In cloud-native development, managing security across every phase of the development lifecycle is critical. Whether working with Docker files, identity systems, microservices or serverless functions, each component presents security risks that must be addressed early.
Implementing code to cloud security ensures that every stage of development, from build to runtime, receives the necessary protection. The imperative is to mitigate risks that could otherwise lead to vulnerabilities post-release.
Navigating Key Security Tools
The journey begins with cloud security posture management (CSPM) and progresses to more comprehensive solutions like the cloud-native application protection platform (CNAPP). Other critical tools include:
- CIEM (cloud infrastructure entitlement management)
- DSPM (data security posture management)
- KSPM (Kubernetes security posture management)
- CDR (cloud detection and response)
- CWP (cloud workload protection)
While these tools integrate security into every stage of cloud-native applications, questions remain. Who’s responsible for shifting security left? Is it the domain of DevOps, SecOps or CloudOps?
Identifying Security Challenges in Cloud Deployments
Consider a containerized application deployed on a managed Kubernetes infrastructure through a cloud provider like AWS, Azure or Google Cloud. Developers traditionally focus on meeting functionality deadlines, often overlooking security until the testing or production phase. When vulnerabilities emerge at these late stages, fixing them becomes complicated, as microservices lack on-the-fly patching capabilities.
CloudOps teams address these issues by leveraging tools like CSPM, CWP and CDR. Developers adopt practices involving:
- IaC Scanning (infrastructure as code)
- SCA (software composition analysis)
- SAST (static application security testing)
These tools allow teams to detect security gaps early. The challenge lies in aligning them across teams — making a strong case for shifting security left.
Shielding Left and Right
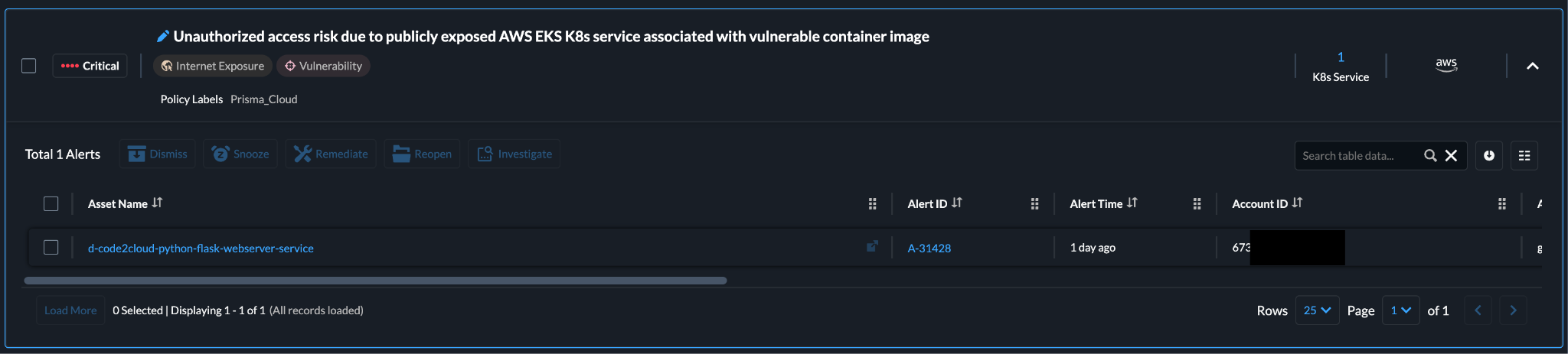
Figure 2 illustrates a containerized application running on an Amazon EKS cluster, exposing a service to the internet. The development team ensured security throughout the build process, shifting security left. After deploying the service, cloud security tools monitored for anomalies and zero-day vulnerabilities — a practice known as shielding right.
