Prisma Cloud can evaluate the security posture of your cloud estate. This is done by comparing your cloud assets to policy and alerting on deviations.
The cloud operations team has already tuned the environment to meet security requirements and conform to policy. It’s been quiet for several weeks, but today, Prisma Cloud is generating alerts and policy violations.
To determine why, the cloud operations team might want to check the Prisma Cloud audit logs to see if anything’s changed. But the team doesn’t want to log into yet another console to get more information about their AWS environment. Mature cloud security solutions should be able eliminate friction between cloud practitioners and cloud operations teams.
If your organization is using AWS CloudTrail Lake for auditing, you can use Prisma Cloud to enrich AWS CloudTrail data by creating a custom integration and using native functionality within Prisma Cloud to send events to AWS.
AWS CloudTrail Lake is a managed data lake in AWS used for storing and analyzing AWS activity for audit and security purposes. AWS CloudTrail Lake allows you to aggregate and immutably store logs for search and analysis — and it offers the ability to import events from non-AWS sources. By setting up a custom integration, cloud operations teams can use their AWS CloudTrail lake queries to get information from Prisma Cloud.
This post provides an overview of the process on how to deploy a custom integration and ingest Prisma Cloud audit events in AWS CloudTrail Lake.
The Solution
At a high level, the integration will look like this:
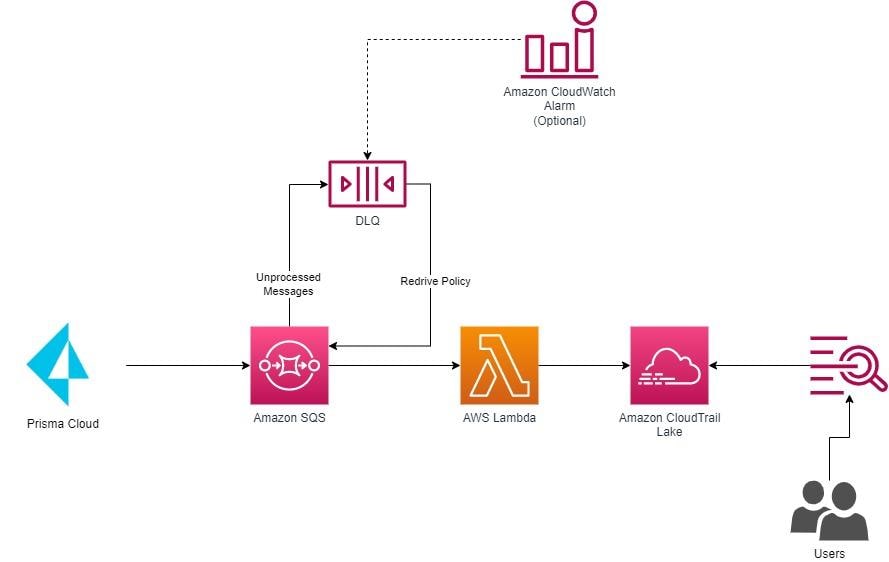
Prisma Cloud will integrate with Amazon SQS and emit audit event messages. Amazon SQS will trigger an AWS Lambda function to format and send the messages to AWS CloudTrail Lake using a custom integration. The solution will use a built-in capability of AWS CloudTrail Lake to validate the integrity of the message before ingestion. If messages can’t be processed and ingested, they’ll be sent to a dead-letter queue for reprocessing and (optionally) an alert will be generated in CloudWatch alerts.
Note that all the assets in the integration will reside in your AWS account, giving you full control to administer and modify them as required.
The Implementation
Prerequisites
Before proceeding, obtain the ARN of the IAM role your organization used to onboard the AWS account into Prisma Cloud:
- Log in to the Prisma Cloud console.
- Navigate to Settings, then Cloud Accounts.
- Click the Edit icon on the AWS account that will be used for the integration.
- Copy the Role ARN.
Deploy the AWS CloudFormation Template
An AWS CloudFormation template will be used to deploy and configure the resources described. To deploy the CloudFormation, follow these steps:
Step 1: Log in to your target AWS Account. This will be where AWS CloudTrail Lake and the SQS integration are configured.
Step 2: Click the quick create link. This defaults to region “us-east-1” - change to a different region if desired.
