We’ve just announced the general availability of the CloudGenix SD-WAN integration with the new AWS Transit Gateway Connect. This integration provides a simple and automated way to extend your CloudGenix SD-WAN fabric to AWS through the CloudGenix CloudBlades platform.
Prior to this announcement, CloudGenix customers had different ways to extend their SD-WAN fabric to AWS. CloudGenix customers could deploy virtual CloudGenix IONs through our AWS CloudFormation template-based marketplace listing. The marketplace listing provides two options to deploy IONs: greenfield, where the ION deploys in a new virtual private cloud (VPC), or brownfield where the ION is deployed in an existing VPC.
Customers would typically use the greenfield deployment model, creating a transit VPC where they set up VPC peering and static routes to facilitate the communication between the apps hosted in the peered VPCs and the clients on-premises. This method is usually applicable to small cloud deployments involving only a few applications.
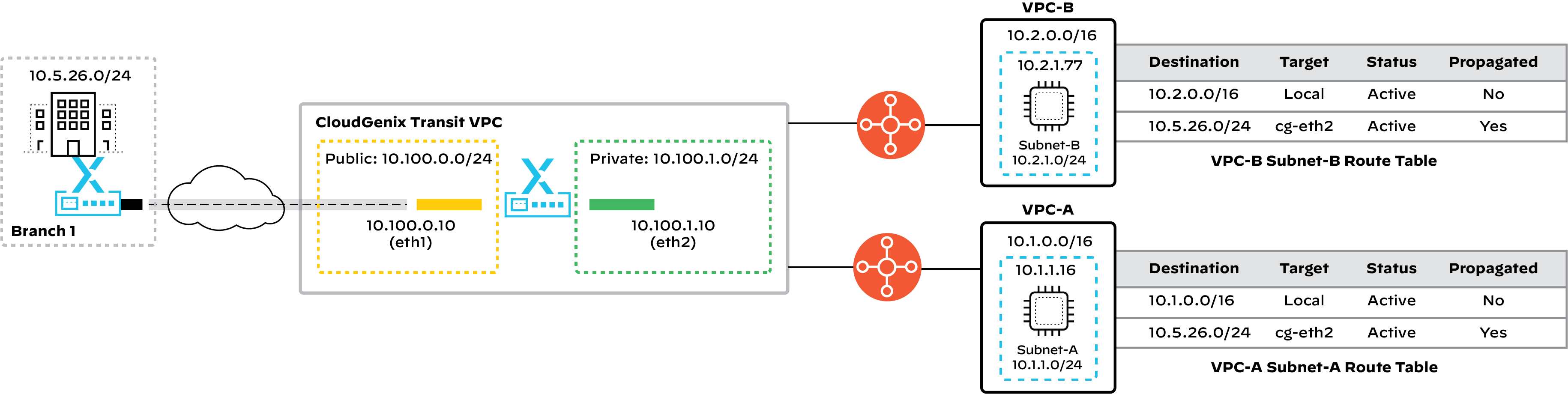
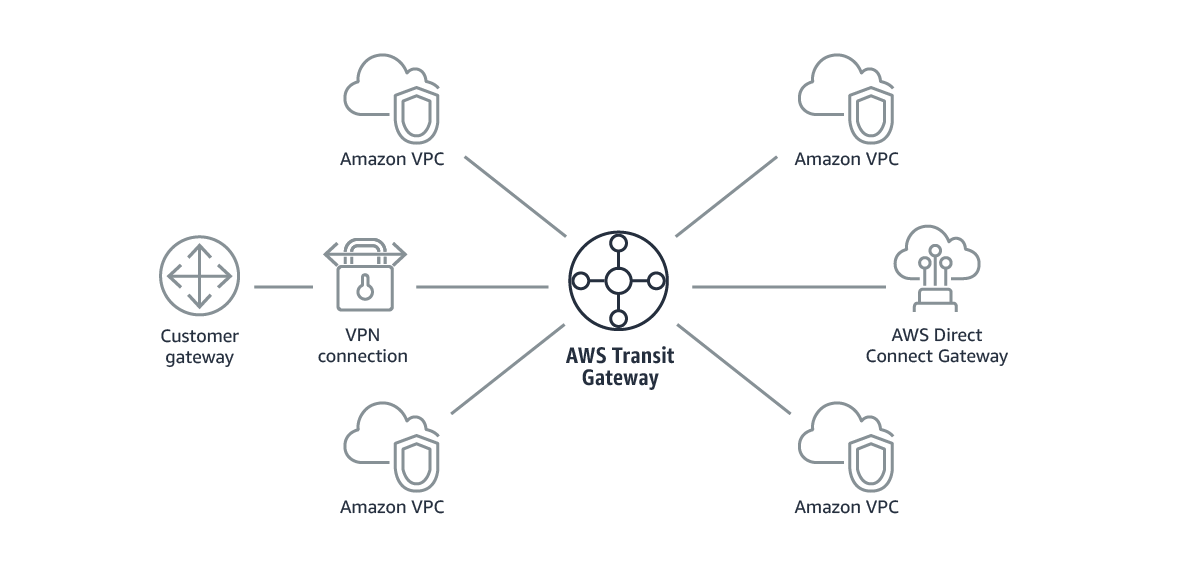
For larger cloud deployments including many VPCs, customers would typically deploy an AWS Transit Gateway per region and have all of the VPCs within the region connect to that transit gateway. There are several ways to connect on-premises networks with these central hubs.
