What happens when you combine the industry’s first extended detection and response platform with the industry’s most comprehensive security orchestration, automation and response platform? The impossible suddenly becomes possible.
Your sea of alerts parts to reveal a manageable number of actionable incidents. You gain the power to enrich alerts based on your unique threat intelligence policies and reputation sources. And you can automatically stop attacks by blocking and quarantining files and isolating endpoints with comprehensive security playbooks which are available out-of-the-box.
The Cortex XDR Content Pack is Available Now in the Cortex XSOAR Marketplace
If you own both platforms, you can take advantage of this powerful combination today, by simply adding the Cortex XDR Content Pack with the click of a button in the Cortex XSOAR Marketplace. Content packs provide prebuilt playbooks, dashboards, integrations, and more that help you orchestrate and automate end-to-end security operations workflows. With the content pack, you can skip writing playbooks and instead focus on eliminating threats.
The free Cortex XDR Content Pack is packed with content, including:
- 16 orchestration playbooks
- 4 automations
- 2 integrations
- 4 layouts, plus classifiers, incident types and fields
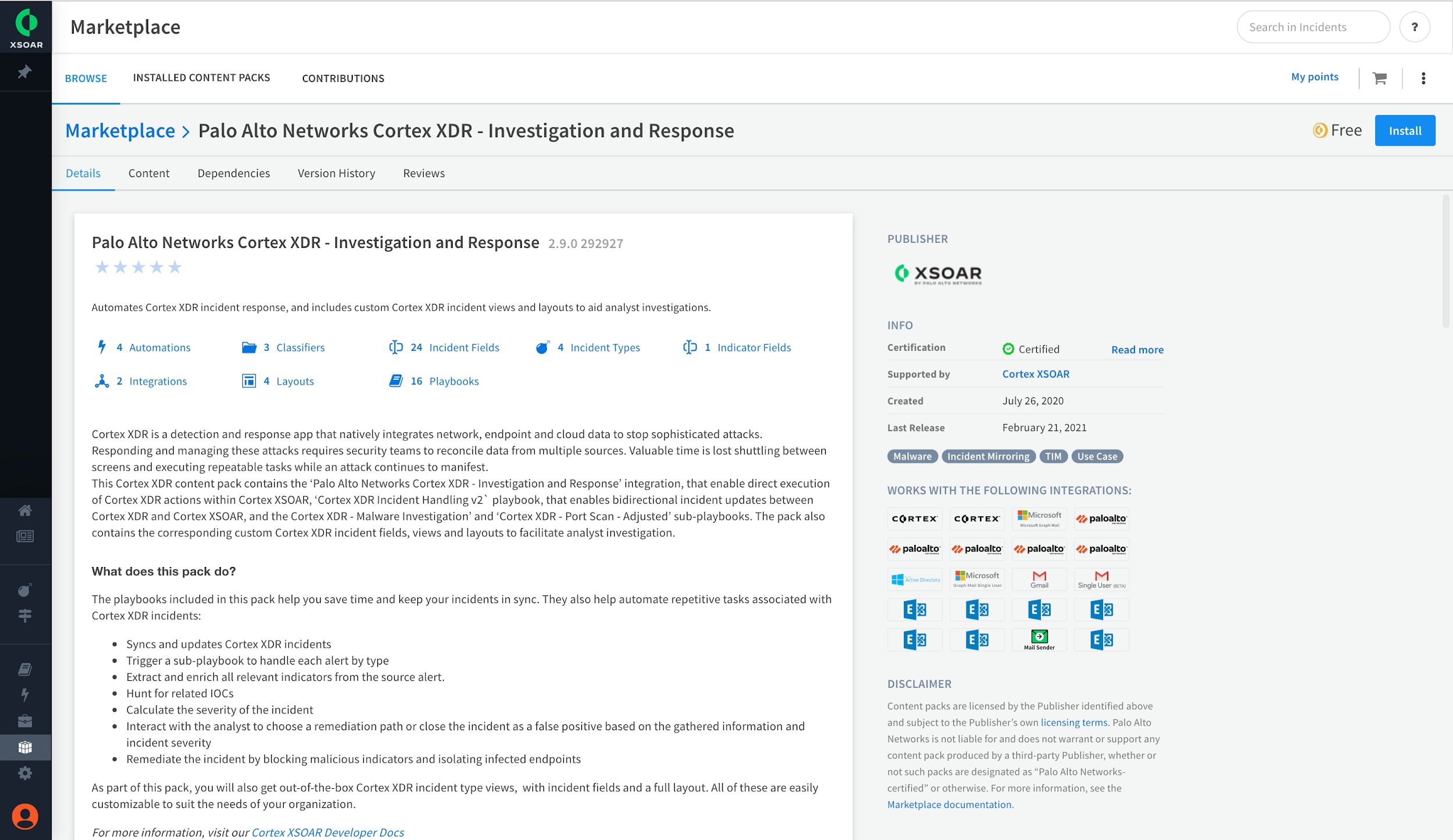
The Cortex XDR content pack in the XSOAR Marketplace
The Cortex XDR Content Pack solves today’s top SecOps challenges that many security analysts struggle with, including limited visibility and manual, repetitive tasks that can slow down incident response. Most security teams lack the resources to manually enrich alerts or hunt for indicators of compromise (IOC). They waste valuable time performing the same process over and over again, such as detonating suspicious files in incidents.
The content pack demonstrates the power of the Cortex platform by enabling analysts to perform detection, investigation, and response, as well as case management, orchestration and collaboration holistically. As an example of what this content pack can do for you, today, when your analysts see a port scan alert, they might need to gather threat intelligence on the source of the port scan, analyze the endpoint process that initiated the scan, isolate the endpoint and notify SOC management. The content pack automates these manual steps with a port scan playbook.
