Shadow IT and unmanaged cloud assets pose significant security risks for organizations. Prisma Cloud, in recent months, has addressed this visibility gap left by legacy CSPM technologies — identifying the unknown internet attack surface through a technology we call cloud discovery and exposure management, or CDEM.
In this blog post, we look at the background of the CDEM and what the new network visibility means.
What Is CDEM?
Cloud discovery and exposure management (CDEM) is a security technology that identifies, evaluates and helps mitigate unknown cloud assets within an organization's digital ecosystem. It expands the capabilities of traditional CSPM by not only managing known and monitored assets but also by uncovering and integrating shadow, or unknown, assets into the security fold. CDEM provides a unique, attacker-like perspective of an organization’s cloud infrastructure.
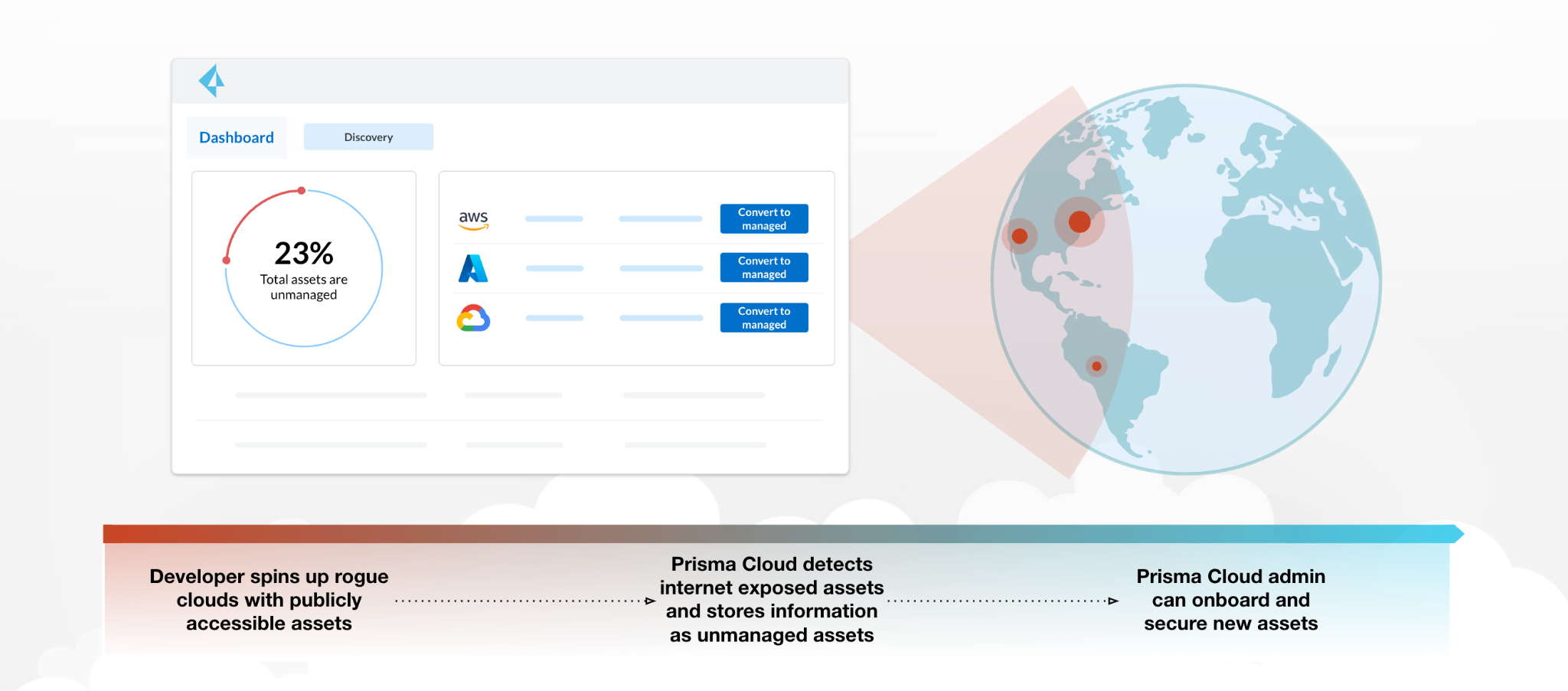
What Is a Shadow or Unknown Cloud Asset?
Shadow or unknown cloud assets are elements of an organization's digital infrastructure that aren’t actively managed or cataloged by its IT department. These can include servers, storage devices or entire applications set up without the explicit approval or knowledge of IT personnel, often in response to urgent business needs. Such assets present significant security risks, as their unmonitored states make them ideal targets for malicious activities.
Why Do I Need CDEM If I'm Using CSPM?
CSPM offers good visibility into secured assets but can only see assets in clouds it’s connected to. CDEM, similar to attack surface management (ASM) tools, can identify IT assets exposed to the internet, many in unconnected clouds the organization is unaware of.
Some CSPM technologies offer agentless network visibility, collecting and illustrating flow logs from cloud providers. This helps organizations understand which assets communicate with others and the internet. Without CDEM context, CSPM tools will flag network connections to unsanctioned assets as unknown or untrusted sources. This is because the CSPM tools don’t know which unsanctioned, internet-facing assets belong to the organization.