Step 3: Update the required parameters, described below:
- ExternalId: A unique string to provide an added layer of protection for inserting events into the CloudTrail events data store. (Default: <blank>)
- PrismaCloudCspmRoleArn: Role used to onboard the AWS account into Prisma Cloud. See “Prerequisites” above.
- RetentionPeriod: Days to retain data in the CloudTrail events data store. (Default: 2557 days / 7 years)
Step 4: Default values have been generated for the following parameters, but feel free to update them if desired:
- PrismaCloudAuditsEventsDataStoreName: Name of the CloudTrail events data store to be created for this integration. (Default: “PrismaCloudAuditsEventsDataStore”)
- PrismaCloudCloudTrailLakeIntegrationChannelName: Name of the CloudTrail custom integration channel that will receive events for the data store. (Default: “PrismaCloudCustomIntegration”)
- PrismaCloudIntegrationDeadLetterQueue: Queue that will hold messages that have failed to process. (Default: “prisma-cloud-audit-events-dlq”)
- PrismaCloudIntegrationQueueName: Name of the SQS Queue for the Prisma Cloud audits events integration. (Default: “prisma-cloud-audit-events-queue”)
- DeployCloudWatchAlarm: If “yes”, a CloudWatch alert will be created to monitor the depth of the PrismaCloudIntegrationDeadLetterQueue. (Default: “no”)
Step 5: Check the “I acknowledge that AWS CloudFormation might create IAM resources” at the bottom.
Step 6: Click “Create stack”
Step 7: When stack creation completes, check the output tabs and note the PrismaCloudIntegrationQueueURL value, required for the next step.
Configuring the Prisma Cloud / Amazon SQS Integration
After deploying the CloudFormation, the next steps are to create the Amazon SQS integration within Prisma Cloud and configure audit logs to send to it.
Create a New SQS Integration
Prisma Cloud provides a native integration to Amazon SQS. Detailed instructions can be found in our documentation, and we give a brief overview of what’s required here:
Step 1: The CloudFormation deployed in the previous step created the Amazon SQS queue required for the integration, so if you’re following along with the detailed instructions in our documentation, you can start at “Step 4 >> Set up Amazon SQS integration in Prisma Cloud.”
Step 2: Log in to Prisma Cloud.
Step 3: Select Settings, then Integrations.
Step 4: Click Add Integration and then select Amazon SQS.
Step 5: Enter the following information:
- Name: PrismaCloudAuditLogsIntegration
- Description: Integration so send Prisma Cloud Audit Logs to Amazon SQS
- Queue URL: <This is the PrismaCloudIntegrationQueueURL output from the CloudFormation above>
Step 6: Click Next.
Step 7: Test the integration and ensure it can connect.
Step 8: Save the integration.
Configure Prisma Cloud to Send Audit Logs to Integration
To configure Prisma Cloud to send audit logs to the newly created SQS integration:
- Log into Prisma Cloud as an administrator.
- Navigate to Settings, then select Enterprise Settings.
- Enable “Send Audit Logs to integration”.
- Select the SQS integration created above.
- Click Save Settings in the top right corner.
Testing and Validation
After deploying and configuring the solution, new audit events within Prisma Cloud should start populating inside of AWS CloudTrail Lake. To validate:
- Ensure that audit events happened inside Prisma Cloud after the solution was deployed: Log in to the Prisma Cloud console, click on Settings, then click on Audit Logs and ensure there are log messages after the integration configuration was completed.
- Ensure that the CloudTrail Lake integration status is “Active”. When initially configured, it will be set to “Incomplete” and remain as such until events are logged for the integration. To validate, log in to the AWS console, navigate to CloudTrail, expand Lake, and select Integrations. Find the integration created by this solution — named “PrismaCloudCustomIntegration” by default — and review the status field.