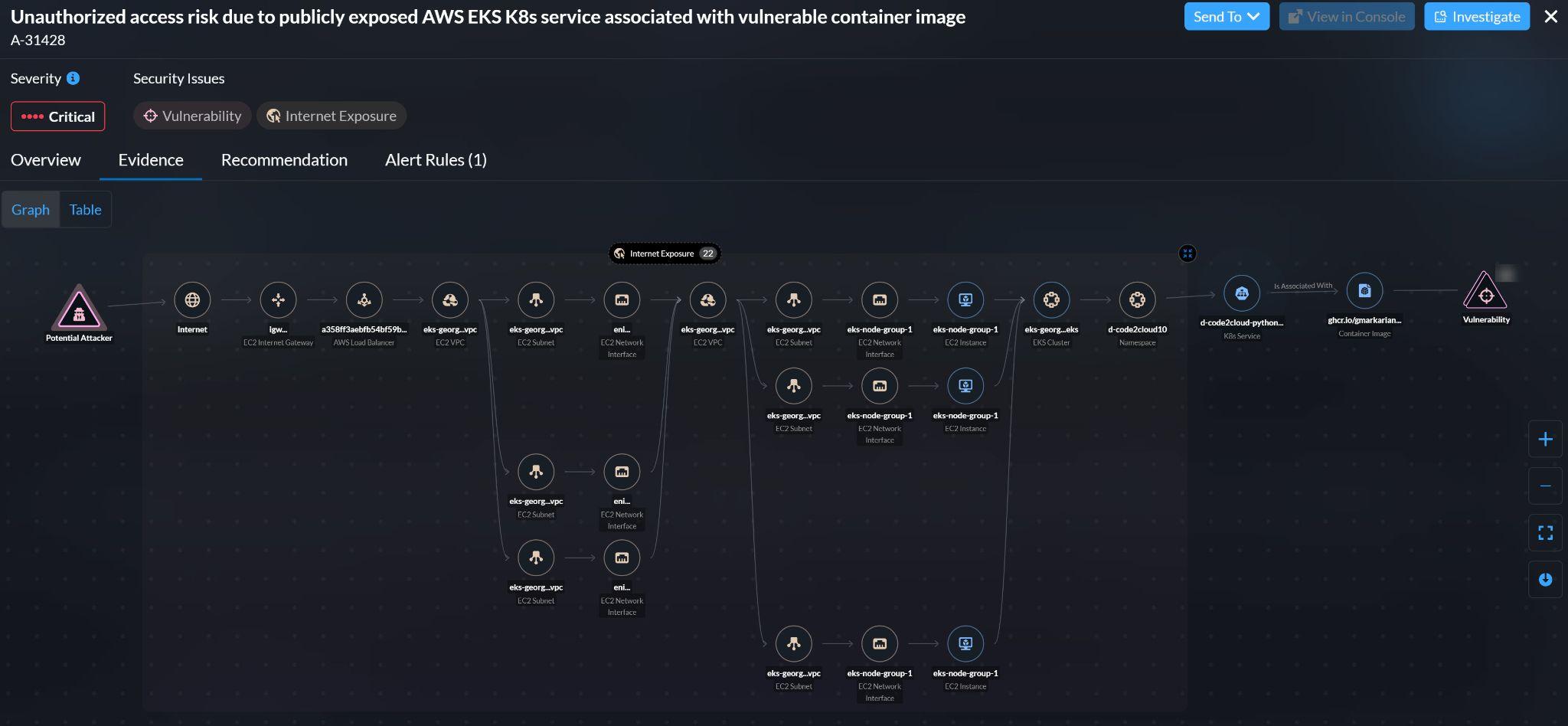
Despite the precautions, a zero-day vulnerability emerged in production, exposing an endpoint to unauthorized access. Whether using agentless or agent-based approaches, the security team identified the attack path. The publicly exposed service was linked to a vulnerable package in the container image.
The discovery raises several pivotal questions:
- Is the service publicly accessible?
- Is the vulnerability already exploitable?
