Cloud storage is one of the most prevalent platform-as-a-service (PaaS) solutions to experience breaches. Given how common these breaches are, it demonstrates how users often fail to effectively manage security for these services. In this article, I will highlight some of the most important actions users can take today to prevent a data breach in cloud storage on Amazon Simple Storage Service (S3).
Mitigations
Use a Comprehensive CSPM Tool
Changes in public cloud infrastructure are constant; it’s just the nature of these environments. So it’s essential to have a Cloud Security Posture Management (CSPM) tool that continuously monitors your cloud services, assess their security posture and takes action on misconfigurations before they can be exploited. Also, there should be a team auditing your infrastructure changes on a regular basis.
Stay Up To Date With Recent Security Features
Cloud vendors often enhance their services’ security features either by introducing new features or deprecating old features. Users should be aware of the latest changes and ensure their infrastructure is always current.
Amazon S3 Block Public Access
AWS has introduced a new security feature called ‘Block Public Access’, which works at the account level as well as the bucket level. With this feature you can block existing and future public access at the account level itself; if any storage is not intended to be public you can place the data in one of these separate accounts.
Properly Define ACLs and Bucket Policies
Ensure that your Amazon S3 buckets use the correct access control lists (ACLs) and bucket policies so they are not publicly accessible. Implementing least privilege access is fundamental in reducing security risk and the impact that could result from errors or malicious intent.
Use S3 Access Points or VPC Endpoints for Amazon S3 Access
Amazon S3 provides functionality for creating and managing access points. As access points have a set of defined restrictions, you can use if your data is shared among VPC users and avoid including sensitive information in the access point name. A VPC endpoint for Amazon S3 will provide a logical entity within a VPC that allows connectivity only to Amazon S3. You can prevent data exfiltration by using a VPC that does not have an internet gateway.
Enable MFA Delete
Multi-factor authentication (MFA) Delete can help prevent accidental bucket deletions. If MFA Delete is not enabled, any user with the password of a sufficiently privileged root or IAM user could permanently delete an Amazon S3 object.
Enforce Data Encryption
On the server side, Amazon S3 encrypts your object before saving it on disks in its data centers, and then decrypts it when you download the objects. Encrypt data client-side and upload the encrypted data to Amazon S3. In this case, you manage the encryption process, the encryption keys and related tools. Use HTTPS (TLS) using the SecureTransport condition on Amazon S3 bucket policies to prevent potential attackers from eavesdropping on or manipulating network traffic using person-in-the-middle or similar attacks.
Use IAM Roles for Applications and AWS Services That Require S3 Access
Applications on Amazon Elastic Compute Cloud (EC2) or other AWS services must include valid AWS credentials in their AWS API requests to access S3 resources. Instead of storing credentials in the application or EC2 instance, you should use an IAM role to manage temporary credentials for applications or services that need to access. The role supplies temporary permissions that applications can use when they make calls to other AWS resources. The IAM role assigned should have restrictive access.
Implement S3 Object Lock and Versioning
S3 Object Lock enables you to store objects using a "Write Once Read Many" (WORM) model. S3 Object Lock can help prevent accidental or inappropriate deletion of data. Versioning enables multiple variants of an object in the same bucket and you can easily recover from both unintended user actions and application failures.
Implement Built-in Logging and Monitoring Tools
Logging provides detailed records of the requests that are made to a bucket. Monitoring is an important part of maintaining the reliability, security, availability and performance of your S3 and other AWS solutions. AWS provides CloudTrial for logging and CloudWatch for monitoring purposes.
Consider Private Storage
Private storage can be used to hold sensitive data that will reside apart from public storage. This storage is always private and cannot be accessed over the internet. Accessing private storage is done through an API wrapped with security controls.
Avoid Human Errors
To avoid unintentional human errors, follow best practices checklists. Whoever has access to sensitive data should be limited and authenticated with multiple factors like MFA devices. Separating the production environments would clearly highlight the differences between public and private storage, and help you prevent accidental exposure of data through S3.
