While sitting in a security operations center (SOC) in the middle of a high-severity incident, you realize Secure Shell Protocol (SSH) (port 22) is open to the world. Sifting through logs and pulling up an organizational chart are the last things you have time to do, but in order to track down the right team to help address the issue, that’s your only means. You embark on a round of Slack and Jira roulette only to find out that the team who provisioned the exposed virtual machine has already moved on, and the most recent changes were from another team who you’ve yet to track down—and the alarms are still going off.
It’s situations like these (and lower pressure situations, too) that highlight how important and challenging it is to identify the right teams quickly when a security misconfiguration is identified.
To make that process easier to navigate, many organizations leverage cloud tagging as a scalable way to attribute cloud resources to organizational owners. Tags can simplify operational tasks, cost allocation, access control, automation and risk management.
However, cloud resource tagging is manual, tedious and only pinpoints cloud resource owners in broad strokes. Especially for teams leveraging GitOps principles and infrastructure as code (IaC), changes must be made and tracked by using IaC tags. Tying a misconfiguration from a cloud resource back to the line of code that caused that misconfiguration is a big challenge. In an incident such as the one previously outlined, if the cloud resource doesn’t have proper tags, finding the resource owner and digging through pull requests to locate the team who modified the code that opened port 22 is a challenge.
Introducing Yor for Automatic IaC Tagging
Today, we are excited to announce our latest open source offering, Yor. This is our first new offering since Bridgecrew’s acquisition by Palo Alto Networks. It is an exciting milestone as we, together, continue investing in open-source projects and communities.
Yor is designed to be built into developer workflows. Yor acts as a stage in continuous integrations and continuous delivery (CI/CD) pipelines, such as GitHub Actions, a pre-commit hook or locally using a command-line interface (CLI). It automatically creates IAC tags for Terraform, CloudFormation and Serverless framework templates with attribution and tracing details.
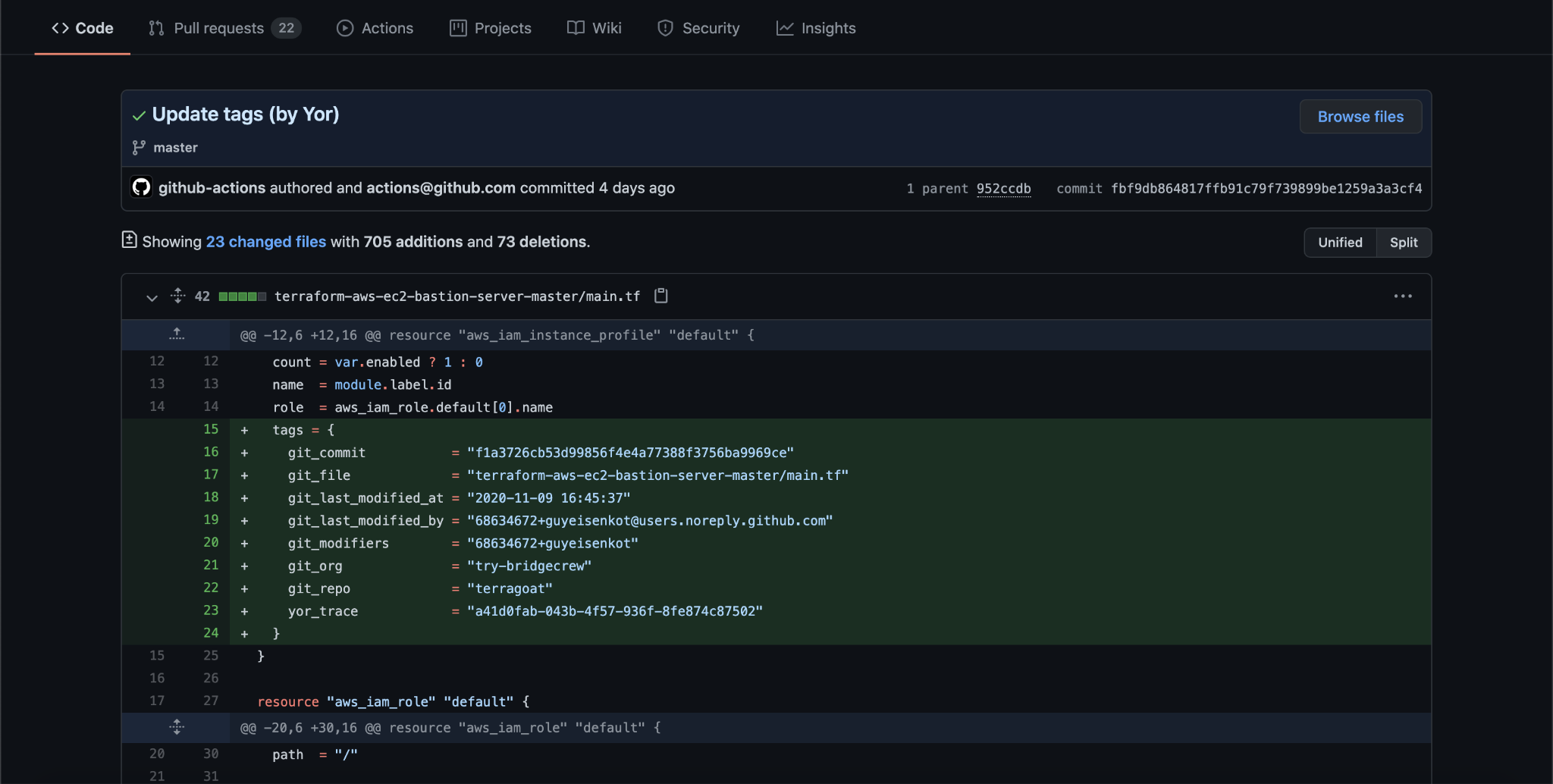
When a developer commits code to a repository, Yor automatically tags the diff for the changes with the tags. These tags carry forward from the IaC template into cloud resources without any lift from developers.
