This post is also available in: 日本語 (Japanese)
In June of 2020, Palo Alto Networks released the 2020 State of Cloud Native Security Report, a survey of more than 3,000 DevOps, cloud infrastructure and security practitioners to better understand the state of cloud native adoption and security requirements. When asked about infrastructure usage, respondents shared that, on average, 30% of workloads are running on VMs and 24% are currently running on containers.
Whether an organization runs standalone VMs or runs containers on top of VMs, DevOps and security teams need to secure these hosts. This requires a combination of vulnerability management, compliance and runtime protection. Prisma Cloud Host Security delivers defense-in-depth for Linux and Windows hosts, and with the latest update, the platform now offers enhanced runtime protection along with powerful visibility.
Improving Host Security: Enhanced Runtime Protection
With the latest release, users gain greater visibility into host behavior and security along with simplified rules creation.
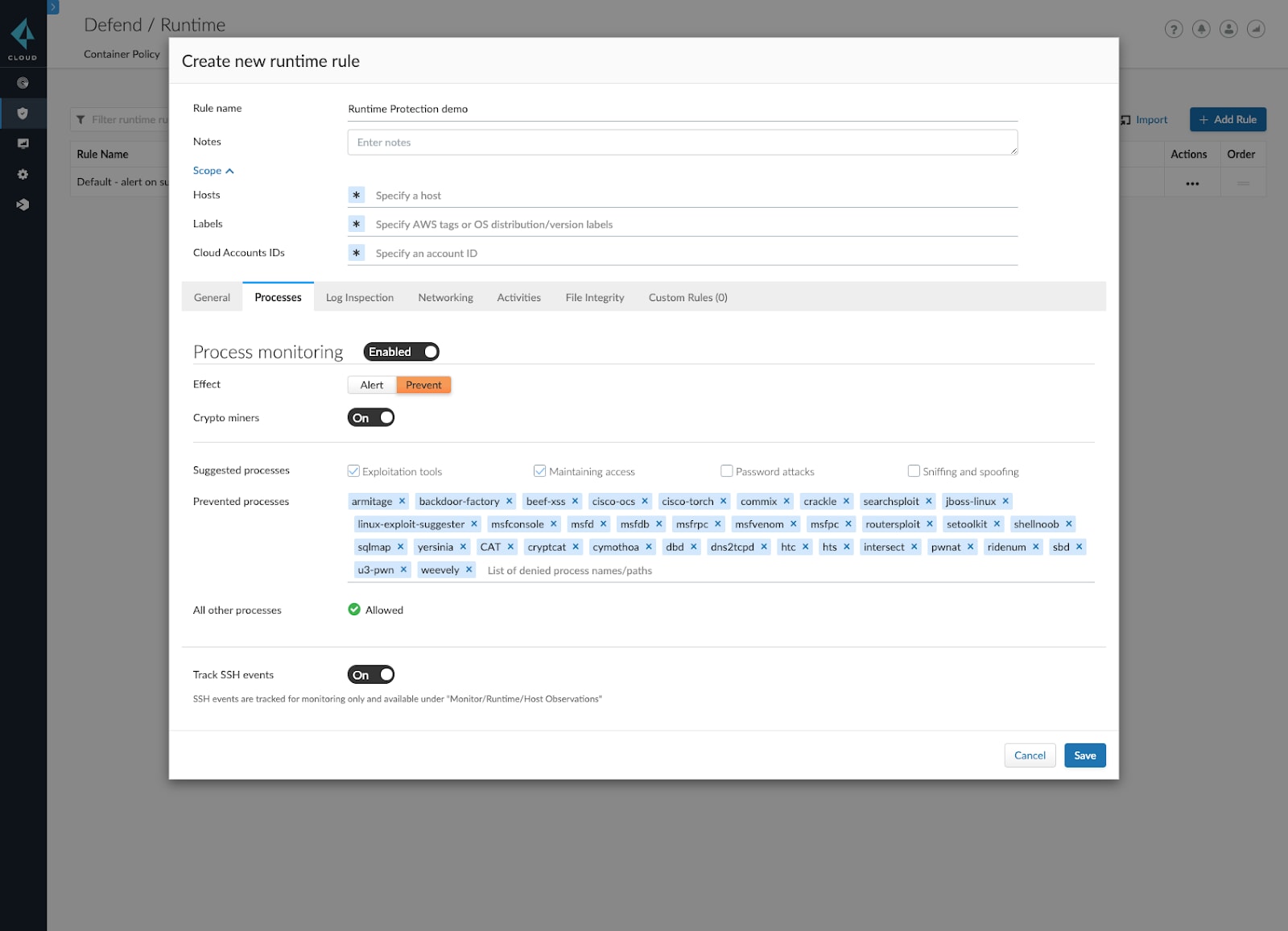
Prisma Cloud now gives users the ability to:
- View SSH events and SSH commands being run in interactive sessions.