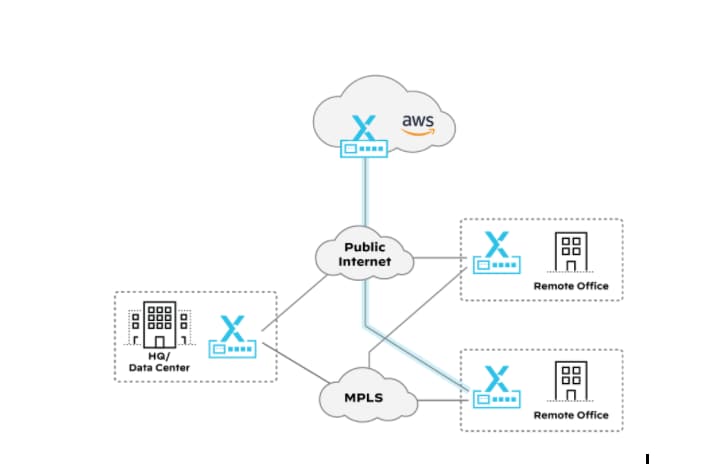
One option would be to build third-party traditional IPsec tunnels directly from all of the CloudGenix remote sites to the transit gateway. This requires manually configuring the VPN attachments on the AWS Transit Gateway for each site and circuit, as well as the reciprocal configuration on the CloudGenix devices. This model is possible but comes with an additional administrative overhead of the IPsec and BGP configuration and management.
Another option involves deploying a pair of vIONs in a transit VPC that is assigned to a DC site on the CloudGenix Controller. The IPsec tunnels are established between these IONs and the AWS Transit Gateway with a BGP “core” peering relationship. The branch sites only need to establish zero-touch secure fabric links (CloudGenix VPN) to the DC for the traffic to flow back and forth between the branch and the applications in the VPC attached to the particular Transit Gateway.
In this model, customers don’t need to manually set up IPsec tunnels from all the branch site vIONs to the Transit Gateway. However, there is still an additional overhead of having to deploy the vIONs, and manually configure the IPsec tunnels and VPN attachments on the Transit Gateway. Furthermore, as the number of remote sites grows, the maximum number of allowed routes at the Transit Gateway can be easily reached, becoming a bottleneck when expanding the number of remote sites. As such, this model could become highly restrictive for customers with many remote sites and prefixes that are not easily summarized.
A third option, and the most common, is to use AWS Direct Connect from the on-premises DC sites to the AWS Transit Gateway. This allows customers to use tried and true routing constructs they’re used to.
Unfortunately, this model defeats the purpose of implementing SD-WAN technology to leverage commodity internet circuits to access business-critical applications in the cloud. Furthermore, traffic backhauled through the DC negatively impacts performance and could potentially prevent the adoption of new business-critical applications to support business growth.
While these are possible options for connecting remote sites to AWS, they all come with a trade-off of operational complexity, additional administrative overhead, and scalability challenges.
AWS Transit Gateway CloudBlade: Gamechanger
We have taken advantage of the flexibility of the CloudGenix CloudBlades platform and AWS’s robust API support for Transit Gateway Connect to develop a new CloudBlade, the AWS Transit Gateway Connect CloudBlade.
Thanks to this newly developed CloudBlade, network administrators don’t need to worry about IPsec parameters, PSK management, BGP configuration, routing scale, VPN attachments, or vION deployments. All they have to do is express their intent in the CloudBlade configuration screen regarding where to extend the connectivity to, and optionally adjust the characteristics of the policies attached to the CloudGenix branch sites. For example, “I want to extend my SD-WAN fabric to these AWS Transit Gateways deployed in these X regions” or “Users attempting to access each of the applications/prefixes hosted in AWS should have this X path, Y QoS, and Z security policy applied.”
A Native Integration that Automates Connectivity and Simplifies Operations
The new AWS Transit Gateway Connect attachment provides native integration with CloudGenix vIONs to simplify configuration and improve the overall scalability of the solution.
