciting enhancements we made in PAN-OS 8.0.
Federal Ignite '17 Security Conference: Washington, DC
If you are in the U.S. government, come to Federal Ignite 2017 to learn more about what we’re doing for you and your peers to make fast threat prevention through automation a reality.