- Is a patch available?
- Which packages are impacted?
- Who relies on those packages?
- What version resolves the issue?
- How can the solution be communicated?
- What steps are required to apply the fix?
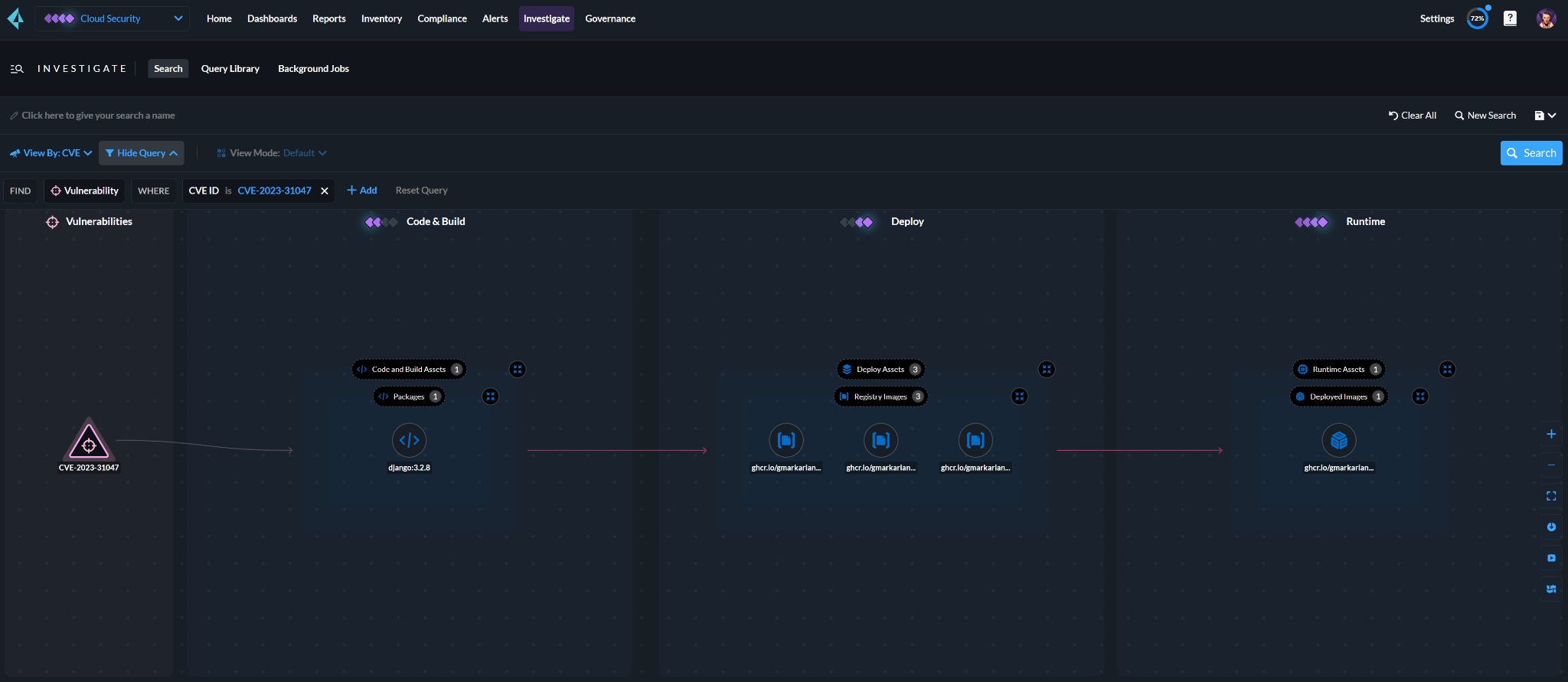
Answering These Questions with Cloud to CodeTM Visibility
With a single, integrated platform, security teams gain visibility across the entire software development lifecycle (SDLC). For example, questions about exposure and exploitability are resolved quickly.