GRE tunnels are now supported between the Transit Gateway and the IONs, which enables greater performance beyond the 1.25 Gbps originally supported with the IPsec tunnels. In addition, scalability is improved by incrementing the number of routes allowed. Altogether, the route management is simplified, and the routing scale across the hybrid environments is further improved.
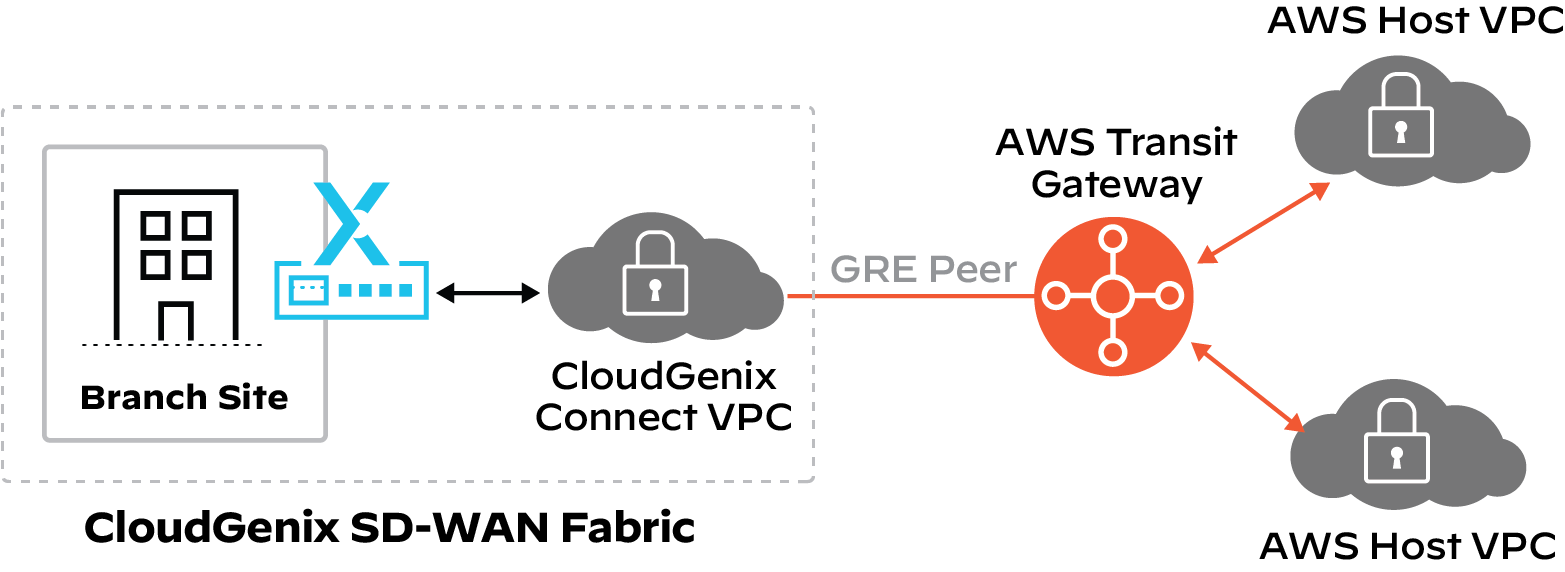
How Does It All Happen?
An administrator configures the CloudBlade parameters on the CloudGenix UI, such as AWS API Key, AWS Subscription ID, and the Transit Gateway regions to attach to.
The CloudBlade automatically performs the following actions:
- Deploys a Connect VPC to the region(s) of the transit gateway(s) specified
- Deploys a pair of vIONs within the VPC(s) in separate availability zones
- Claims and assigns each vION to a DC site per region
- Configures the Transit Gateway Connect attachment to each vION
- Configures GRE tunnels and BGP parameters on both CloudGenix and Transit Gateway
- Activates the DC site
Once the DC site(s) are activated and in control mode, all branch sites automatically build secure fabric links to the DC site(s). Afterward, the administrator can adjust the application policy as needed.
Branch-to-Cloud Access Just Made Simple
As organizations embark on their cloud journey, they come to the realization that they require a complete transformation of their WAN infrastructures. Legacy SD-WAN solutions just do not cut it. They need a next-generation SD-WAN solution like the one provided by CloudGenix SD-WAN, which is purpose-built, based on SDN principles with robust API support, and which allows them to operate and innovate at cloud scale and pace.
The integration of CloudGenix SD-WAN and the AWS Transit Gateway Connect enables organizations to connect branches and users with applications at AWS in a much more automated, efficient, and simpler way that ultimately translates to greater productivity and reduced costs.
To learn more about the benefits of the CloudGenix SD-WAN and AWS Transit Gateway Connect integration, check out our solution brief.