At rest, a container is a standalone file or package of files with everything needed to run an application. This is referred to as a container image. And not all container images are created equal. Images pulled from public repositories – essentially untrusted sources – can present the potential for compromise. These images may contain vulnerabilities, may not be properly configured to meet compliance standards or may even contain malicious components. Last year, Unit 42 highlighted the importance of container image trust in their research on the Graboid cryptojacking worm. While the research is extensive, improving processes around image trust was one of the foundational recommendations for container users.
With Prisma Cloud, users can make sure that the images they are using are safe, secure and only originate from sources within their control.
Trust Groups in Prisma Cloud
Prisma Cloud does this through Trust Groups. With Trust Groups, users can specify which images are safe to run within their environment, either by image or by image layers. Prisma Cloud scans all running images and allows users to select these images for use within these trusted groups. Users are able to specify a registry and/or repository that they would like to permit for deployment within their organization, thereby creating alerts or blocking the container images that try to run outside of this allowed trust. This can even be done with Docker Hub at the repository level if specific images from public sources are used.
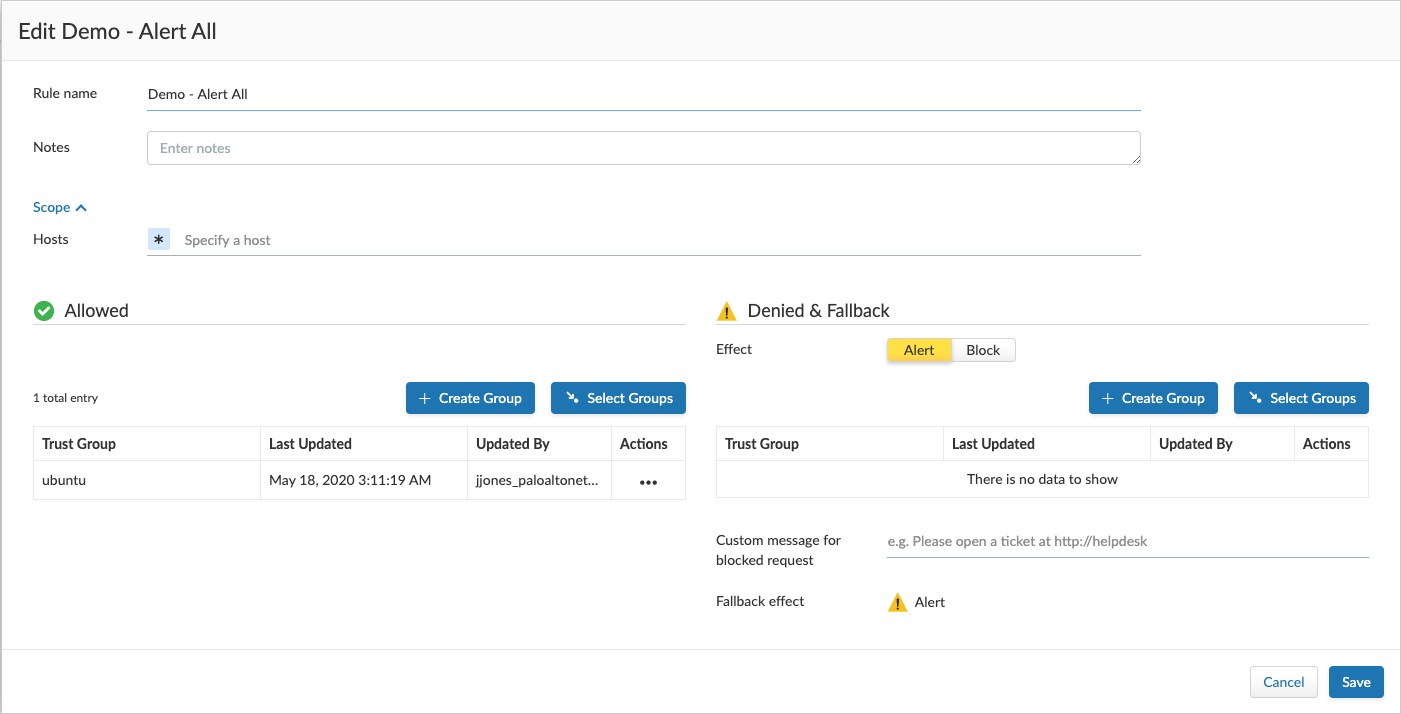
In the screenshot above, we’ve created a Trust Group to allow the Ubuntu repository to run images in a trusted manner. Anything from other sources would have alerts created as untrusted.
Trust Audits
Once your Trust Groups are specified, Prisma Cloud keeps an audit trail of all images that do not match this group, giving users better visibility into the developer workflow and making it possible to fine-tune which images should and should not be running in an environment.
