Prisma Cloud Delivers Five New Innovations to Help Security Teams Reduce Alert Noise, Detect Advanced Threats and Simplify Cloud Data Security
Prisma Cloud monitors more than 2.5B cloud resources for more than 2,000 enterprises worldwide. We combine this aggregate data with machine learning (ML) and broad threat intelligence to deliver threat detection, IAM security and data security that enable a strong cloud security posture across even the most complex architectures. These capabilities help remove security and compliance blindspots, providing users deeper context for incidents, eliminating vague alerts and false positives that bog down remediation and investigation efforts.
As part of our dedication to reducing toil for security teams, we are excited to add new CSPM functionality to this stack to help further reduce risks and detect advanced attacks across cloud infrastructures:
- True Internet Exposure
- Visibility-as-Code
- Network Data Exfiltration Detection
- Anomalous Compute Provisioning Detection
- Customizable Object-Level Scanning for AWS S3
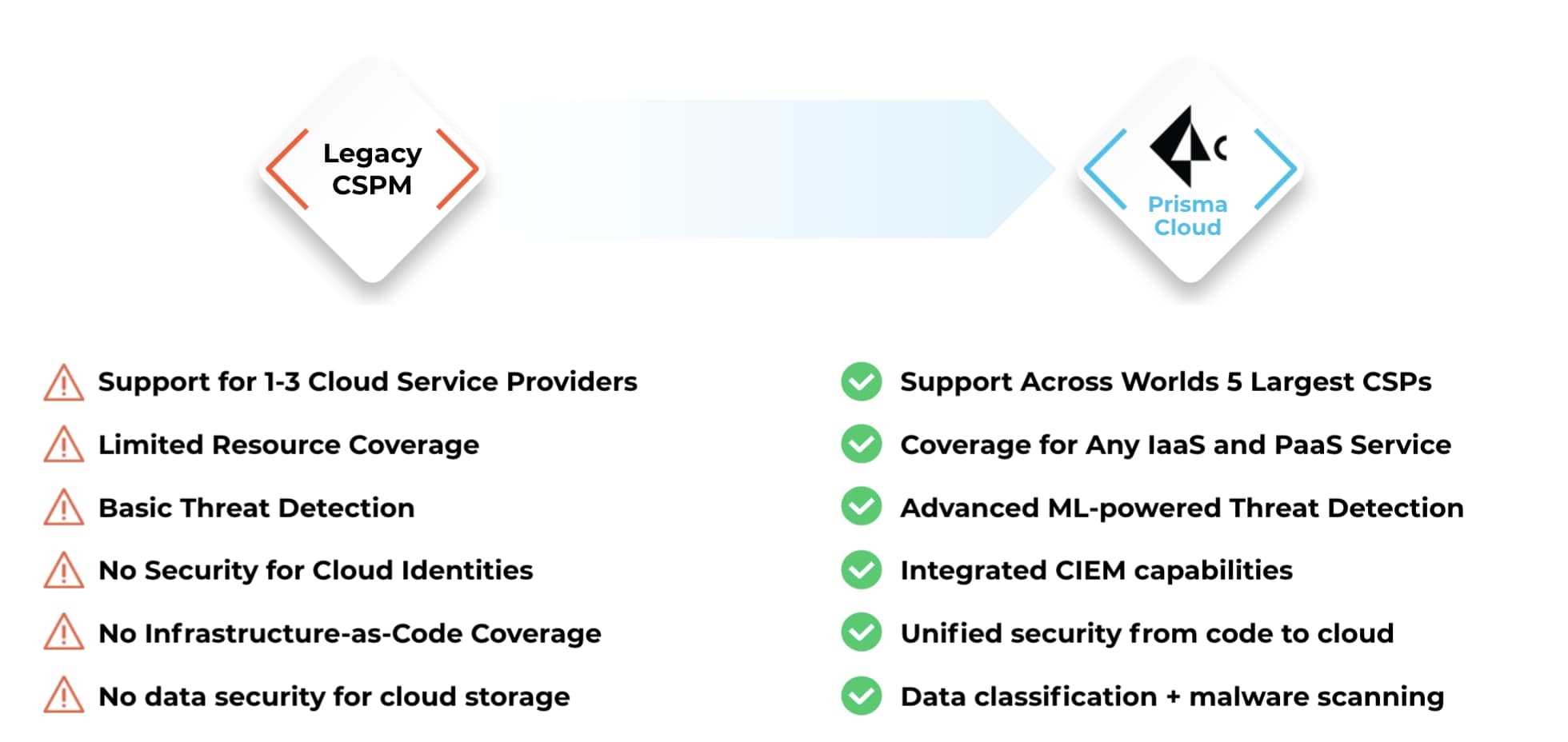
This latest release allows us to continue to deliver best-of-breed Cloud Security Posture Management (CSPM) capabilities across leading cloud service providers (CSPs), all from a single platform, UI and SKU.
