This post is also available in: 日本語 (Japanese)
Clients often ask me, “How do I know if I have ‘enough’ security in the cloud?” This is a great question because it shows a willingness to learn. The truth is that there is no right answer.
However, a simple place to begin is the basics. You should be sure you’re covering the basics well and tracking them closely. This is why I am a huge fan of standards. While they are not the be-all and end-all for security, they give you an excellent place to start. One common set of standards are the Center for Internet Security’s (CIS) top 20 controls, a prioritized list of 20 best practices that help organizations improve cybersecurity.
CIS Controls: Benchmarks for Cloud
Threat research shows that 65% of cloud security incidents are the result of customer misconfigurations. Why is this number so high? Because organizations are not getting the security basics right. This is where standards like
the CIS controls can provide an excellent benchmark for those foundations.
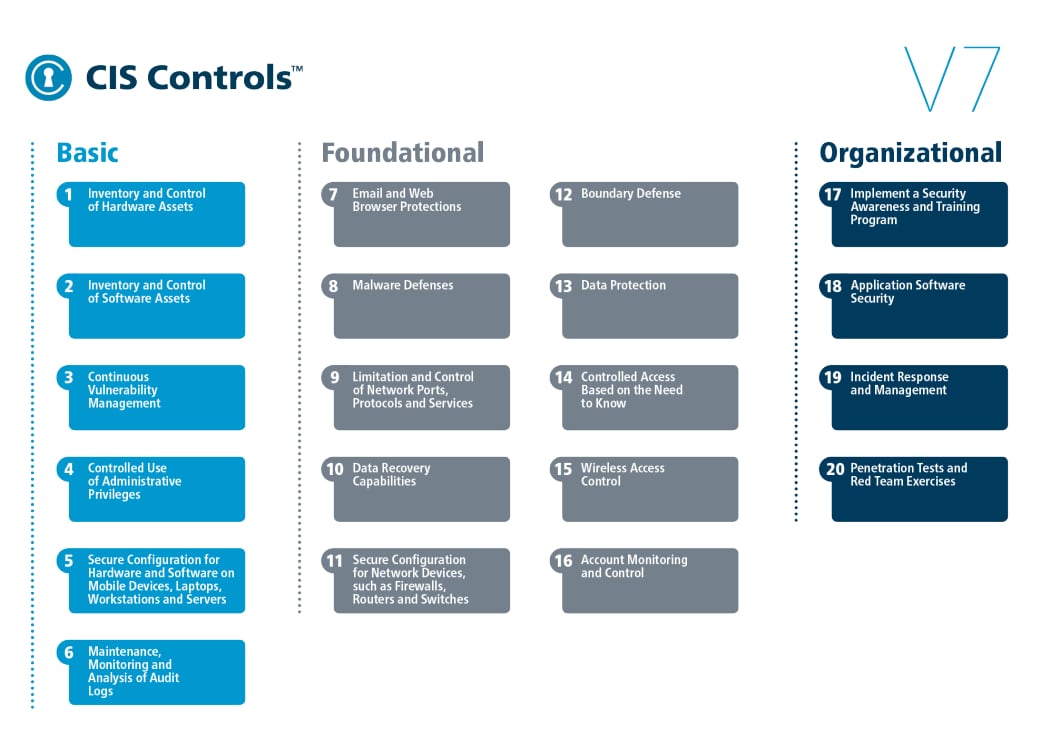
Source: Center for Internet Security
A great exercise for your cloud program is to map these 20 controls against what you have in place today. With the exception of control 15, Wireless Access Control, these are all relevant to varying degrees across infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS) platforms.
Measure a Complete View of Cloud Security Using CIS 20
The trick for your security program is to measure as many of the 20 controls as possible using cloud native tooling. By cloud native, I mean platforms that integrate with multiple cloud service providers (CSPs), hybrid-cloud environments and common software development tools like CircleCI, GitHub and Jenkins.
Most security teams think of only the attack surface on the CSP, however the entire CI/CD pipeline is just as critical. This is why it’s important to use security platforms that are completely integrated across all the major public cloud providers and development pipelines. Otherwise, you are only seeing a part of the picture. See figure 2 below.
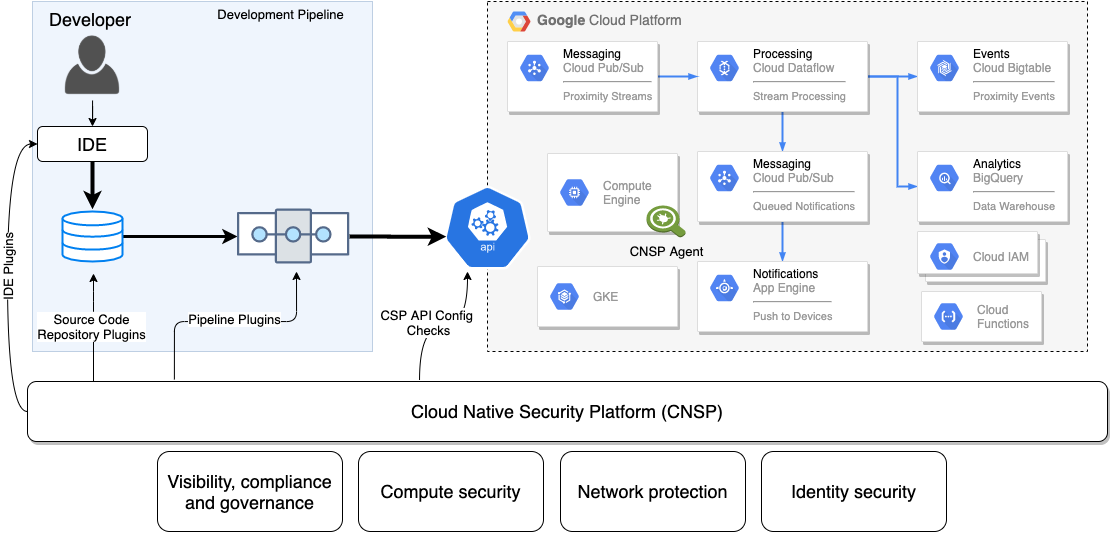
We know that most security programs lack this holistic view into the development pipeline thanks to the Spring 2020 Cloud Threat Report from Unit 42. Researchers analyzed hundreds of thousands of infrastructure as code (IaC) templates and came up with some interesting findings. The most pertinent: nearly 200,000 insecure templates in use, 43% of cloud databases not being encrypted and 60% of cloud storage services with logging disabled. These numbers illustrate why it’s important to examine your entire cloud stack when assessing your cloud security.

