As organizations increasingly move their applications and data to the cloud, the shift to cloud-native application development has introduced a new set of security challenges, particularly when it comes to managing access to sensitive information. Cloud identity and access management (IAM) has become the new perimeter for security teams.
Let’s look at why net-effective permissions and least-privileged access are critical for securing cloud environments.
Cloud IAM Challenges
The aim of administering IAM policies in public cloud environments is to reduce the attack surface by enforcing least-privileged access. But security practitioners face several IAM challenges when it comes to successfully identifying net-effective permissions.
IAM Frameworks Are Complex
Cloud service providers (CSP) offer native IAM frameworks to control access to cloud infrastructure; but organizations must consider several unique types of permissions, such as allow, deny, service control policy (SCP), boundaries, and more. Let’s call these raw permissions.
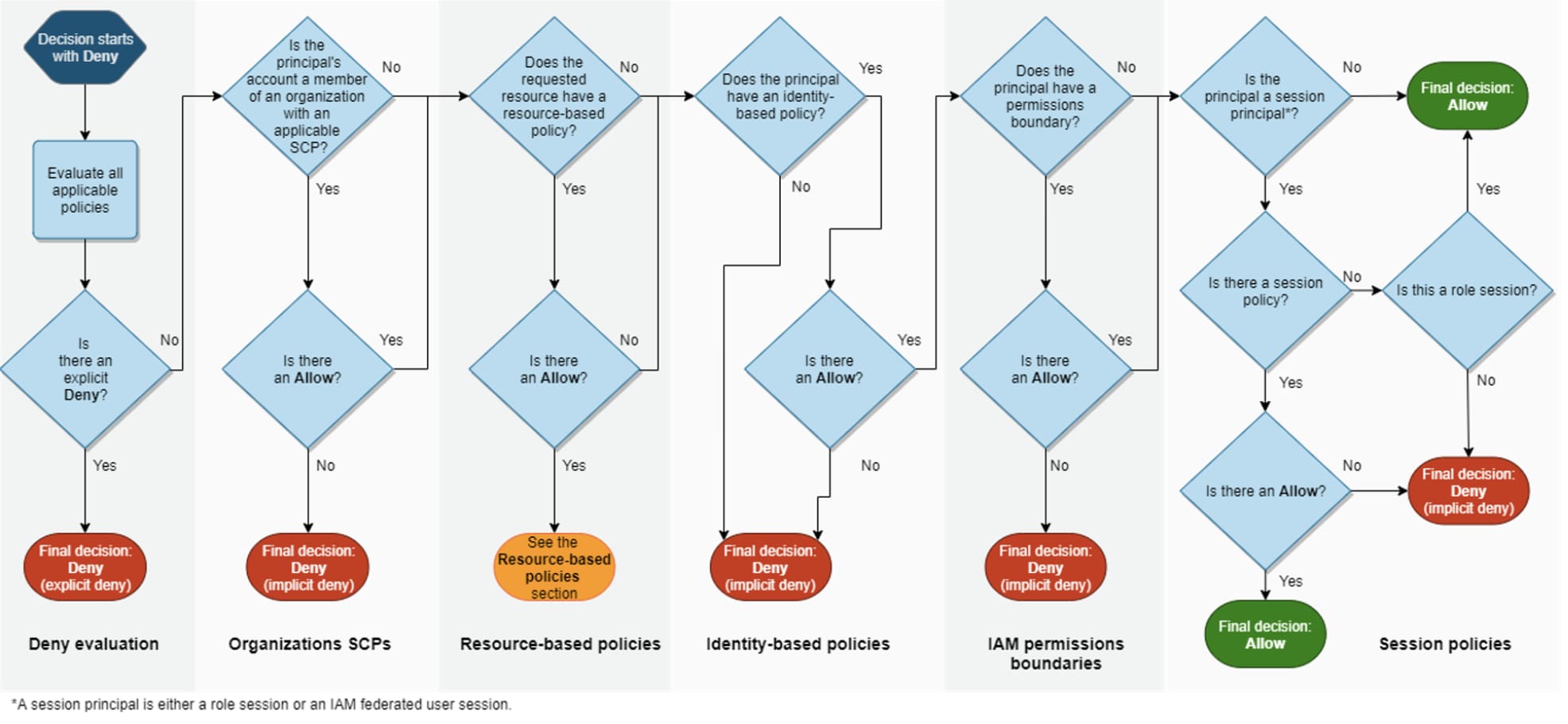
To help organizations get started with IAM policies, native CSP tools offer pre-built privileges known as CSP managed permissions. One of the most common CSP managed permissions is “admin privileges”, which grants users with read and write permissions for all infrastructure.
But without integrated tooling to make sense of raw permissions, organizations are left to manually assess net-permissions, which, at best, is a daunting prospect.
Identity Providers (IdP) Add Another Layer of Complexity
To scale access management to cloud infrastructure, organizations use external IdPs and single sign-on (SSO) providers, such as Okta and Azure Active Directory.