Here we provide an overview of the latest enhancements.
Visibility, Compliance, Governance
True Internet Exposure
Legacy CSPM solutions function by generating alerts for any permissive or exposed security group, even if the security group is not attached to a compute instance, or if the compute instance isn’t truly exposed to the internet in the first place. This process floods security teams with alerts that often provide little value. Just because a security group exists, it does not mean it’s attached to a cloud instance.
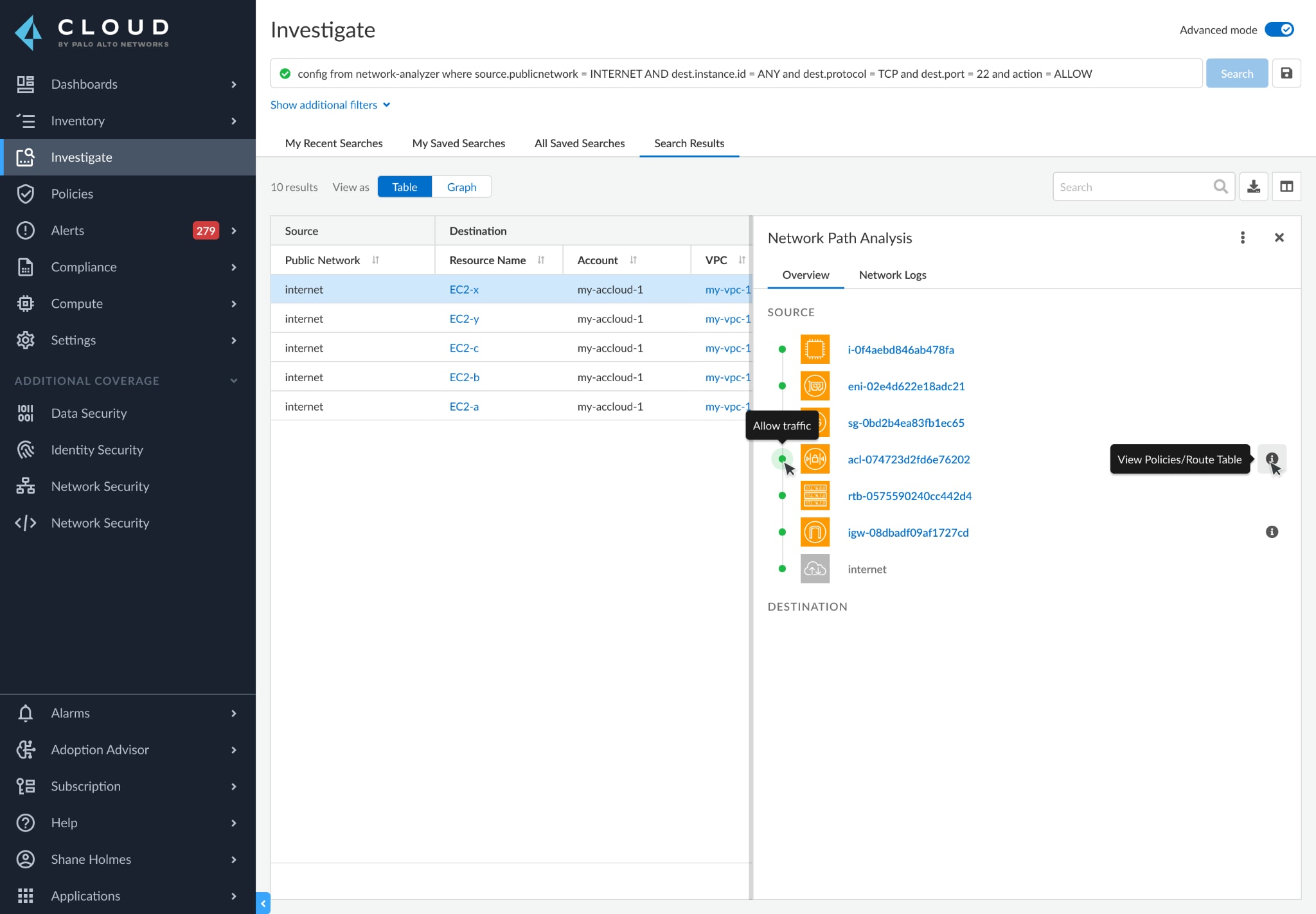
Prisma Cloud takes a multi-dimensional approach to identifying overly-exposed resources by providing:
- End-to-end network path visibility from any source (e.g, AWS EC2 virtual machine, DB instance, Lambda application), to any destination (e.g., internet, another VPC, on-prem networks).