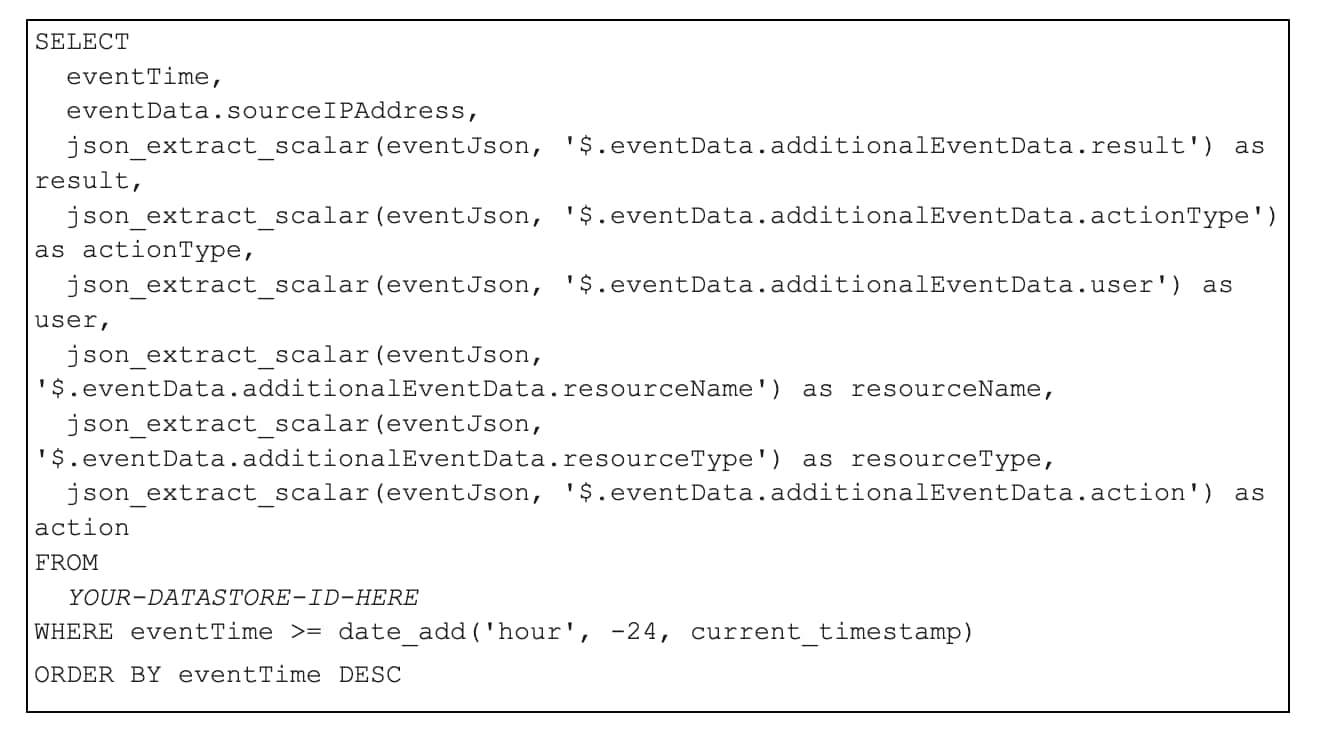
Once you have confirmed audit data is flowing into the CloudTrail event data store, you can begin to query it. Below is a sample query (be sure to replace the data store ID with the appropriate value):
Considerations
There are several considerations to be aware of when deploying this solution:
- There are several billable resources created by the CloudFormation solution provided above. This includes SQS, Lambda, CloudWatch Logs and Alarms (if used), and the CloudTrail data store. Refer to the following AWS pricing guides to get a better understanding of how the solution may impact your AWS bill:
Amazon SQS | AWS Lambda | Amazon CloudWatch | AWS CloudTrail
- The solution provided will not import existing audit events from Prisma Cloud into AWS CloudTrail Lake. If existing audit events are desired, you can load them using the following script: import-audit-events.sh. This script should be run as a user — via CloudShell or a properly authenticated AWS CLI — with the appropriate permission to write to the integration Amazon SQS queue.
- AWS puts a deleted event store in “pending deletion” for seven days until it is permanently removed. If you delete the deployed CloudFormation stack and attempt to redeploy, be sure to pick a different name for your data store.
Next Steps
Integrating Prisma Cloud and AWS CloudTrail Lake enables organizations to maintain a consistent view of their security posture, significantly improving their ability to detect and address security issues promptly on AWS. By following the steps outlined in this blog post, you can achieve this integration and enjoy the benefits of a unified security management solution.
We encourage you to continue exploring the capabilities of Prisma Cloud and AWS CloudTrail Lake, and consider implementing this integration to enhance your organization's security posture on AWS.
If you haven’t tried Prisma Cloud, we invite you to take it for a test drive. Discover how Prisma Cloud can evaluate the security posture of your cloud estate with a free 30-day trial.