The Bridgecrew team is excited to announce the release of Checkov 2.0, further enhancing one of the most popular open source IaC security scanners available. We’ve completely rebuilt the back end as a graph-based infrastructure as code (IaC) scanner, to help identify cloud misconfigurations in environments with complex dependencies across resources and modules.
This release also includes nearly 250 additional policies, ready to use out-of-the-box to improve compliance benchmark coverage and Dockerfile misconfiguration scanning capabilities.
Checkov is used by developers to scan IaC templates, such as Terraform files, to prevent misconfigurations that lead to security violations in cloud infrastructure. Since its launch in late 2019, Checkov has been downloaded over 1.2 million times! This is a testament to the importance of securing cloud infrastructure prior to runtime, and the crucial part developers play in doing so.
Why Is IaC Security Important?
IaC is the process of using code to define the architecture of cloud infrastructure for applications. Instead of clicking through a cloud provider’s UI or multiple disorganized CLI commands, IaC provides a code-based way to declare what infrastructure should look like. Tools like Terraform and CloudFormation then take that code and provision the infrastructure automatically.
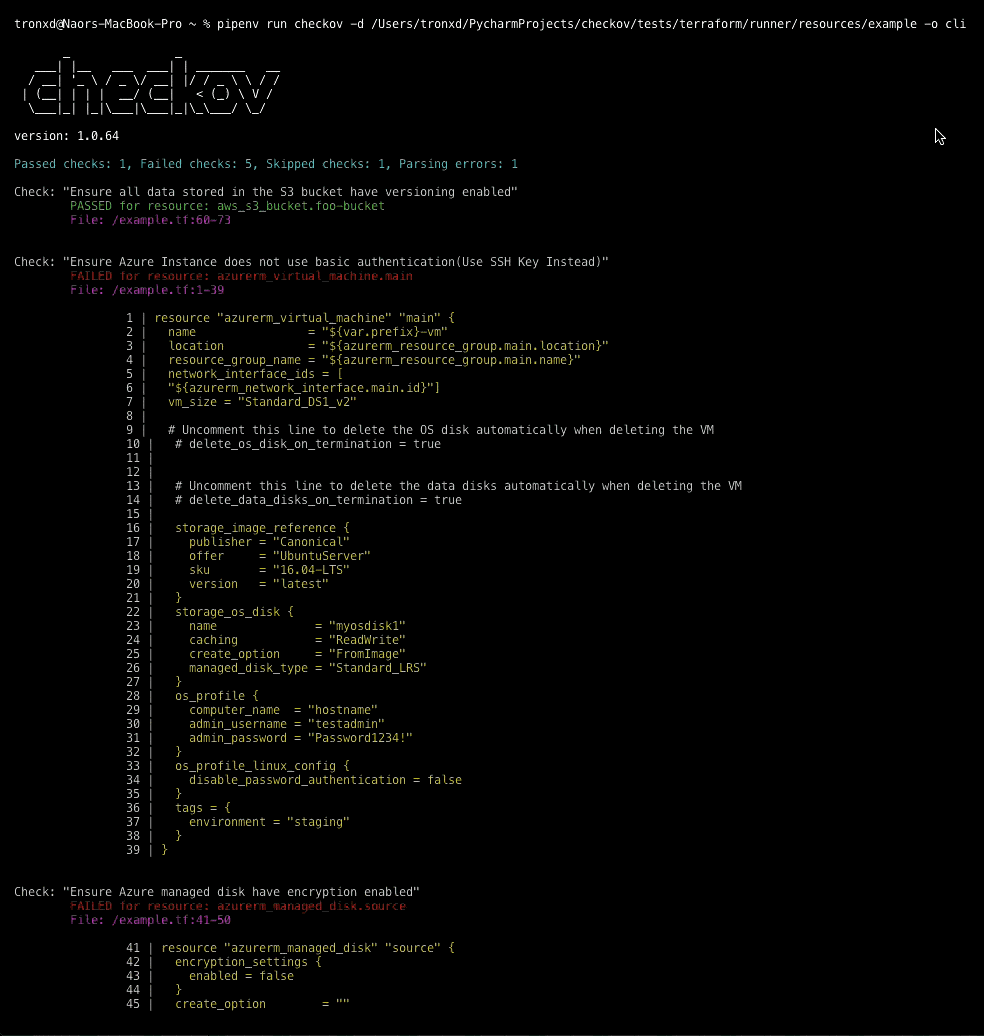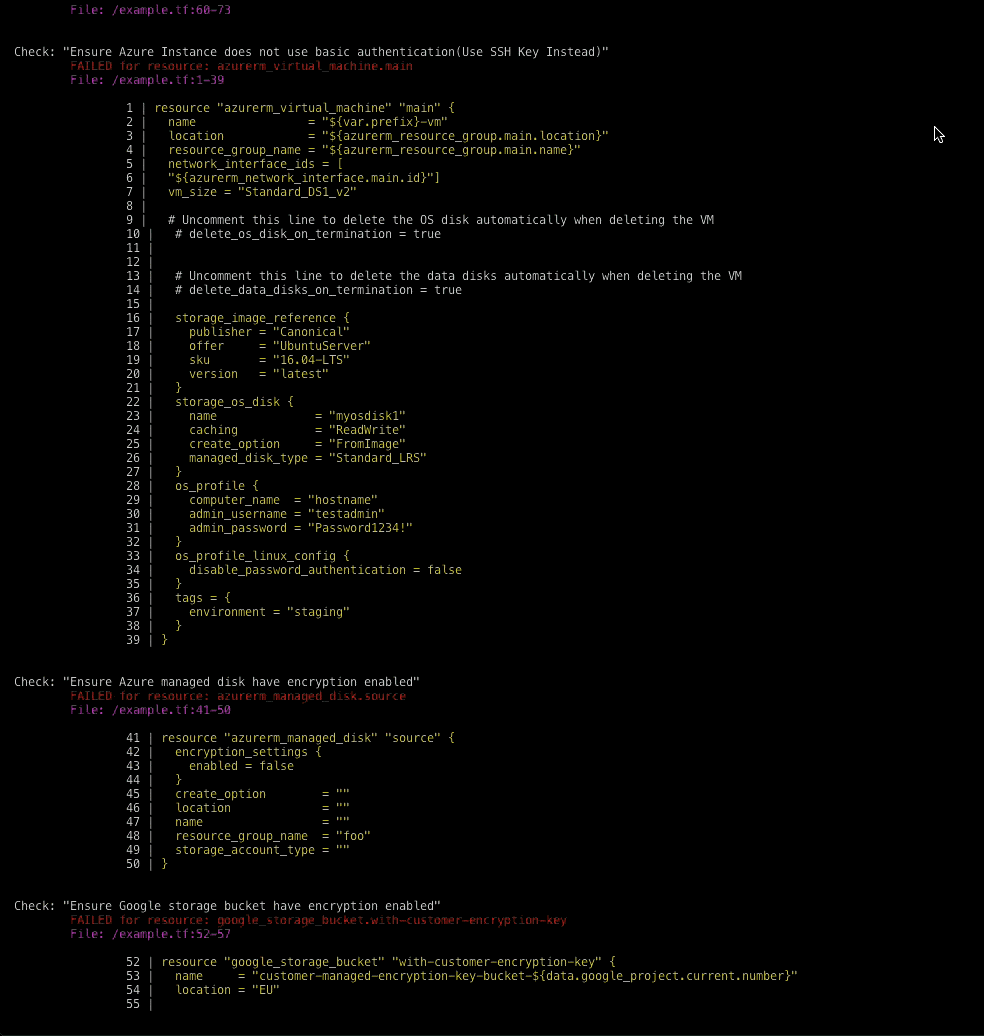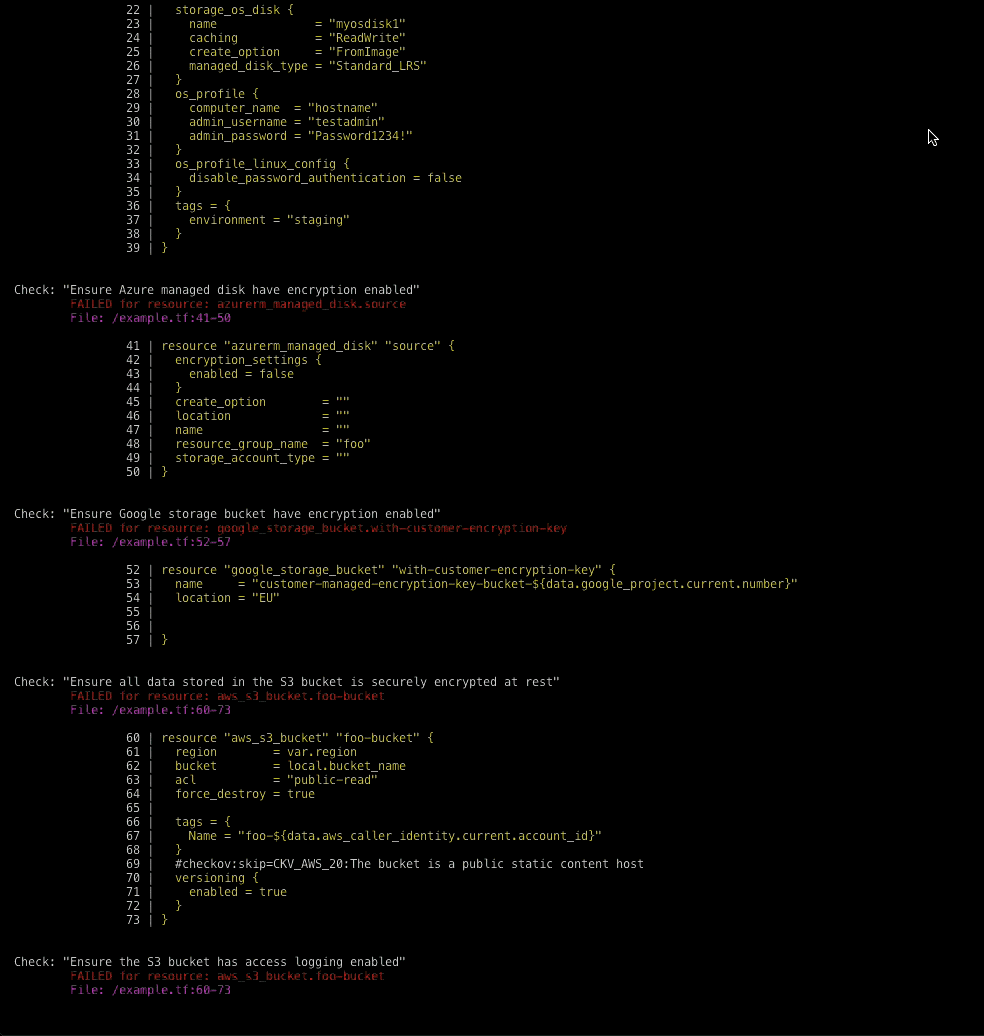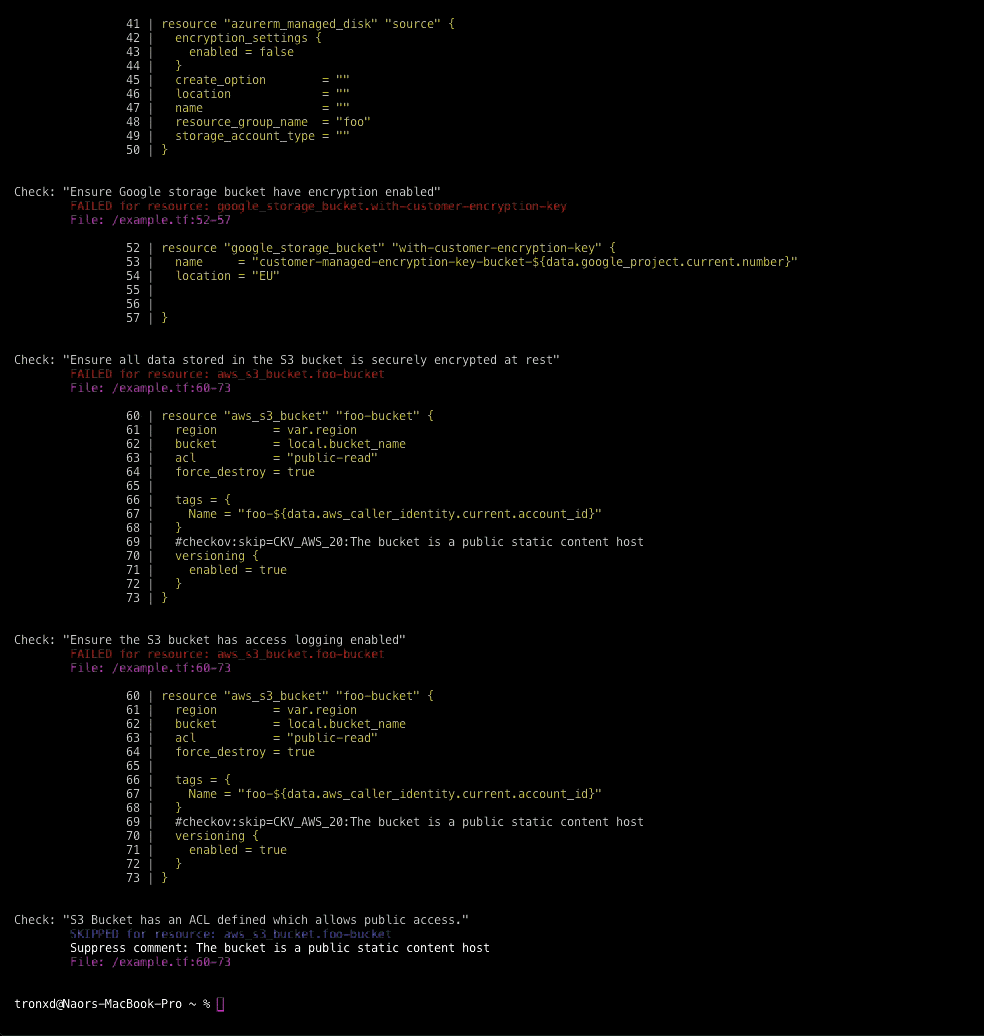
IaC can also be checked into repositories, making it easier to audit who made changes, roll back any breaking changes and generally move faster for tasks like updating and duplicating environments. The problem is that many misconfigurations we see in cloud environments, like open buckets in AWS Simple Storage Service (Amazon S3), also show up in IaC templates.
This is where open source IaC security steps in. Developers leverage scanners like Checkov to find and fix bugs during the development process, and catch those misconfigurations before they ever hit production.
Understanding Complex Dependencies in Cloud Computing
By design, IaC templates are not as straightforward as reading a book line by line. Due to their declarative nature, things can be provisioned out of order, and relationships are not always 1:1.
For example, in an IaC template, a virtual private cloud (VPC) can be defined after an Amazon Elastic Compute Cloud (EC2) instance, but in build time, that VPC must be provisioned first. Additionally, knowing that the VPC is just a dev or test environment changes the security requirements of the EC2 instance attached.
Standard static analysis can’t understand that relationship, so you’d typically have to wait for runtime to know the full extent of your exposure.
