Even more network security efficiency for the cloud is here. We are excited to announce you can now use the new Amazon Web Services VPC More Specific Routing feature for VM-Series virtual firewalls. This allows you to secure your virtual private cloud (VPC) traffic with Palo Alto Networks VM-Series high-availability (HA) virtual firewalls and AWS Gateway Load Balancer (GWLB)-based deployments.
As more organizations migrate to the cloud, they can rely on VM-Series virtual next-generation firewalls to augment AWS native network security controls by protecting against exploits, malware, known and unknown threats, and data exfiltration. Some of the capabilities critical to ongoing operations include full visibility and control, consistent policy enforcement, application security, exfiltration prevention, compliance and risk management, security automation, and cloud-agnostic management. And now, with the new integration between the Amazon Web Services VPC More Specific Routing feature, you can now seamlessly insert a VM-Series virtual firewall to protect traffic between the subnets within a VPC.
More Ease in Deploying Security Services Arrives
For one thing, this makes it easier to deploy production-grade applications with the security services you require within your Amazon Web Services VPC. For example, you can now redirect East-West traffic flowing between two subnets in a VPC through third-party appliances such as VM-Series firewalls.
This development also allows you to strengthen your overall security posture by allowing the inspection of all traffic between your subnets in a VPC through the VM-Series firewall stack exposed as a Gateway Load Balancer endpoint in your VPC. And to further galvanize your security posture you can also configure GWLB Endpoints as the next hop in your subnet route rules to enable redirection of all traffic within the VPC through the firewalls.
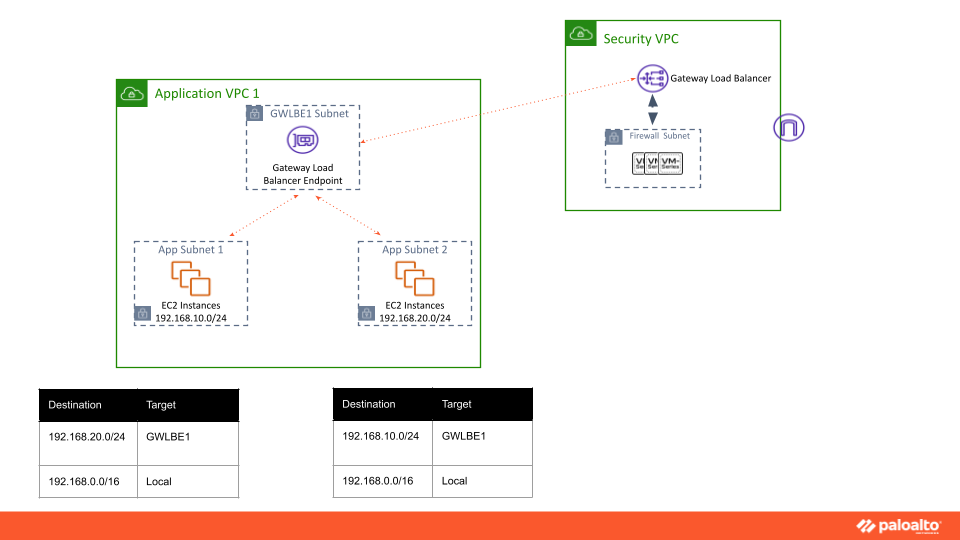
Take A More Real-World Approach to Operations
Additionally, the Amazon More Specific Routing feature facilitates siloed operations of application teams and central security teams. Security teams can continue to deploy the firewall stack in the central security VPC for traffic inspection and expose it as GWLB endpoints in the application VPCs. Previously application teams could inspect all their VPC Internet Ingress traffic using the GWLB endpoints, but they were not able to effectively inspect the Internet Egress traffic (via NAT gateway) because the firewalls lacked visibility to the non-NATed source IP of the VPC workloads. No longer.
