The United States Department of Defense (DoD) was an early adopter of containerized technologies, and it continues its rapid adoption of microservices in all environments. As part of that adoption and other overall cyber initiatives, the Defense Information Systems Agency (DISA), a DoD agency, collaborates with private industry to create Security Technical Implementation Guides (STIGs). These STIGs provide the DoD and other federal agencies with operational configuration guidance to harden computer systems and protect cyberinfrastructure that might otherwise be vulnerable to malicious computer attacks.
Recently, DISA collaborated with Docker, the container platform, to create the Docker Enterprise 2.x Linux/UNIX STIG. The purpose of this STIG is to provide guidance for securing Docker and the supporting Linux and UNIX-based operating systems.
We’re excited to announce that Prisma Cloud now supports the Docker DISA STIG compliance template, allowing users to monitor adherence to its specific policies.
DISA STIG Compliance Template
The Prisma Cloud Compliance Explorer monitors and helps enforce industry standards, best practices and security compliance benchmarks to your organization’s hosts, containers and serverless environments.
We have curated the checks within the Docker Enterprise 2.x Linux/UNIX STIG into a “DISA STIG” compliance template. When you create a new compliance policy and select the DISA STIG compliance template, you will automatically receive alerts based on the checks aligned with the STIG. You can then further modify your compliance policy to meet your organization’s requirements.
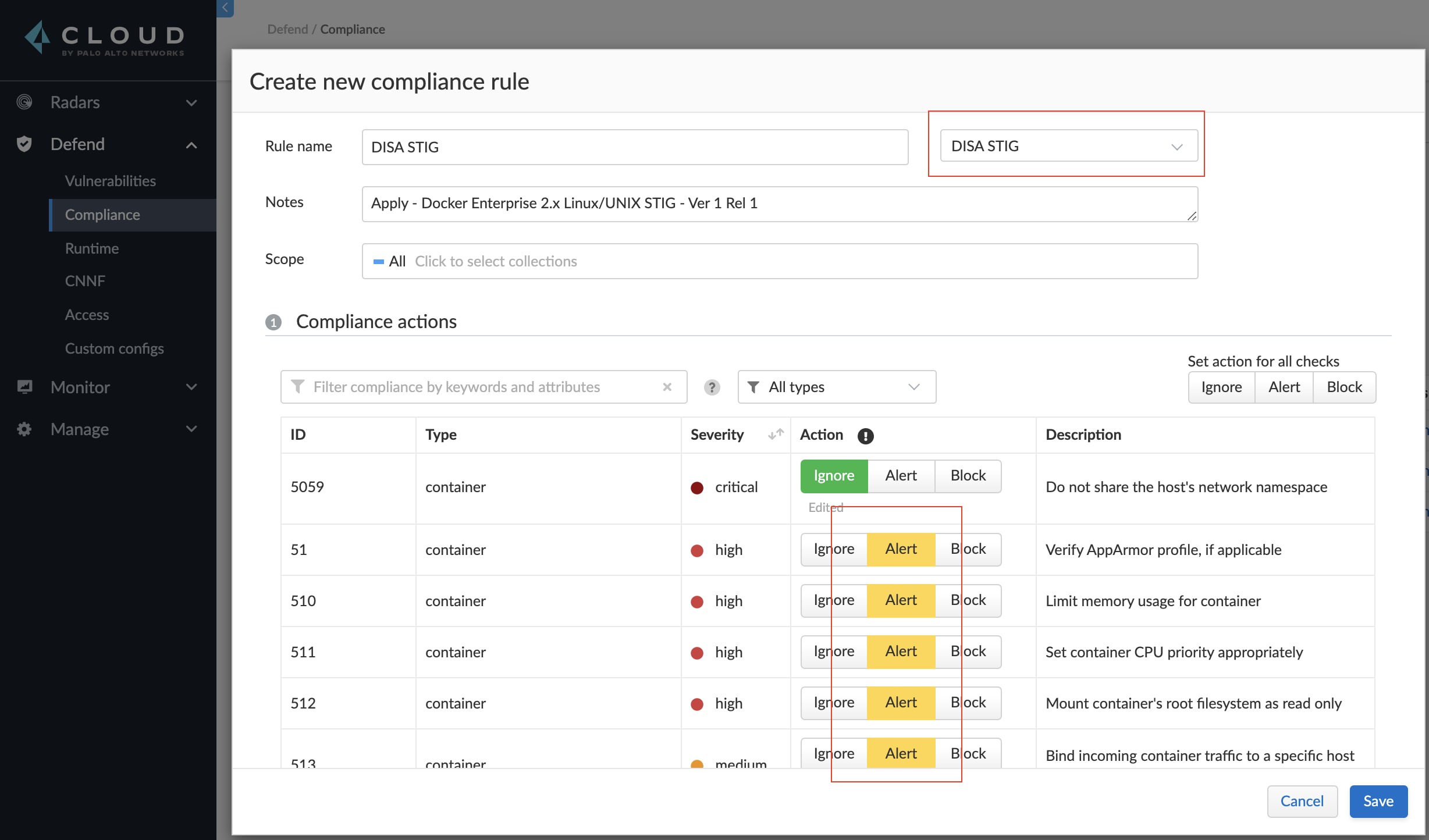
