Cybersecurity researchers have identified Name:Wreck as a set of nine DNS-related vulnerabilities that affect the TCP/IP stacks in four operating systems often used in IoT devices: FreeBSD, IPNet, NetX, and Nucleus NET. Attackers can exploit these vulnerabilities to perform Denial-of-Service attacks, DNS cache poisoning, and remote code execution. As a result, attackers can disrupt normal device activity, take devices offline, redirect them to malicious sites, and gain control of devices. At the time of this writing, there have been no reports of these vulnerabilities being exploited in the wild. Also, note that not all devices using these operating systems are susceptible to the Name:Wreck vulnerabilities.
Name:Wreck Vulnerability Overview
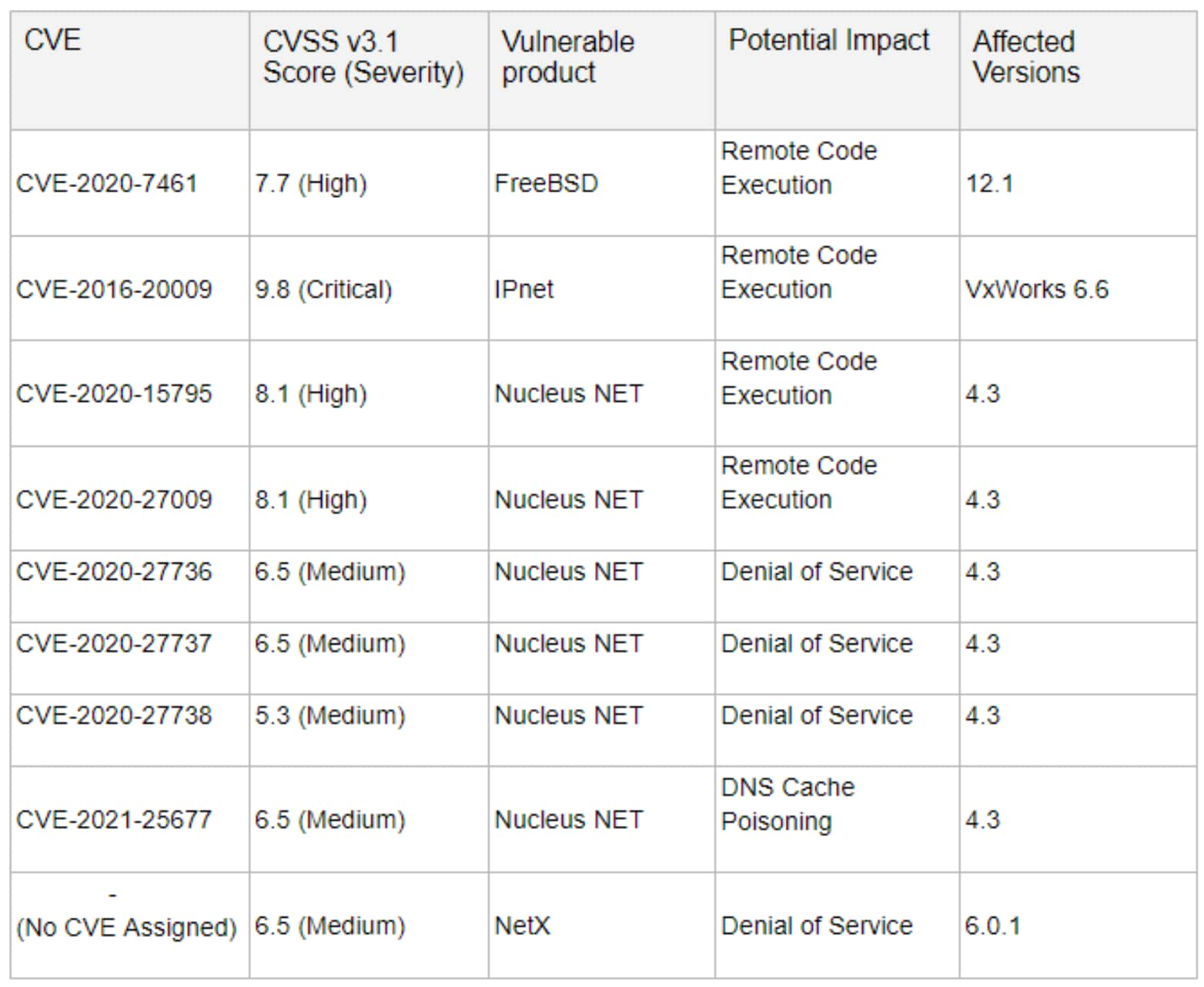
These vulnerabilities are mainly caused by improperly parsing the names in the DNS responses or during domain name record decompression in the aforementioned TCP/IP stacks. Attackers can exploit these nine vulnerabilities by acting as the DNS server for Internet-connected devices and responding to DNS lookups with maliciously crafted responses that disrupt device operations and gain remote access. The attackers can then leverage compromised devices to expose confidential information and sabotage internal and critical devices.
