More data leaked or was stolen during the month of January 2021 than there was during the entire year of 2017. This may not come as a surprise, as the amount of data stored on the web has also grown exponentially during those years. What should be alarming though, is that the volume of reported breaches has also grown by triple-digit percentages for several years. Meaning the number of breaches continues to grow, and those breaches are also increasing in severity.
To help our customers better protect their cloud data in the face of such growing risks, Prisma Cloud Data Security now allows users to scan data for public exposure, and scan for sensitive data within any publicly exposed data.
Let's take a look at how we are helping our customers tackle each of these use cases to prevent data breaches.
A Multifaceted Problem
After having many conversations with customers, we've found that data security challenges tend to fall into three categories: the sheer volume of data makes it difficult to gain a comprehensive view; the data itself is constantly changing; and the data is often shared among numerous external third parties.
Given these challenges, customers are faced with two common questions:
- Is any of my data publicly available?
- Does any of my publicly accessible data contain sensitive information?
The first question often comes from cloud-first organizations or hybrid-cloud organizations that use cloud storage as part of business operations. For these organizations, putting data in the cloud supports wider business needs such as scaling out projects or even for data protection reasons. So while these organizations have clear plans to put operational and/or sensitive information into the cloud, it is certainly not their intention to share this information beyond the organization.
The second question is frequently brought up by organizations that are knowingly sharing things like AWS S3 buckets with third-party vendors or customers, but are concerned about sensitive data within those buckets. For these organizations, day-to-day operations require that business data be stored on public buckets, but they do not expect those public buckets to contain any sensitive data.
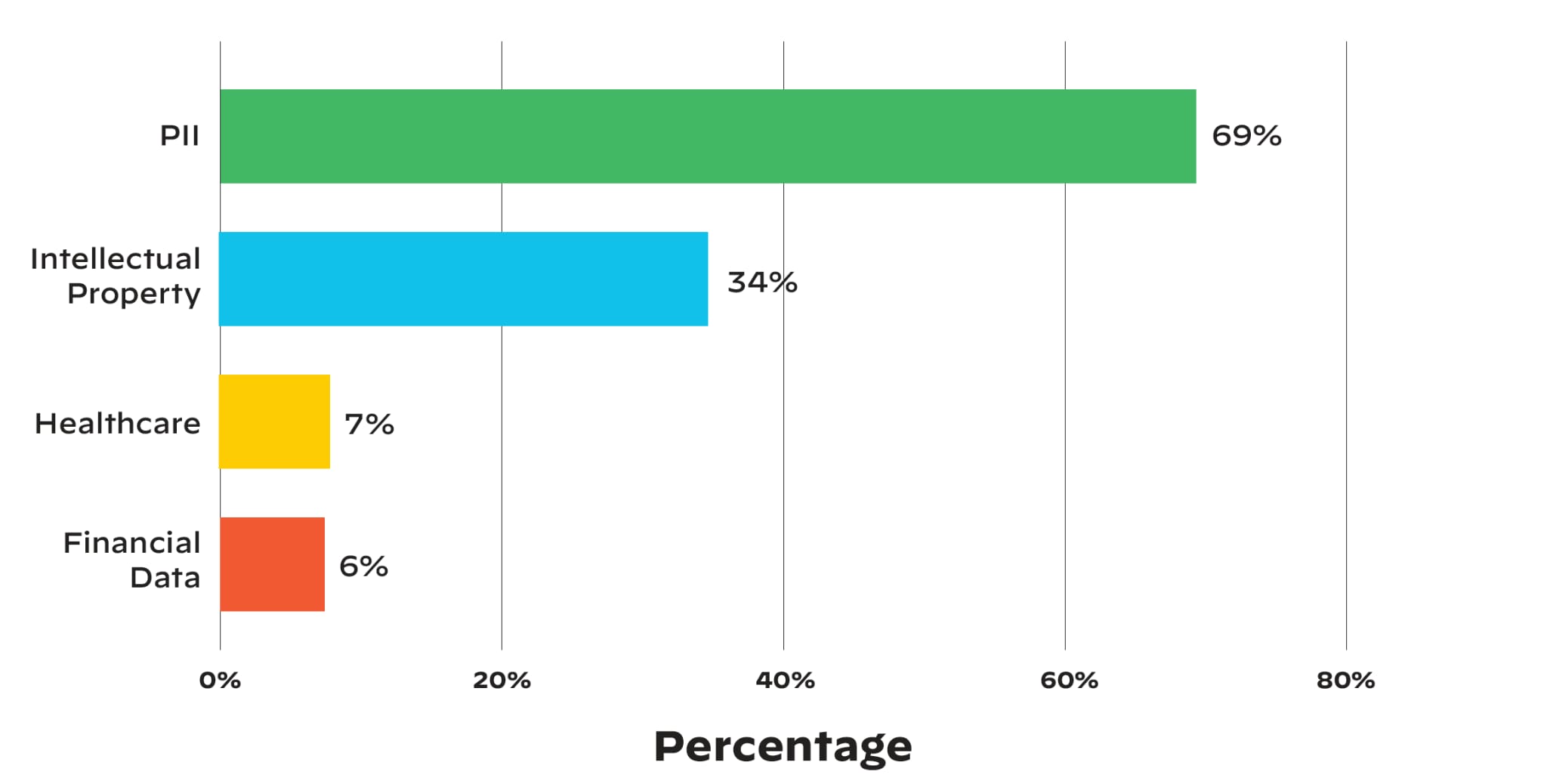
Unfortunately the answer much of the time is that data is publicly exposed, and it contains sensitive information. Recently, the Unit 42 Cloud Threat Research team found that 35% of businesses permit their cloud storage resources to be publicly accessible, and 30% of organizations with publicly accessible cloud data appear to be storing sensitive information (e.g., personally identifiable information, intellectual property, healthcare, and financial data).