The result is less tedious work for developers and more consistent and accurate tracking for security and operations teams.
Fine-Grained Attribution and Tracing
With more detailed IaC tags, it is more straightforward and faster to trace a misconfiguration back to the line of code and to the developer who introduced the code.
Security and operations teams can leverage this data to tie a resource back to an owner, track change management or trace resources from code to cloud. This helps pinpoint the root cause of a runtime misconfiguration and makes it more foolproof to detect drift between code configuration and running resources.
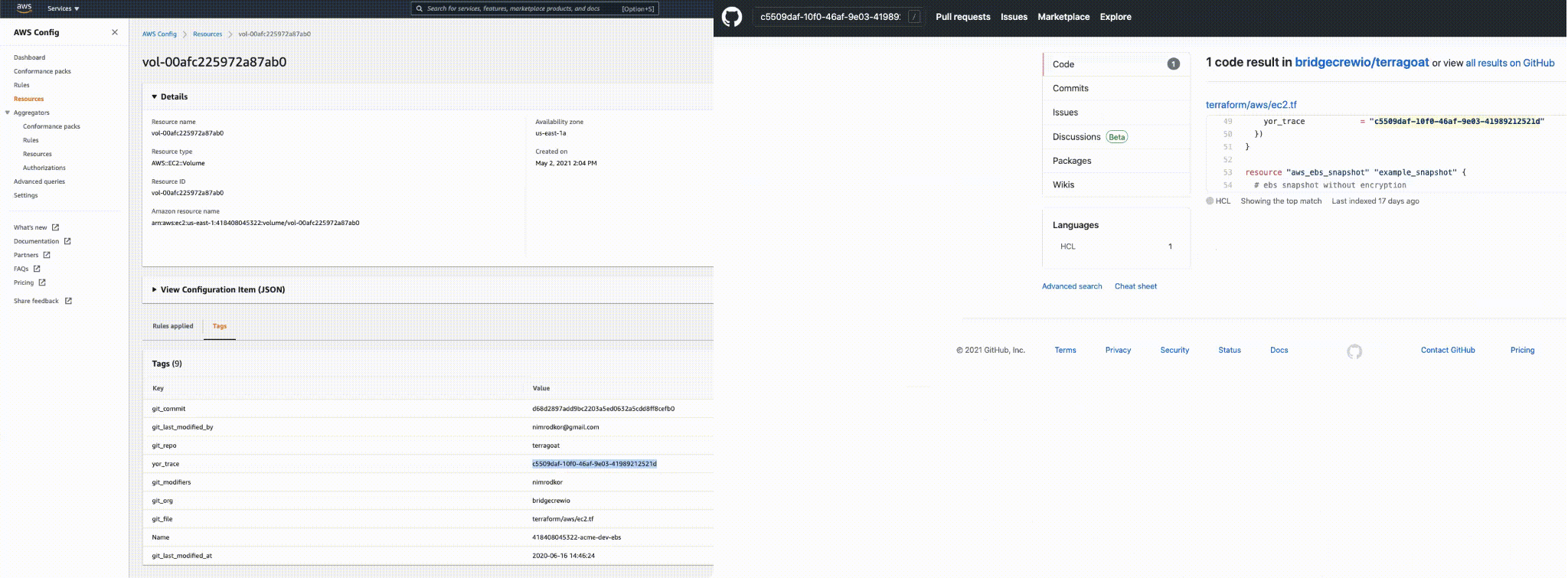
Yor is the latest way we are helping organizations realize more secure cloud infrastructure from build-time to runtime. We’re excited by the prospect of new tool integrations, use cases and custom IaC tags that the open-source community will develop. Also, expect to see more features in the Bridgecrew by Prisma Cloud platform that utilize consistent tagging to speed up remediations and prevent drift.
Yor is a free and open-source tool, so try it today or learn more about how it works on the Bridgecrew blog!