Identifying and remediating vulnerabilities across applications, workloads and systems is important to protect against cyberattacks and keep data safe. This comes as no surprise, considering that 80% of open-source software packages contain vulnerabilities.1 At an average rate of 87 per day,2 MITRE publishes new CVEs — and research shows that adversaries can exploit them within 15 minutes of publication.3
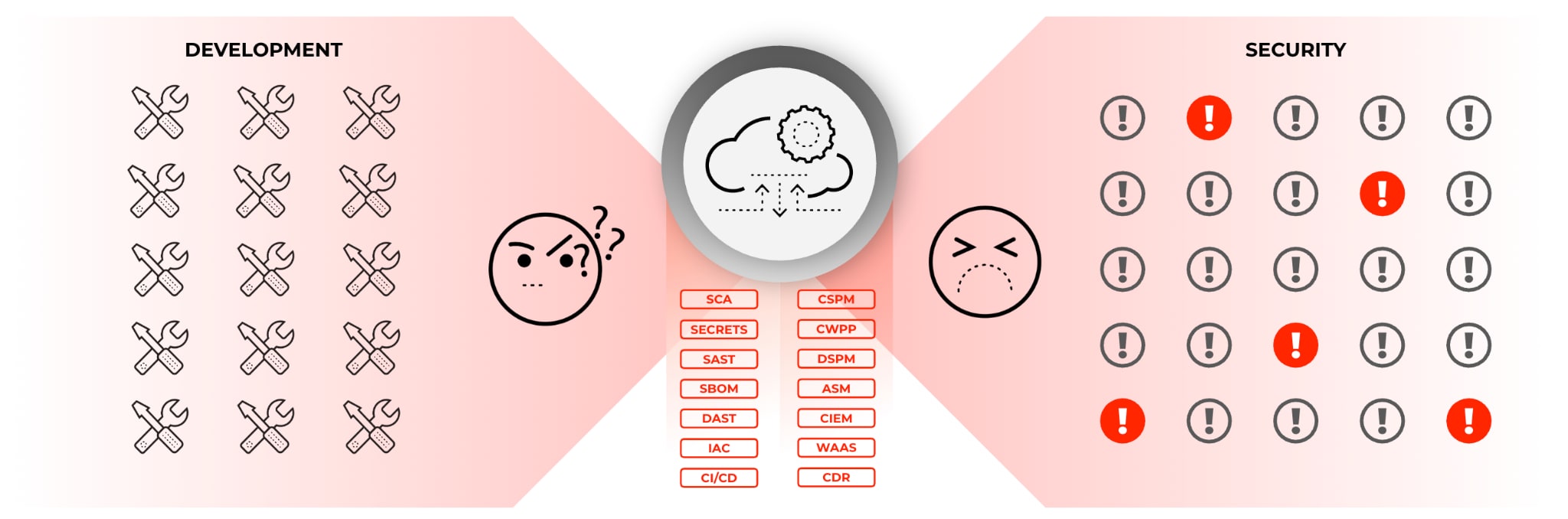
Security and InfoSec teams are in a race with malicious actors. At the same time, they’re dealing with an abundance of vulnerabilities that require the lion’s share of their resources just to find the consequential ones putting their enterprise at risk.
Teams need more than spreadsheets and pivot tables. They need full visibility into all assets, the compute workloads of their cloud environment — and that includes easy access to meaningful, actionable data.
The Real-World Challenge
For the most part, vulnerability management tools have kept up with modern cloud-native applications developed using open-source code and automated CI/CD pipelines to deploy the software across cloud environments. They do a good job when it comes to identifying vulnerabilities. Problems arise with the magnitude of vulnerabilities detected — which overshadow the actual risks.
Dealing with the noise has typically overwhelmed security teams pulling in developers, essentially handing them laundry lists of hundreds or thousands of vulnerabilities, saying "Please fix." But without code-to-cloud context, developers can’t discern what's most important. As a result, it can take months to patch a vulnerability.4
The challenge with managing vulnerabilities begins once tools identify them. It lies in the all-important next steps — prioritization and remediation — and involves nothing short of bringing order to chaos.