- See pending security updates for Ubuntu and Debian OS, based on updated compliance checks.
- View running apps with process, outgoing ports and listing ports details.
- View host incidents, including cryptominers, malware downloaded, suspicious executable and linkable format (ELF) headers and execution flow hijack attempts.
- Set runtime rules based on Amazon Web Services (AWS) tags, OS distribution and version.
Robust Host Security Capabilities in Prisma Cloud
This new functionality is on top of an already robust set of host security capabilities in Prisma Cloud:
Vulnerability Management
Continuously monitor Linux and Windows hosts for vulnerabilities. Vulnerability Management provides risk prioritization through top 10 lists of known CVEs across any environment with unique risk scoring for each vulnerability. Additionally, Prisma Cloud identifies risk factors, such as vendor fix status and known exploit information.
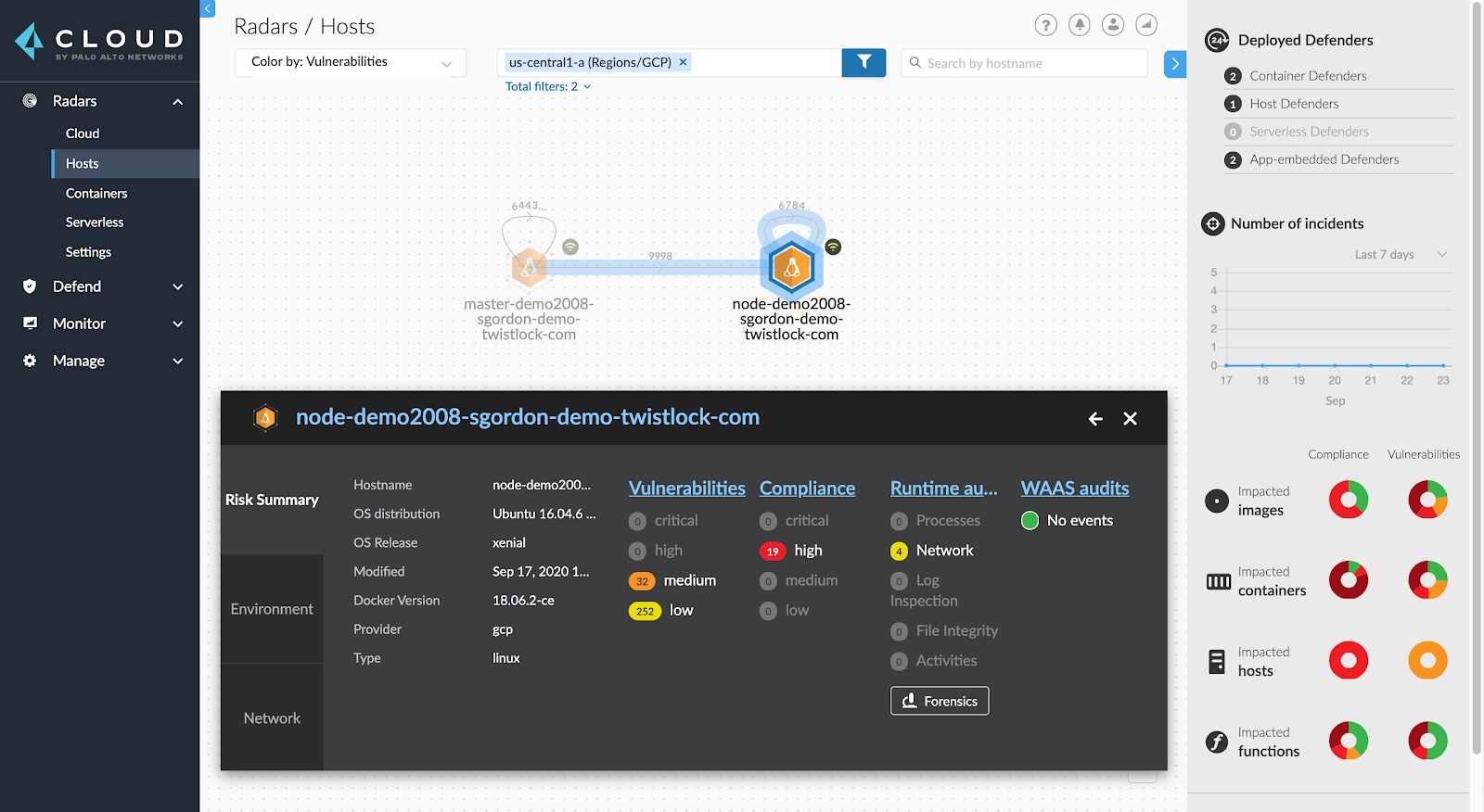
Compliance
Monitor and enforce pre-built security policy compliance checks with the Linux CIS Benchmark and Windows configuration checks, or implement custom compliance checks. Compliance dashboards surface data such as severity and issue description for hosts, containers and serverless.
