Cloud Identity and Access Management (IAM) solutions represent a foundational component of a cloud native security platform. Yet, most enterprises that manage large numbers of cloud accounts and resources currently struggle to gain visibility and effectively govern permissions for them.
The new Prisma Cloud IAM Security module addresses these challenges by providing broad visibility of effective permissions, monitoring for risky and unused entitlements, and least privilege recommendations with automated response. Users get simple yet powerful IAM security controls across their cloud environments, seamlessly integrated into Prisma Cloud.
Addressing Requirements for Cloud Infrastructure Entitlement Management
Over-permissive roles, poor credential hygiene, and accidental public exposure have all contributed to some of the most significant vulnerabilities of enterprise cloud environments. Security tools for cloud infrastructure entitlement management (CIEM) address these challenges, which are often insufficiently addressed by cloud services providers' built-in tools.
Prisma Cloud IAM Security is an industry-leading CIEM solution, on top of other identity security functionality. It provides users an easier path to achieving least privilege access – a security best practice that says each user or service account gets the minimum amount of entitlements needed to perform a given task.
By taking a uniquely comprehensive approach that combines greater visibility and granular access control along with user entity and behavior analytics (UEBA), Prisma Cloud reduces alert fatigue by delivering high-fidelity, contextual alerts on suspicious identity-related activities.
IAM Security Module in Prisma Cloud
Here’s how the new IAM security controls can help users:
Visibility to Net-Effective Permissions
Gain deep visibility into who has the ability to take what action on which resources. By running complex calculations that analyze permissions such as Amazon Web Services (AWS) IAM roles, policies and groups; AWS resource-based policies; and AWS service control policies (SCPs), the IAM Security module can precisely determine net-effective permissions.
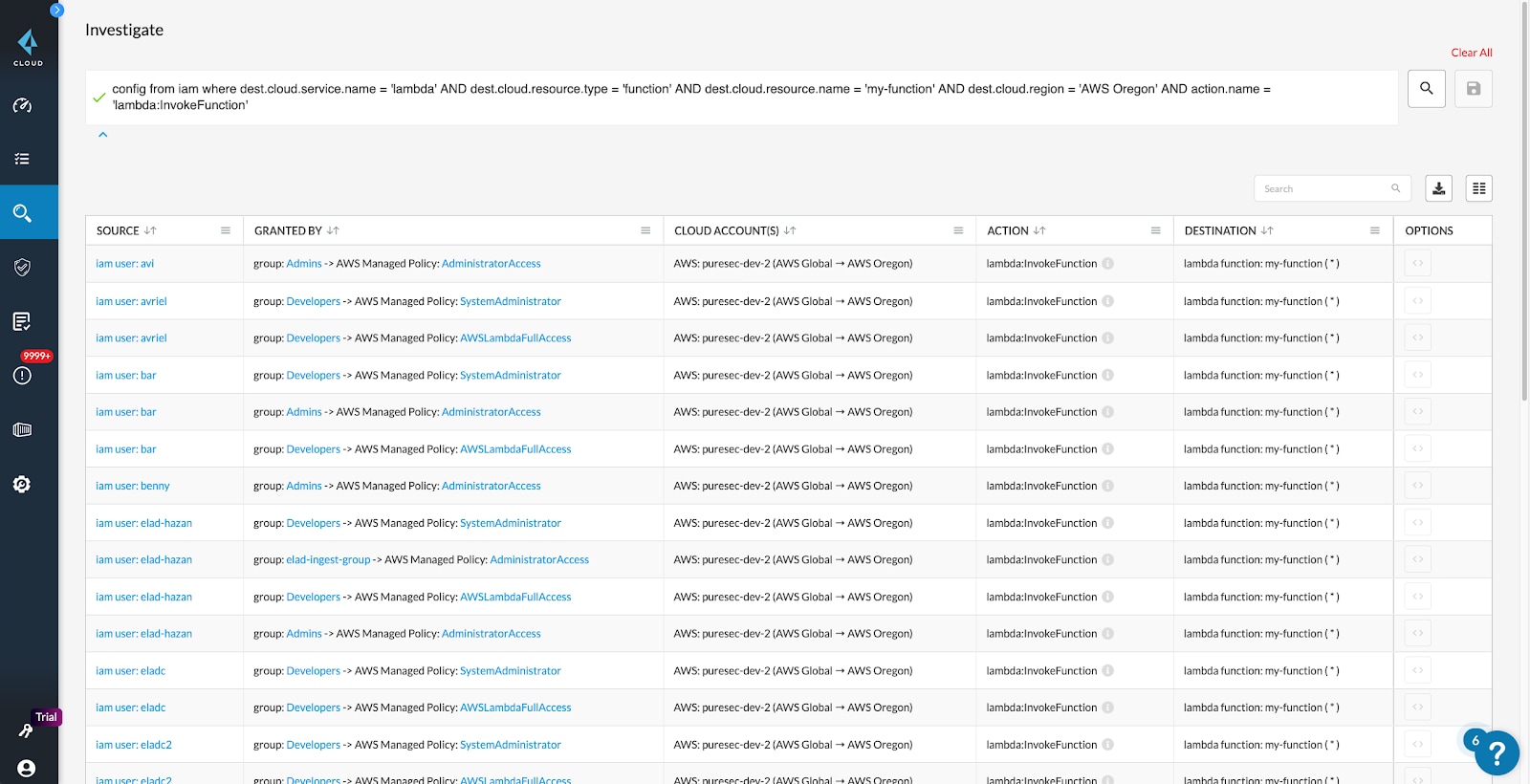
Rightsizing Permissions
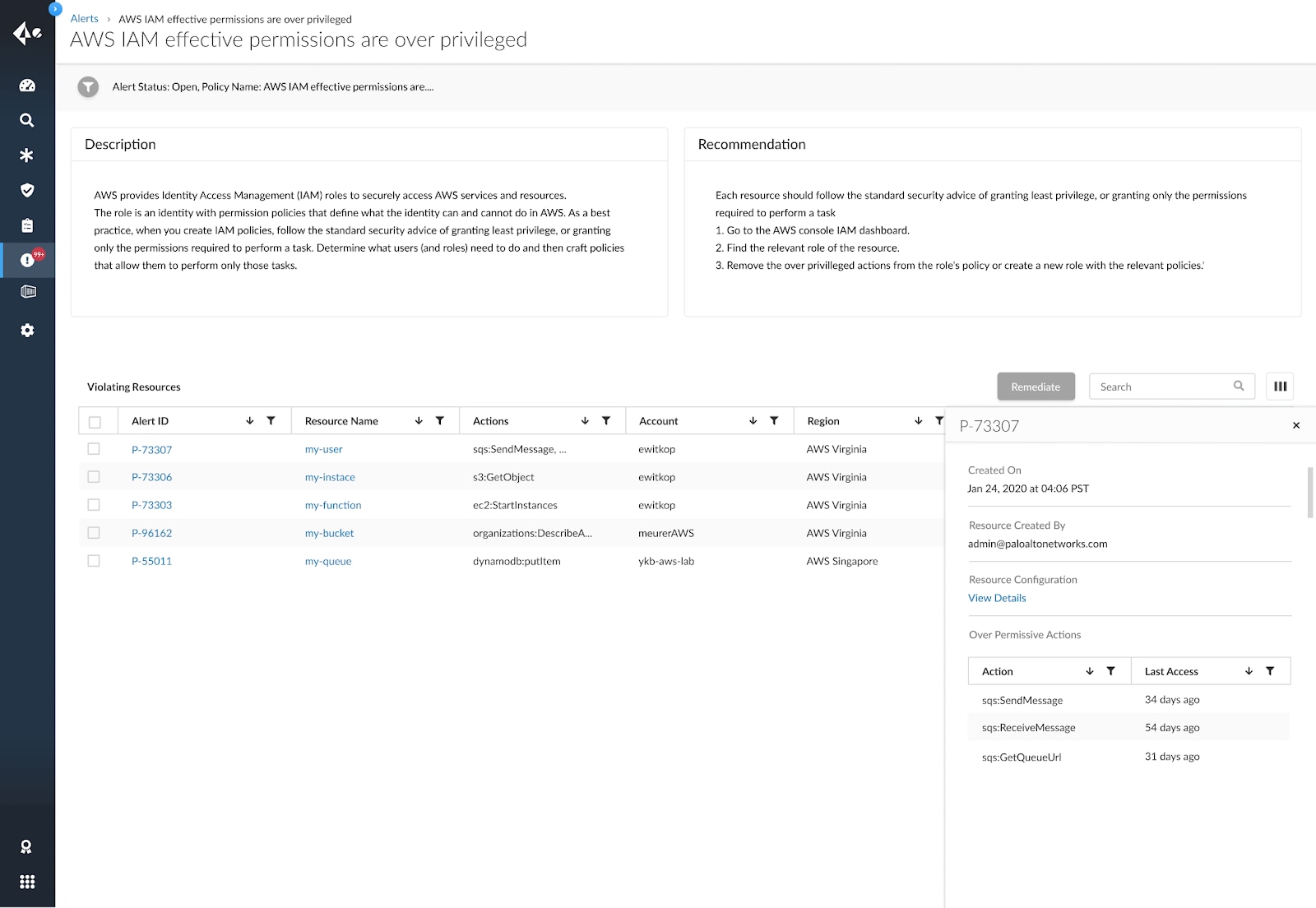
The Prisma Cloud IAM security module ships with specialized out-of-the-box policies to detect risky permissions and help remove unwanted access to cloud resources. It can automatically detect overly permissive user access, then provide suggestions to rightsize them to achieve least privilege.
