One major use case for cloud security posture management (CSPM) tools is to reduce risk by remediating or alerting on resource misconfigurations. While some tools offer visibility into these misconfigurations, they lack nuance needed to assess risks, resulting in more false positives and generally increasing the total number of alerts. Security teams need an approach that helps them understand over-exposed cloud networks – not just a list of misconfigured resources.
True Internet Exposure in Prisma Cloud solves this issue by mapping all possible network paths to, from or across cloud resources, and assessing total risks around internet exposure before generating an alert. This provides greater visibility for users while reducing alert noise.
I’ll highlight the problems with existing cloud network configuration management and show how Prisma Cloud can help.
Why Cloud Network Configuration Management is Important
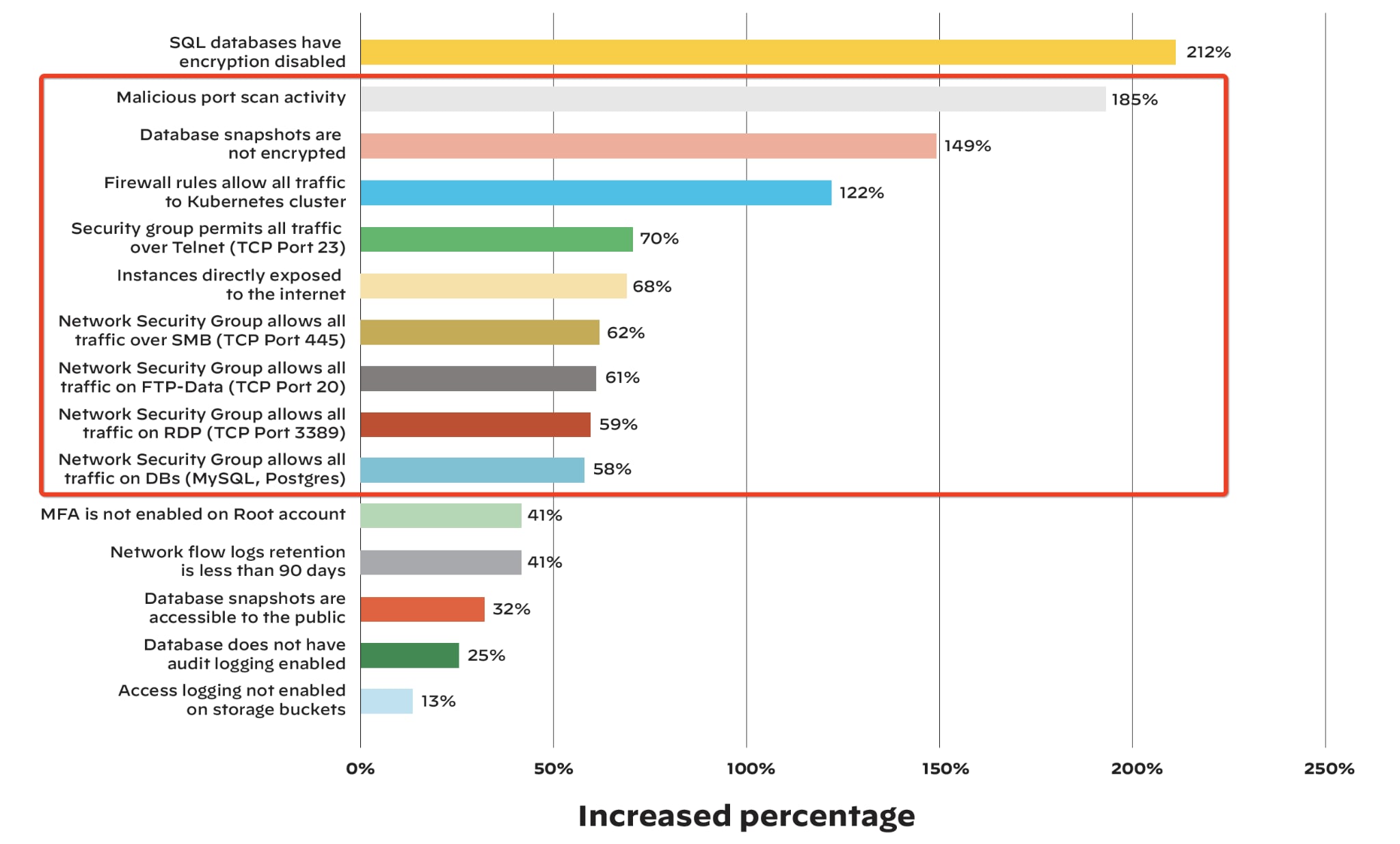
Cloud workload adoption is growing, but security is not keeping up. In the 1H 2021 Unit 42 Cloud Threat Report, researchers found significant increases in a wide variety of security risks during the COVID-19 pandemic:
- Malicious port scan activity has increased by 185%
