In today’s enterprise environment, the intricate web of interconnected SaaS applications, identity providers (IdP), and service accounts with disparate policies has made securing user identities and data challenging. This complexity increases the risk of misconfigurations, identity sprawl, and unauthorized access, hindering efforts to ensure robust and consistent security.
According to the Verizon Data Breach Investigations Report, nearly 40% of breaches in the first half of 2024 involved multifactor authentication (MFA) bypasses due to configuration errors.
It has become daunting for organizations to uncover the hidden dangers within their identity infrastructure and secure users and data across platforms amid digital transformation. Security professionals must navigate the complexities of interconnected systems while staying ahead of potential threats and vulnerabilities.
Fortifying Your Defenses: The Vital Role of Identity Security
The complexity and proliferation of modern SaaS and IdP ecosystems have created unique challenges. Inconsistent policies across SaaS, unknown owners of local service accounts, and shadow access to sensitive data via interconnected apps have created gaps in visibility and security. Moreover, ongoing policy and configuration changes without fully grasping its downstream impact can result in identity sprawl and unintended access to sensitive data.
Today, a comprehensive identity security posture management (ISPM) solution is crucial for organizations to gain insight into user activities, maintain control over access, mitigate risk of misconfigurations, and ensure compliance across complex systems. It enables continuous monitoring, assessment, and improvement of identity-related security measures to reduce vulnerabilities and enhance overall cybersecurity resilience.
Introducing Palo Alto Networks Identity Posture Security
Palo Alto Networks is thrilled to announce the general availability of Identity Posture Security. This advanced ISPM solution is part of SaaS Security Posture Management (SSPM) and natively integrated with Next-Generation CASB.
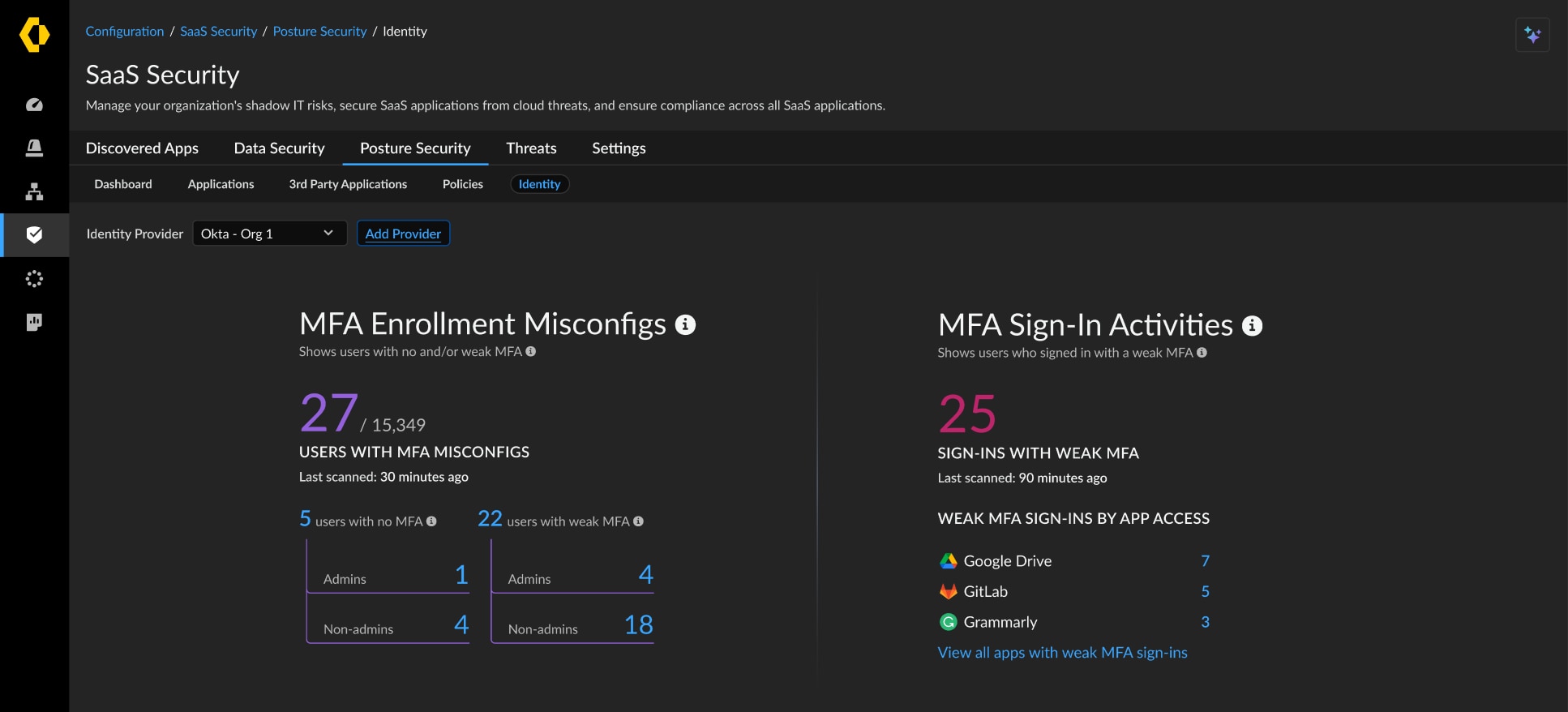
Figure 1: Identity Posture MFA Dashboard
Our first release introduces several innovations to help organizations safeguard users, applications, and data at scale.
| KEY FEATURES | |
| MFA Enrollment | Identify users not enrolled in MFA or those enrolled in weak MFA protocols within emails, passwords, security questions, SMS codes, and more. This feature can differentiate between Administrative and Non-Administrative users. |
| MFA Activity | Detect and remediate MFA activities deemed to be insecure.
|
| MFA Reports | Filter and download MFA usage reports for compliance audits and to adjust security policies. |
Simplifying Security to Stay Ahead of Threats
Palo Alto Networks Identity Posture Security helps simplify SaaS authentication with consistent policies to easily detect misconfigurations, identify and monitor all service accounts (tieing them to real users), and prevent threats from shadow access.
By simplifying the monitoring, assessing, and optimizing of identity-related misconfigurations and security measures, Identity Posture Security empowers organizations to maintain robust cybersecurity resilience to safeguard what matters most - users, applications, and data.
Level Up Your Identity Security Today
Identity Posture Security is available today. Stay tuned as we innovate with upcoming features such as nonhuman identity management, shadow app detection, privilege escalation tracking, and more.
Begin your 60-day free trial of SaaS Security Posture Management and discover the benefits of Identity Posture Security today.
This blog contains forward-looking statements that involve risks, uncertainties and assumptions, including, without limitation, statements regarding the benefits, impact, or performance or potential benefits, impact, or performance of our products and technologies. These forward-looking statements are not guarantees of future performance, and there are a significant number of factors that could cause actual results to differ materially from statements made in this blog. We identify certain important risks and uncertainties that could affect our results and performance in our most recent Annual Report on Form 10-K, our most recent Quarterly Report on Form 10-Q, and our other filings with the U.S. Securities and Exchange Commission from time-to-time, each of which are available on our website at investors.paloaltonetworks.com and on the SEC's website at www.sec.gov. All forward-looking statements in this blog are based on information available to us as of the date hereof, and we do not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.