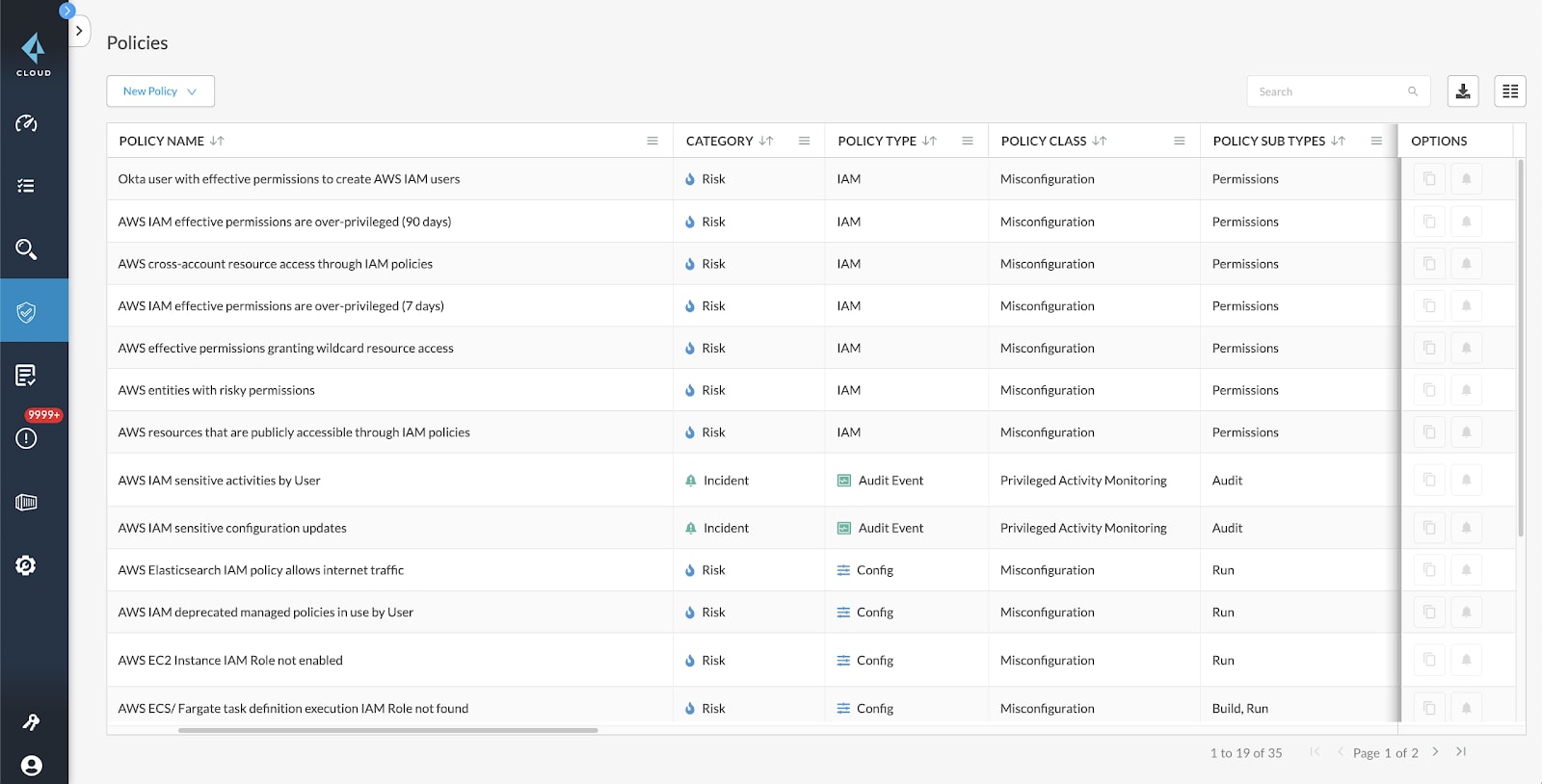
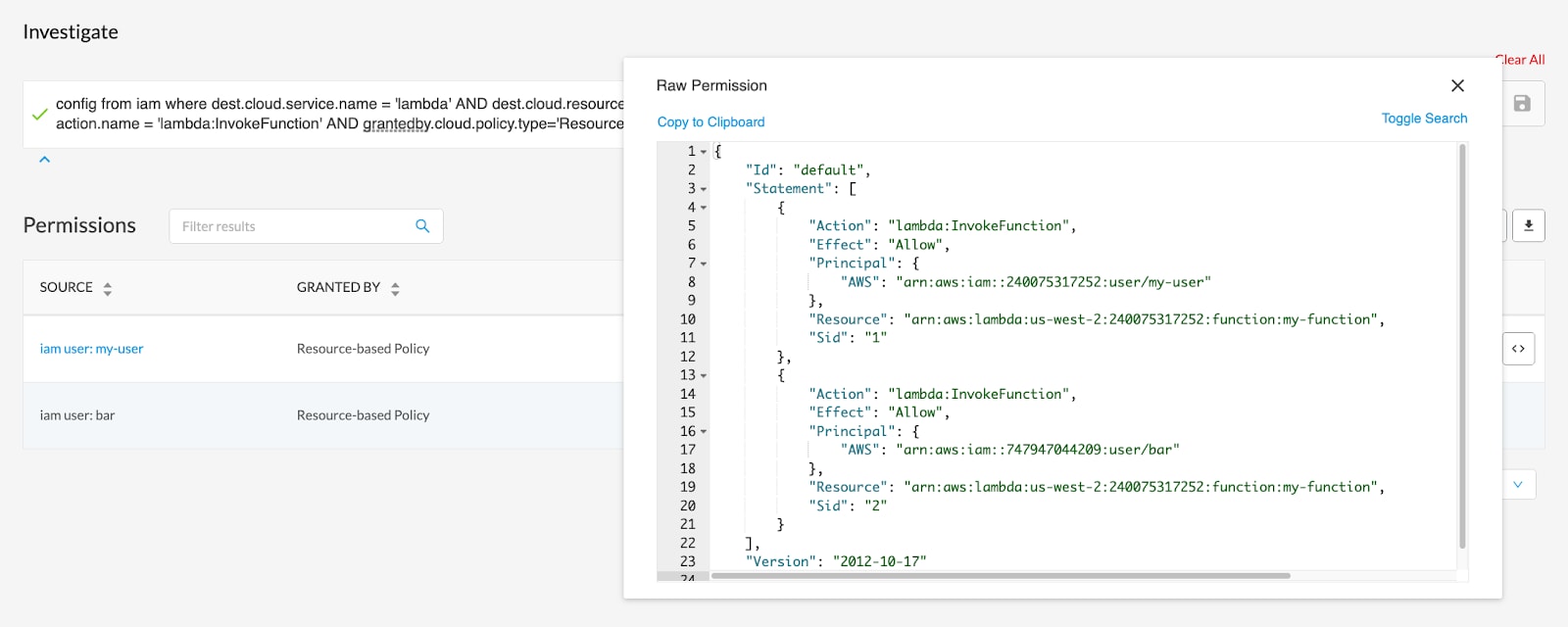
Investigate IAM Entitlements
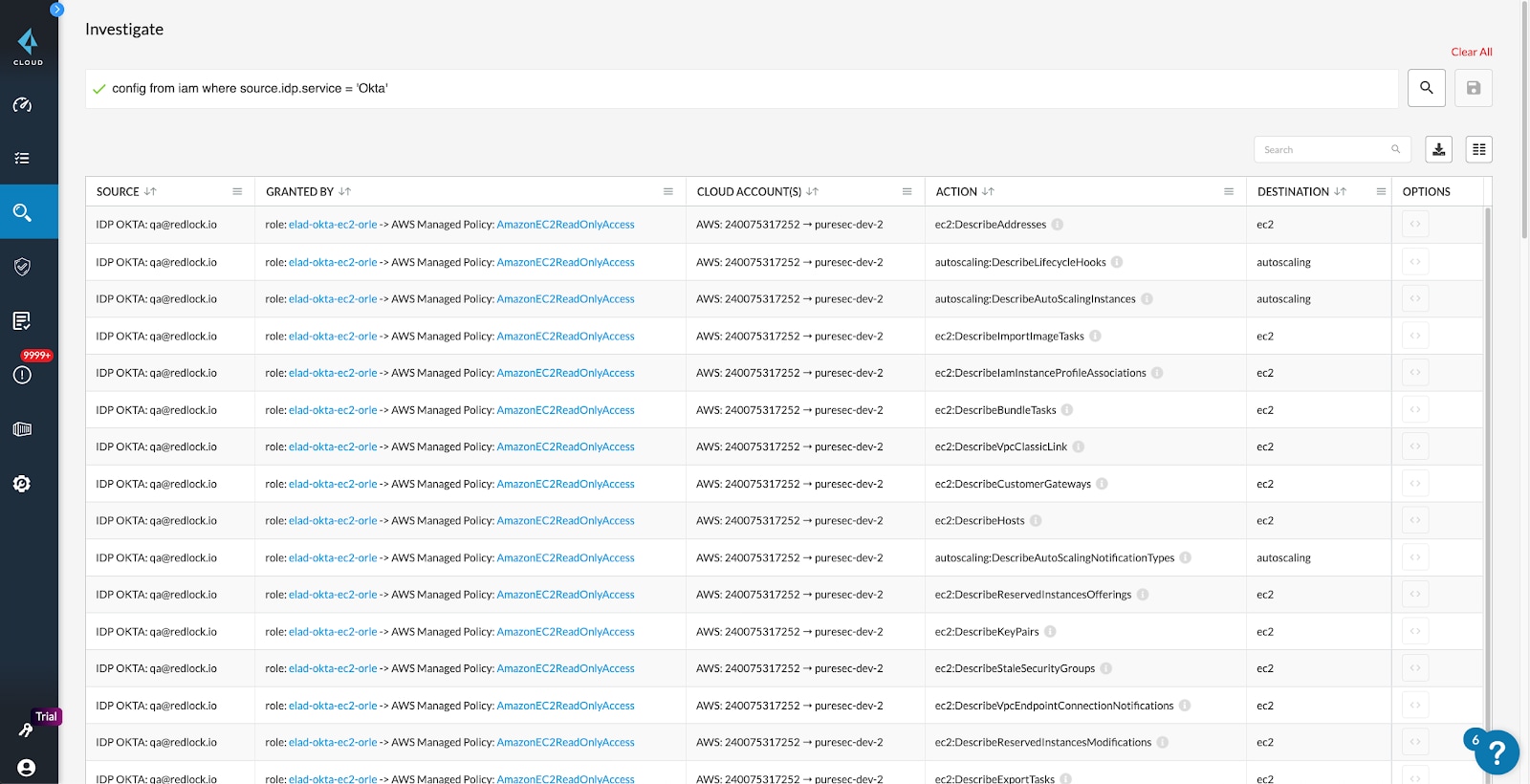
Leverage Prisma Cloud Resource Query Language (RQL) to quickly gain deeper insight into specific entitlements and their effective permissions. Ask nearly any identity-related question, such as:
- Which users have access to a given resource
- What accounts, services, or resources a specific identity has access to
- Whether any users outside of a specific group have access to a given set of resources
You can view documentation on Prisma Cloud RQL to see the breadth of potential insights.