- Visibility into the associations between security group and compute instance, regardless of the compute instance location, whether it is in a public subnet or if the VPC has an attached internet gateway.
By correlating multiple data points, including routing table configurations, Prisma Cloud is able to determine true network reachability, and then surface high fidelity alerts. This frees security teams from sifting through alert "noise" such as false exposure, so they can focus on more impactful security issues.
Visibility-As-Code
Our customers leverage many Infrastructure-as-a-Service (IaaS) and Platform-as-a-Service (PaaS) platforms in their cloud environments, and every year CSPs release or update hundreds of new services. As such, security teams often struggle to protect the sheer volume of new resources dev teams are deploying, resulting in blind spots. In some cases, dev teams may even be prevented from using new cloud services until their security teams can secure them, creating unnecessary conflict.
By reading a simple text file, Prisma Cloud can now automatically build the right API ingestion hook to deliver protections for any CSP service – providing visibility-as-code. This new CSPM functionality means security teams can offer support for new IaaS or PaaS services in just days, providing Dev teams the freedom to use any cloud service, while maintaining needed security measures.
Threat Detection
We are adding two new threat detection capabilities to thwart cybercriminals' two most important objectives – data exfiltration and resource misuse. This expands our already-comprehensive set of ML and intelligence-based threat detection capabilities that also align with the MITRE ATT&CK Framework.
Network Data Exfiltration Detection
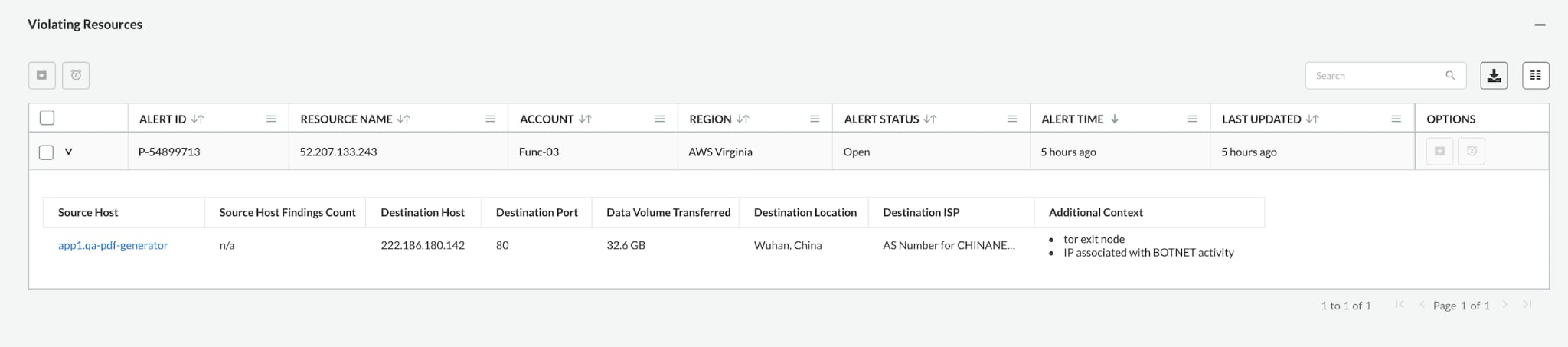
Prisma Cloud analyzes the flow logs of every customer environment, then leverages ML to comprehend typical traffic patterns and detect abnormal egress traffic to TOR exit nodes. While basic security solutions only use one of these techniques, Prisma Cloud combines both to detect malicious data exfiltration attacks with high efficacy and low false positive rates.