How Prisma Cloud Helps
To help our customers with these two use cases, Prisma Cloud Data Security now provides two more options on top of the existing comprehensive scan: public exposure scanning and sensitive data scanning on publicly exposed data.
Scanning for Public Exposure
The feature lets customers scan all objects within selected S3 buckets and shows the status of each object, providing security teams with a baseline for their data-exposure landscape.
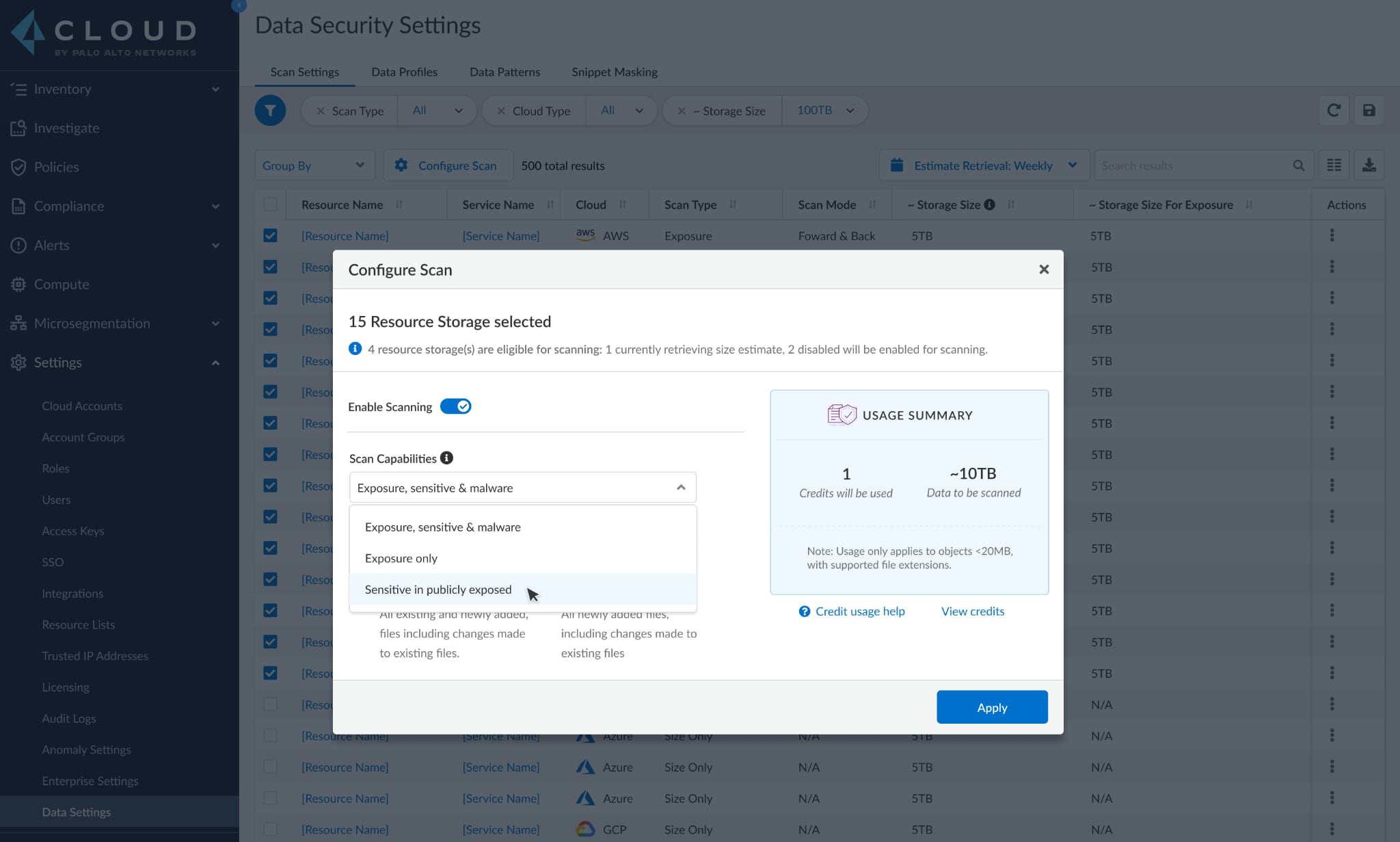
Scanning for Sensitive Information in Publicly Exposed Data
This offers an object-level approach by performing a two-pass scan. First, for all selected buckets, the objects within are scanned for public exposure. Then, the publicly exposed objects will be scanned again for sensitive data such as financial information, health information, or personally identifiable information (PII).
With these options, security teams are now able to focus on other high-impact tasks by reducing the time and energy spent on scanning. A second, useful benefit is the reduced cost of scanning that comes as a result of being able to narrow efforts to only publicly exposed buckets.
Begin Using the New Scanning Features
These two new additional scan capabilities will be available in the coming quarter.
In the meantime, you can learn about operationalizing other CSPM strategies in our white paper, Guide to CSPM Tools.