The growth of globally-interconnected systems and the increase in cyberthreats are causing security challenges for federal agencies. With the added responsibility of maintaining national security and adhering to mandates, federal agencies are experiencing increased pressure to accelerate the adoption of a Zero Trust architecture.
To support the federal government’s Zero Trust cybersecurity initiative, Palo Alto Networks announced today that its IoT Security solution has achieved Federal Risk and Authorization Management Program (FedRAMP) Moderate Authorization. With this milestone, Palo Alto Networks IoT Security offering is helping agencies protect their unmanaged IoT devices with machine learning (ML)-powered visibility, threat prevention and Zero Trust policy creation with enforcement in a single platform. This adds to Palo Alto Networks existing product offerings that support the U.S. government's cybersecurity mission.
Earlier this year, the U.S. Department of Veterans Affairs (VA) selected Palo Alto Networks to modernize their cybersecurity. Among other initiatives, the VA is expanding its use of next-generation security technology to gain automated visibility and security for all the Internet of Medical Things devices on its network.
Cybersecurity Solutions to Support Federal Mandates
Recent guidelines, such as the President’s Executive Order on Improving the Nation’s Cybersecurity, issued in May 2021, and the more recent federal Zero Trust strategy from the U.S. Office of Management and Budget (OMB), spotlight the need to protect managed devices and unmanaged Internet of Things (IoT) devices, owned or controlled by federal agencies.
While these advisories are intended to further the security of IoT devices used by federal agencies, a focus on device-level security alone is not enough. Manufacturing supply chains are complex and not transparent, meaning at-risk technology may be embedded in devices that do not obviously contain vulnerable or banned components. In addition, the service life of many devices, such as medical infusion pumps, can be far longer than the viability of the technology they contain.
These guidelines are in addition to the following mandates to protect IoT devices:
- The Secure Networks Act (July 2020) – The Public Safety and Homeland Security Bureau published a list of communications IoT equipment deemed an unacceptable risk to national security.
- Internet of Things Cybersecurity Improvement Act (Dec 2020) – Requires the National Institute of Standards and Technology (NIST) and the OMB to take specified steps (SP 800-213) to increase cybersecurity for IoT devices.
- Health Information Technology for Economic and Clinical Health Act (January 2021) – Incentivizes healthcare providers to follow federal recommendations and best cybersecurity practices to secure patient information.
Zero Trust Security for IoT Devices
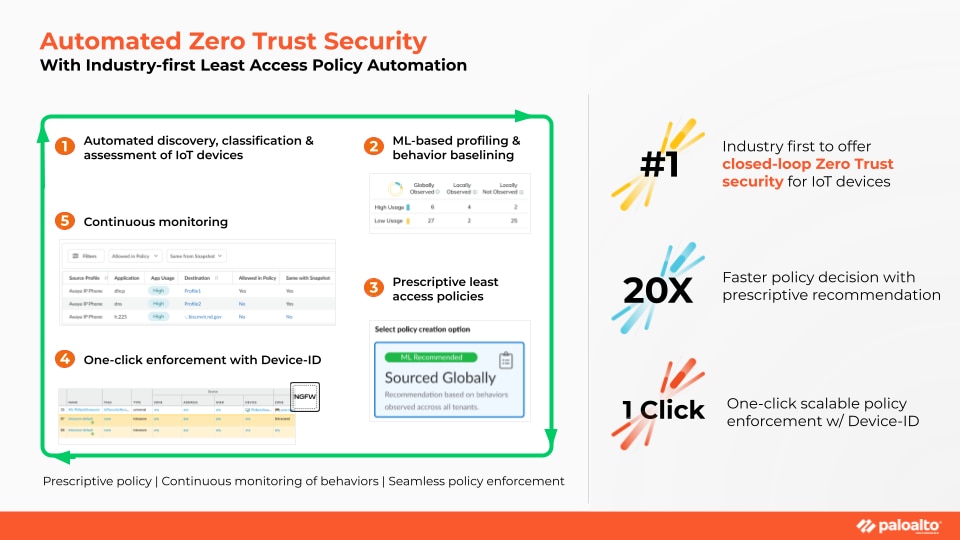
The IoT Security solution helps U.S. agencies leverage their current Palo Alto Networks Next-Generation Firewalls (NGFWs) to help automate Zero Trust security for IoT devices as follows:
- Automated Device Discovery, Classification and Assessment – The agentless IoT security solution uses ML and deep-packet inspection in combination with crowdsourced telemetry to discover and classify every connected IoT device in the network, including unmanaged devices. IoT Security then detects and assesses risk by analyzing crowdsourced device data, ML-powered behavior anomaly assessment, proprietary Unit 42 threat research, common vulnerabilities and exposures, as well as third-party vulnerability management information.
- ML-Based Profiling and Behavior Baselining – The solution automatically ascertains the device's identity and verifies "normal behaviors.” Once normal behaviors are determined, the solution kicks in anomaly detection to uncover and prioritize any potential deviation from the baseline.
- Prescriptive Least-Access Policy – Least access as a policy is a key tenet of Zero Trust. IoT Security automatically provides risk-reducing Zero Trust least-privileged access policies by comparing metadata across millions of IoT devices with those found in your network. For each IoT device and category of devices, it provides recommendations to restrict or allow trusted behaviors and help implement Zero Trust strategies without painstaking manual processes.
- One-Click Enforcement – IoT Security enforces the recommended Zero Trust security policies natively with one click via our NGFWs. Our patented Palo Alto Networks Device-ID™ policy-construct tracks all IoT devices across the network and applies policy regardless of changes to the device’s IP address or location.
- Continuous Monitoring – Continuous monitoring is the final and crucial step in closing the Zero Trust security loop for IoT devices. Continuous monitoring ensures that if and when a connected device is found to be compromised, its access to the resources and the network is blocked immediately. Continuous monitoring also helps to refine policies over time.
![Table showing automated Zero Trust Security with industry-first least access policy automation.]()
Network-Level IoT Security for Federal Agencies
Given the dynamic nature of IoT and the environment in which devices are deployed, it is critical to go beyond embedded device security and have the capability to dynamically secure the data center, healthcare and critical infrastructure network extending from headquarters to branch offices, to work-from-home settings, in real-time.
Networks can and should be a priority detection and enforcement point for IoT device security. Technologies exist today, grounded in ML, to help federal agencies realize this goal.
Learn more about the importance of putting IoT security at the forefront of your agency’s Zero Trust strategy by reading our white paper: The Right Approach to Zero Trust for IoT Devices.