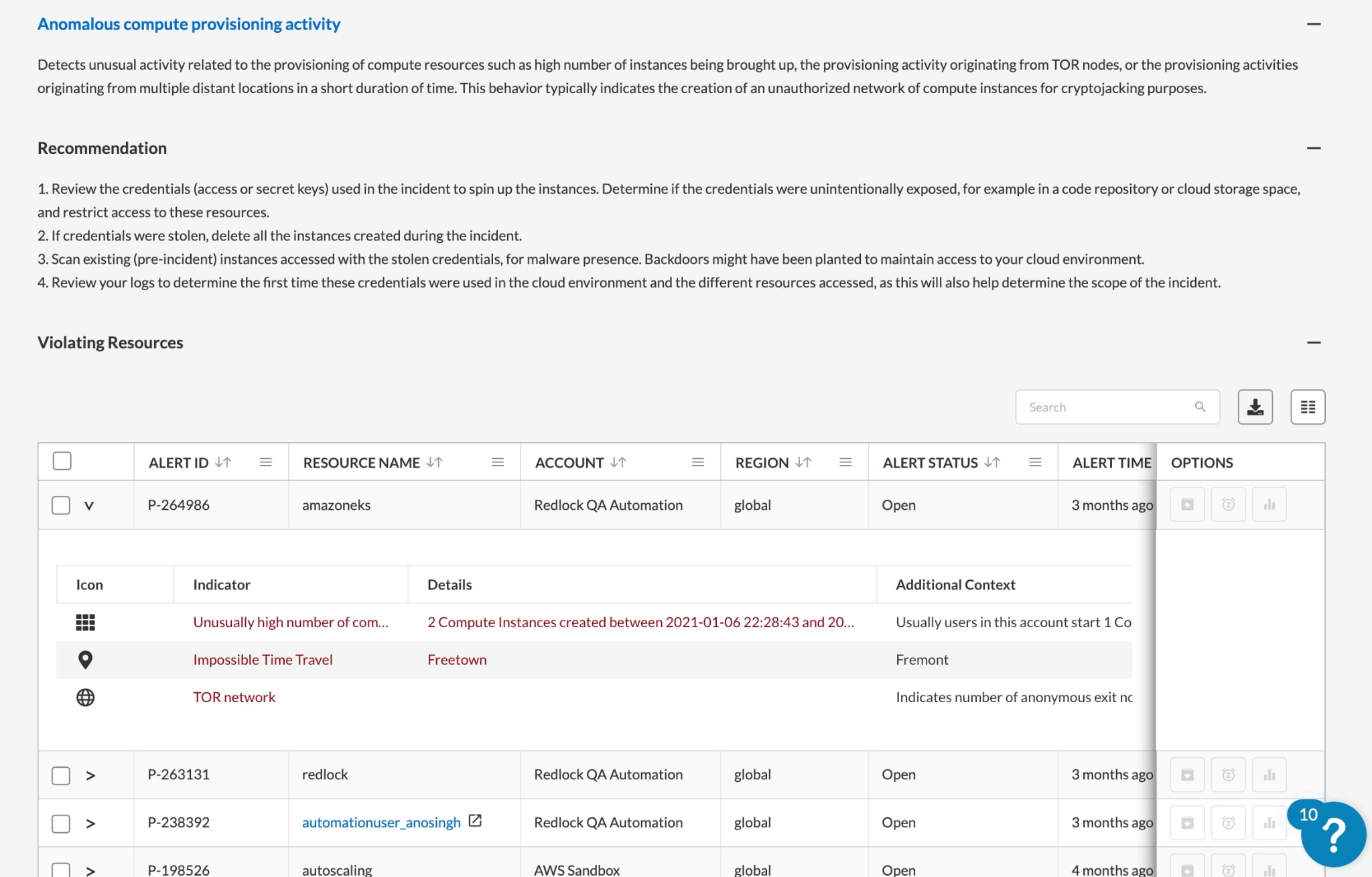
Anomalous Compute Provisioning Detection
This new CSPM functionality detects provisioning of abnormal numbers of VMs, which is often attributable to cryptojacking or other resource misuse. Additionally, Prisma Cloud analyzes permission use alongside TOR exit node data to further minimize false positives. For example, if a user account jumped from one location to another while launching a large number of VMs and/or hiding behind a TOR exit node, that suspicious activity will be alerted.