- A 122% increase in firewall configurations that allow all traffic to a Kubernetes cluster
- Internet exposed instances have increased by 68%
- As much as 70% increase in insecure security group configurations allowing all traffic to specific ports (e.g., allow 0.0.0.0/0 to tcp 23, 20, 445, 3389)
Cloud service providers (CSPs) offer built-in network security controls which help limit the exposure of cloud resources; however, it is the organization’s responsibility to properly configure those tools in order to reduce risk. Enterprises are turning to CSPM tools to augment these capabilities and gain visibility into cloud network misconfigurations and maintain hygiene.
What Most Cloud Security Posture Management Tools Are Missing
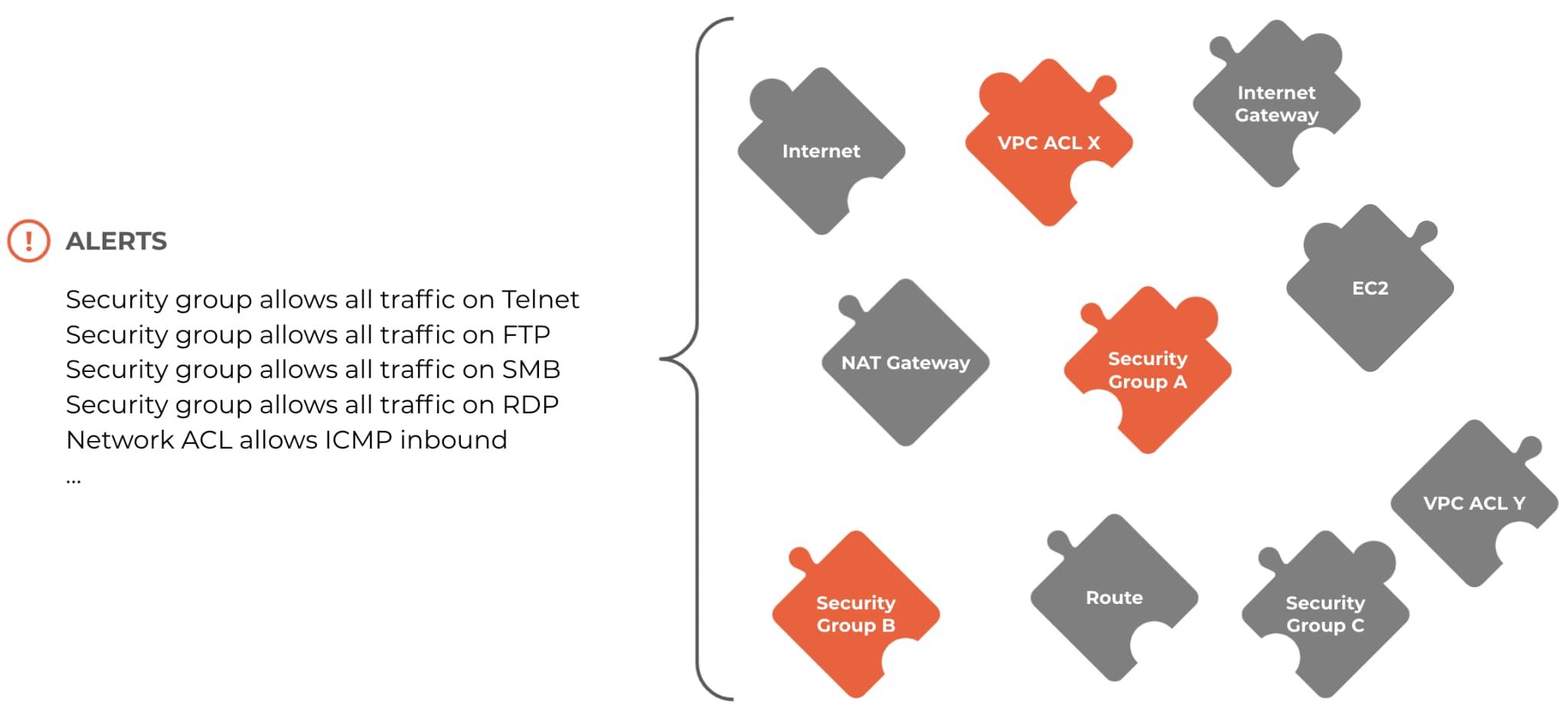
CSPM tools can offer visibility into hundreds, thousands or even millions of cloud resources, and security teams get an alert when even one of them is misconfigured or out of compliance. For example, if a security group is overly permissive or a native cloud firewall allows all traffic to SSH, then an alert is generated. The problem with most CSPM tools is that they look for these individual fragmented configurations without consideration for the wider network. There are two challenges with this approach:
Incomplete risk profile
It’s no secret that networking is complex. Organizations maintain network resources such as virtual private cloud (VPC) subnets, route tables, gateways, access control lists (ACLs), security groups – the list goes on. So, while an overly permissive security group should be addressed, a basic misconfiguration alert does not provide context about the associated risk, or answer questions like:
-
- What compute resource(s) is attached to the insecure security group?
- Are my instances exposed to the internet and/or other cloud networks?
- What risk am I inheriting from a given misconfiguration?
Alert fatigue
Security teams then struggle to address misconfiguration incidents, as they are forced to examine each alert in order to gain the appropriate context. Oftentimes those alerts turn out to be false positives if the cloud network resources have no impact on other compute resources. For example, when an overly-permissive security group is not actually attached to any cloud VMs.
In this sense, maintaining good cloud hygiene is like putting together a puzzle. Each cloud resource or network connection is a puzzle piece, and mapping their relationships is like fitting pieces together to make a picture. As stated above though, current CSPM tools only provide visibility into network and resource misconfigurations – they only provide a list of which puzzle pieces don't seem to fit, they don't provide a box with the final picture on it for you to confirm.
But security teams need an approach that helps them understand overly exposed cloud workloads, not just a list of misconfigured security groups and ACLs. They need to be able to see the final picture on the box before adjusting any individual piece. Security teams need automation to build that picture of their network before being able to act on any single alert.
True Internet Exposure with Prisma Cloud
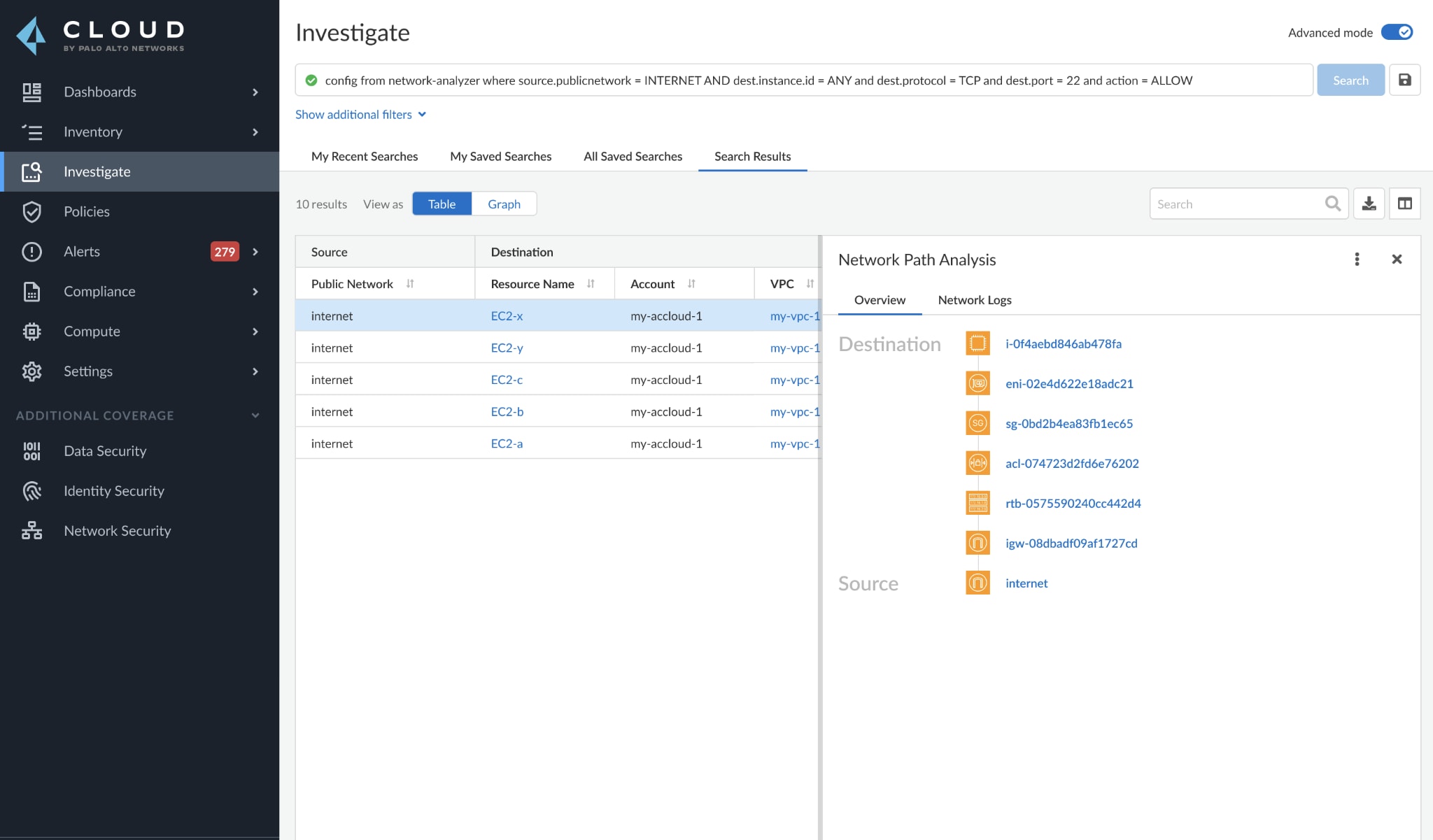
True Internet Exposure is a new functionality from Prisma Cloud that once again raises the bar for CSPM tools. We take a multi-dimensional approach to identifying overly-exposed cloud resources, providing end-to-end network path visibility between any source and destination – IaaS instances, PaaS instances, serverless functions, the internet, or other VPCs, just to name a few.