The Future of Vulnerability Management Begins Now
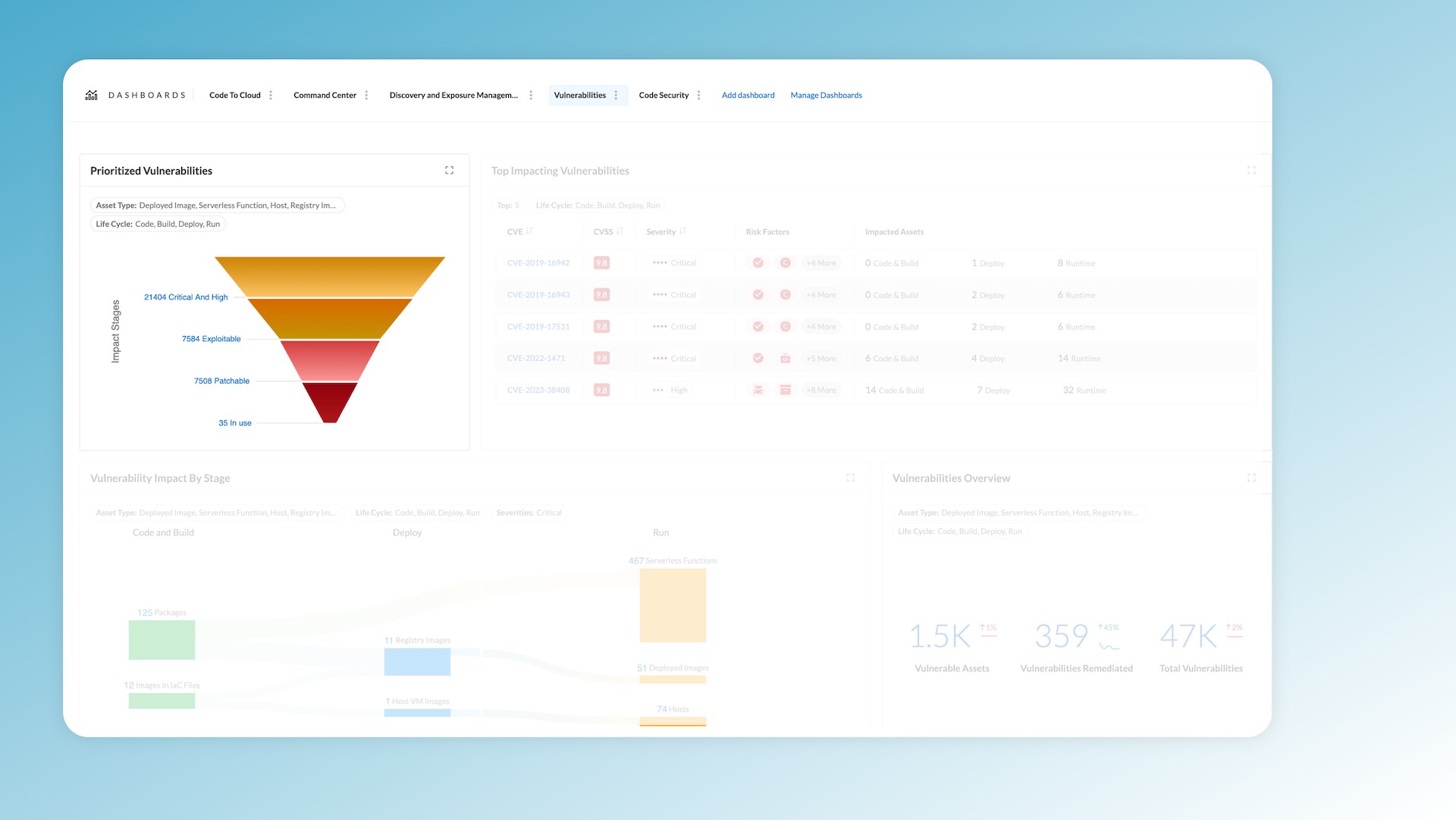
Prisma Cloud's Vulnerability Management Dashboard, introduced last week in the Darwin release, simplifies vulnerability discovery, prioritization and remediation. Using contextual layers, its funnel feature filters out noise and directs teams to urgent and high-impact issues. By efficiently identifying key vulnerabilities in cloud environments, security teams can devise targeted remediation plans and act quickly, reducing risks associated with delayed responses.
