In today’s threat landscape, the exponential growth of vulnerabilities makes it extremely challenging for network and security teams to prioritize remediation efforts and deliver maximum business value. Public data reveals that close to 29 thousand Common Vulnerabilities and Exposures (CVEs) were disclosed just in 2023, representing an increase of 15% compared to the number of CVEs in the previous year.
For critical infrastructure environments such as industrial and healthcare deployments, maintaining mission-critical systems uptime and ensuring patient care and safety are vital for OT, biomedical and network security teams. The increasing number of CVEs impacting IoT, Operational Technology (OT) and Medical IoT (MIoT) assets puts relentless pressure on these teams and limits their ability to remediate risks that are critical for the continued operations of their business.
Risk-Based Vulnerability Management
Many organizations have been using the Common Vulnerability Scoring System (CVSS) - an industry standard for assessing the characteristics and severity of cybersecurity vulnerabilities - to prioritize vulnerability remediation.
Since its introduction in 2005, CVSS has gone through three major revisions, incorporating metrics and scoring criteria to more accurately reflect the severity of vulnerabilities. Through these revisions, the standard recognized that considering the context of a specific vulnerability plays an important role in assessing its risk. While Temporal and Environmental group metrics were intended to address this issue, they were “optional”, as they reflect characteristics that change over time and are specific to individual organizations, adding overhead for organizations to manually assess them and therefore consuming a lot of time and resources. As a result, CVSS adoption never really grew beyond the use of the Base metrics.
The challenge with relying solely on CVSS Base scores for prioritization is that organizations may find themselves not focusing on what really matters most for them. A given CVE may have a high CVSS Base score, but what if the likelihood of an attacker exploiting the vulnerability is very low or if it only affects less critical assets in your organization? For example, a compromise in a PLC running a critical industrial control system is likely to cause higher business impact to the organization than one in an unimportant test lab.
Particularly for critical OT and Healthcare environments, where system uptime and patient safety are vital metrics, utilizing a better vulnerability prioritization approach is even more important. Patching requires resources and coordination across different teams, sometimes involving external contractors/ OEMs, to prioritize and test the patches and plan for maintenance windows. In many cases, maintenance windows are hard to secure since they impact critical operations and may require devices to be down for extended periods of time. Committing all these efforts while prioritizing lower priority vulnerabilities not only leads to suboptimal allocation of resources, but may also leave your most critical infrastructure exposed, potentially causing significant operational, financial and compliance related losses.
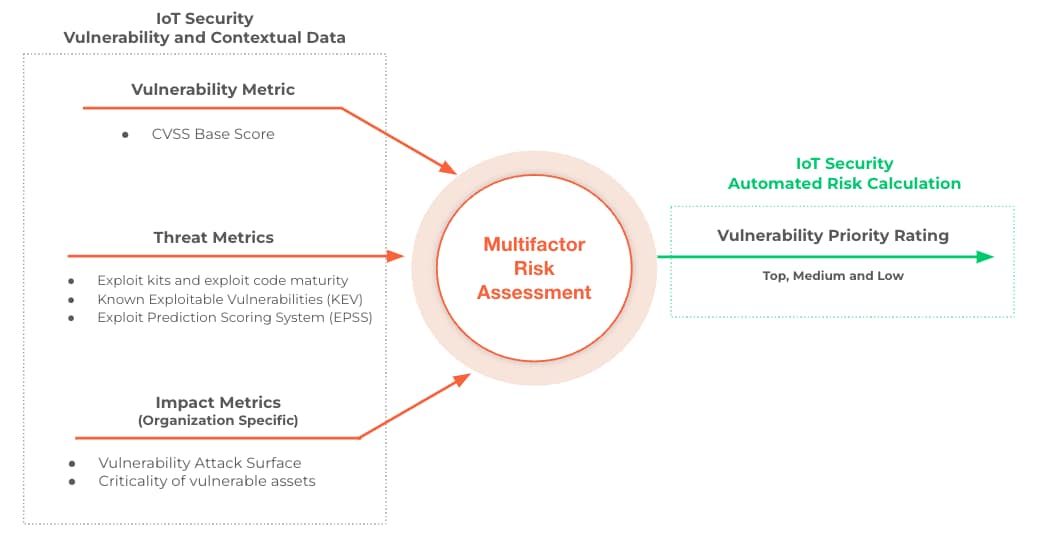
We believe a more effective approach to vulnerability prioritization should assess the risk posed by vulnerabilities , considering not only their severity level but also the current threat landscape and the context of the vulnerable assets. This contextual approach should be flexible to accommodate factors that are relevant and unique to the organization’s environment, similar to those defined under Temporal/Threat and Environmental metric groups and provide prioritization insights in an automated fashion for a faster and impactful vulnerability response. This is where our risk-based vulnerability management comes into play.
