Trusting container images or virtual machines simply because they come from public registries, marketplaces, or previous snapshots is dangerous. Container images, running containers, and virtual machines may contain misconfigurations or malware, such as crypto miners or viruses. For example, Unit 42 found 30 malicious images in Docker Hub with cryptominers that had been pulled 20 million times.
Prisma Cloud has included threat intelligence feeds from public feeds and private research that identify malware in container images. To further advance that capability, we are excited to announce that we now offer a native integration with Palo Alto Networks WildFire for advanced malware analysis for containers and hosts in both CI/CD pipelines and in runtime.
Full Lifecycle Anti-Malware Identification
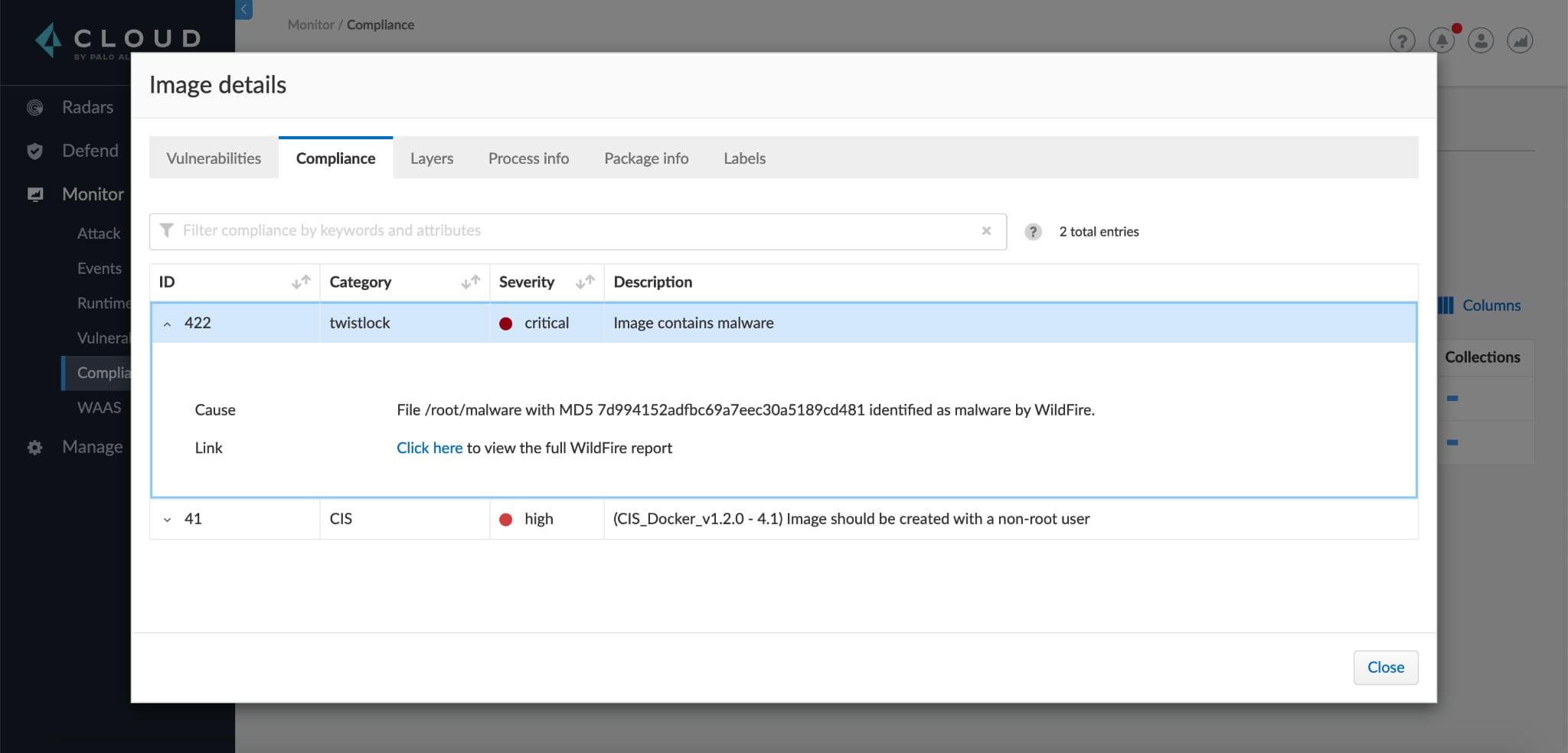
Prisma Cloud performs malware analysis in two places: CI pipelines leveraging our command line tool twistcli and in runtime. In CI pipelines, images with recognized file hashes are checked locally against threat feeds from Prisma Cloud and WildFire in near-real time.