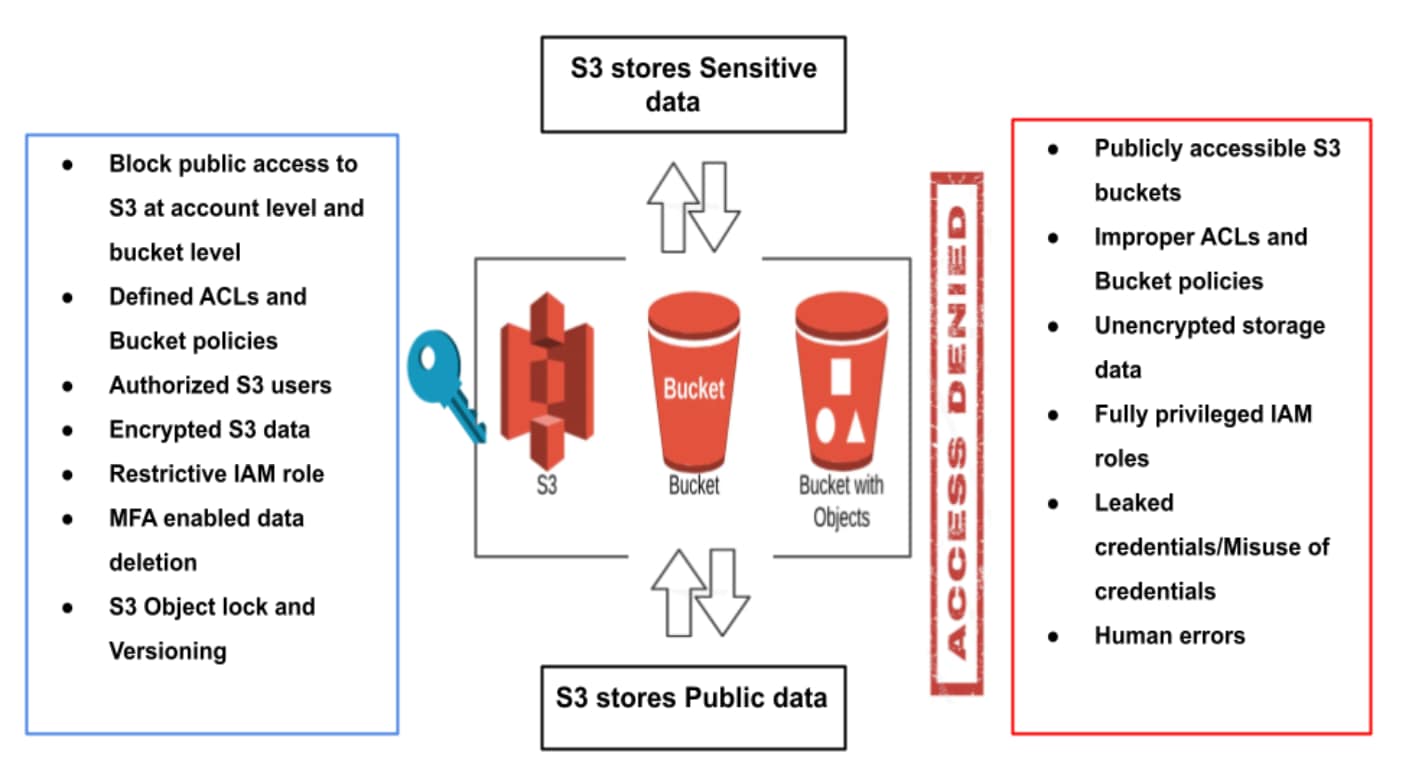
Checklist for protecting your data from cloud storage breaches.
Conclusion
When it comes to security, cloud service providers offer a number of tools and controls. But users often leave gaps in the security controls, and therefore leave these services they use exposed to breaches. Even if unintentional, the cost of a data breach can exceed millions of dollars.
Getting started with the right CSPM tool will improve your security stance and reduce your risks and provide you protection against such breaches.