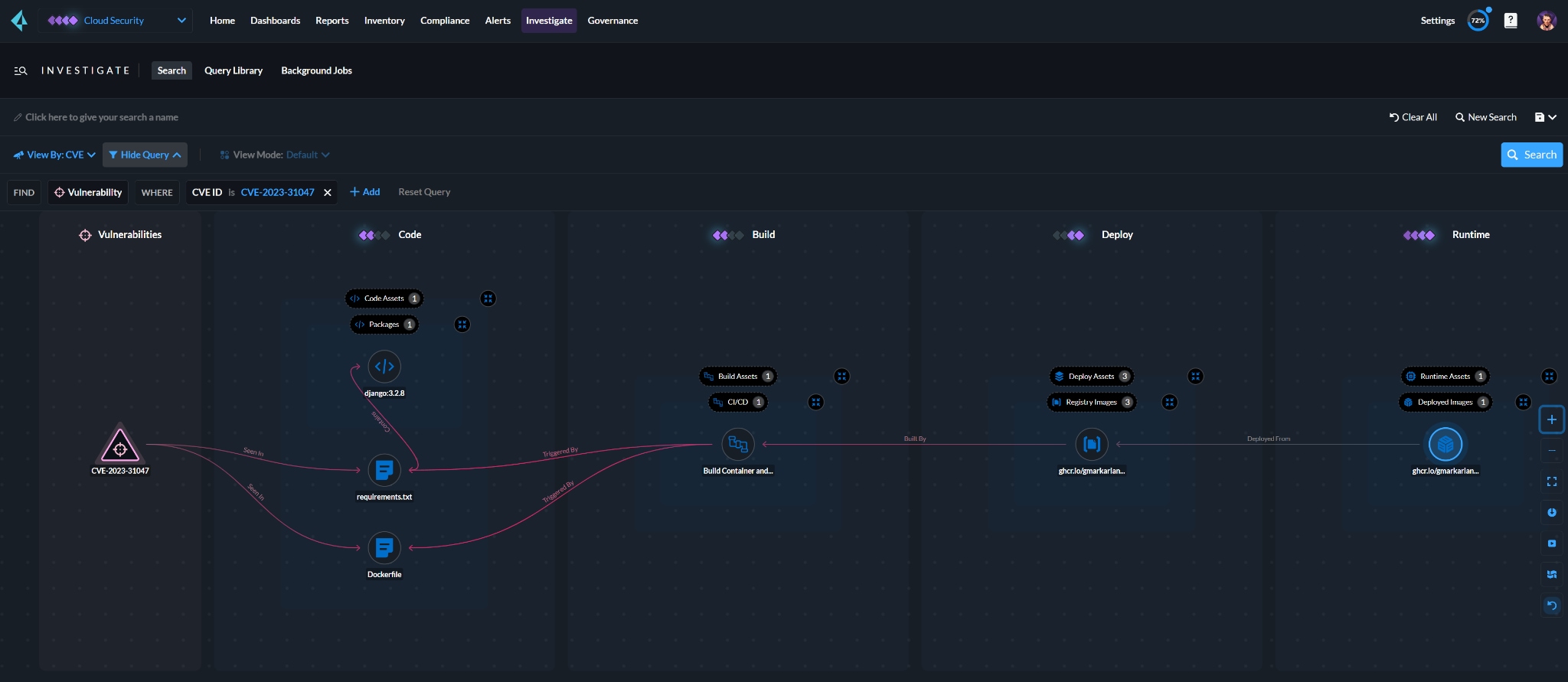
By prioritizing business-critical applications, teams can map cloud to code vulnerability traces. The method answers package-related questions and identifies dependencies, allowing for efficient remediation.
A deeper dive into the Docker file reveals that a Python dependency caused the issue. The platform pinpoints the exact repository, owner and the required version to resolve the problem.