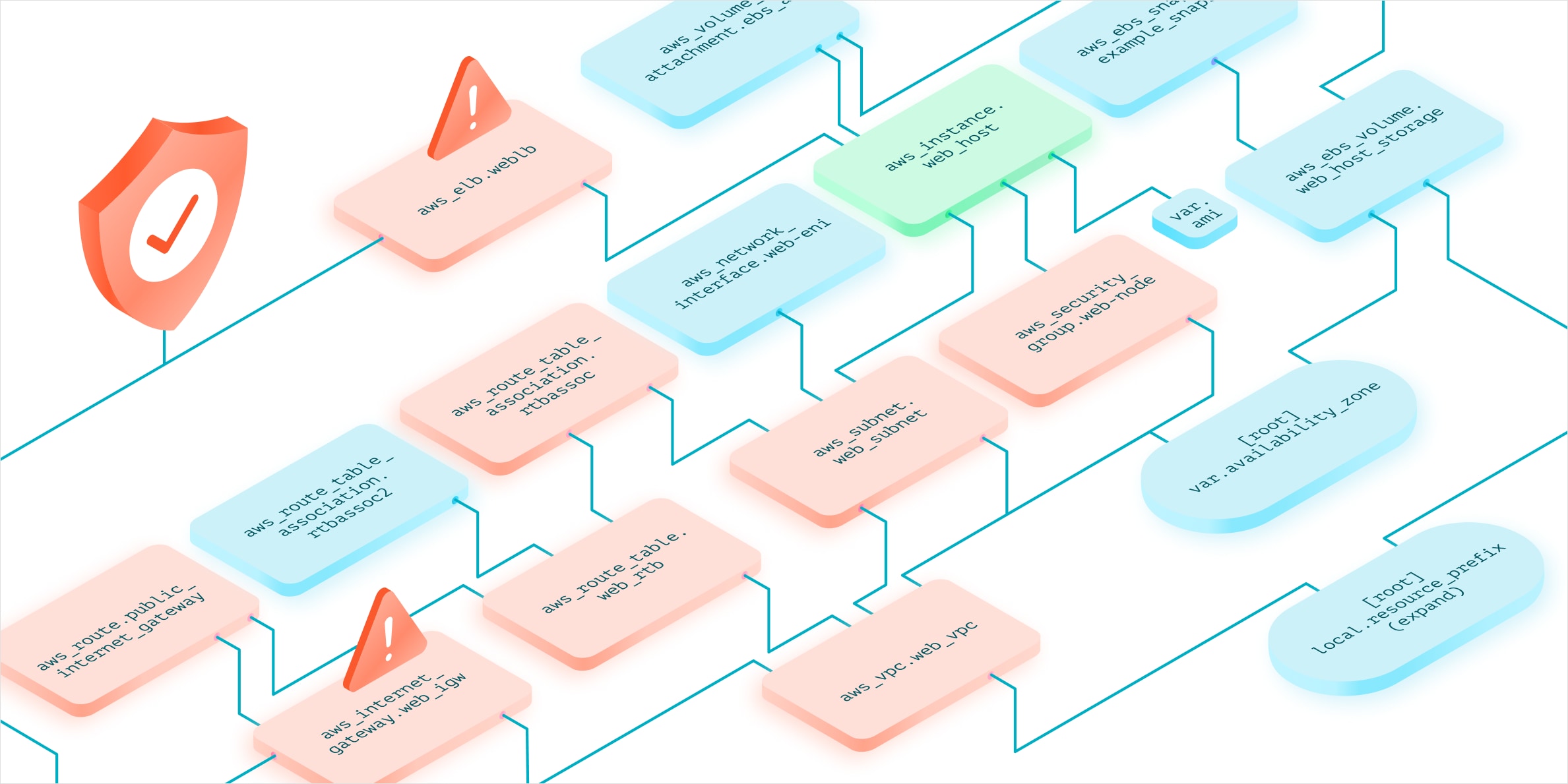
Now with Checkov 2.0’s graph-based mapping, those complex dependencies can be fully mapped out and understood prior to the development process.
This drastically improves the accuracy of scans and helps to provide better risk prioritization while reducing false positives. In addition to all of these benefits, the new architecture comes with a significant performance boost – developers will receive feedback faster, with more accuracy, improving their productivity.
