New capabilities that dramatically improve the end-to-end process of seeing and securing connected medical devices for network security and clinical engineering teams
Palo Alto Networks introduced Medical IoT Security, our IoT security product designed specifically for healthcare providers in 2022. Since then, our product has been recognized as a leader by industry analysts, and has helped our healthcare customers keep their devices and networks more secure.
Palo Alto Networks Medical IoT Security secures millions of devices so healthcare providers across the globe can deliver care to millions of patients every year
We’re committed to helping healthcare organizations stay ahead of the ever evolving cybersecurity threat landscape by protecting their most critical assets. We are excited to announce several new capabilities in our Medical IoT Security product that take connected device security in healthcare to the next level. With these enhancements, our healthcare customers will now benefit from:
- More comprehensive device visibility through improvements in device discovery.
- Easier understanding of device context and risk through intuitive visualization.
- Improved efficiency of vulnerability remediation through risk-based prioritization.
- Unified and simplified security management with Strata Cloud Manager and Cortex XSIAM.
More comprehensive device visibility through improvements in device discovery and identification
Device discovery is the first step to securing critical medical devices: you can’t secure what you can’t see. However, the increasing volume and diversity of connected medical devices and other IoT devices on hospital networks makes it more challenging to accurately identify and profile new and never-before-seen devices.Our Medical IoT Security product already has a robust approach to device discovery, combining device data collected through network traffic logs with our patented three-tier machine learning (ML) model for device identification and classification. We continue to make enhancements to our ML algorithm to discover and classify new and never-before-seen network-connected devices at scale.
However, sometimes device attribute data (such as the vendor, model, firmware and OS) is not readily retrievable from network traffic logs alone since the device isn’t generating sufficient traffic to analyze or the traffic isn’t being sent to the NGFW/ SASE device, especially when firewalls are deployed at the network edge. For instance, in-home patient monitoring device data is processed and analyzed by edge computing resources that are built into medical devices and might not pass through the firewall or SD-WAN device. To address this challenge and to improve the quality and completeness of the device profile data provided by Medical IoT Security, we’re introducing selective polling. Selective polling uses native protocol queries such as WinRM and uPNP to actively retrieve the required device attribute data when this data is not readily available through passive network traffic analysis. Additionally, we have a new built-in third party integration with Microsoft SCCM to import supplemental device data points from the SCCM inventory.
Easier understanding of device context and risk through intuitive visualization
As we continue to enhance the richness of the device data we gather, our customers need a simple and modern visualization in order to easily draw actionable insights. To offer customers greater understanding and control of their connected medical devices, we’ve introduced several updates to our Device Details page:
- At-a-glance understanding of device context and risk: Customers get an new at-a-glance view of 20 key device attributes within the page header by selecting from a list of 100+ attributes. The device attribute list is comprehensive, ranging from basic device information (e.g. vendor, model, IP Address, MAC address, etc.), to device identity information (e.g. model, OS, Firmware version, etc.) and device security information (e.g. risk level, endpoint protection, antivirus installability, data encryption, etc.). For clinical devices, specific security attributes such as FDA Classification, ePHI (electronic Personal Health Information), MDS2 (Manufacturer Disclosure Statements) are available to help assess the clinical risk of a device. In addition, custom attributes like Asset Criticality help clinical engineers to put the security risk of the device within the clinical context.
