Preventing Attacks at Every Stage of the Attack Lifecycle for a Secured Future
Security teams face unprecedented challenges as cyberthreats become more sophisticated and unpredictable. Legacy security architectures, built for a more predictable cyber environment, can struggle to keep up with the speed and complexity of modern attacks. Enterprises now contend with a wider attack surface, an increasingly intricate security stack and a lower barrier to entry for attackers. Additionally, security teams are overwhelmed by a relentless flood of alerts, a fragmented array of security tools operating in silos, and a persistent shortage of skilled cybersecurity professionals to analyze vast amounts of threat intelligence.
The rise of AI has dramatically increased the scale, speed and sophistication of cyberthreats, making it even more challenging for organizations to defend against AI-driven attacks.
Cybercriminals aren’t replacing traditional attack methods. They’re enhancing them with AI, making their tactics more efficient, evasive and harder to detect. Adding to the challenge, AI-powered attack tools are no longer limited to nation-states or elite hackers. The democratization of cybercrime means that advanced threats are now accessible to a broader range of bad actors, raising the stakes for cybersecurity defense.
Even low-level threat actors can now deploy sophisticated, automated attacks at scale, increasing both the frequency and complexity of breaches. The traditional reactive approach of detecting and mitigating threats only after they infiltrate the network is no longer sufficient. Enterprises must shift to a proactive, intelligence-driven defense strategy that anticipates and neutralizes threats before they materialize.
Today’s enterprises need a unified security approach that integrates AI-driven automation, real-time threat intelligence and adaptive security measures. This evolution in cybersecurity is no longer just an advantage — it is necessary for enterprises seeking to protect their digital assets, maintain business continuity, and stay ahead in the ongoing cyber arms race.
Stopping Threats at Every Turn
How Adversaries Leverage Deceptive Tactics to Gain Access

Cybercriminals meticulously plan their attacks, starting with reconnaissance to scan publicly exposed assets and probe for vulnerabilities. They exploit misconfigurations, leverage stolen credentials, and use social engineering to deceive employees and bypass security defenses. Once inside, they move laterally, escalating privileges and embedding themselves deep within networks to evade detection.
The attack often begins with phishing via malicious URLs, where attackers send deceptive emails containing harmful links. Unsuspecting users who click these links may unknowingly expose their credentials or download malware. Advanced URL (AURL) Filtering mitigates this by using AI-driven analysis to detect and block malicious URLs in real time, helping ensure users never reach harmful domains.
Once attackers gain access, they deploy malware by disguising threats as legitimate files to execute on an endpoint. As malware authors grow more sophisticated, they design sandbox-aware threats that are increasingly difficult to detect.
Advanced WildFireⓇ(AWF) addresses this challenge by analyzing unknown files in real time using Precision AIⓇ, static analysis and dynamic sandboxing. To counter these advanced evasion techniques, Advanced WildFire employs hypervisor emulation, in-memory analysis and other cutting-edge detection methods to uncover and stop stealthy malware. If a file is deemed malicious, Advanced WildFire blocks it before execution, effectively preventing ransomware, trojans and other advanced threats from compromising the system.
Next, the malware attempts to establish command and control (C2) communication, allowing attackers to control compromised systems remotely. Adversaries often use red team tools and obfuscation techniques to evade detection.
Advanced Threat Prevention blocks these attempts by identifying and disrupting C2 traffic through advanced deep learning models, cutting off attacker access before they can further compromise the system. And the best part? Once Advanced Threat Prevention detects a brand-new C2 destination, it will share the new threat intelligence with AURL, which will automatically add the new C2 to its database globally to protect all of our customers.
Finally, adversaries aim for data exfiltration, using clever techniques like DNS tunneling to disguise outbound traffic and evade detection. Advanced DNS Security (ADNS) thwarts this by identifying anomalous DNS patterns, blocking malicious domains and leveraging real-time threat intelligence to prevent data theft.