For unrecognized files, the new integration takes the suspicious file and checks them with WildFire for deeper malware analysis. WildFire identifies new and unknown malware through multiple cloud-based analysis techniques, including sandboxing.
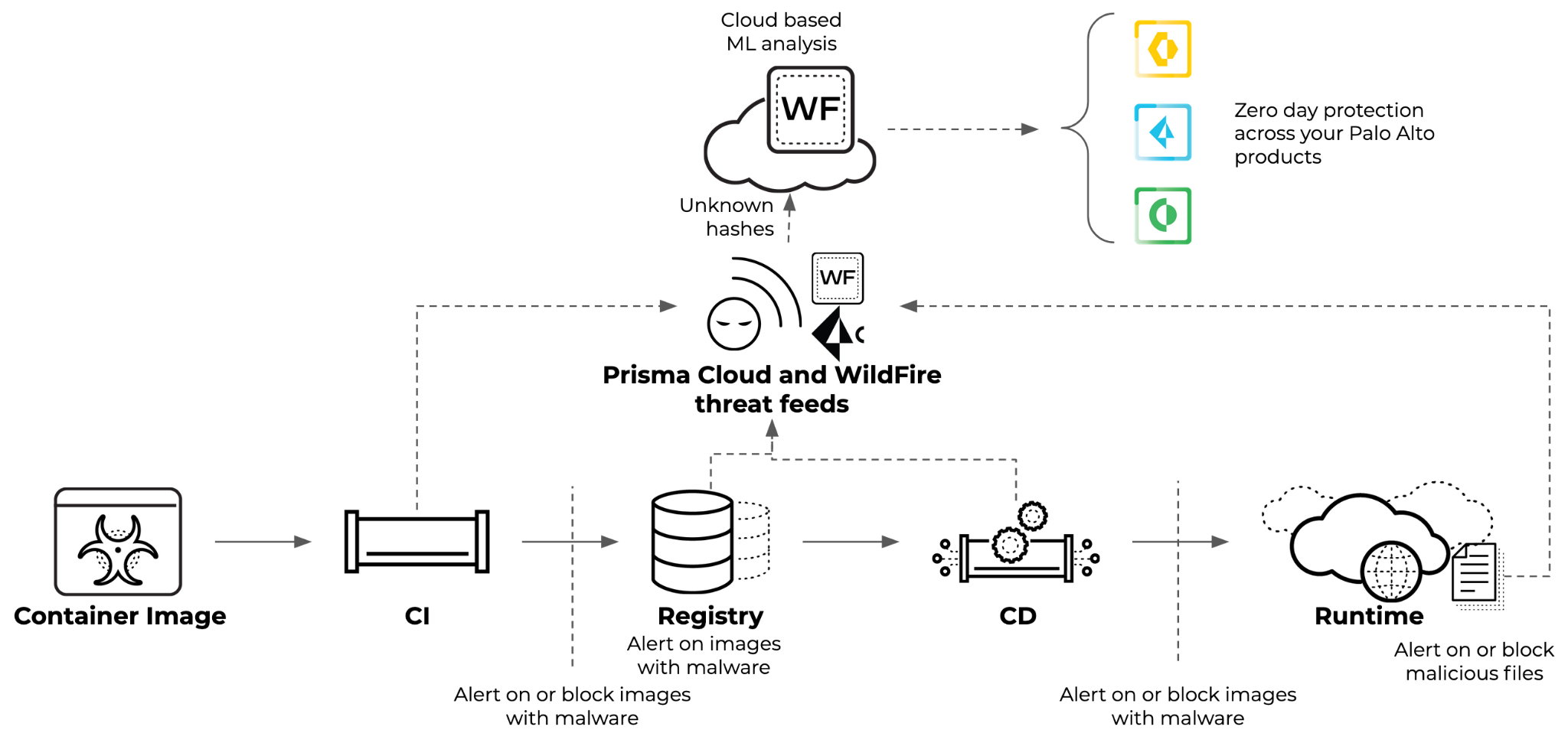
WildFire observes files in a purpose-built, evasion-resistant virtual environment, enabling detection of zero-day exploits and malware using hundreds of behavioral characteristics. If the WildFire analysis detects malware, you can choose to alert or block those builds. Limiting deployments to just Trusted Images that have been vetted prevents malicious images from ever entering your system.