Prisma Cloud also provides over 20 contextual risk factors to help narrow down the scope of vulnerabilities. For example, it provides context into whether you have an exploit in the wild, whether the vulnerability is patchable and, most importantly, whether the package containing the vulnerability is in use. This context helps you home in from thousands of vulnerabilities to the handful you should fix.
Contextual Analysis: Focusing on Impactful Vulnerabilities
Vulnerability management isn’t about eliminating every risk, but about addressing the vulnerabilities that could wield the most impact. The majority of solutions don’t provide the context, which makes it difficult for teams to pinpoint the most consequential vulnerabilities and make informed decisions that optimize system performance and reliability.
As seen in figure 3, Prisma Cloud’s Vulnerability Management Dashboard ranks the top 5 most impactful vulnerabilities, providing a detailed view based on metrics such as CVSS score, severity and risk factors. If your environment includes an instance of log4j, for example, a single click reveals its far-reaching consequences across your infrastructure.
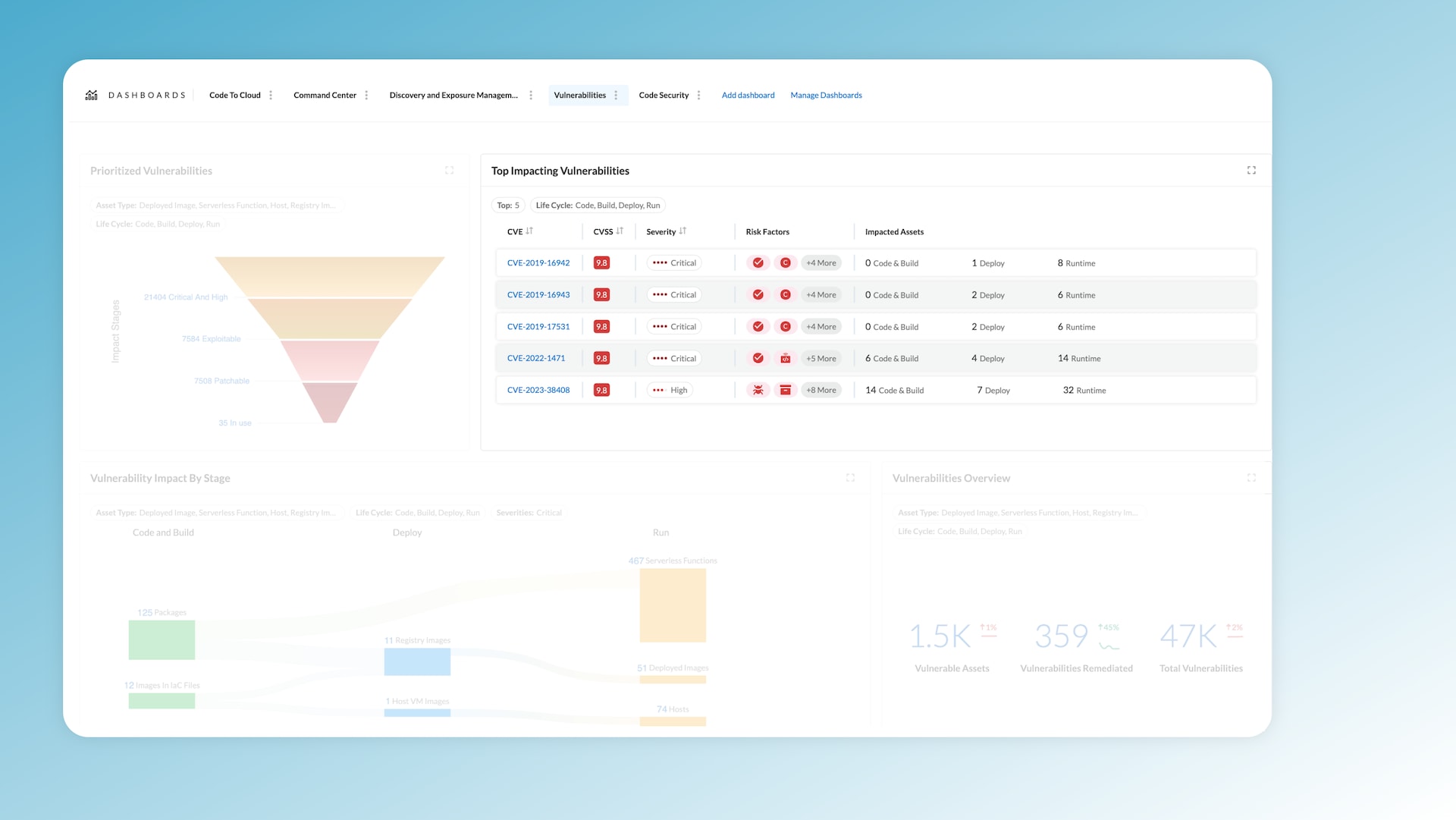