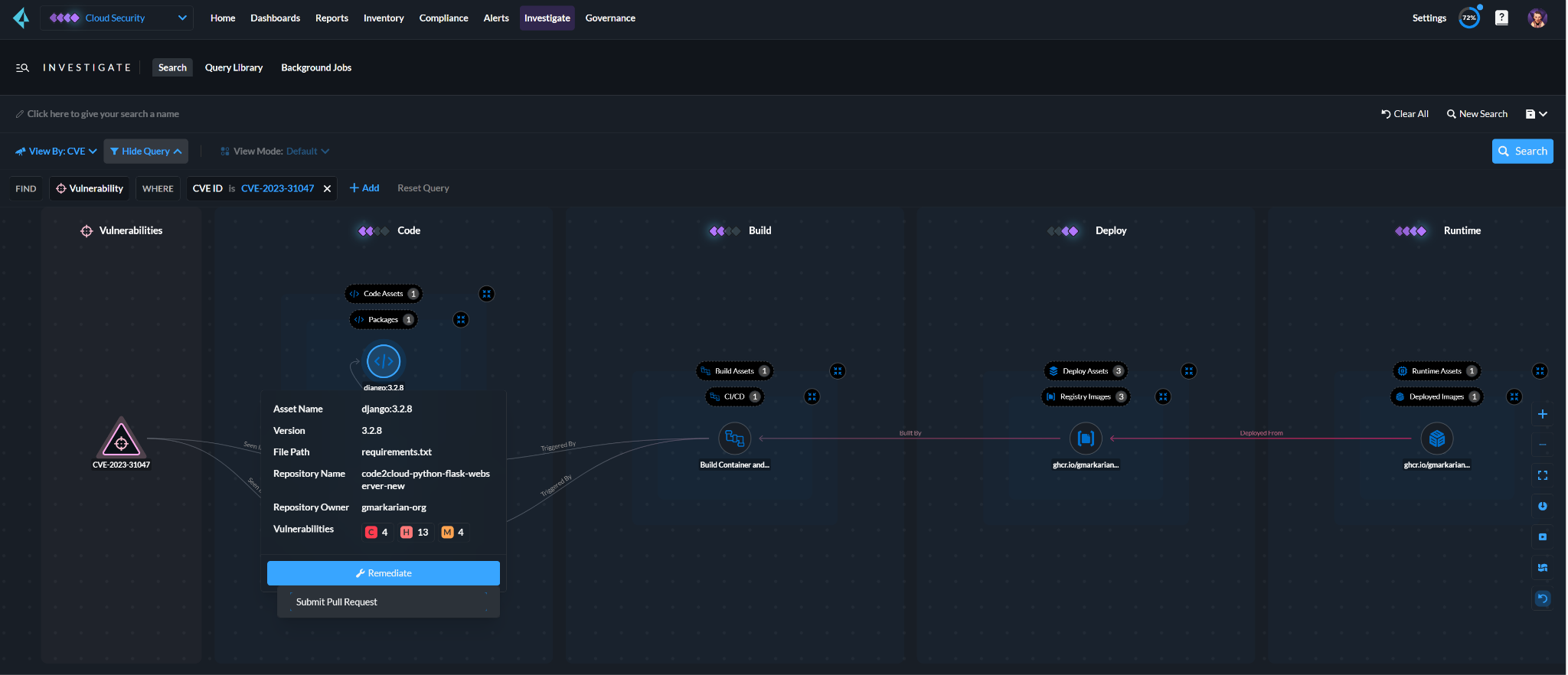
Streamlining Developer Communication
To fix the vulnerability, security teams submit a pull request to the developer responsible for the affected code. By avoiding disruptions or unnecessary meetings, this approach respects the developer’s workflow. "Pulling security left" ensures that security fixes integrate smoothly into the development process.