Illuminating Connections to Shadow Assets
For years, Prisma Cloud has been ingesting network flow logs across AWS, Azure and GCP clouds to help organizations understand their network-based application dependencies and communications to and from malicious internet sources. The recent integration of CDEM takes this capacity to the next level.
Through CDEM technology, Prisma Cloud correlates network flow data with internet attack surface scans, identifying transactions between sanctioned and unsanctioned cloud assets. In other words, the platform contextualizes findings across CSPM and external attack surface scans to identify, evaluate and help mitigate risks associated with both known and unknown cloud assets.
Security teams can understand network-based application dependencies to potentially unknown assets. Additionally, as internet-exposed risks emerge, security teams get insights into potential lateral movement points. Visibility into these relationships can also help teams prioritize onboarding and remediation steps, as internet exposure attack surfaces can impact the managed environment.
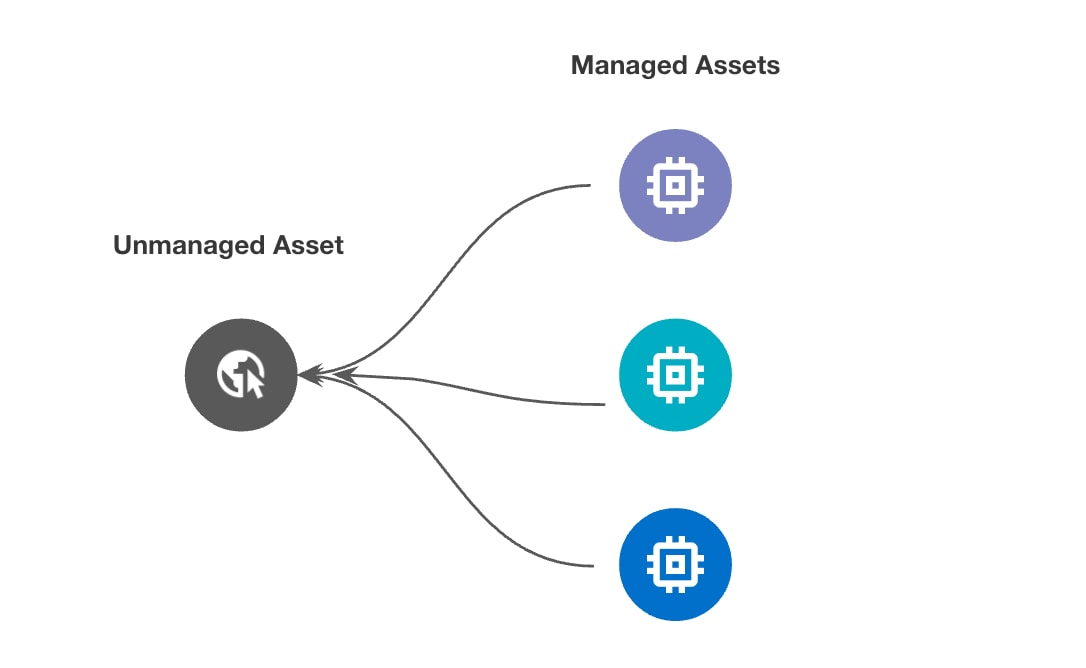
How Does CDEM Work?
The operational framework of CDEM involves several key processes that ensure comprehensive management and protection of cloud assets. Initially, CDEM tools scan the entire cloud environment — including parts not covered by existing CSPM solutions. This is typically achieved by scanning the IPv4 space to identify all internet-facing assets associated with the organization.
Discovery Phase
The discovery phase of CDEM involves an extensive scan of the cloud environment using machine learning algorithms to identify all assets exposed to the internet. These assets include everything from virtual machines and databases to third-party services and APIs. Palo Alto Networks uses data from various sources such as IP registration databases, DNS records and certificate details to accurately attribute each discovered asset to the organization.
Risk Assessment
Once these assets are identified, Prisma Cloud assesses them for vulnerabilities and exposure risks. This assessment is not just limited to identifying insecure configurations or outdated systems but also includes analyzing the network flows and relationships between known and unknown assets. This comprehensive evaluation helps in understanding the potential pathways an attacker could exploit.
Integration and Management
After identification and evaluation, the next step involves integrating these previously unknown assets into the organization's managed cloud environment. Prisma Cloud provides workflows that help transition these assets from unmanaged to managed status, bringing them under the monitoring by CSPM. This transition includes setting up proper governance, compliance checks and continuous monitoring to ensure they remain secure.
Continuous Monitoring and Remediation
Finally, CDEM ensures that all cloud assets, once brought into the managed environment, are continuously monitored for new risks and vulnerabilities. The system automatically prioritizes risks based on their potential impact, guiding security teams on which issues to address first. Additionally, it provides actionable insights for remediation, reducing the time and resources required to secure the cloud environment.
Learn More
With the mission of helping organizations secure their applications from code to cloud, Prisma Cloud offers visibility into internal risks and external attack surfaces. Additionally, the platform correlates risk signals, helping security teams connect the dots across their cloud-native estate.
To learn more about how internet-exposed assets are discovered, what processes are used to identify and prioritize risks, and how to remediate the risk created by rogue, unmanaged assets, download our white paper Cloud Discovery and Exposure Management. And if you’d like to see CDEM technology in action, book a demo with one of our experts.