On September 27, 2023, Progress Software released an advisory alerting customers of a critical vulnerability (CVE-2023-40044) in their WS_FTP Server product. WS_FTP Server is a secure file transfer server software designed to facilitate the exchange of files between a local computer and a remote server. This critical vulnerability is concerning since it could allow an attacker to execute arbitrary code, potentially compromising a system and gaining privileged access to sensitive data.
Since this CVE was announced, Cortex Xpanse researchers have observed over 11,900 instances of WS_FTP servers across the global internet. According to cyber research engineer, Choman Saleem, the majority of responses have been identified through TCP/22 (SSH) and TCP/21 (FTP) services, and many of these instances are running versions known to be vulnerable. The low-complexity nature of the vulnerabilities further underscores the urgency of addressing them.
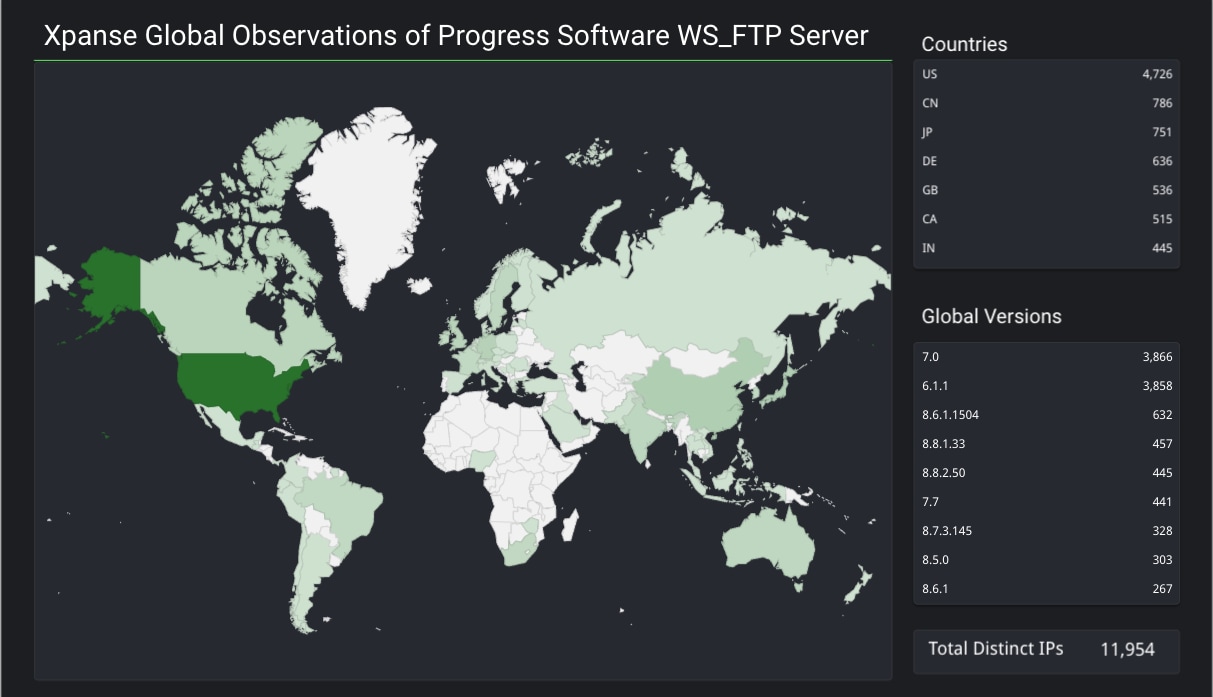
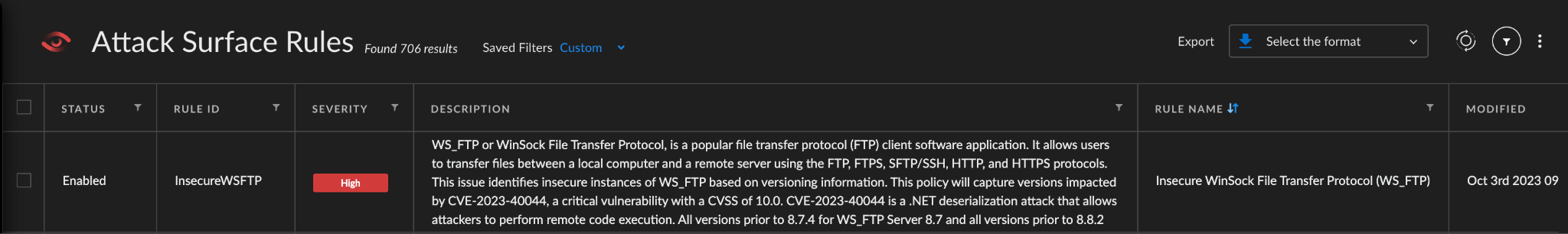
To mitigate the risks associated with the WS_FTP vulnerability, organizations should proactively manage their attack surface. Xpanse has developed an Attack Surface Rule designed to identify exposed instances of WS_FTP, enabling organizations to promptly detect and address vulnerabilities, thereby reducing the risk of exploitation.