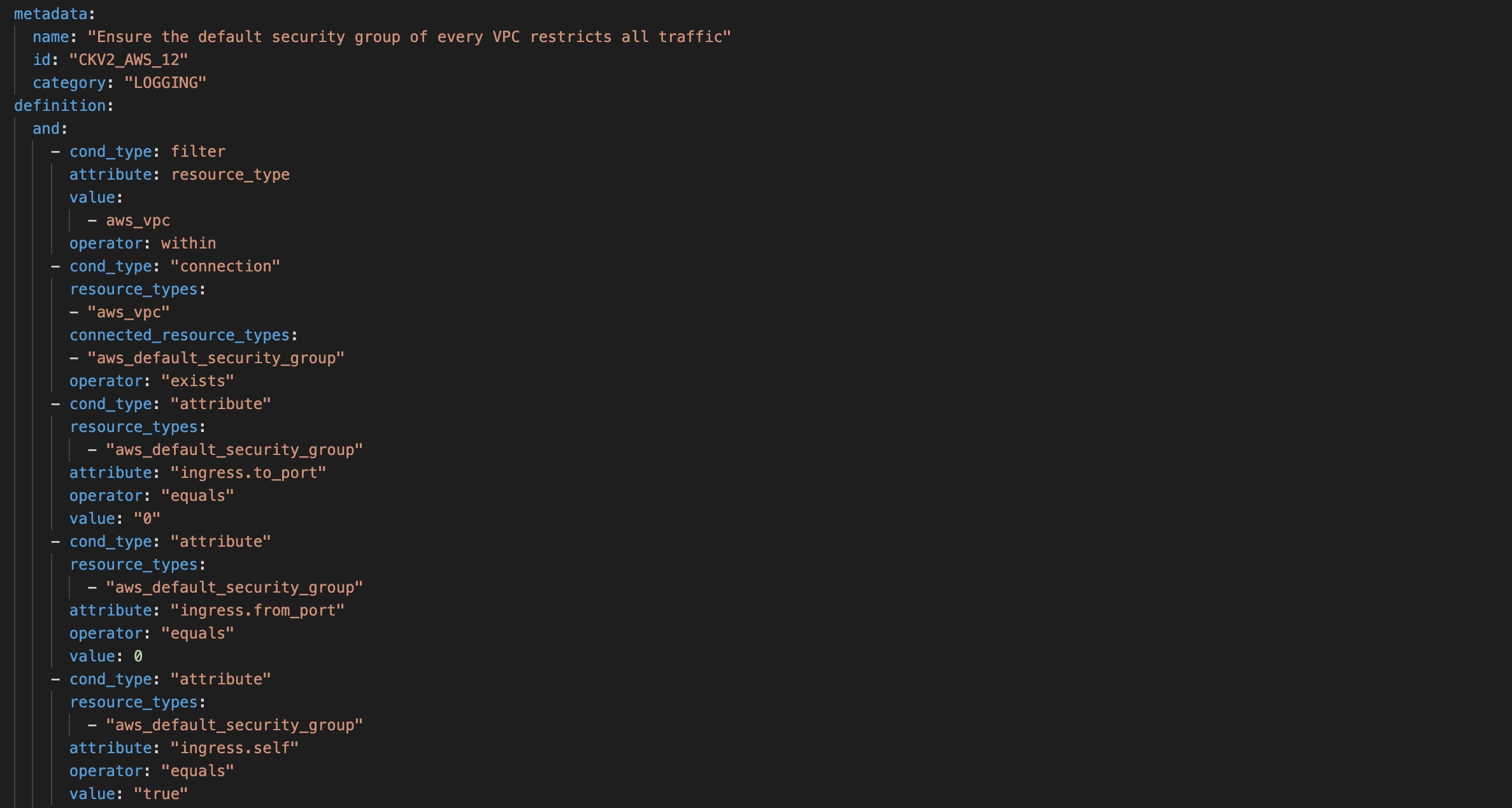
Expanded Out-of-the-Box Policy Library
With the graph-based rewrite, there are nearly 250 new policies available out-of-the-box, including some that weren’t possible before this new approach. These added policies mean that Checkov now covers more than 50% of configurations for most CIS Benchmarks, including more than 60% of the CIS Kubernetes Benchmark version 1.6.0. Security teams and developers can be more confident that they can meet compliance requirements before a single cloud asset is provisioned in production.
We’ll continue to source new policies from the community and with the combined power of Prisma Cloud threat research teams.