We've added eight new compliance checks specifically for the DISA STIG template, in addition to 49 existing checks that already align with it. The remaining 43 STIG checks are not applicable. For example, STIG ID: DKER-EE-002180, SAML integration, must be enabled in Docker Enterprise. The complete mapping of the STIG rules to the Prisma Cloud Compute compliance rules can be found in our technical documentation.
How Compliance Checks Work
Prisma Cloud DISA STIG compliance checks can be applied to images, containers, and hosts. The template is available in the following compliance policies.
Images
Prisma Cloud will scan images as they are being built by developers. You can stop the development workflow of an image that does not comply with the DISA STIG. Following the example below, you can set Prisma Cloud to fail a Jenkins pipeline build of an image that does not define a USER command.
| STIG ID | Rule Title | Compute Check # | STIG Severity | Compute Severity |
| DKER-EE-003200 | Docker Enterprise images must be built with the USER instruction to prevent containers from running as root. | 41 | CAT II | High |
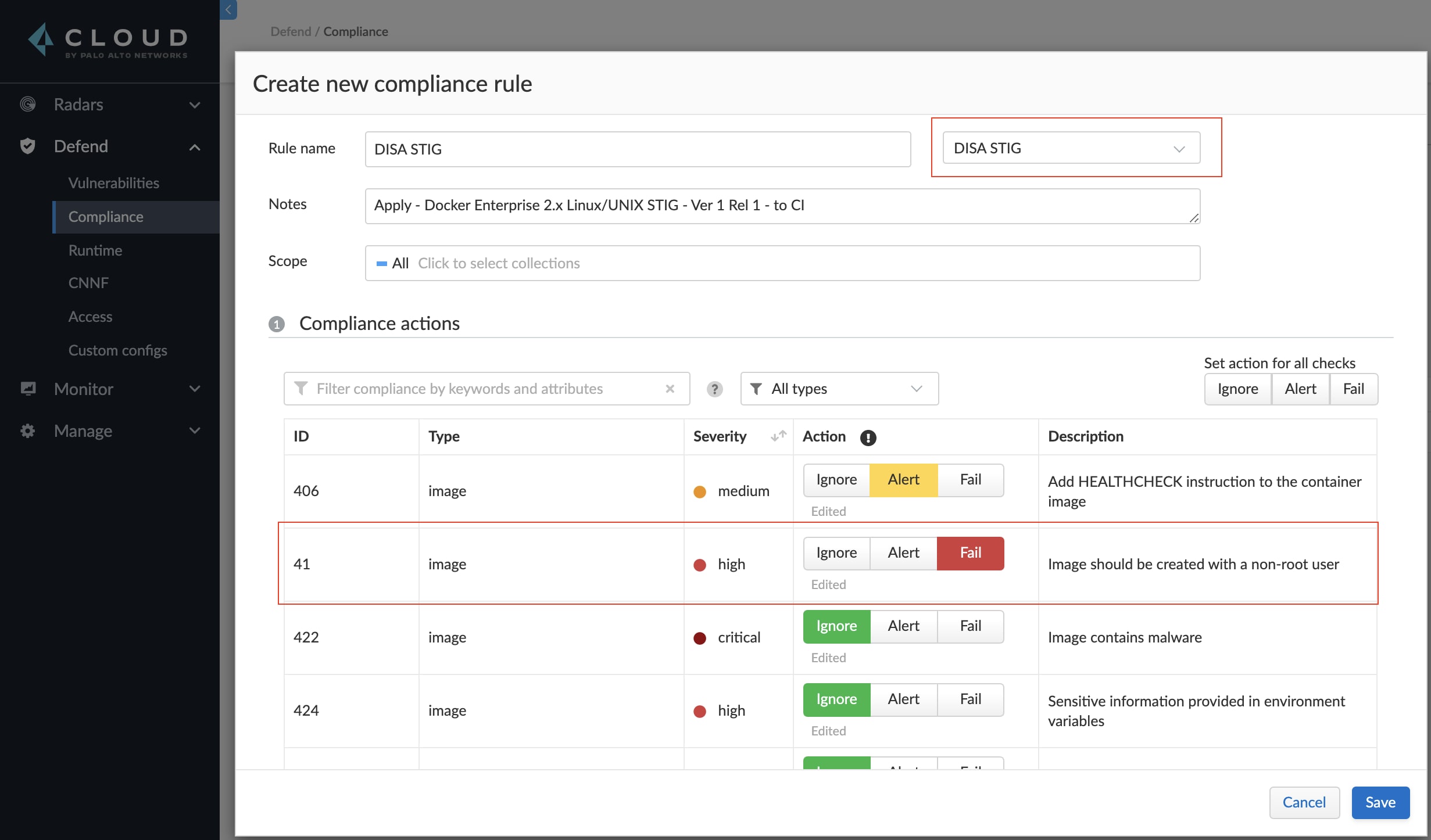
Step 1
Create a new policy in Manage > Compliance > Containers and images > CI, then apply the DISA STIG template and modify rule #41 from Alert to Fail.
Step 2
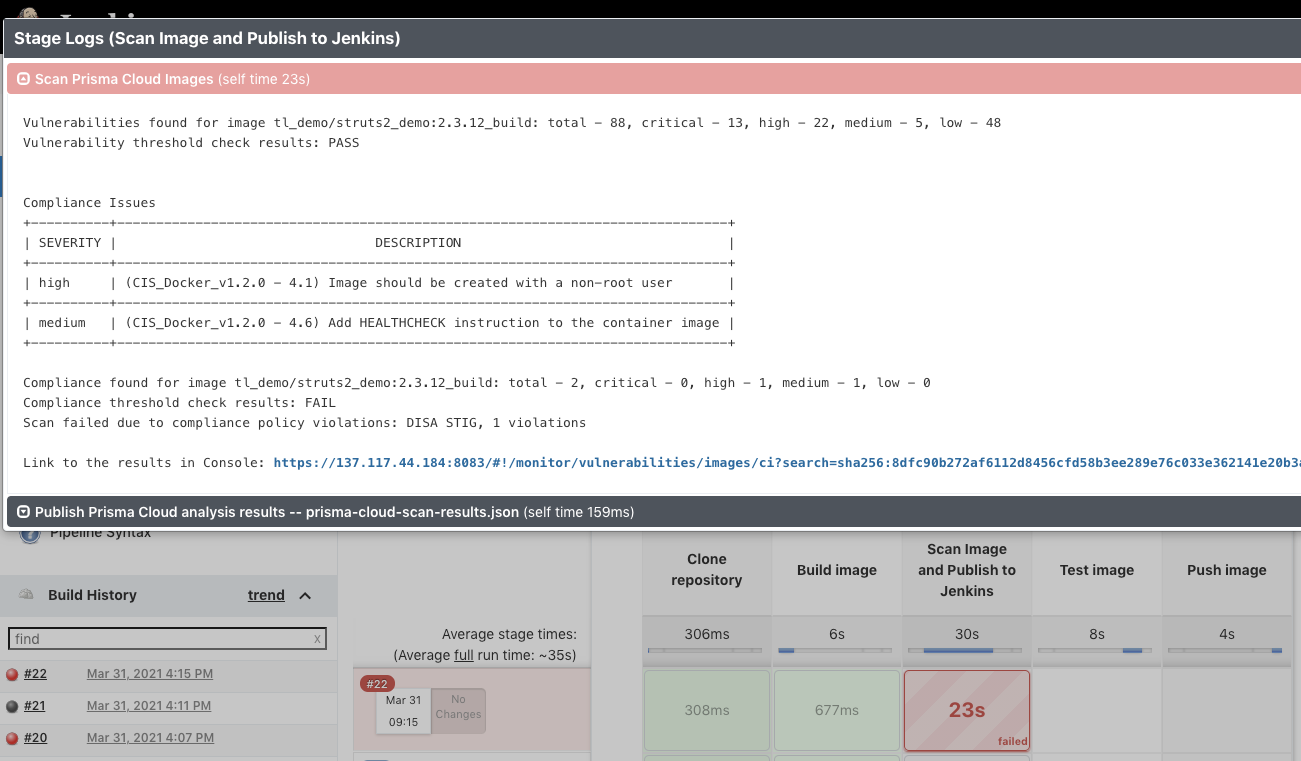
Then, integrate vulnerability and compliance scanning into the Jenkins environment and pipeline. The pipeline run will fail, and the developer will be notified as to why. It will appear in Jenkins:
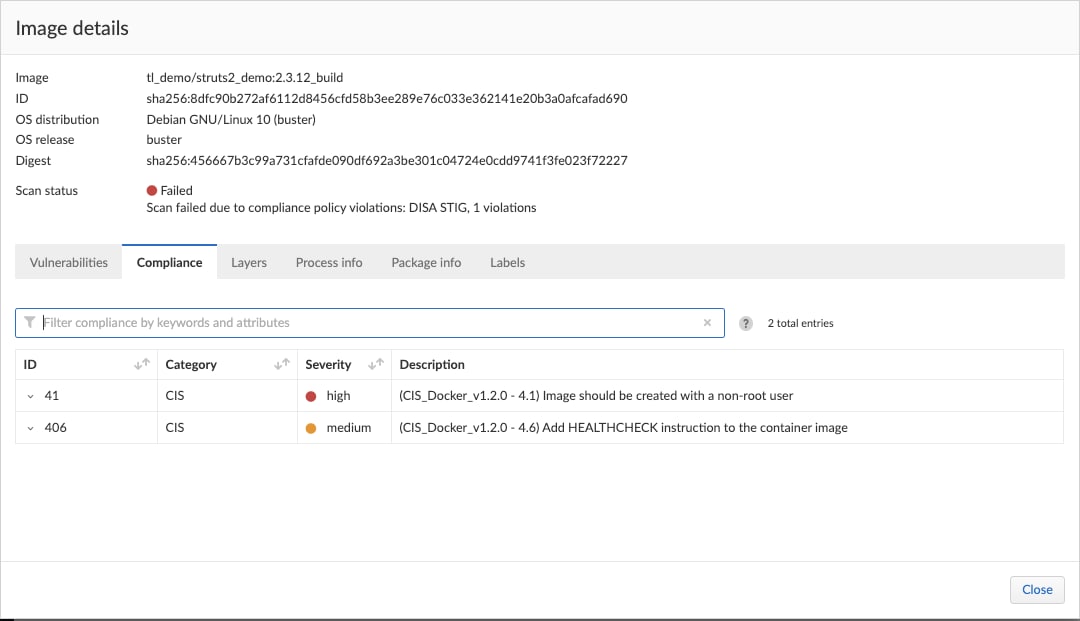
And within the Console’s Monitor > Compliance > Images > CI:
Containers
Next in the life of an application, Prisma Cloud will scan images and containers that are found on running nodes and stored in registries. Here is how to create an error alert for containers.