Data Security
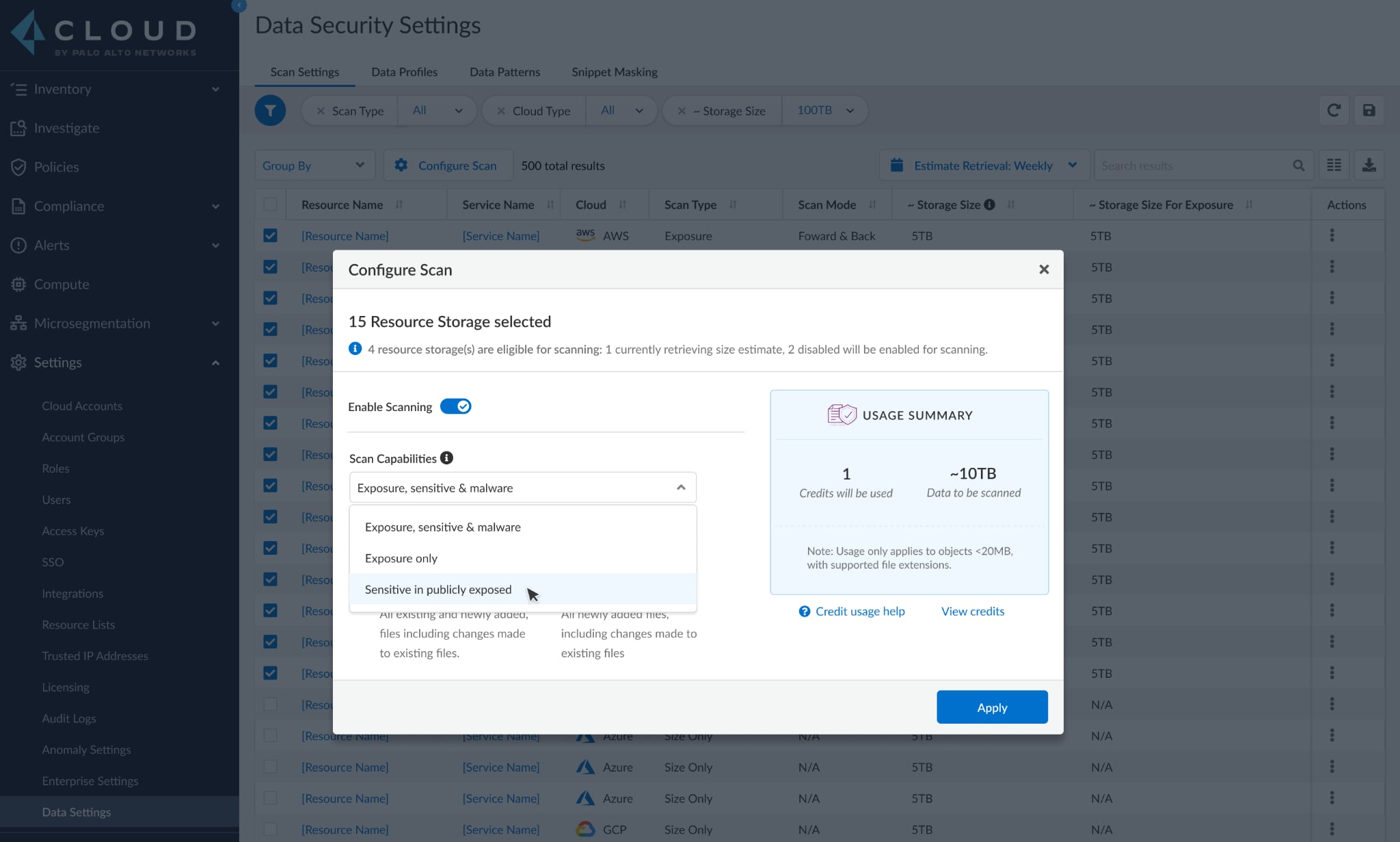
Customizable, Object-Level Scanning for AWS S3
In October of 2020 Prisma Cloud became the first CSPM solution with integrated data security. This enables customers to go beyond mere configuration checks of their cloud storage services to gain deep visibility into, and direct control over, the stored data.
Now, Prisma Cloud Data Security provides further control and flexibility by letting users self-select which AWS S3 buckets, or even specific objects, are scanned for malware, public exposure or sensitive data. For example, customers can choose to scan only publicly-exposed objects for sensitive data, such as personally identifiable information (PII), as opposed to all objects in a bucket. Or, they could scan all objects in a bucket to learn which have public exposure.
Not only does this new CSPM functionality save significant time and resources, but can also reduce the sheer volume of alerts and potential false positives security teams must sift through.
Begin Using the New CSPM Functionality
Current users can begin using most of this new CSPM functionality right away. Anomalous compute provisioning detection is available now and can be found in the Policies tab. Visibility-As-Code is immediately available for Oracle Cloud Infrastructure (OCI) users as well. Then, network data exfiltration detection and customizable object-level scanning for AWS S3, as well as True Network Exposure for AWS, will be available in the next two months. We'll continue rolling out these features across additional clouds over the coming months.
For a deeper look at the strategies that drive strong CSPM, including a technical overview of the toolsets that enable it, read through our white paper, Guide to CSPM Tools.