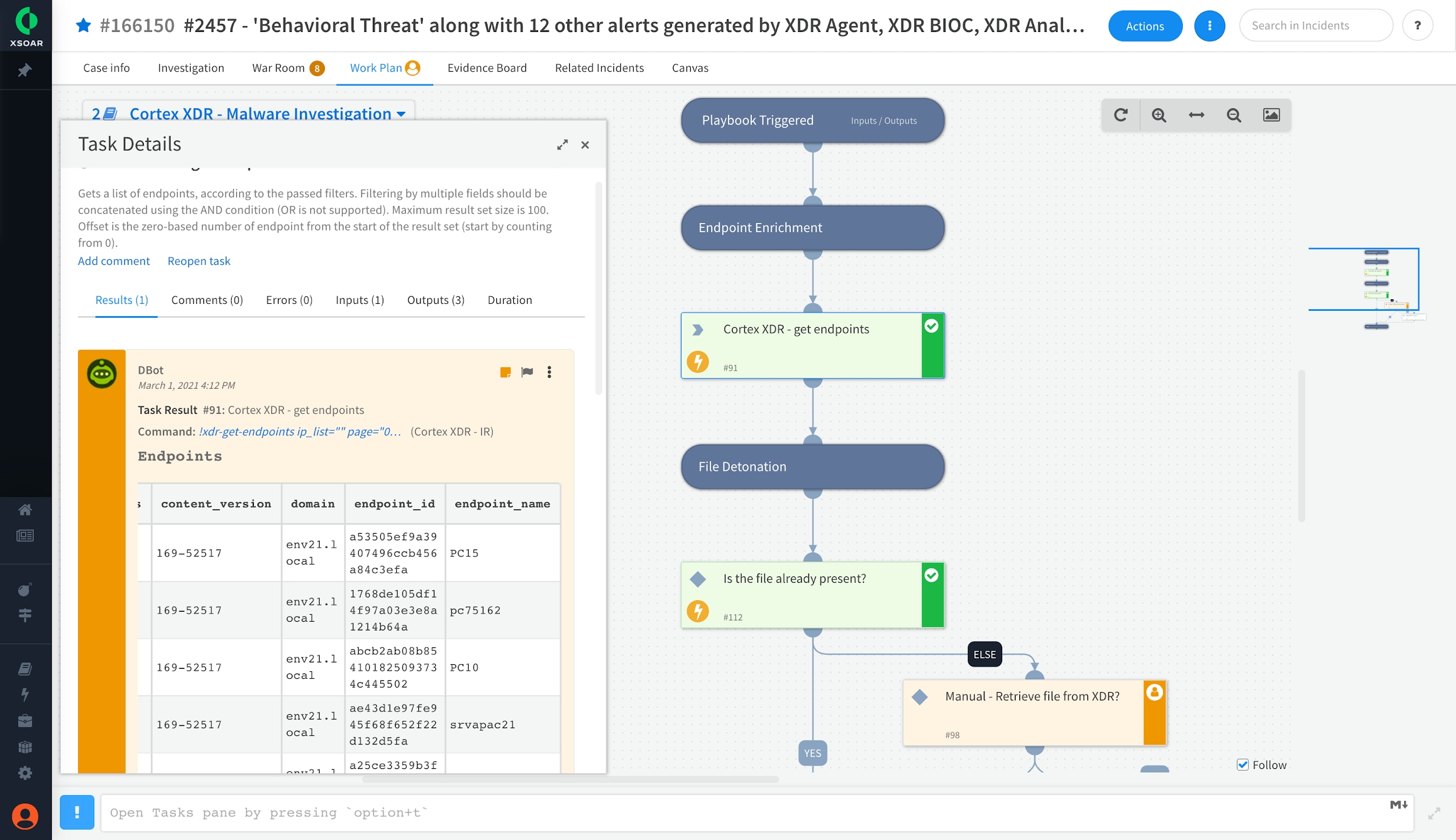
The malware investigation playbook enriches endpoint alert data and detonates files
The playbooks in this content pack help you avoid repetitive tasks, reduce manual errors, and speed response times by:
- Extracting and enriching all relevant indicators from the source alert.
- Hunting for related IOCs.
- Updating the severity of an incident based on threat intelligence information.
- Letting analysts easily enrich, investigate, and remediate threats across your full security stack with the comprehensive capabilities of Cortex XSOAR.
- Syncing incident updates between the platforms.
The content pack also delivers out-of-the-box Cortex XDR layouts and incident type views with predefined incident fields. You can easily customize all this content to suit the specific needs of your team and your environment.
When it comes to protecting your organization, your security technology needs to streamline and automate threat detection and response to stay ahead of new and evolving threats. Cortex XDR and Cortex XSOAR work as a force multiplier for detecting and responding to threats. With the Cortex XDR Content Pack available now in the Cortex XSOAR Marketplace, unleashing this power has never been easier.
Learn How Your SOC Can Benefit from the Cortex X-Factor
Join us on March 25 at 9:00 AM PST for the webinar “Cortex® XSOAR Marketplace Top Use Cases Webinar,” to learn how to use Cortex XSOAR and Cortex XDR together to take your investigation, hunting, and response to the next level. We will discuss best practices for using the new Cortex XDR Content Pack and provide you a demo of the content pack playbooks and integrations. Save your seat today!
Don’t have Cortex XSOAR? Download our free Community Edition today!