Step 1
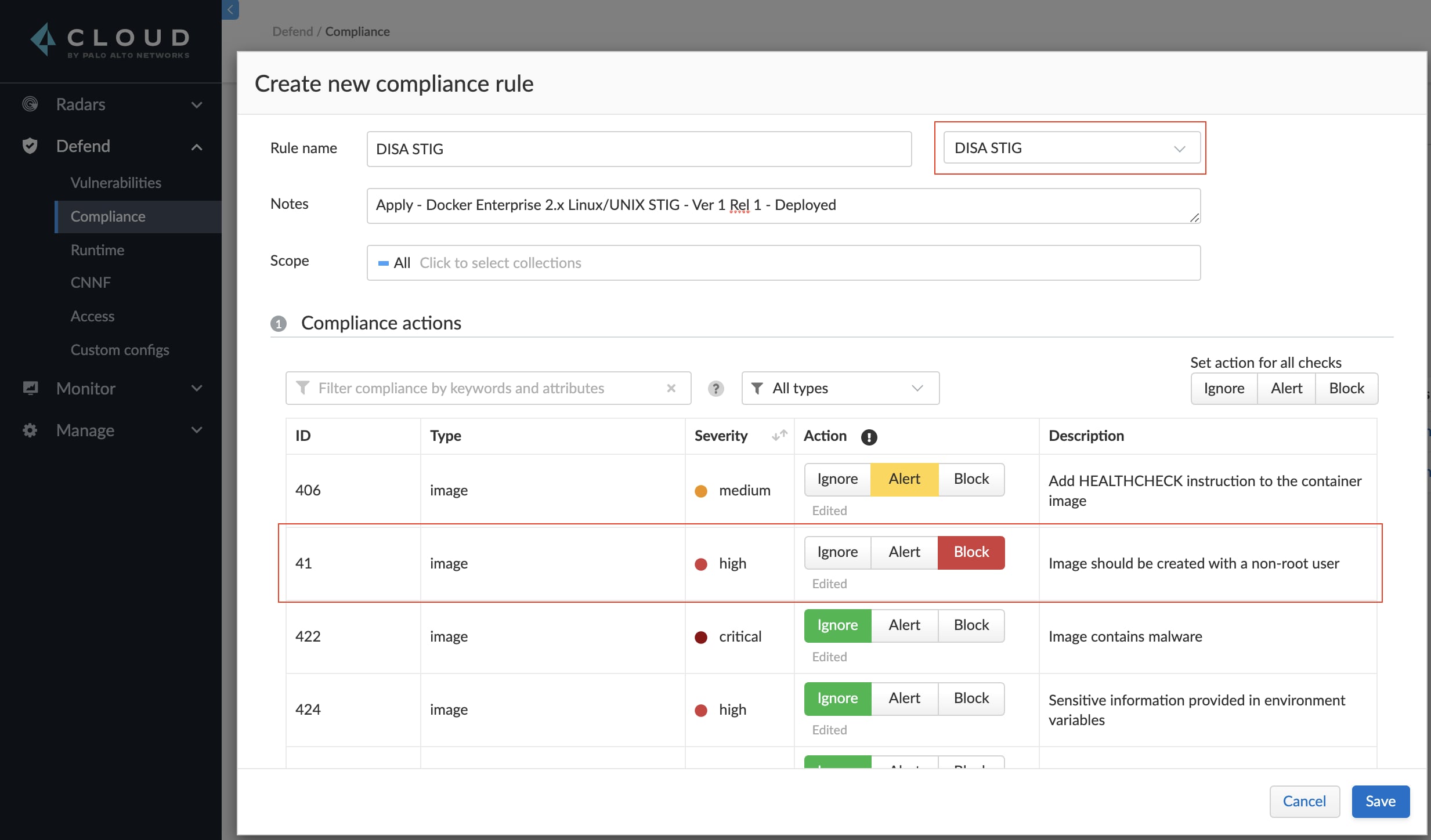
Create a new compliance rule in Manage > Compliance > Containers and images > Deployed and use the DISA STIG template to set the associated checks to alert.