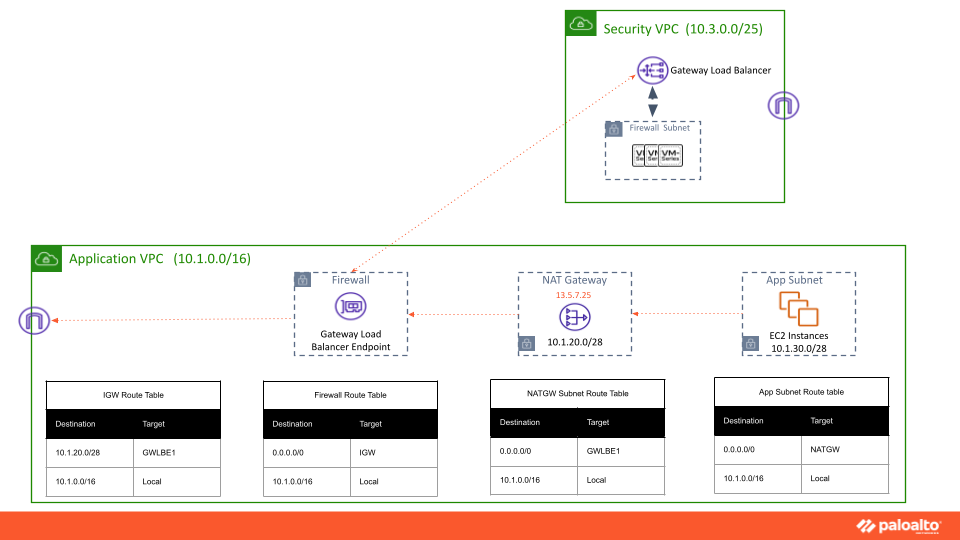
With Amazon More Specific Routing, application teams can also inspect the VPC Internet egress traffic from workloads in the private subnets, with complete visibility using the GWLB endpoints. Traffic from the app subnet can be directly sent to the GWLB endpoint, which will give more visibility to the firewall. For ingress and egress traffic, you will need to configure two separate GWLB Endpoints. The default route for the ingress GWLB Endpoint will be IGW, and the Egress GWLB Endpoint default route will be pointing to NATGW.
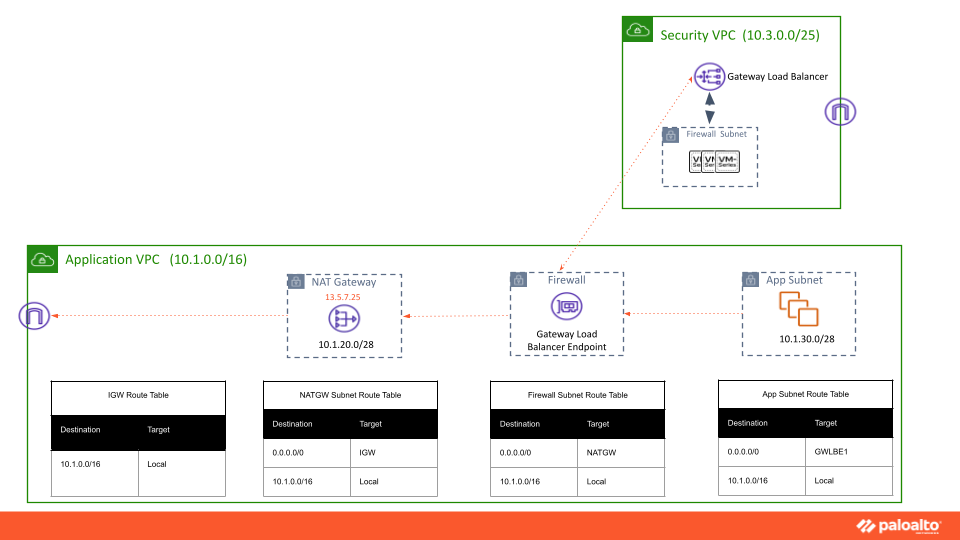
VPC More Specific Routing integration with the VM-Series firewall will help customers gain visibility into ingress and egress traffic and improve the security posture of the Amazon VPC.
To find out more about getting started, visit this AWS marketplace listing. You may also find more information on how VM-Series adds an additional layer of protection to AWS environments on the Live Community AWS resource page.