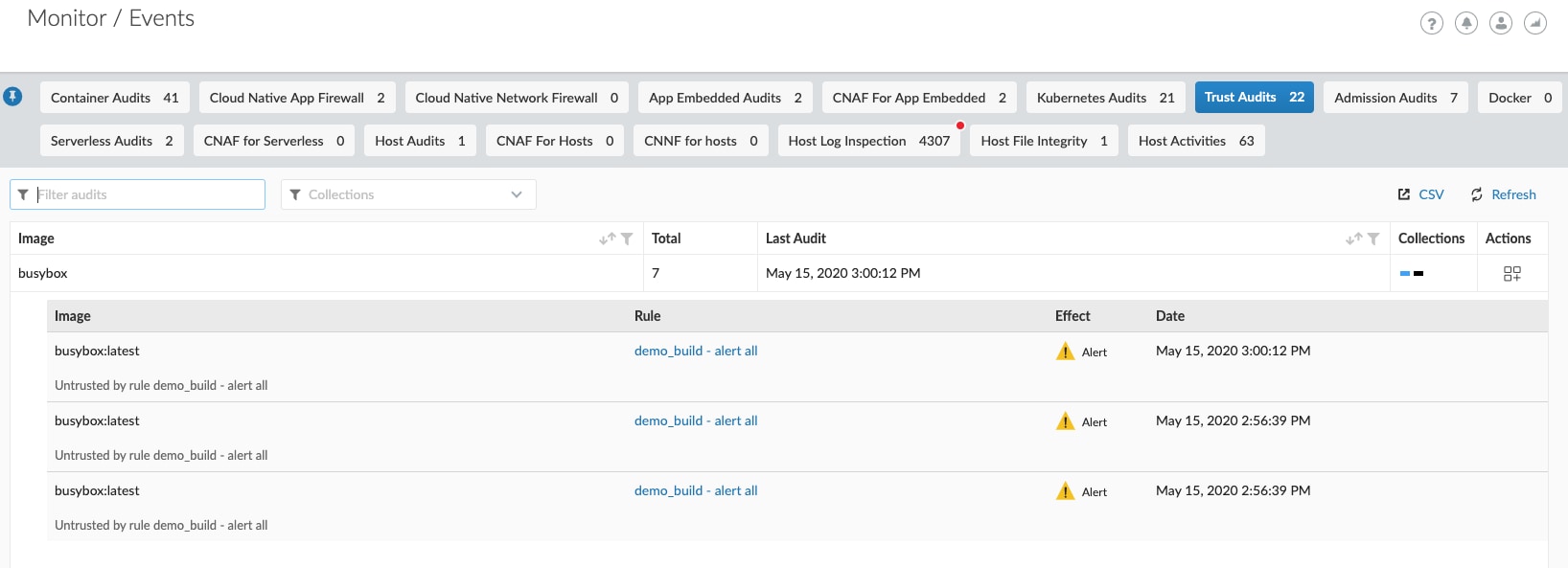
In the above screenshot, we can see that BusyBox generated an alert because it did not adhere to the established trust rule. We can add these images to the trust rule from this page, making an easy addition to the Trust Group.
Visibility Across Images
Prisma Cloud provides visibility into which images within the environment are trusted and untrusted, making sure users have a complete picture of the running environment. This is a good way to visualize at a glance which images are trusted to run within the environment and to quickly alert users to which images are running in an untrusted manner.
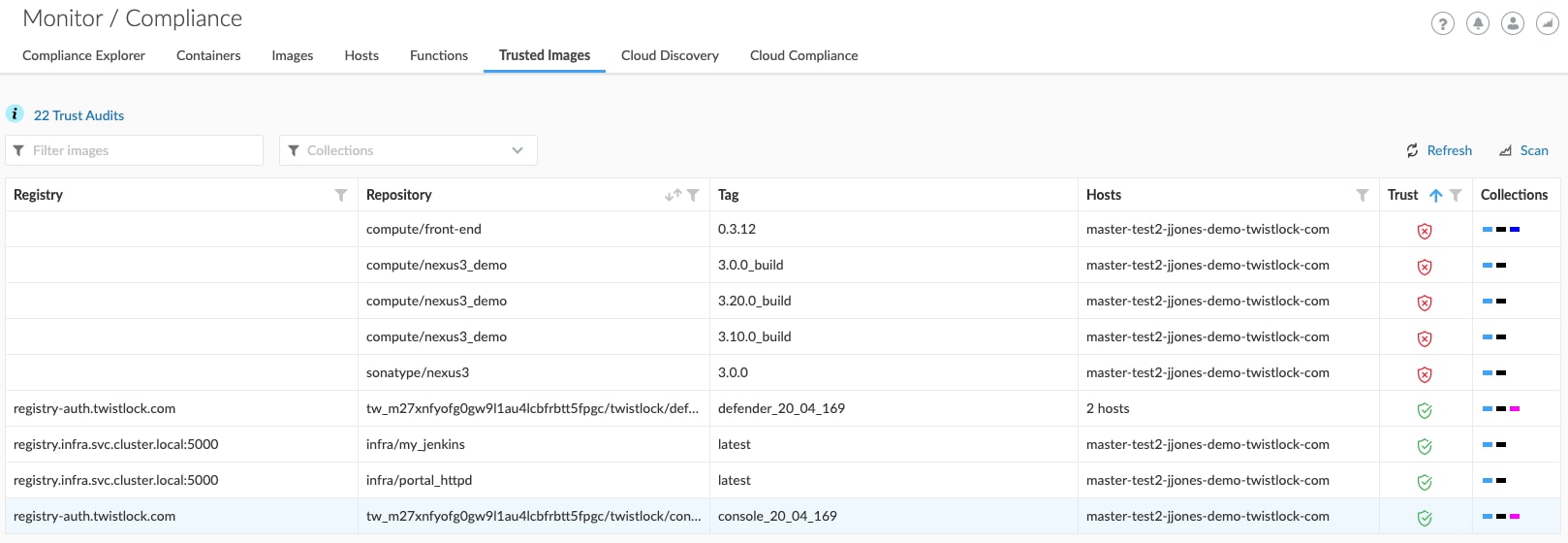
In the above screenshot, we can quickly see which images are trusted and which are not by just looking at the trust column of our container images.
Better Container Image Trust, Less Effort for Security Teams
Trusted Images is a great feature for controlling container images that are allowed to run within the environment. Prisma Cloud offers deep functionality to monitor, set up alerts and gate images. It also provides visibility into images running within the environment. The result for users is a much more secure environment for far less effort, allowing teams to instead invest energy in keeping the environment compliant with secure container standards.
For more information on how Prisma Cloud manages containers and other workload security, you can view our compute security page.