Step 2
Change rule 41 to block, which will halt a non-DISA STIG compliant image from launching as a container.
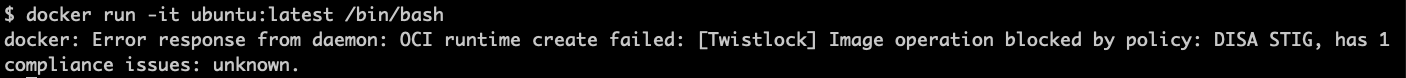
If someone tries to run the image as a container, an error appears:
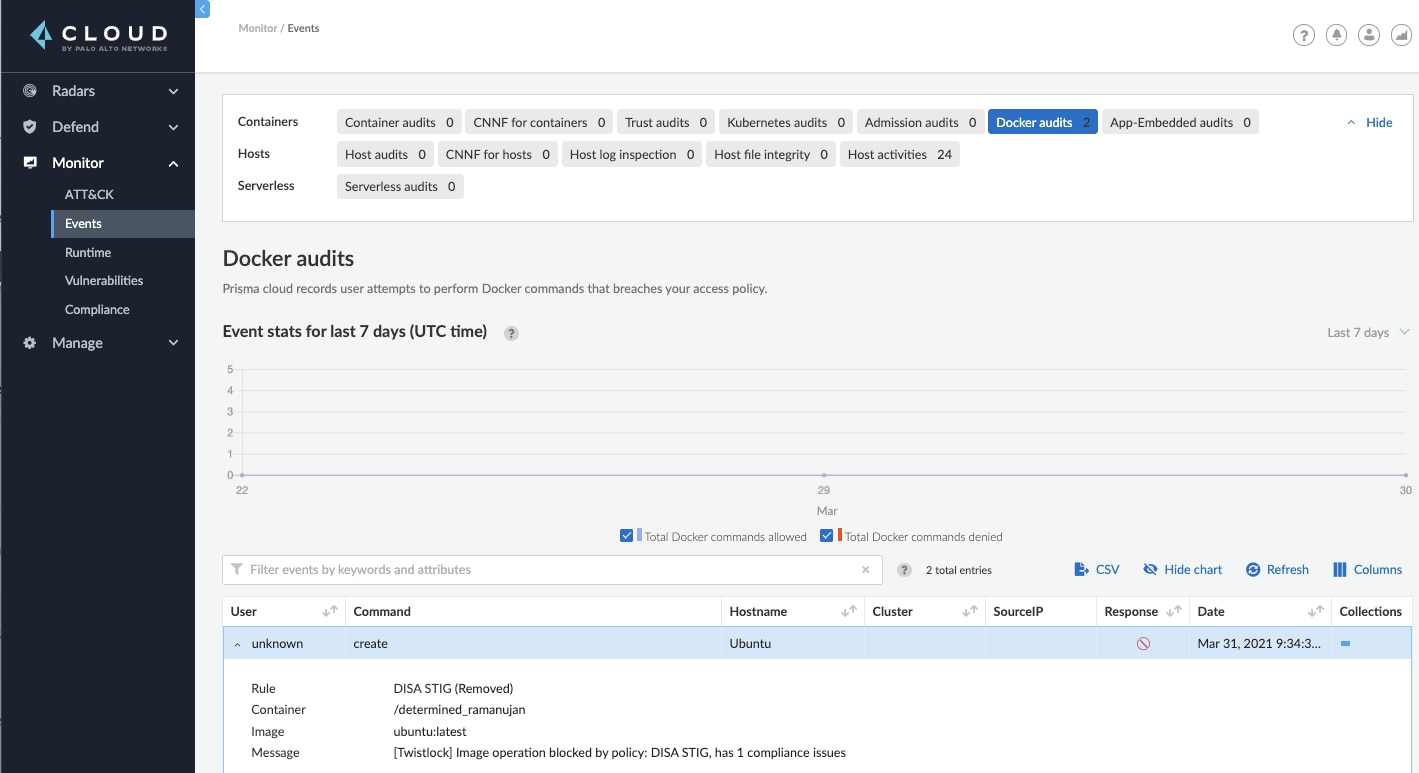
Step 3
You can view the event logs within Monitor > Events > Docker audits.