Source: unit42.paloaltonetworks.com/cloud
How to Apply CIS Controls to Cloud Development
So how do you apply the CIS 20 to your entire cloud stack? The first thing I recommend is reading through the CIS Controls Cloud Companion Guide. The guide will help you create metrics for each control, decide what end result you’re looking for and begin to work backward to determine where and how to collect data.
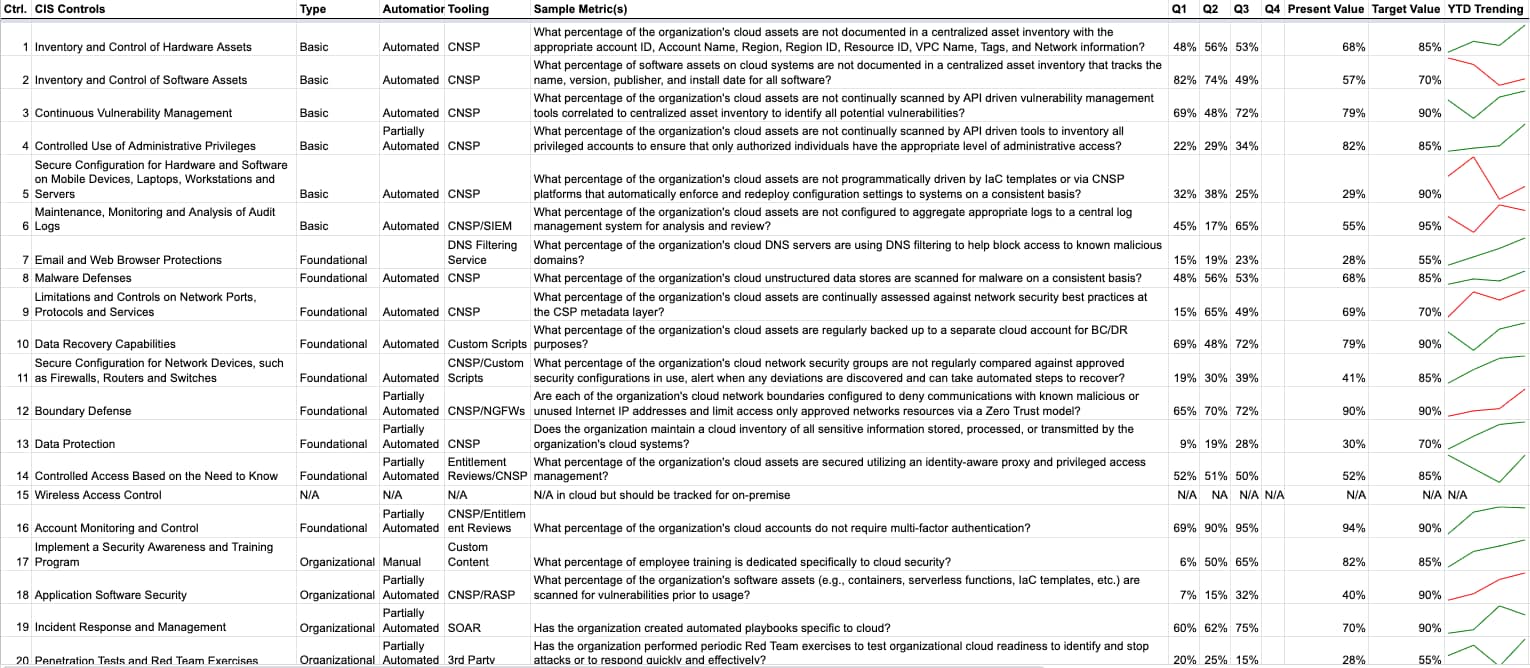
Again, it's important to keep the entire cloud stack in mind. Don’t just focus on the CSP but be sure to include your entire development pipeline. These 20 critical controls should evenly apply across the stack.
Don’t expect to have this process perfect overnight. A great way to test this out would be to make these metrics a key requirement for any proofs of concept your team is likely running on cloud native security platforms (CNSPs). The key question is will the CNSP enable you to track these metrics over time and take corrective action when necessary?
How Much Is Enough Cloud Security?
In my view, you can only begin to answer the question of whether you have “enough” cloud security by first covering the basics. Step number two – and the key to long term success in the cloud – then comes by measuring the controls consistently over time across the entire stack. Combined, these give you a better sense of your overall posture, and can inform whether your current controls are enough.
You can see real-world data on how thousands of other companies are securing their cloud native stacks in the State of Cloud Native Security 2020 survey.