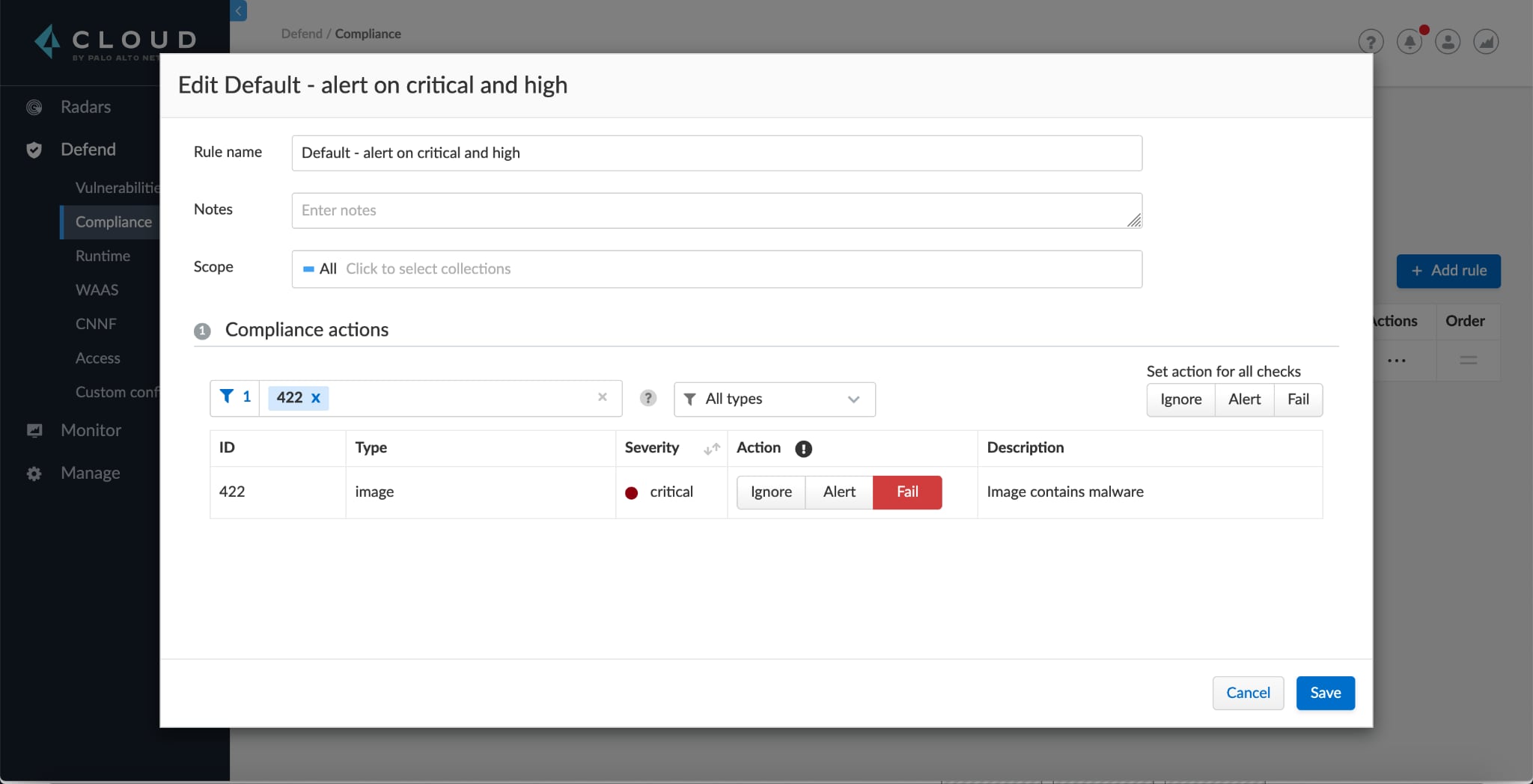
Wildfire analysis is integrated as a part of the compliance checks in your CI/CD pipeline, creating a secure path for vetted, trusted images and preventing supply chain attacks, like poisoned image attacks. Prisma Cloud can explicitly mark these verified images as trusted and can build a secure software development lifecycle (SDLC) by restricting container deployments to only those trusted images. However, not all malware comes from images. If a bad actor gains access to a host or container, it’s necessary to add another layer of protection.