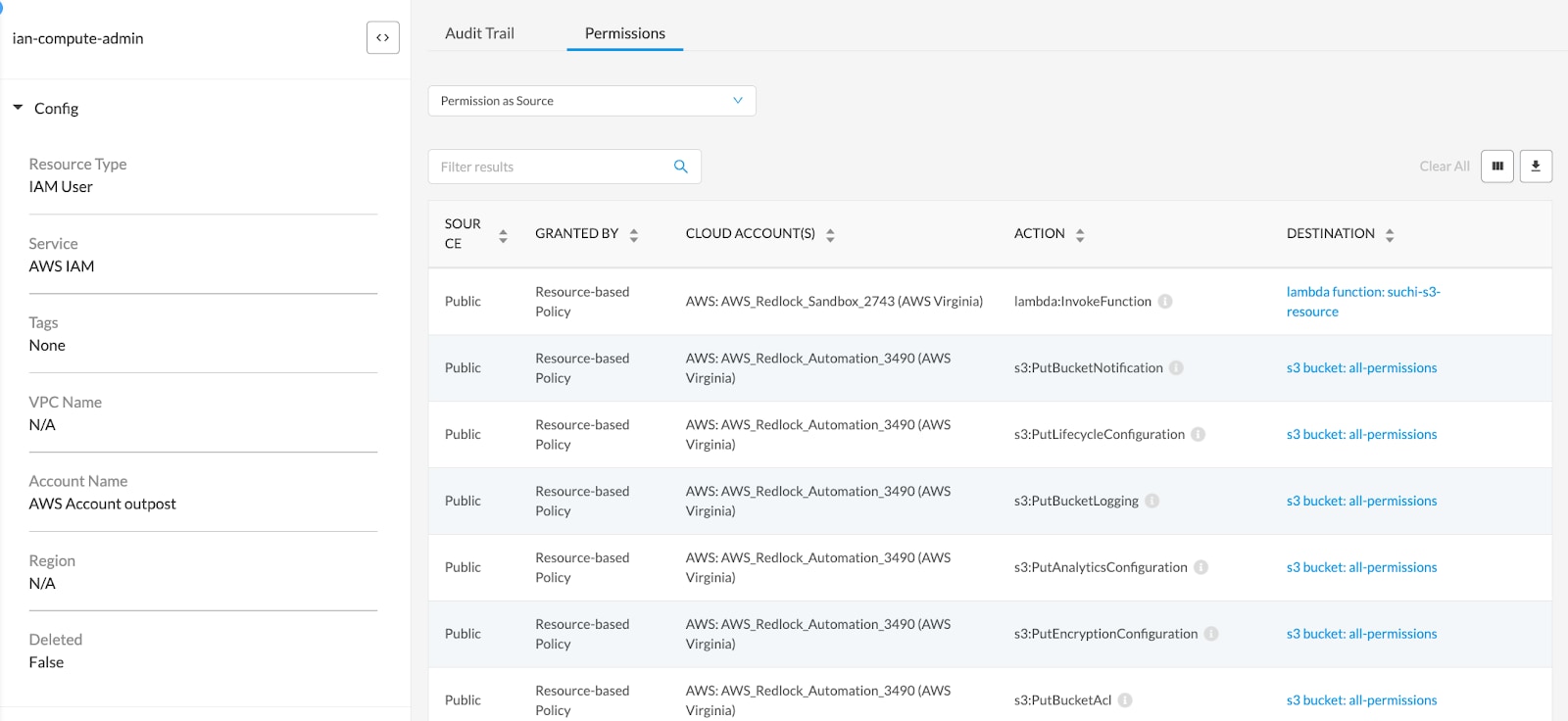
Audit Permissions for Internal Compliance
In addition to the existing resource audit trail which captures any change made to a resource from the moment it’s first deployed, the new permissions tab displays all of the permissions “of” a resource and “to” the resource. It also enables users to look back and understand when an overly permissive entitlement was granted and by whom.
Identity Provider Integration: Okta
Federate user identities with existing identity providers and management systems to prevent unnecessary management overhead like system duplication. Prisma Cloud integrates with Okta to ingest single sign-on (SSO) data for an effective permissions calculation and enables users to list the effective permissions of Okta users across cloud accounts.
Auto remediation of Over Privileged Users
IAM Security helps users maintain good identity and access management hygiene by suggesting the ideal permissions level for any cloud user. Automatic permissions adjustments can ensure continuous enforcement of least privilege access.
Start Using the Prisma Cloud IAM Security Module
Combined with the rest of the functionality in the recent release, the IAM Security module gives users the most comprehensive platform for cloud native security available today.
To learn more about best practices for IAM security, including the depth of threats presented by misconfigurations, check out the Unit 42 Cloud Threat Report 2H 2020.