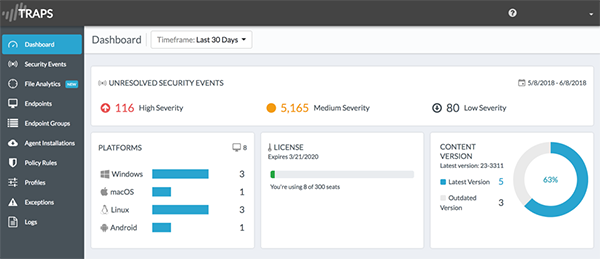
Protecting Endpoints From Day One
Deploying and managing endpoint protection shouldn’t be difficult. However, customers of traditional endpoint protection products complain about day-to-day management, database maintenance, agent updates, and constant tuning to eliminate false positives and keep resource utilization in check. Worst, even with all this work, endpoints still get compromised.