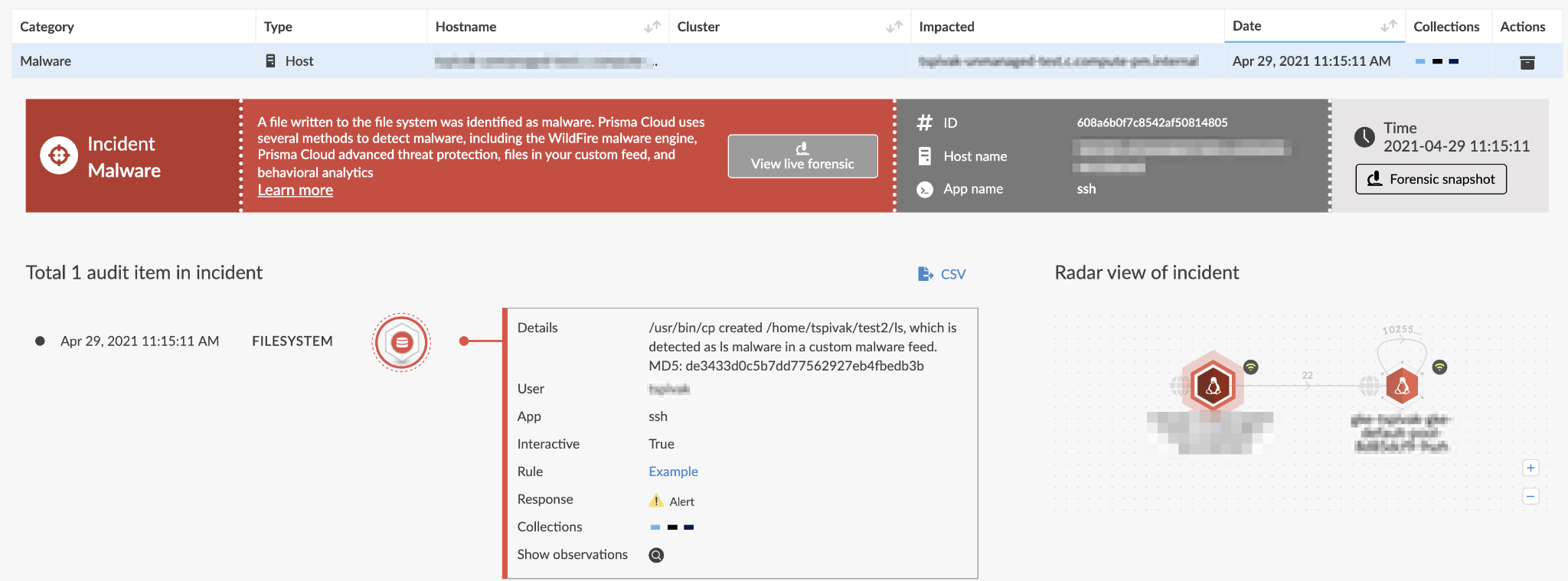
Prisma Cloud’s runtime defense detects and blocks anomalous and malicious processes, filesystem access and network behavior. With the WildFire integration, if malware is written to the file system, Prisma Cloud will block the malware and automatically capture forensic data about the events leading to and after the malware was detected. This provides full lifecycle, end-to-end protection against malware.
