As a leader in the network, endpoint and cloud security markets, we collect an incredible amount of data that can be ingested and integrated to feed machine learning, analytics and automation that could provide immense value and revolutionize the Security Operations Center (SOC). But, it’s largely discarded by the SIEM because they aren’t designed to use this data.
How do we know the data we collect can work wonders in the SOC? Because we do it in our own SOC:
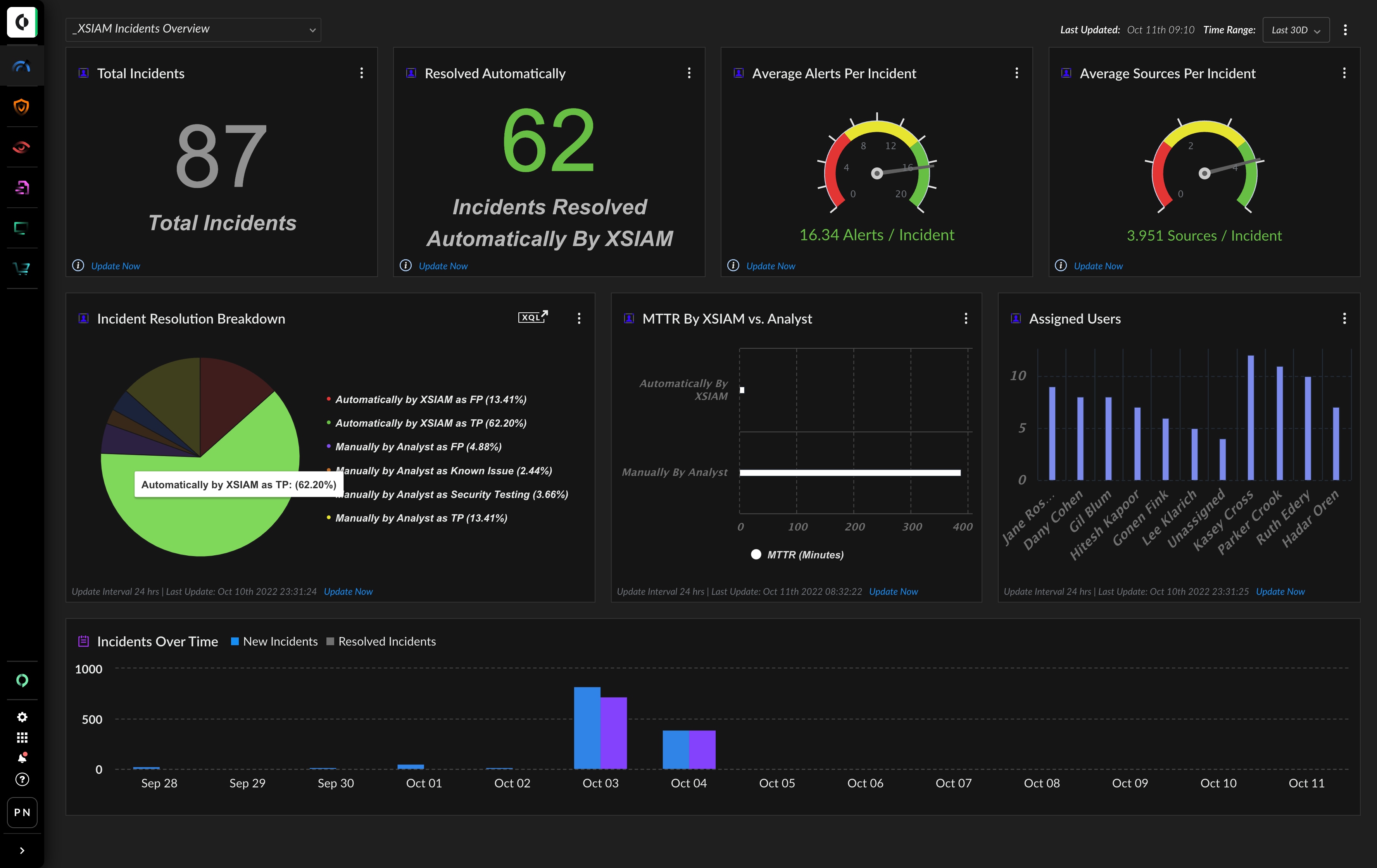
- The Palo Alto Networks SOC ingests over 1 trillion events per month, nearly 40 billion per day, and intelligently groups and analyzes alerts, resulting in only eight incidents a day on average in need of investigation.
- Our mean time to detect is ten seconds, and our mean time to respond to high priority alerts is one minute, all with a relatively small global team working regular hours.
- Our analysts do the kind of interesting and valuable security work they joined the industry to do, without burnout or heroics, because we’ve built our SOC on a platform designed from the ground up, for the modern threat landscape.
And your SOC can, too, with XSIAM – the autonomous platform powering the modern SOC, which I am excited to share, is now generally available.
Before we detail exactly how XSIAM can revolutionize the SOC, let’s explore the issues security operations is currently facing.
The SIEM Just Isn’t Working
What’s become increasingly clear is that SIEM just isn’t working for many customers: they complain it’s too expensive, too hard to manage, too hard to operate, and it fails at the most important task – helping stop threats and keep organizations safe.
