New graph visualization and Google Cloud support in Prisma Cloud enables customers to get comprehensive visibility into permissions and enforce least-privilege access across multi-cloud infrastructure.
Companies adopting multi-cloud infrastructures quickly become overwhelmed with managing identity permissions. To ensure security doesn’t prevent developer agility, organizations grant unnecessary privileges to nearly all cloud identities. In fact, Unit 42 Threat Researchers found that 99% of the cloud users, roles, services, and resources were granted excessive permissions which were left unused.
Last year, Palo Alto Networks introduced Cloud Infrastructure Entitlement Management (CIEM) into Prisma Cloud – the industry’s first Cloud Native Application Protection Platform (CNAPP). Our commitment with CIEM is to help businesses ensure their cloud identity permissions don’t expand their attack surface.
Today, we’re announcing two critical capabilities to combat permissions risk:
- Graph Visualization: Take control of cloud permissions sprawl with an interactive graph visualization to easily find connections between identities (human, non-human, IdP) and cloud resources.
- Support for Google Cloud Platform (GCP): Discover, secure, and monitor permissions on GCP, in addition to AWS and Azure.
With the latest release of Prisma Cloud, our customers get access to best-in-breed identity security from an integrated security platform to protect their public cloud and multi-cloud infrastructure.
CIEM Graph Visualization
The nature of multi-cloud environments present new security challenges. Every machine receives an identity and the number of workloads in the cloud outnumber humans causing an identity sprawl. Recent Unit 42 research found over 680,000 cloud identities spanned across 200 organizations — an average of 3400 identities per organization. Without a comprehensive view of cloud identities and access, security teams don’t know where to start with entitlement management.
Prisma Cloud now provides a graph view of cloud permissions risk across AWS, Azure, and Google Cloud. This new functionality analyzes all cloud identities, entitlements, and access across multi-cloud infrastructure, calculates the net effective permissions, and normalizes data into an easily consumable graph visualization. Prisma Cloud provides instant visibility into exactly who or what has access to your resources and what they can do. With an interactive graph visualization, security teams can easily identify permissions gaps between identities (human, non-human, IdP) and cloud resources and take control of cloud infrastructure access.
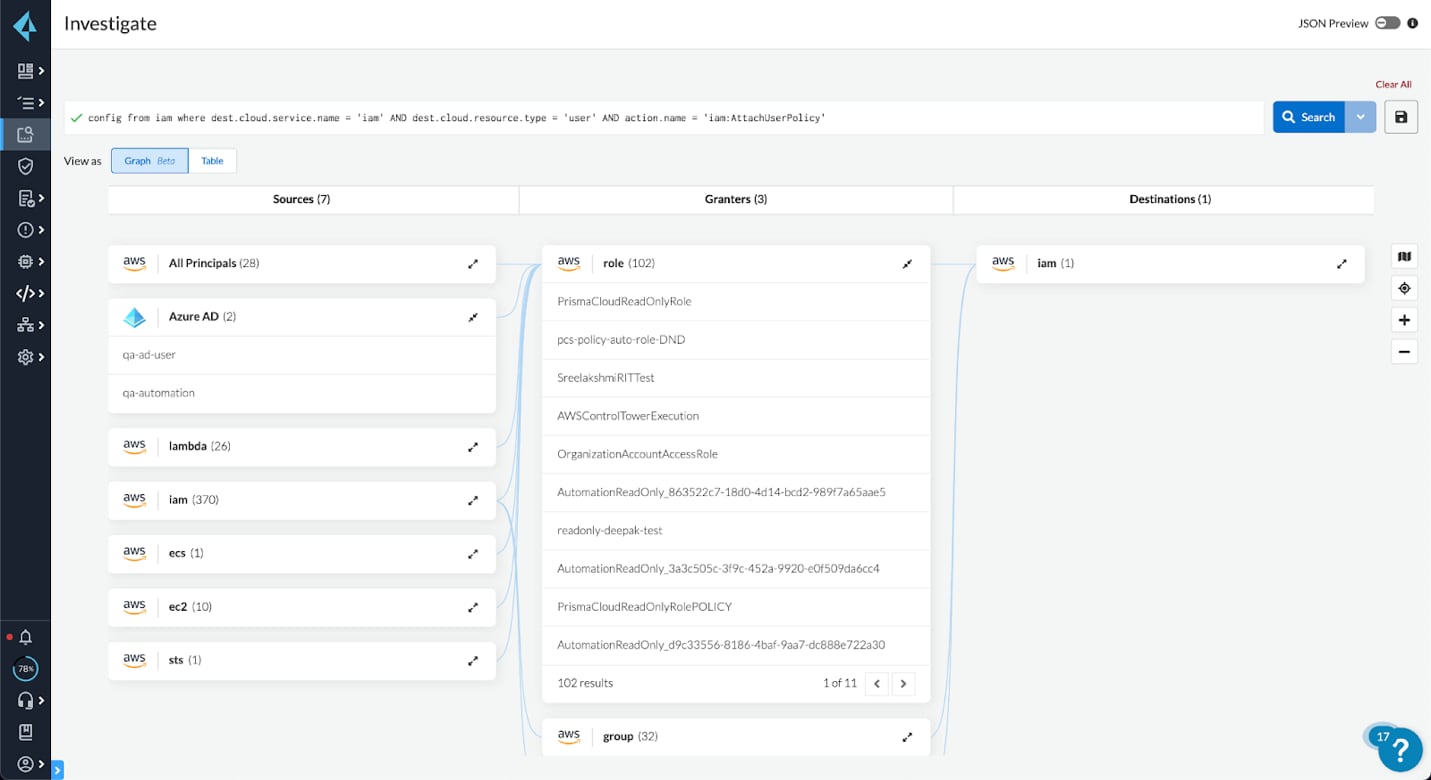
Cloud Infrastructure Entitlement Management (CIEM) for Google Cloud Platform
According to Gartner, 81% of organizations said they are working with two or more public cloud providers. Each time a company adopts a new cloud service provider—AWS, Azure, and GCP—they’re also taking on a new policy model to manage cloud identities and permissions. Since public cloud providers introduce new taxonomies and do not natively integrate, security teams quickly become overwhelmed with managing permissions risk across clouds.