Visualizing the impact of a vulnerability across the software development lifecycle is no small feat. Prisma Cloud's Vulnerability Management Dashboard offers a full view across code, build, deploy and run stages. In the build stage, you can identify affected packages and infrastructure-as-code resources across multiple repositories.
The dashboard also highlights how these vulnerabilities propagate through host and container images, ultimately affecting runtime hosts, containers and serverless functions. In other words, you can view a complete list of every asset impacted by a particular vulnerability, showing you exactly where (and why) remediation is imperative.
From Insight to Action
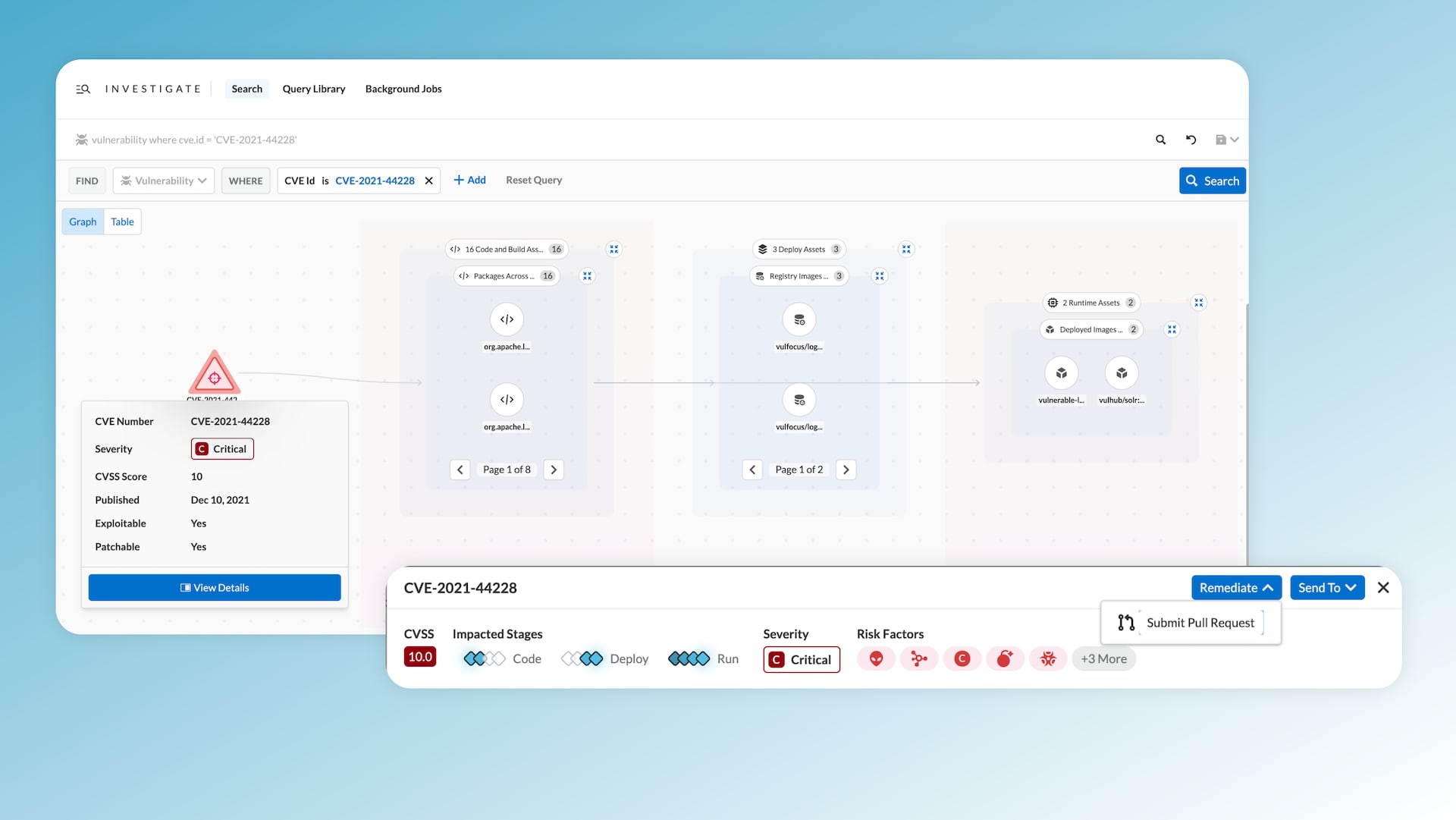
Once you've identified and analyzed exploitable, patchable and active vulnerabilities, the next step is remediation. Prisma Cloud traces each vulnerability from the workload back to the source code file and package — and provides a Fix-in-Code action. With this feature, Prisma Cloud can automate the remediation process by submitting a pull request. Addressing vulnerabilities at their source embodies shift left security, making future deployments secure by design.
The Path Ahead with Prisma Cloud
Palo Alto Networks Prisma Cloud is reshaping how organizations manage vulnerabilities from code to cloud. Providing unparalleled visibility with context into critical vulnerabilities across the application lifecycle, it surfaces