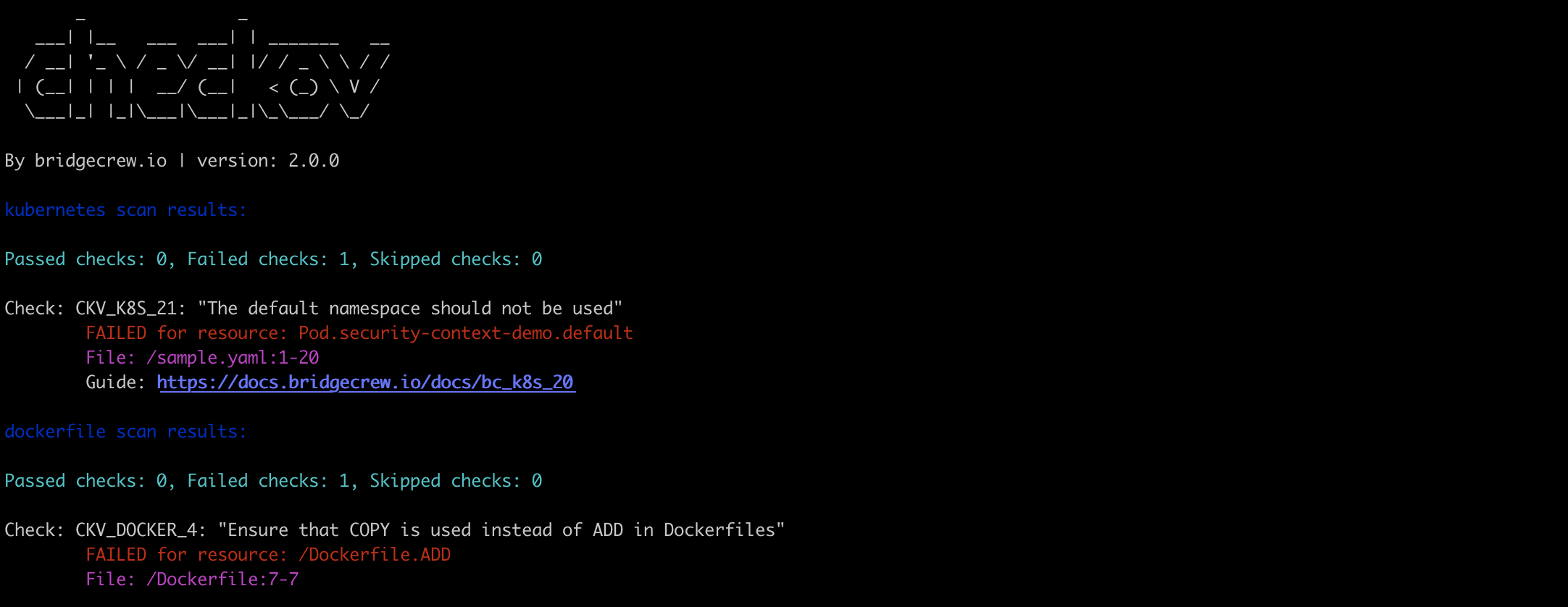
New Dockerfile Misconfiguration Scanning Capabilities
Checkov scans for misconfigurations in Terraform, CloudFormation, Azure Resource Manager (ARM), Kubernetes, Helm, and Serverless Frameworks. And Checkov 2.0 now supports Dockerfiles as well.
Docker containers are susceptible to misconfigurations such as open ports, running as root and containing secrets. Checkov will automatically discover resources and scan them to identify those misconfigurations early, including many of the other CIS benchmark requirements, helping developers patch their code before the container is built.
Get Started with Checkov
We’re excited to shift further left to secure more of the cloud native security stack. All of these features are available free and open sourced today. Checkov is available in many popular package managers, so you can try it for yourself. Everything included in this release is also available in the Bridgecrew product for both paid and free tier customers. You can sign up for a free 14-day trial to get started.
To learn more about this release and our vision for this space, tune in to our community office hours hosted by the builders and maintainers behind Checkov, live on Thursday, April 8 at 10am PT/1pm ET or view the recording anytime after on Twitch.