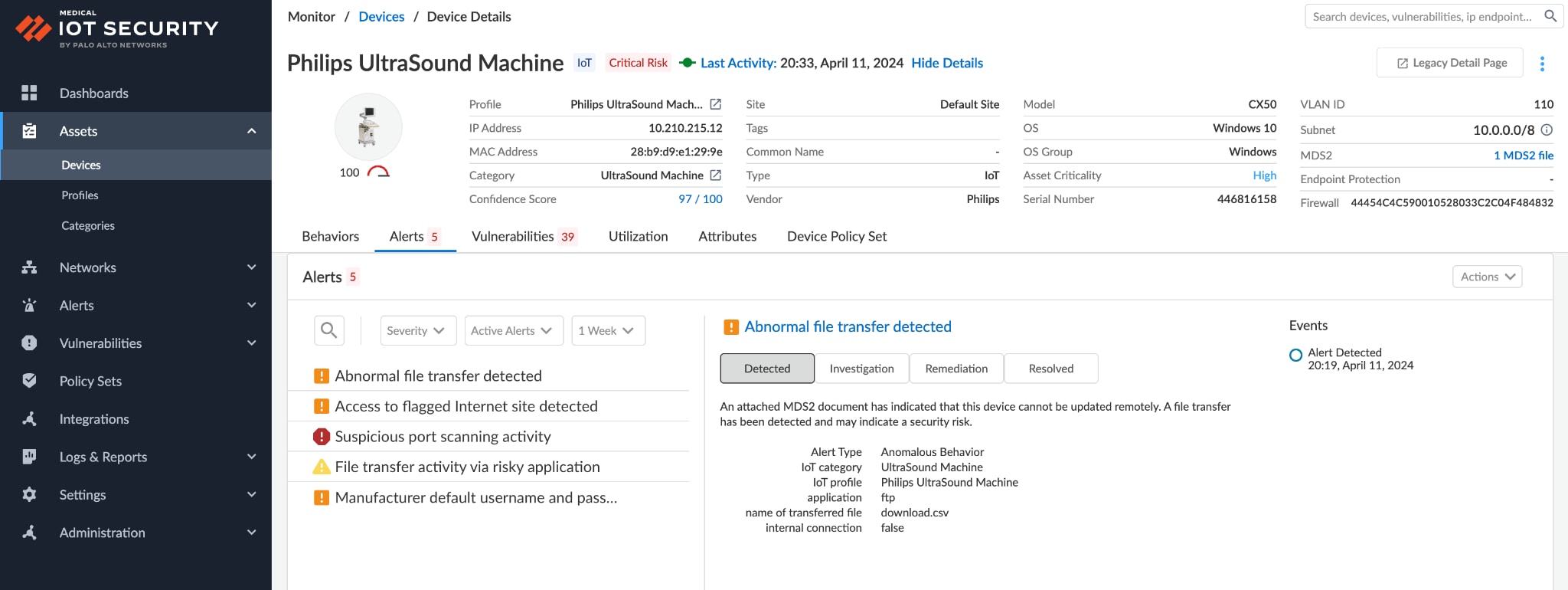
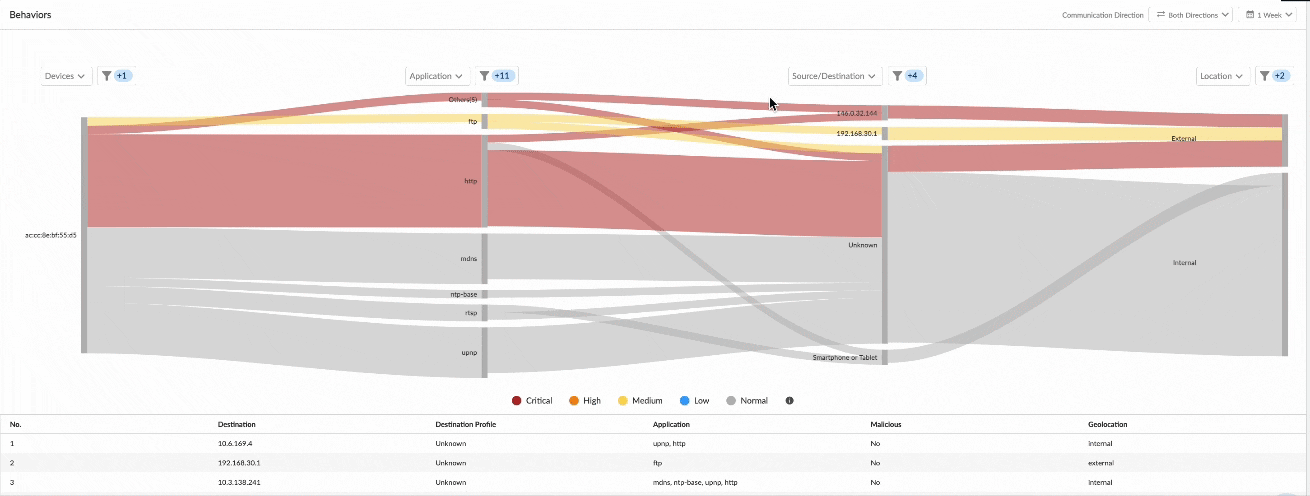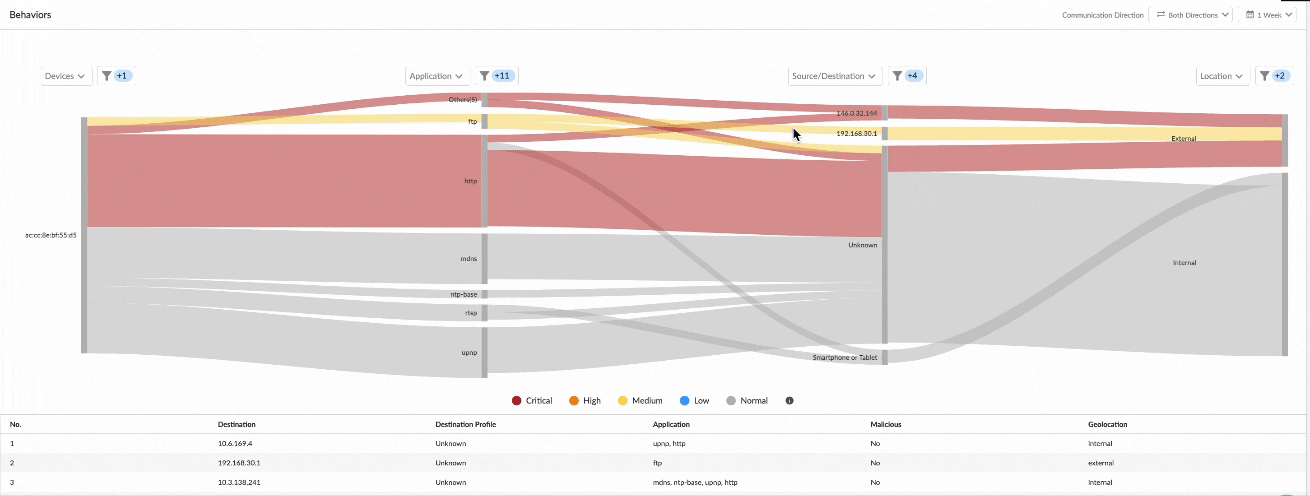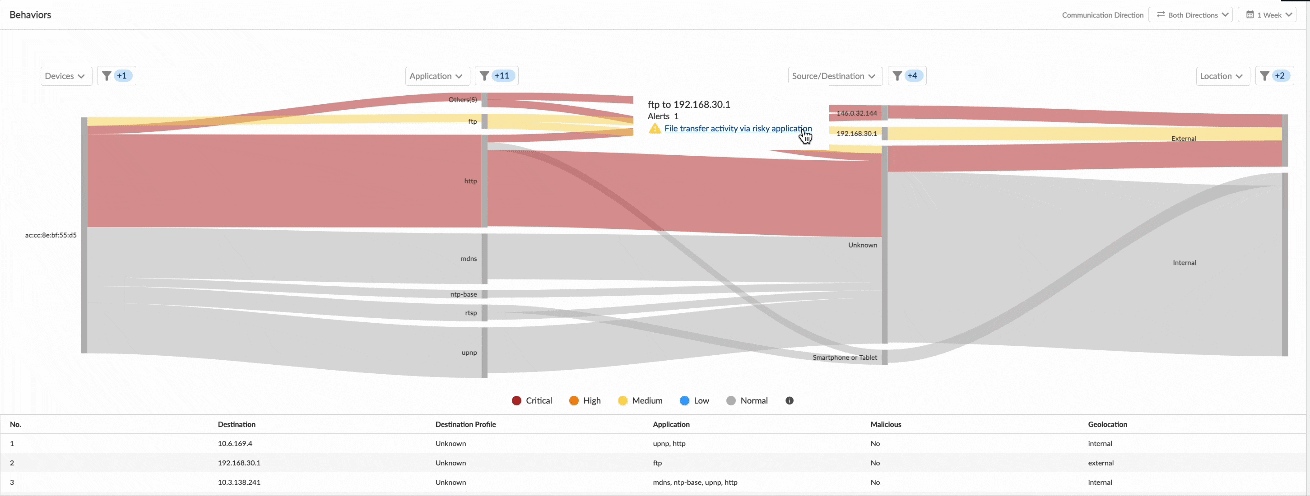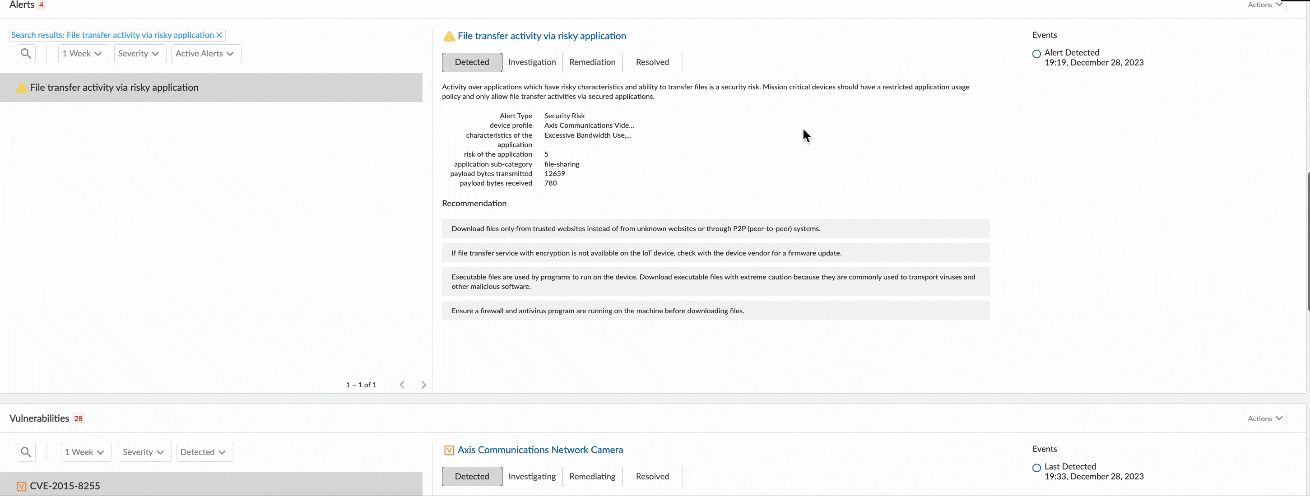
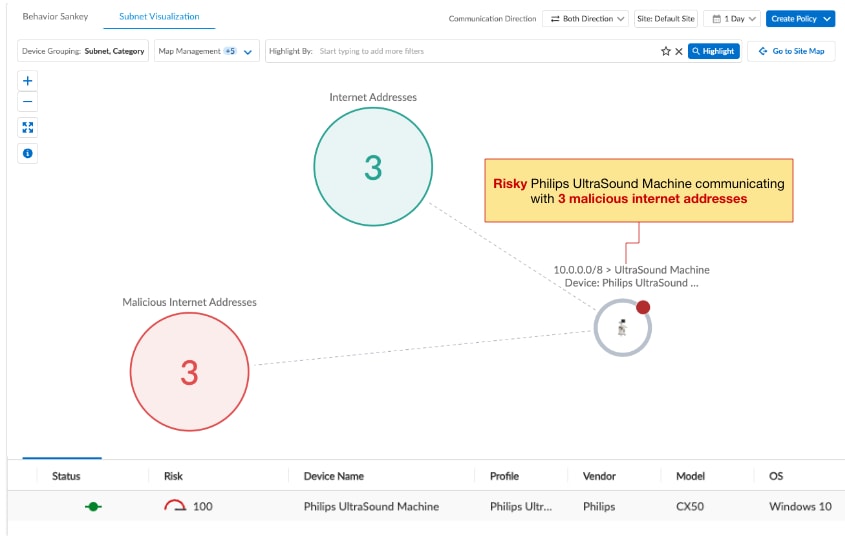
- Easily spot and investigate anomalous/risky device behavior: Flat, unsegmented networks in hospitals make it easy for threats to move laterally from IT devices into critical medical IoT devices and vice versa. Our Unit 42 threat research found that 72% of healthcare VLANs mix IoT and IT assets. We’ve introduced two new visualization tools that will help network security teams more easily spot and investigate risky device communications and determine what segmenting controls can be applied to mitigate that risk. Our dynamic Sankey chart in the device details page illustrates device connections by application, source/destination and traffic direction so it is easy to spot risky communications and investigate anomalous traffic. The device behavior tab in the Device Details page also provides a subnet visualization of the device so that network security teams can locate which segment the medical device is in and other systems and subnets the device is communicating with. The device subnet visualization enables network security teams to more easily visualize devices within each segment to more accurately determine (and control) the blast radius of exploits.