risks that may have otherwise gone unnoticed. This comprehensive approach covers everything from IaC files, code repositories packages and CI pipelines to container image registries and runtime environments. And its ability to initiate source-based remediation empowers organizations to proactively manage vulnerabilities.
Learn More
Tune in to our on-demand webinar, CNAPP Supercharged: A Radically New Approach to Cloud Security, to learn about Prisma Cloud's latest innovations and how to streamline app lifecycle protection. And don’t miss an opportunity to test drive best-in-class code-to-cloud security with a 30-day Prisma Cloud trial.
References
- “The Software Composition Analysis Landscape, Q1 2023.” n.d. Forrester. Accessed September 17, 2023. https://www.forrester.com/report/the-software-composition-analysis-landscape-q1-2023/RES178778?utm_campaign=Image%20Editing%20%2F%20Aviary%20Launch.
- “NVD - February 2023 Listing.” n.d. Nvd.nist.gov. Accessed October 11, 2023. https://nvd.nist.gov/vuln/full-listing/2023/2.
- “2021 Cortex Xpanse Attack Surface Threat Report – Palo Alto Networks.” n.d. Start.paloaltonetworks.com. Accessed September 17, 2023. https://start.paloaltonetworks.com/asm-report.
- “2023 Data Breach Investigations Report.” n.d. Verizon Business. https://www.verizon.com/business/resources/reports/dbir.