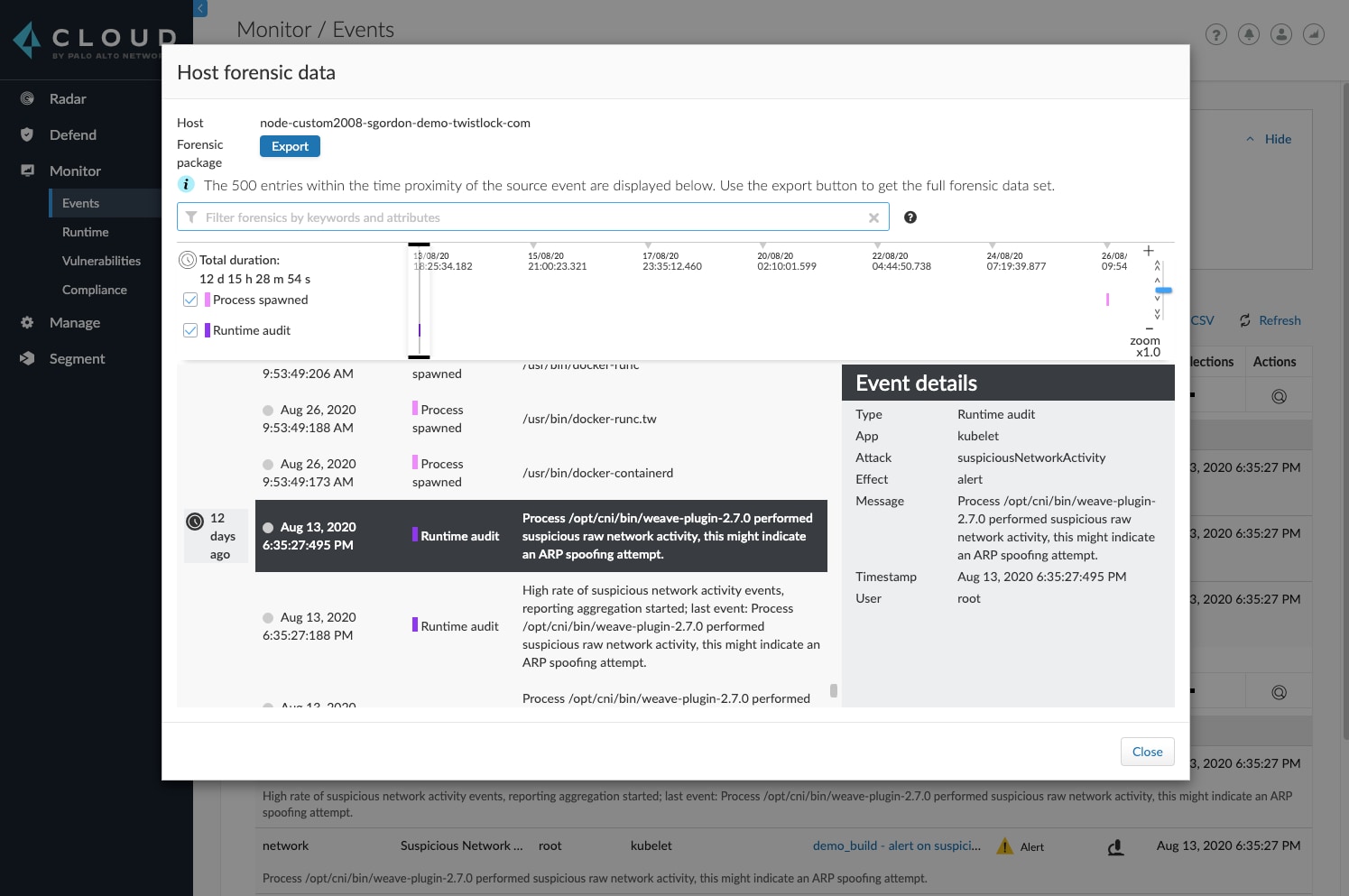
Runtime Protection, Including File Integrity Monitoring and Log Inspection
Prisma Cloud automatically profiles workload behavior to alert on or prevent anomalous and nefarious behavior. Integrated protection includes file and directory read/write changes, host log inspection and custom runtime rules language.
AMI Scanning
Scan Amazon Machine Images (AMIs) for vulnerabilities, just like a container repository, before VMs are deployed on AWS.
Conclusion
Unifying protection for hosts, containers and serverless architectures is a central requirement for Cloud Workload Protection (CWPP). With this latest update for enhanced runtime security, teams get a single solution for broad host security alongside existing capabilities for containers and serverless.
To learn more about requirements for CWPP, download the 2020 Gartner Market Guide for Cloud Workload Protection.