And all of these capabilities work for both network security and biomedical/clinical engineering teams. Customers can choose to drill down into device information tailored to their specific needs. Network Security administrators can get a detailed view of alerts and vulnerabilities associated with a device and take remediative actions based on the recommendations provided. Biomedical/clinical engineers can get device utilization insights like hours of operation in order to better plan preventative maintenance or vulnerability scans.
Improved efficiency of vulnerability remediation through risk-based prioritization
Connected medical devices are critical to hospital operations and any disruption could lead to loss of revenue and, worse still, impact patient outcomes. When these devices have vulnerabilities (which is often the case), their high operational uptime requirement influences which vulnerabilities to patch and when to patch them to avoid any disruption to care delivery.
To help both security and clinical teams reduce operational risk by focusing on what matters the most, we are pleased to introduce a risk-based vulnerability priority classification feature within Medical IoT Security. To identify device vulnerabilities that pose the greatest risk, Medical IoT Security uses a multifactor risk assessment that goes beyond basic CVSS, evaluating threat likelihood indicators and the impact to a customer’s organization should their clinical assets be compromised.
Additionally, our Medical IoT security subscription offers enhanced threat protection with virtual patching capabilities. In some cases, patches may not be readily available for CVE remediation or it may be difficult for asset owners to perform patching, especially in critical environments like hospital floors, leaving critical assets susceptible to exploits. Threat Prevention profiles can be incorporated into Device-ID based Zero Trust policies as a compensating control. This helps prevent cyberattacks from exploiting known vulnerabilities while asset owners await maintenance windows for potential patching or even extending lifespan of EOL devices. This allows clinical and security teams to maintain the stability and reliability of critical systems while delivering patient care.
Unified and simplified security management with Strata Cloud Manager and Cortex XSIAM
Finally, a comprehensive medical device security solution must “close the loop” on security by providing both visibility and protection of all network connected endpoints within a single platform. With the proliferation of connected medical devices and other IoT/OT devices in hospital networks, the approach to securing them needs to evolve from a niche (visibility & alert only) approach to a more mainstream, network-based, comprehensive platform approach to securing all connected devices.
Palo Alto Networks Medical IoT Security was already ahead of the curve here, not only do we provide ML-based visibility into unmanaged connected devices, but also threat prevention and security policy enforcement to protect devices from known and unknown threats, all within a single integrated platform. We’re taking the benefits of our platform approach to the next level with the following new capabilities:
- Integration with Strata Cloud Manager: Palo Alto Networks recently announced Strata Cloud Manager (SCM), an AI-powered, Zero Trust management solution. It transforms network security by strengthening security and preventing network disruptions consistently across all enforcement points. SCM includes a dedicated Medical IoT Security dashboard, granting quick access to critical device security parameters, such as medical device inventory, risk and alerts. With SCM, security teams reap the operational benefits of comprehensive configuration and security policy management across all form factors, including SASE, hardware and software firewalls, as well as security services to ensure consistency and reduce operational overhead.
- Integration with Cortex XSIAM: Cortex XSIAM is our AI-driven platform that converges SOC capabilities, leverages AI for accurate threat protection and applies an automation-first approach to security operations. Customers can now get visibility into connected medical devices and all other IoT/OT devices within the Cortex XSIAM Command Center. This integration enables customers to streamline SOC workflows and reap the benefits of the platform by unifying security operations management across all connected endpoints within a single, seamless interface.
To learn more about how your healthcare organization can benefit from these new capabilities, attend one of our upcoming Hands-on-workshops and try out our product for free by registering here to get a 30-day trial of our Medical IoT Security product.