Combining the Power of the Palo Alto Networks Portfolio
If a zero day is detected in the Prisma Cloud WildFire integration or other Palo Alto Networks products such as our NGFW and Cortex XDR, all products that use WildFire will be protected from that unknown malware. Reports aggregate all analysis performed in a centralized format.
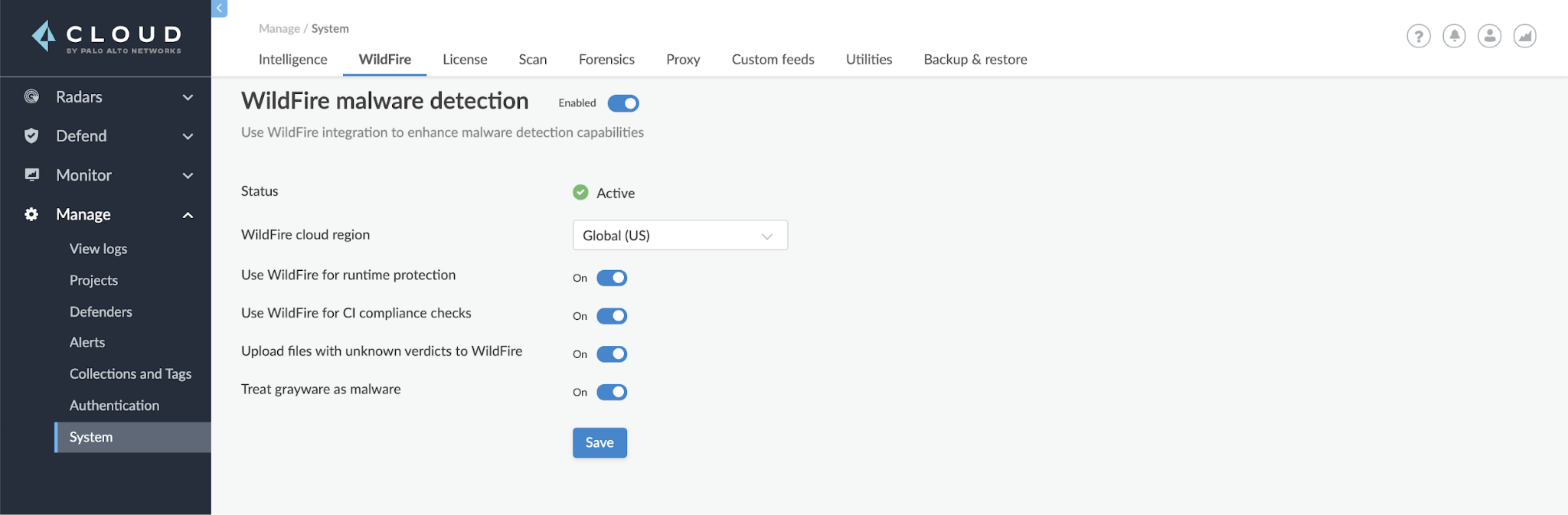
The WildFire integration is configurable from the System menu in Prisma Cloud. There is a switch to enable WildFire detection and you can pick the cloud region that is closest to the workload. Here you can further configure WildFire settings to fit your needs.
Prisma Cloud provides comprehensive security across the full development lifecycle to maximize the protection of cloud native workloads. With WildFire, we continue advancing our better together story by working across our entire portfolio of Palo Alto Networks products.
Find out more about WildFire malware protection and Prisma Cloud’s latest cloud workload protection capabilities.