In addition to deploying an Attack Surface Rule for WS_FTP, Xpanse also incorporates threat intelligence data into its platform via its Threat Response Center. By utilizing the latest information concerning high-priority vulnerabilities, methods used for exploitation, and threat actors, Xpanse enables organizations to take proactive measures to mitigate vulnerabilities before they become widespread. This information substantially boosts an organization's capacity to strengthen their defenses against emerging threats, including the WS_FTP vulnerability.
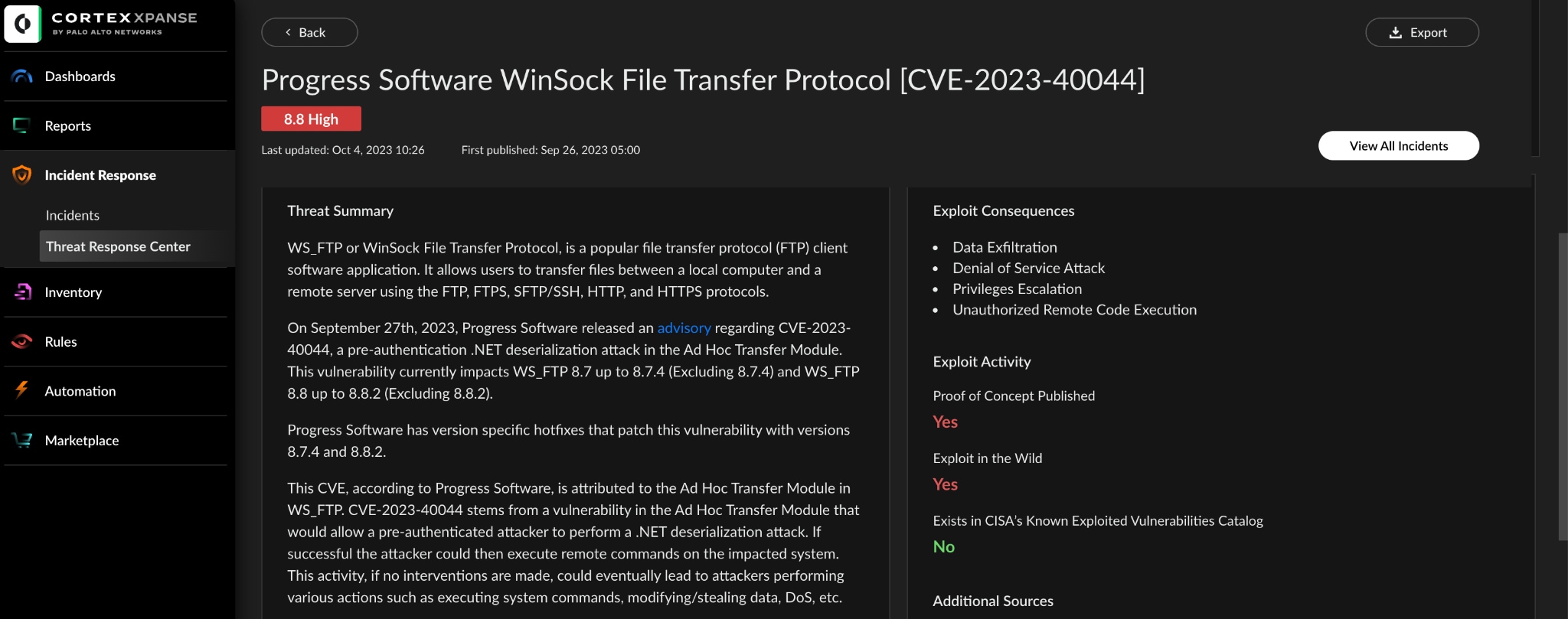
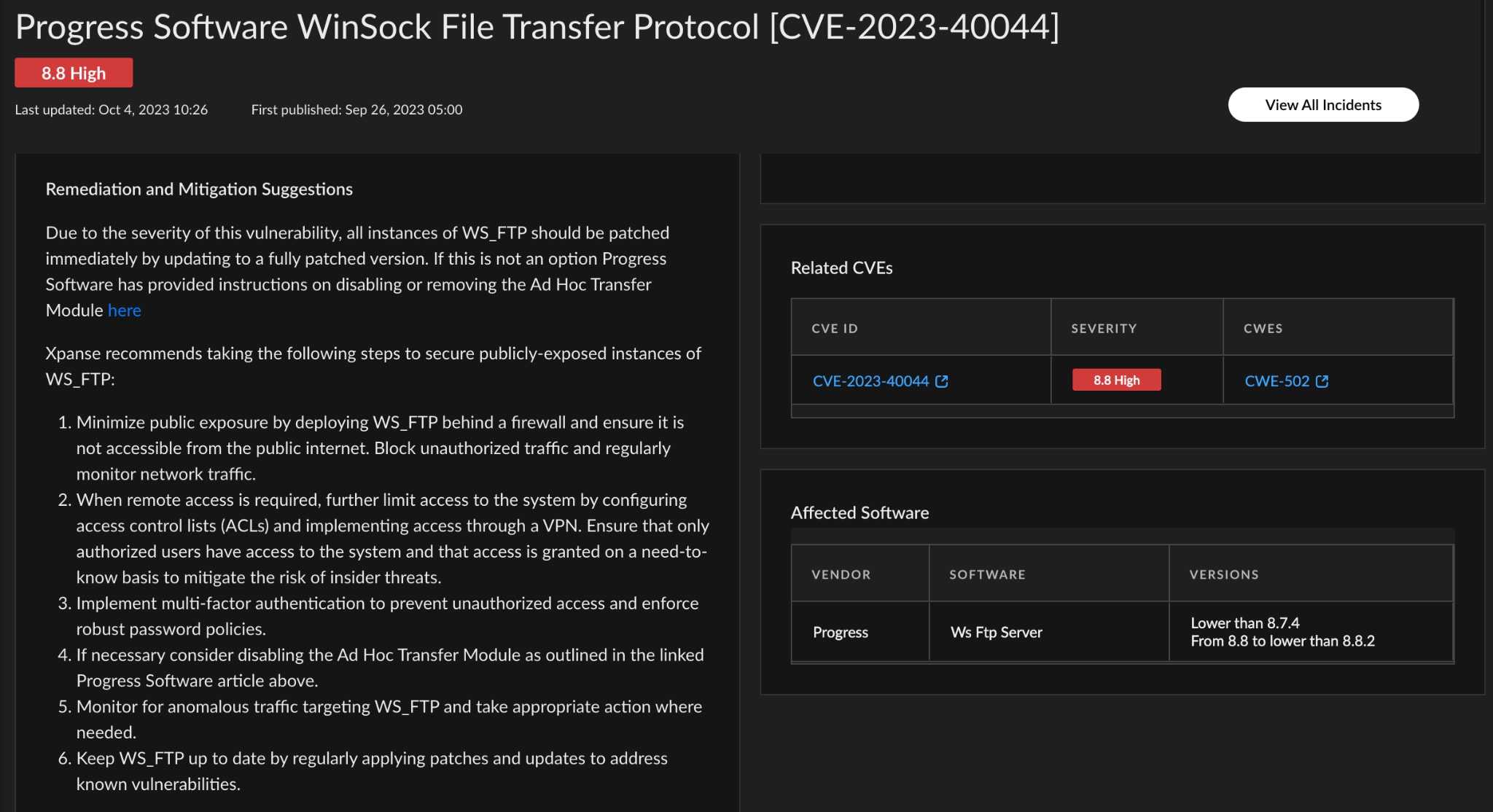
If you have identified a vulnerable and exposed instance of WS_FTP, you should take immediate steps to remediate the issue. Cyberattacks targeting this vulnerability can result in financial losses, legal consequences, damage to reputation, and significant disruption to individuals and organizations. With its dedicated Attack Surface Rule for WS_FTP technologies, and Threat Response Center alerting, Xpanse offers organizations an enhanced capability to actively seek out and remediate vulnerabilities, thereby strengthening their overall security posture.
To learn more about the Threat Response Center, read our datasheet.
Palo Alto Networks Unit 42 further illuminates some of the riskiest security observations around attack surface management (ASM) with the 2023 Unit 42 Attack Surface Threat Report.