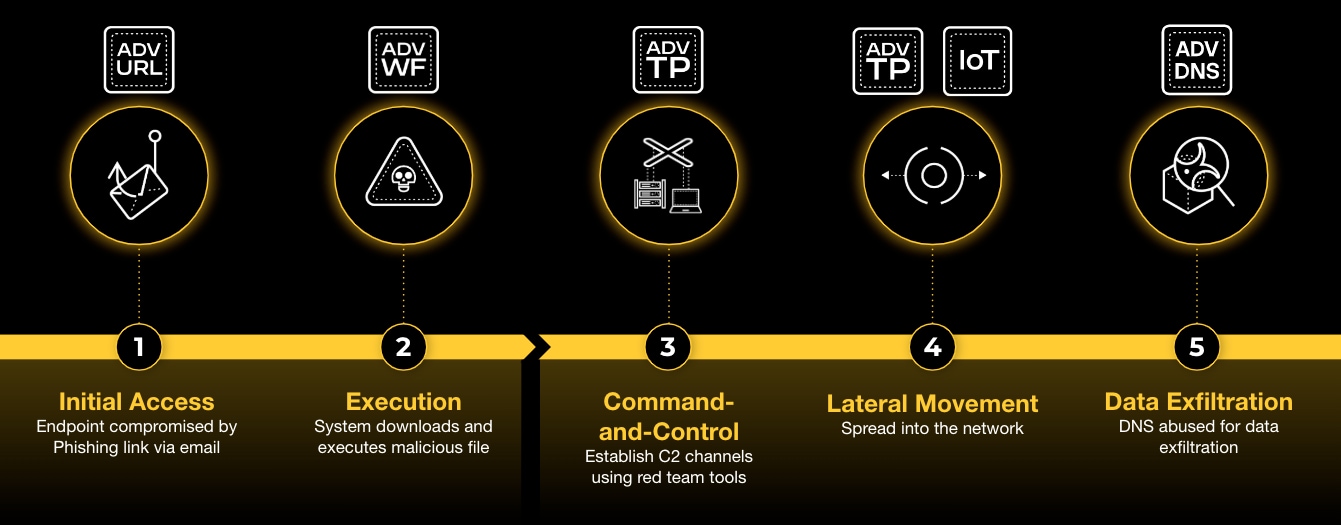
Prevention at each stage of the attack lifecycle.
From blocking phishing attempts and preventing malware execution to stopping C2 communications, containing lateral movement and preventing data exfiltration, our integrated security approach delivers comprehensive, real-time protection against advanced threats.
Tomorrow’s Threats, Today’s Solutions: The Future of Cyber Defense
Advanced Cloud-Delivered Security Services Powered by Precision AI
Palo Alto Networks Cloud-Delivered Security Services (CDSS), powered by Precision AI, provides organizations with a comprehensive security stack for their entire infrastructure. Our advanced solutions leverage Precision AI, which incorporates cutting-edge AI capabilities including machine learning (ML), deep learning, and generative AI (GenAI), to deliver trusted and effective security outcomes.
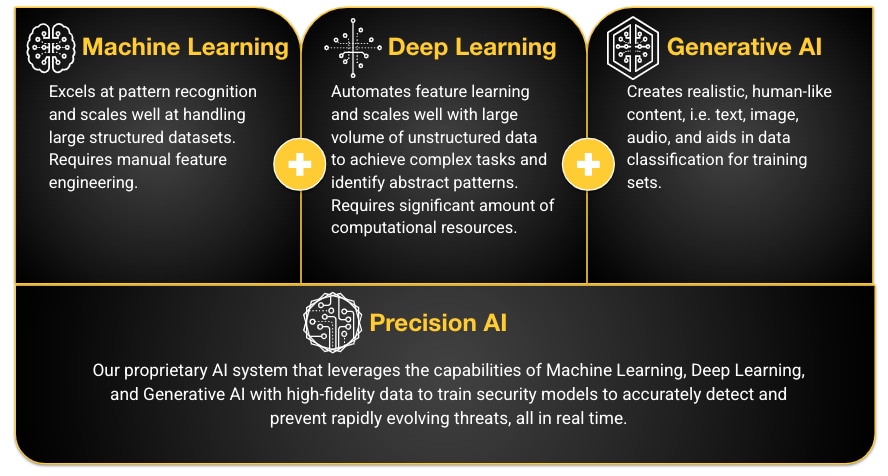
Precision AI defined.
The Palo Alto Networks advanced cloud-delivered security services work together seamlessly to stop attackers at every stage of the attack lifecycle. What started as a sophisticated multilayered attack is rendered powerless by the intelligence-driven, AI-powered security ecosystem. From preemptive exposure management to automated threat prevention, our advanced security services help ensure enterprises stay ahead of cyberthreats, protecting users, data and applications across cloud, network and endpoints, driving a 357% ROI over three years.
Stay Ahead. Stay Secure.
The industry-leading advanced security services from Palo Alto Networks offer organizations a proactive defense strategy that can reduce the attack surface, simplify security management, and make it significantly harder for attackers to exploit vulnerabilities. Our advanced security services — spanning Advanced Threat Prevention, Advanced WildFire, Advanced DNS Security and Advanced URL Filtering — combined provide comprehensive protection at every stage of an attack. When security is built for every stage of the attack lifecycle, attackers don’t stand a chance.
For more information, contact your local Palo Alto Networks representative to schedule a customized Security Lifecycle Review (SLR) and identify potential threats and vulnerabilities that may bypass your network.