Recent discoveries have shown that open-source TCP/IP stacks are vulnerable to several attacks such as Ripple20 and Amnesia:33, among others. These stacks add useful networking communication capabilities for services such as HTTP Server, Telnet Client and Server, and DHCP Client. FreeBSD, IPNet, NetX, and NucleusNet are used in devices from various vendors across multiple industries like healthcare, industrial control systems, and IT. Because of the basic networking functionality that the TCP/IP stacks provide and the widespread use of these four operating systems across various industries, the nine Name:Wreck vulnerabilities present tempting targets for attack.
Identification, Detection, and Remediation
Devices must first be identified before any vulnerabilities can be detected and alarms raised. Palo Alto Networks IoT Security first identifies devices on the network using its patented three-tier deep-learning engine. Using machine learning, IoT Security leverages anonymized cross-tenant data to create device profiles and behavioral models. It then uses its patented anomaly-detection mechanisms to detect deviations from normal network behavior. Such deviations can include, for example, a sudden appearance of traffic from a new source, an unusually high number of connections, or an inexplicable surge of specific attributes appearing in IoT application payloads. Finally, it generates alerts to notify the administrator of the detected anomalous behavior, explains if they indicate known vulnerabilities, calls out security implications, and suggests actions to take to remediate the threat.
When IoT Security determines the identity of a device, it does so down to its type, profile, and model. After this, IoT Security checks if any known vulnerabilities exist for devices matching these identified attributes. If so, it displays them in the IoT Security portal. As various vendors release advisories for affected devices in their product line, IoT Security monitors them and continuously adds detections based on such advisories. In this way, IoT Security can pinpoint IoT devices in your inventory that are running operating systems vulnerable to the nine CVEs listed above.
In addition to anomaly detection and product advisories, a set of threat prevention IPS signatures detect active exploits of the Name:Wreck vulnerabilities have been added to the latest upcoming content release. If an active exploit is observed, an alert is triggered that informs administrators of the security event. It prompts them to take countermeasures such as quarantining the targeted device or the VLAN where the attack was observed. Wherever applicable, IoT Security can work with other Palo Alto Networks security products such as DNS Security and Threat Prevention to provide more comprehensive protection of your devices.
Take Action
If you find any device exhibiting anomalous behavior, consider taking the following actions:
Different vendors and manufacturers with products using the TCP/IP stacks, as mentioned above, release firmware upgrades or patches that address the issues exposed by these vulnerabilities. Check respective vendor websites for updated firmware versions. If they are available, patch your devices with those releases.
If you cannot patch your devices, take the following steps to minimize risk and keep your network safe:
- Configure IoT and critical devices to ensure they are not accessible from the Internet.
- Configure your network segments to ensure IoT devices are behind firewalls and isolated from guest and business networks.
- Block any anomalous IoT traffic.
- Quarantine victim devices to stop attacks from spreading to other vulnerable devices in the same network segment.
We’re committed to delivering security without compromise. At Palo Alto Networks, we offer best-in-breed cybersecurity solutions today to ensure you can securely advance your organization.
If you have any questions, do not hesitate to contact us at IoTSecurity-info@paloaltonetworks.com.