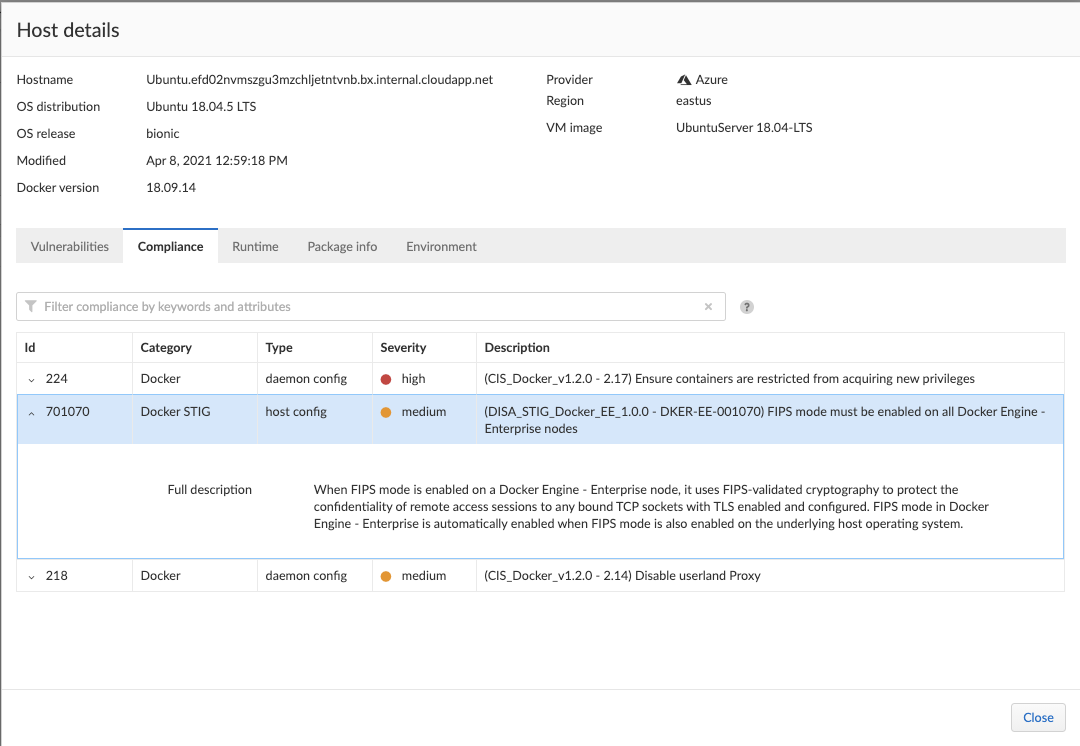
Hosts
Prisma Cloud will also scan for host misconfigurations. Securing the hosts where containers run is paramount. One of the new compliance checks we added to Prisma Cloud is the ever "favorite" Federal Information Processing Standards (FIPS) enablement.
| STIG ID | Rule Title | Compute Check # | STIG Severity | Compute Severity |
| DKER-EE-001070 | FIPS mode must be enabled on all Docker Engine - Enterprise nodes. | 701070 | CAT I | Medium |
Step 1
Create a new compliance rule in Manage > Compliance > Hosts and use the DISA STIG template to set the associated checks to alert. Note the new check 701070, FIPS mode must be enabled on all Docker Engine - Enterprise nodes, which correlates to STIG ID: DKER-EE-001070.