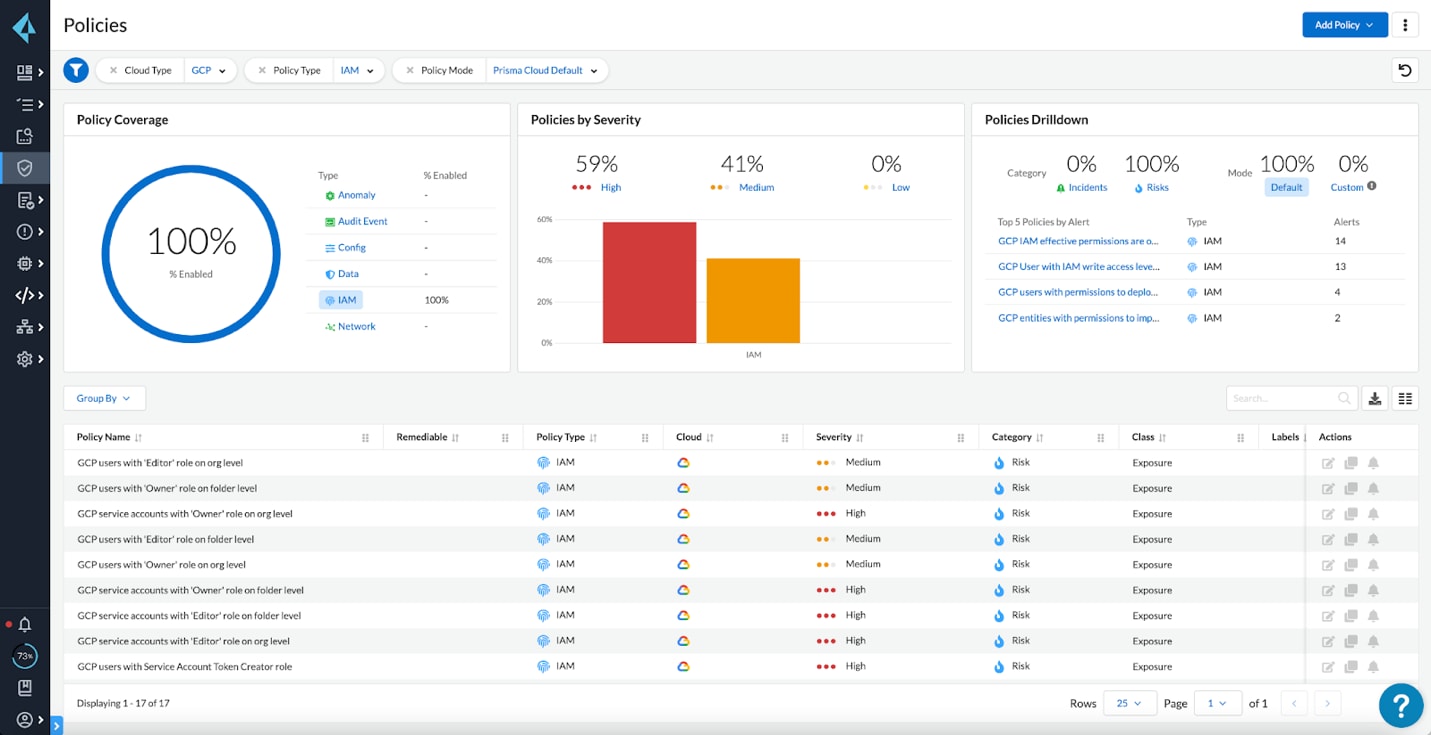
With the newly added CIEM capabilities, Prisma Cloud can now help customers discover, secure, and monitor permissions on GCP. Prisma Cloud calculates and analyzes net-effective permissions, monitors for risky and unused entitlements, and offers least-privilege recommendations for GCP cloud accounts, in addition to Amazon Web Services (AWS) and Microsoft Azure. By combining this newly added support with the new graph visualization, security teams can easily identify permissions risk across their GCP environments and reduce their attack surface.
Learn More
These new capabilities are available to customers interested in beta trials and will be generally available later this summer.
If you’re interested to learn more about the graph visualization, then check out the demo video below. Or if you want to get valuable hands-on experience with Prisma Cloud then request a 30-day trial to try out the Cloud Identity Security capabilities.