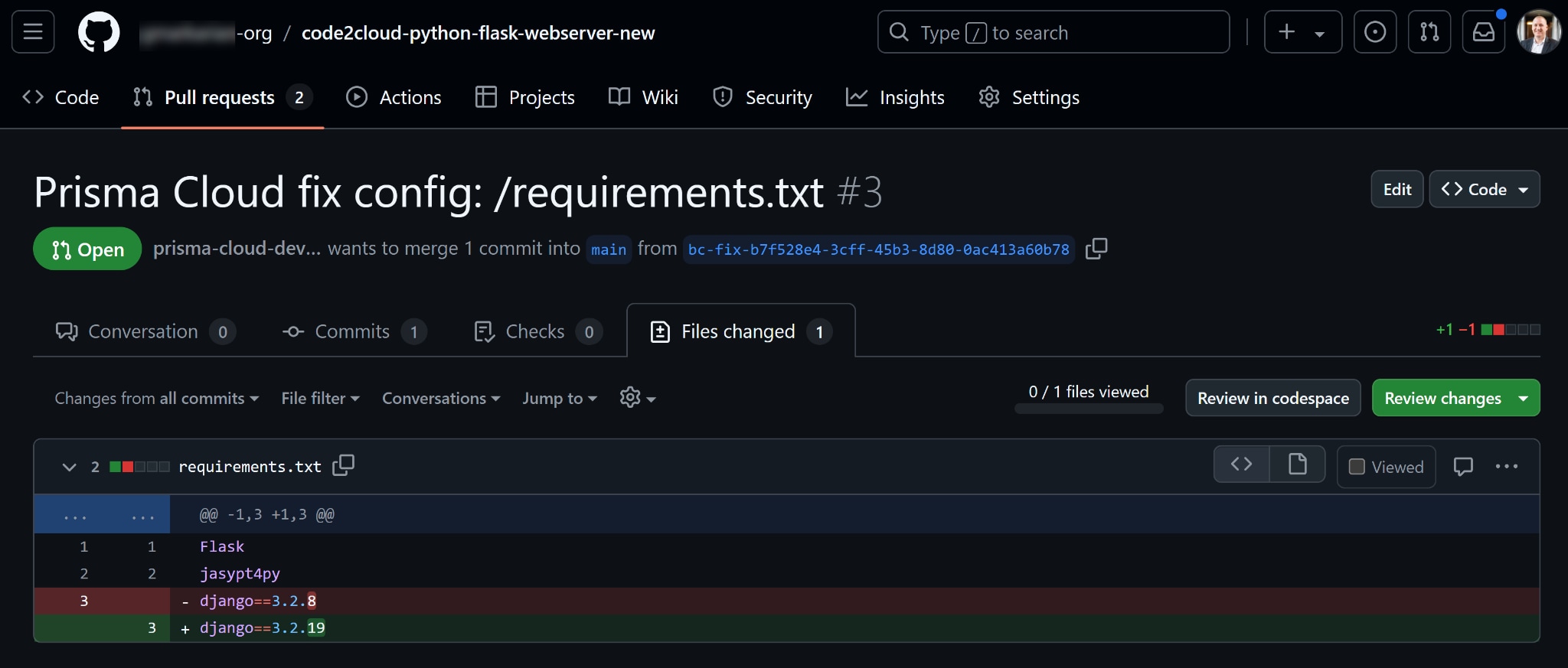
The Case for a Unified Security Platform
Using a unified security platform provides several advantages:
- Full visibility across the SDLC
- Tools for developers to prevent issues early
- Production security monitoring to detect vulnerabilities post-release
- Streamlined communication between security and development teams
Learn More
Prisma Cloud by Palo Alto Networks offers a solution that aligns with these goals. It boosts security outcomes, enhances developer productivity and encourages better collaboration across teams.
If you haven’t tried our Code to Cloud platform, we invite you to experience best-in-class security with a free 30-day Prisma Cloud trial.