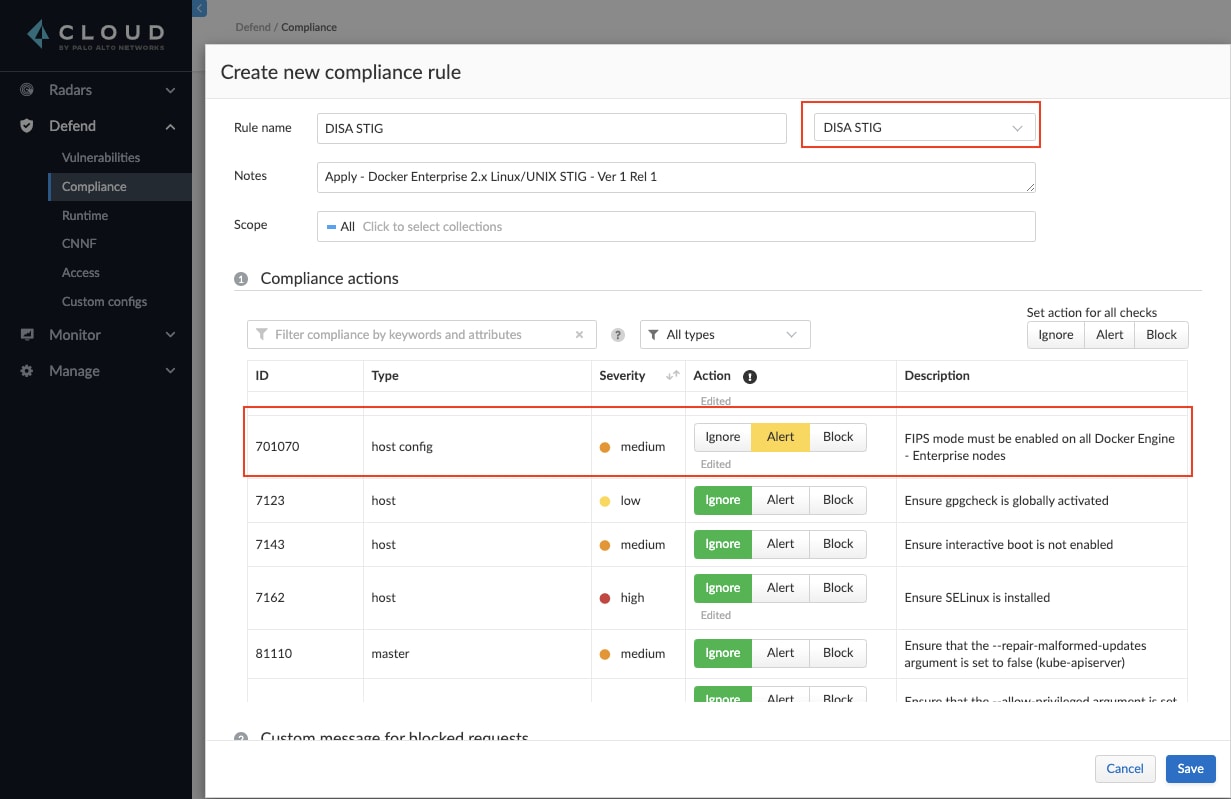
Remember, this STIG is for Docker Enterprise Edition and is required to perform the FIPS enablement check.
Conclusion
Palo Alto Networks has been – and will continue to be – a committed partner with our public sector customers. We know you operate highly regulated and controlled environments, and that new regulatory guidance is continually developed and published – as is the case with the DISA Docker Enterprise 2.x Linux/UNIX STIG. The Prisma Cloud DISA STIG compliance template enables public sector customers to quickly assess and control their microservice environments based upon this guidance.
You can download the Docker Enterprise 2.x Linux/UNIX STIG directly from DISA’s site for more information. Or if you are not yet a customer, you can sign up for a personalized demo of Prisma Cloud to see the compliance functionality in action.