Introducing Our Approach to Risk-Based Vulnerability Management
We’re excited to announce our newest risk-based vulnerability management capability within our Enterprise IoT/ Industrial OT/Medical IoT Security solutions to address the vulnerability prioritization challenges faced by many organizations overwhelmed by exponential growth of vulnerabilities.
Our solution brings together vulnerability metrics along with in-depth threat and asset context to provide a risk assessment of each vulnerability while automating calculations to reduce operational overhead and facilitate vulnerability response at scale. Vulnerabilities are classified by their risk level using a priority rating that can be used to identify or filter the actual risky CVEs in the customer environment.
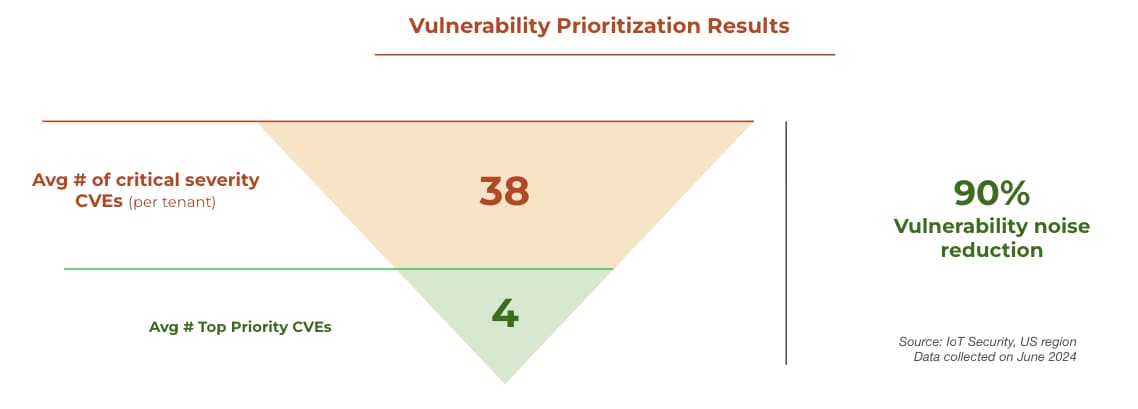
In fact, by applying our risk-based vulnerability prioritization across our US customer base, our methodology was able to reduce the vulnerability noise by 90%. On average, only 10% of the critical severity CVEs (CVSS score) were classified as top priority, helping distinguish the truly risky CVEs from other CVEs that are unlikely to pose significant risks.
Not only can our prioritization methodology help reduce the load of CVEs, it can also call out CVEs that, despite having lower CVSS Base scores, are potentially more risky than the ones with higher scores and that would have been ignored if CVSS Base score was the only prioritization criteria being used.
To learn more about the technical details behind our methodology, check out our live community blog.
Wrapping It All Up
The risk-based vulnerability prioritization is one of the many innovations in our IoT/OT/Medical IoT Security solutions that can help secure all your devices while significantly optimizing your operations. These solutions offer a comprehensive Zero-Trust architecture that allows our customers to quickly discover every device, understand their attack surface, prioritize risk mitigation efforts and secure hard-to-patch vulnerable IoT, OT and Medical IoT devices with context-rich security policy recommendations and vulnerability threat signatures to stop exploit attempts.
Want to learn more about what our IoT/OT Security solutions can do for you? Check out the following links:
Enterprise IoT Security Introduction | Upcoming Hands on workshop
Medical IoT Security – Introduction | Upcoming Hands on workshop
Industrial OT Security – Introduction | Upcoming Hands on workshop
We want to help keep all your devices secure. Start a free trial with us here!