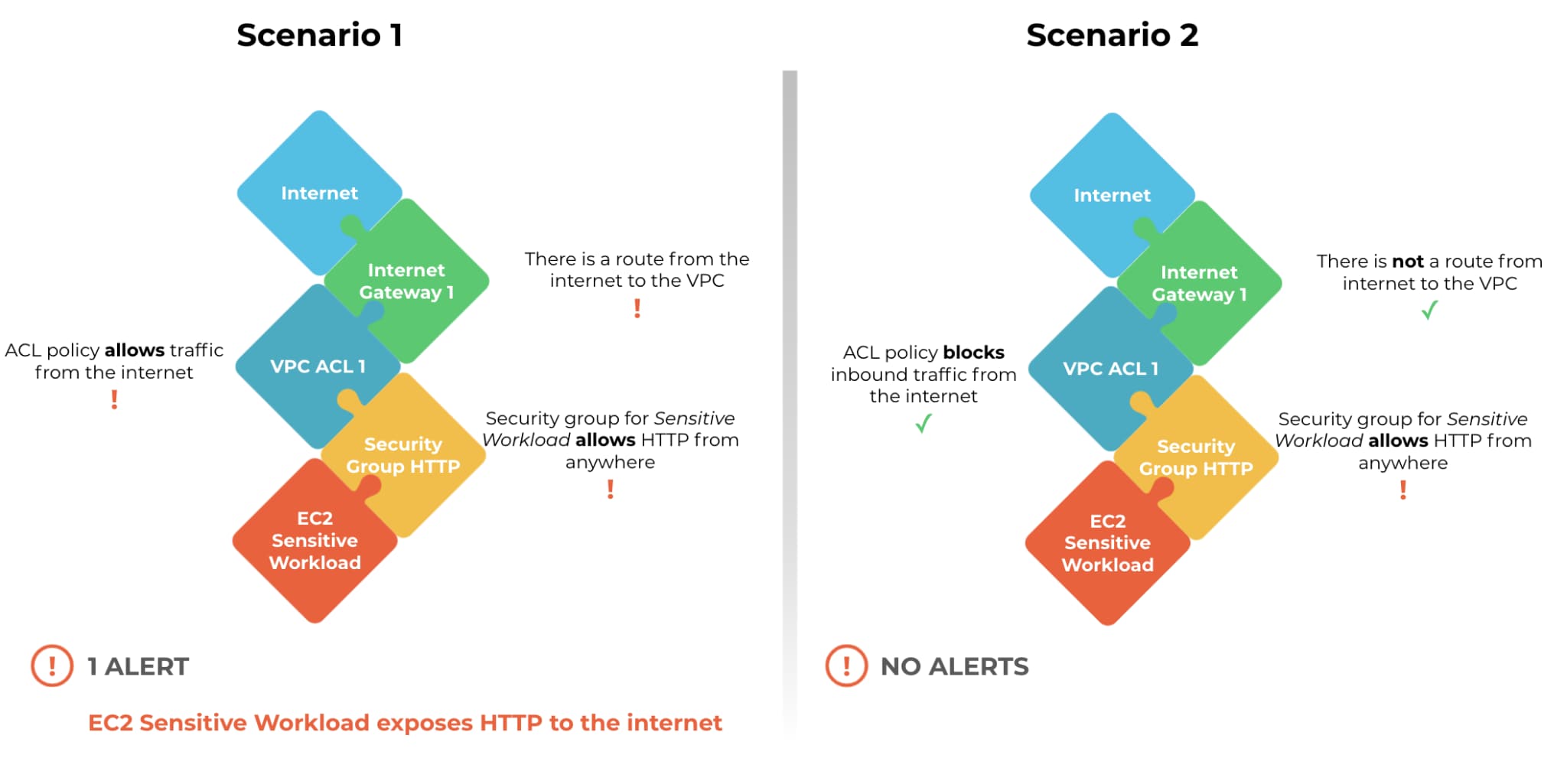
This breakthrough capability uses advanced graph analytics to evaluate possible network paths to cloud resources, including complex environments relying on transit gateways, load balancers, or firewalls. True Internet Exposure offers numerous benefits.
Comprehensive Visibility
Spend less time combing through configurations and manually stitching together resource mappings to understand the cloud network. Prisma Cloud builds a complete network path to and from cloud resources to give you easy-to-understand visibility.
Improved Risk Assessment
Easily identify open pathways that allow lateral movement across the cloud infrastructure and make informed security decisions that help you reduce the attack surface radius and partition the network.
Reduced Alert Fatigue
Stop false positives and move away from alerts against single network points (such as security groups). Adopt a model that evaluates network exposure of resources before generating an alert.
Learn More About True Internet Exposure
The True Internet Exposure functionality is part of Prisma Cloud’s CSPM capabilities and will become generally available (GA) for AWS environments soon. This new feature will help customers reduce alert fatigue and get visibility into the reachability of business critical cloud workloads in order to make informed policy decisions on how to reduce exposure.
Learn more about Prisma Cloud’s industry-leading CSPM capabilities.