Be a Defender, Not Just a Detective
It’s not difficult to see that there’s a problem. Whenever an organization suffers an attack, they are always able to figure out what happened afterwards. They can reconstruct methods, know which systems were affected and which information was taken. But, if the data is available to understand what happened afterward, why couldn’t it have been used to stop the attack in the first place? The answer, sadly, is that too many alerts and too many silos ultimately lead to too little insight.
The problem is that SIEMs are built to digest and prioritize alerts, then present them to analysts for triage and investigation. But, the amount of alerts keeps growing, so the analysts simply can’t keep up. Of course, today there is so much more data than just alerts and logs. Without the ability to handle that larger data set, and more importantly, to make sense of it for early detection and response, a huge opportunity is lost. Further, the modern SOC processes EDR, NDR, cloud, identity, threat intelligence and other types of data, but all in silos and almost never as part of the SIEM.
Not a Cost Problem, but a Value Problem
Contrary to what some vendors say, this isn’t a cost problem. It’s a value problem. However, we believe it’s possible to address both: dramatically improved value and lower cost. If your SOC could ingest ALL relevant data, apply machine learning to detect in real time, and apply automation to free up humans to do what only humans can do, it would dramatically improve the ability to detect attacks in real time and respond fast enough to prevent successful breaches. That’s the promise of SIEM, but it’s a promise that hasn’t been fulfilled.
Our customers asked us if we could build something better. So we did. Since February, we’ve worked with design partners to tune XSIAM, and the feedback has been strong:
“XSIAM is already helping us to resolve and address threats way more quickly and efficiently, reduce risk and track metrics,” said Paul Alexander, director of IT operations at Imagination Technologies Group, an international leader in the creation and licensing of semiconductor System-on-Chip Intellectual Property.
"From our first demo of XSIAM as part of the early access program, we were shocked and impressed with the maturity of the platform,” said Randy Watkins, chief technology officer at Critical Start. “This was not a beta product, but a solution that customers would immediately be able to build their entire security operations program around. The data models within XSIAM are some of the best approaches we’ve seen to solving the lack of consistency with log management.”
Revolutionize the SOC with XSIAM
We believe that the only way a SOC platform can operate at today’s scale is to completely rebuild from the ground up. So we’ve done exactly that with XSIAM, the autonomous security operations platform designed to enable all customers to achieve the outcomes Palo Alto Networks does in our own SOC. How? It all comes down to data that drives analytics, automation and proactivity.
Data and Analytics: Much More Detail, Much More Insight
When designing XSIAM, we started with an assumption that it would have to collect massive amounts of data (more than just alerts and logs) to implement our vision for analytics. XSIAM would need to pull data from endpoints, the network, identity systems, the cloud and data about the environment itself (such as, attack surface data). To use this data as the foundation for analytics, XSIAM must normalize it, understand it, and integrate it (i.e. stitch it together), so our machine learning doesn’t process it as unrelated subsets, but with an understanding of how the data elements relate to each other.
Imagine how much more intelligent a system can be if it analyzes every event from the perspective of the endpoint, the network, the identity systems and the cloud, all at the same time. And then uses that context to drive the detection, investigation and response capabilities.
Automation: More Than Workflow
When we talk about automation, we don’t just mean workflow automation, (i.e. automating what a human analyst does with an alert). We also mean native automation embedded into the product to normalize and stitch events together into an “attack story,” to create new detectors to dispatch alerts, etc. With XSIAM we have built this native automation in addition to workflow automation. In some areas, we’ve combined the two. For example, XSIAM can recommend new playbooks or response actions based on machine learning, thereby making workflow automation (SOAR) more powerful.
Proactivity: Actually Getting Ahead of Attacks
If you were to talk to SOC analysts, many would describe their job as reactive. But, defending against attacks is a lot easier if they never happen, so we decided to provide capabilities for the SOC to get ahead of attackers. An excellent way to do that is to start proactively looking at the attack surface and which systems are vulnerable before an attacker discovers an opportunity to exploit something that's misconfigured, open or otherwise at risk. Embedding attack surface discovery and response into XSIAM frees the analyst from the cycle of responding to never-ending alerts.
What can a “liberated” SOC actually accomplish? Analysts can actually hunt threats. They can look at the attack surface and take action to secure it before a vulnerability becomes an attack. In our own SOC, we’ve seen the benefits of proactive security combined with greatly-improved response. It’s turning 36 billion daily events into zero major incidents through effective analytics, automated response and a continuous reduction in the attack surface.
Check It Out for Yourself
At Palo Alto Networks, we've been here before. Sixteen years ago, the IT world was struggling with traditional firewalls, trying to surround them with IPS, URL, sandbox and proxy systems to fix all their gaps. We saw that the only way to solve the problem was to start over and design something from the ground up – the next-generation firewall. For the SOC, it’s time to stop surrounding the SIEM in hopes you can hide the flaws; it’s time to fix it from the ground up with data, analytics and automation. All of that is to say we understand what it takes to revolutionize a market, and we know this is going to be a journey – one we’re excited to begin with XSIAM.
Today, I am happy to share that it’s generally available, and we are excited to tell you even more. You can read more on the website and download our solution brief. In addition, on November 2 we’ll hold an online launch event including a demonstration, and we’d love to have you join us.
XSIAM is ready, and the future of the SOC is here.