While IdPs help organizations enforce consistent user authentication across the company apps, they further complicate the mapping between identities and their raw permissions. In addition to creating a gap in visibility, IdPs can make it difficult to accurately determine the IdP user's access, which may increase the risk of a security breach, as well as non-compliance with regulatory requirements.
Adopting Multicloud Requires Learning Unique IAM Languages
Approximately 90% of enterprises have a multicloud strategy, which increases the difficulty of managing permissions, as each cloud adopted introduces a new IAM framework to learn and manage.
While CSP tools can be good for setting up privileges, they’re less than ideal for monitoring and employing least-privilege access in multicloud environments. Using native tools that don’t integrate with tools from other CSPs requires security teams to learn and operate multiple frameworks and manage each cloud's identities separately.
How Understanding Net-Effective Permissions Can Help
Net-effective permissions refers to the complete set of permissions granted to an identity or group of identities, regardless of whether the identities are humans or machines. In other words, net-effective permissions help organizations to comprehend the extent of who has access to what in the cloud environment and why.
Embedding security with net-effective permissions is critical for gaining visibility and control over entitlements in the cloud. Foundational best practices include:
- Distill IAM frameworks into a natural language: Instead of trying to make sense of all possible entitlements and policy types, practitioners should think in terms of “who has access to what in my cloud?”
- Make IdP providers transparent: Any user, no matter where they log in from, should be easily identifiable. Understanding net-effective permissions means mapping external IdPs to the CSP IAM policy model and seeing permissions end to end.
- Unify multicloud policy models: The ideal state is to use the same IAM language no matter where your cloud assets are deployed. As you take on more cloud providers, working with net-effective permissions should make multicloud IAM adoption seamless for consistent security.
Cloud Infrastructure Entitlement Management Tools Address This Problem
Cloud infrastructure entitlement management (CIEM) is the process of managing identities and privileges in cloud environments. The purpose of CIEM is to understand which access entitlements exist across cloud and multicloud environments, and then identify and mitigate risks resulting from entitlements that grant a higher level of access than they should. By using a CIEM tool organizations can apply the principle of least privilege to reduce their attack surface.
Some CIEM tools address IAM challenges by auto-calculating the net-effective permissions for organizations, including organizations using IdPs, SSOs, and employing multicloud environments.
With a tool that provides a centralized platform for managing and monitoring access rights, organizations can utilize net-effective permissions mapping to highlight overly permissive access. CIEM tools can help easily remove overly permissive access for both user and machine identities to reduce the attack surface.
Advantages of using a CIEM tool include the following key functions.
- User and resource management allows organizations to manage users, groups, and resources from a centralized location.
- Real-time monitoring provides continuous visibility into the access rights of users and resources, enabling organizations to highlight overly permissive access and remediate it.
- Automated workflows automate common tasks, such as granting and removing access rights, to simplify processes and reduce the risk of errors.
Prisma Cloud Fills the Gap
Prisma Cloud CIEM delivers simple, consistent IAM across Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Accurately calculating net-effective permissions, Prisma Cloud helps organizations understand your multicloud identity risk, including identities managed with IdPs and SSO tools, such as Azure AD.
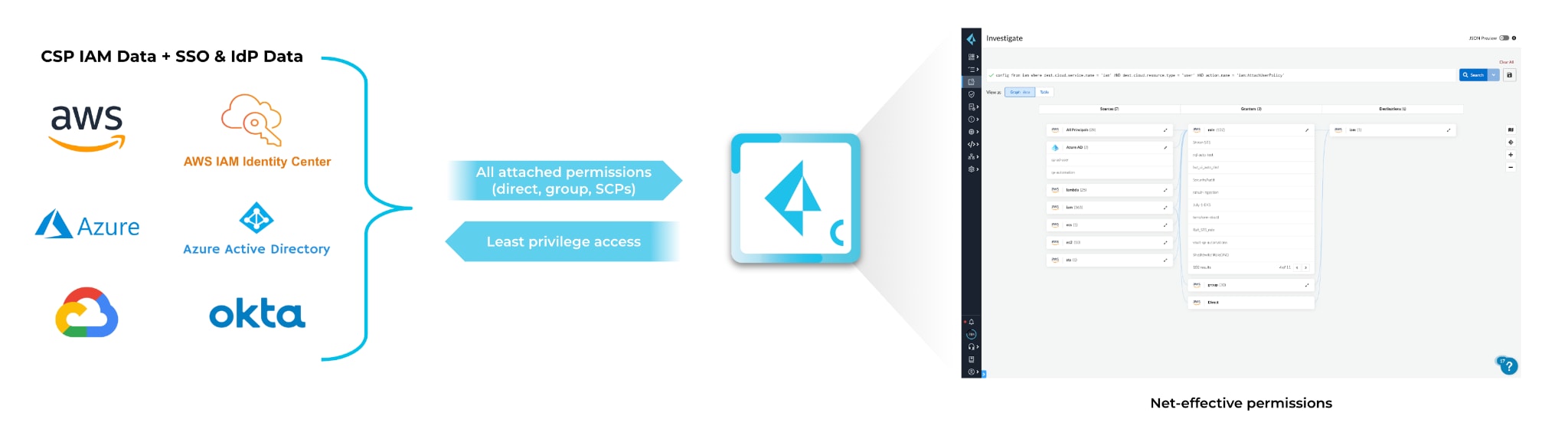
To enforce least-privileged access, Prisma Cloud will help organizations rightsize permissions and employ automated remediation to continually adjust permissions, reducing the attack surface. Additionally, Prisma Cloud provides intelligent graph visualizations, helping IAM practitioners visualize who has access to what across cloud environments.
