Exploring the latest enhancements of Cloud Discovery & Exposure Management (CDEM) to combat shadow IT with Prisma Cloud.
The flexibility and scalability of cloud-native development create a strong platform for organizations to drive innovation. These benefits, though, can disperse cloud assets, which poses challenges. The go-to solution addressing the essential need for visibility is cloud security posture management (CSPM). CSPM’s capabilities span the organization’s cloud ecosystem, equipping security teams with visibility into all of their cloud assets. And enabling this visibility in most cases entails merely onboarding your cloud accounts with read access.
But what happens if you don’t onboard your account at the organizational level (which is often the case)? What if a developer spins something up in another account or with a cloud service provider (CSP) that’s not onboarded to your CSPM tool?
The short answer is; You won’t have visibility into risks emerging from non-onboarded cloud accounts and services.
In reality, it's quite easy for developers to create cloud resources outside of the CSPM's scope and for those resources to go unnoticed. In fact, approximately 30% to 40% of an organization's publicly accessible attack surface is unknown. What does this mean to you? Your organization likely has a far greater infrastructure than you know.
How Does CDEM Fit into Your Cloud Security Strategy?
CDEM and CSPM are counterparts. While CSPM scans your cloud ecosystem based on internal configuration, cloud discovery and exposure management (CDEM) implements IP-based scans to look at your exposures from the outside-in. CDEM covers the void, in other words, discovering assets and accounts that have escaped the view of your CSPM because they were never onboarded into your CSPM.
Are Your Managed Assets Interacting with Unmanaged Assets?
A capability of CSPM within Prisma Cloud is the ingestion of network flow logs across AWS, Azure and GCP. By ingesting VPC flow logs and cloud network configuration logs, you can monitor network traffic. This vantage allows you to explore the interconnectivity of your cloud resources by account and region using data points such as, packets, bytes, source or destination resource, source or destination IP address, and source or destination port information.
With CDEM, you can identify unmanaged assets attributed to your organization by their IP addresses. By leveraging the ability to visualize traffic flow between internet-exposed (unmanaged) and secure (managed) assets, you can make informed decisions to prioritize and take appropriate actions to secure the internet-exposed assets.
With 5 Minutes to Fix Unmanaged Assets, Where Should I Start?
Oftentimes, you end up with a sea of unmanaged assets and aren’t sure where your biggest risks are and how to go about prioritizing them. Here’s our thoughts on how to approach unmanaged asset prioritization.
Start with What’s Critical
Focus on exposed assets with vulnerabilities, those that are interacting with managed assets. Assets exposed to the internet, vulnerable to exploitation, and connected to a managed asset in Prisma Cloud are patchable.
Progress Through the Hierarchy of Risk
Once critical vulnerabilities are fixed, move to assets with patchable and exploitable vulnerabilities and work down the list.
- Exploitable: Assets exposed to the internet containing a vulnerability with a known exploit and is patchable
- Patchable: Assets exposed to the internet containing a patchable vulnerability
- Vulnerable: Assets exposed to the internet containing a vulnerability
- Exposed: Assets exposed to the internet
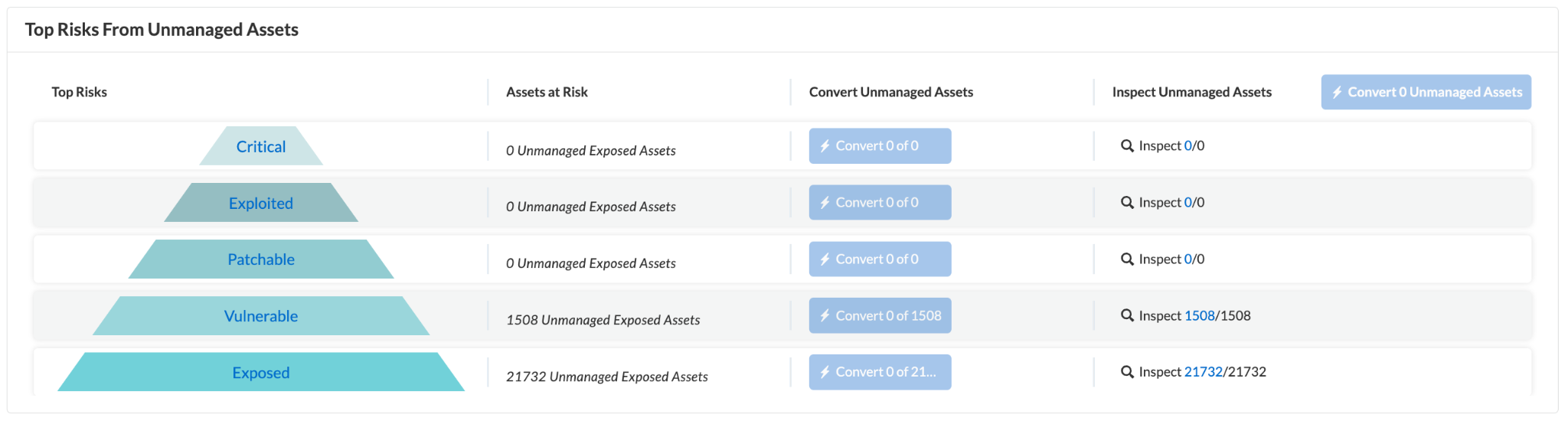
In some instances, you may encounter issues that you don’t want to address immediately or that are intentionally exposed. Regardless, you’ll still want to convert unmanaged assets to managed. Within Prisma Cloud, you can temporarily or permanently snooze these unmanaged (internet-exposed) assets while inspecting them in the Discovery and Exposure Management Dashboard widgets. This functionality allows you to separate active assets from snoozed assets in the unmanaged assets inventory, providing greater flexibility in asset management.
Learn More
Prisma Cloud is dedicated to helping organizations secure their applications from code to cloud. The platform provides visibility into internal risks and external attack surfaces, and it correlates risk signals to help security teams connect the dots across their cloud-native environments.
Discover more about internet-exposed assets, the processes involved with identifying and prioritizing risks, and how to remediate risks posed by unmanaged assets, download our white paper Cloud Discovery and Exposure Management. If you'd like to see CDEM technology in action, book a demo with one of our experts.