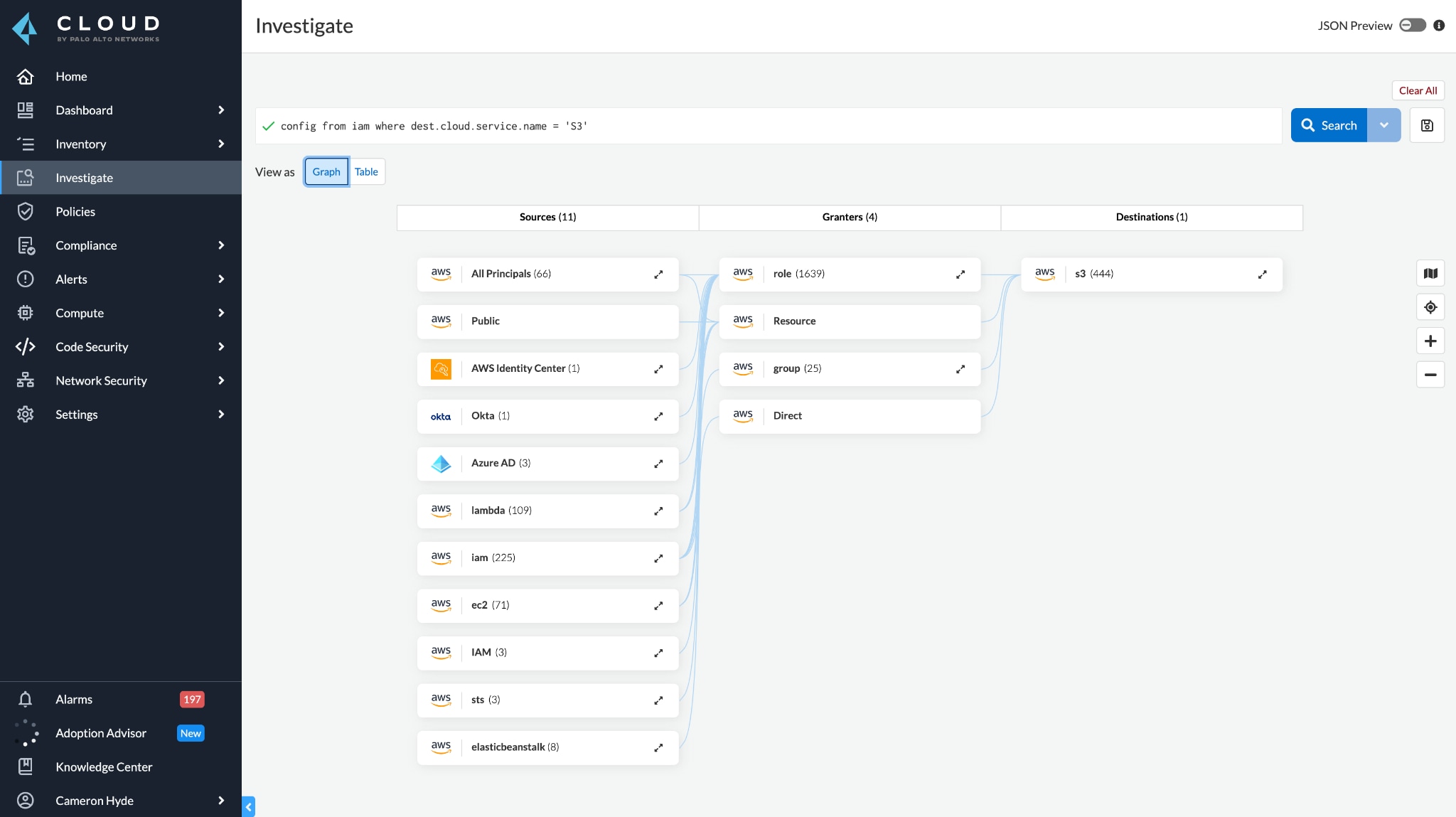
Prisma Cloud incorporates CIEM into its cloud-native application protection platform (CNAPP) to secure applications from code to cloud across multicloud environments. The platform delivers comprehensive security with both continuous visibility and proactive threat prevention throughout the application lifecycle. Prisma Cloud enables security and DevOps teams to effectively collaborate to accelerate secure cloud-native application development and deployment.
Learn More
Learn more about the CIEM capabilities of Prisma Cloud and take it for a free 30-day test drive to experience the advantages firsthand.