THE INSIDER THREAT CHALLENGE IS UNSOLVED AND GROWING:
Insider threats are growing almost 40% year-over-year. These threats can be particularly difficult to discover and remediate, with 73% of breaches involving an insider going undetected for months.
Surfacing risk and accelerating response to insider threats should be key priorities for any security operations team -- even more so as the increasingly collaborative (and virtual) workforce culture continues to move the goalposts for data security. Currently, 31% of workers admit to exfiltrating data through cloud-sharing platforms. At a time when employee departure rates are high for many industries, increased signal to look for potential insider threats – such as an employee uploading a resume in a web browser – in tandem with turn-key automated processes, can provide security teams with the actionable context needed to speed investigations and take a right-sized approach to incident response.
Furthermore, the shift to remote work has impacted how security teams work together cross-functionally with other departments – such as HR and Legal – on business processes throughout the employee lifecycle, including employee offboarding and incidents involving workers with access to sensitive or proprietary information.
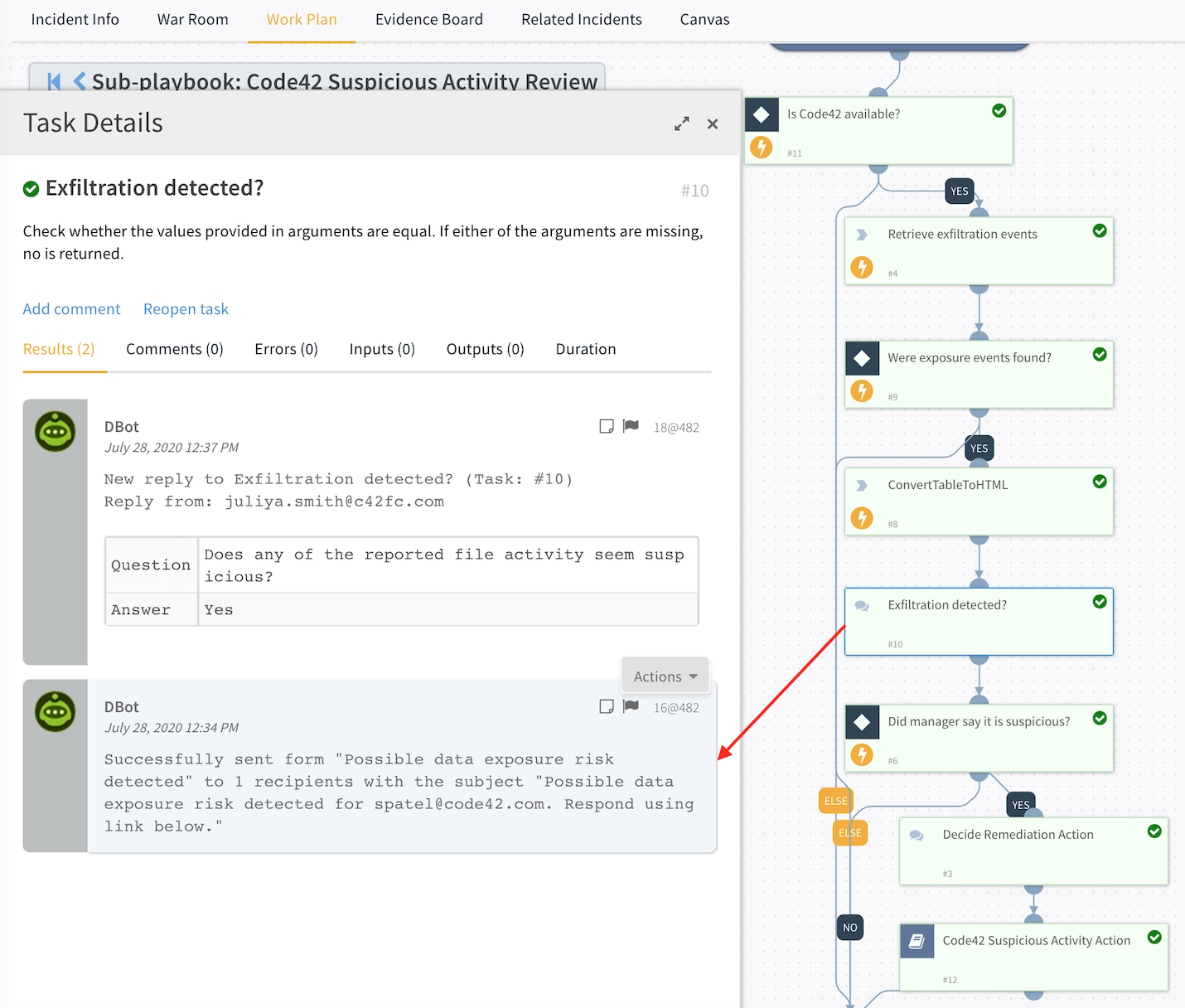
THE BENEFITS OF AN INTEGRATED ECOSYSTEM – THE CODE42 INSIDER THREAT REMEDIATION CONTENT PACK:
Considering most security stacks are built to address external threats and regulatory compliance, it continues to be difficult to detect when sensitive or proprietary data is put at risk from the inside. Code42’s integration with Cortex™ XSOAR by Palo Alto Networks allows joint customers to surface insider risk and accelerate incident response throughout the employee lifecycle.
Code42’s turn-key pack within the Cortex XSOAR Marketplace offers a configurable lookback of an employee’s historic file movements – including browser uploads and cloud sync activity – and can be initiated based on preset triggers, such as an email sent from a human capital management (HCM) system indicating an employee has been terminated or is leaving the organization to go to a competitor.
USE CASE: JOHN: A TRUE EXFILTRATION STORY
THE DISGRUNTLED EMPLOYEE - You know how this story starts! John has been an employee with QRST Inc for 4 years and was recently passed up for a promotion. Coincidentally, John has recently turned in his 2-week notice and it turns out that he’s joining a competitive firm. An email from the human capital management (HCM) system triggers the process. The big question for QRST - what files might John be taking with him?
UNDERSTANDING RISK EXPOSURE - QRST Inc is able to immediately add John to the departing employee workflow directly from Cortex XSOAR, enabling them to understand any situations of data exfiltration in real-time.
ALERTS WITH CONTEXT - Not surprisingly, within 24 hours the security team at QRST Inc receives an alert that John is indeed moving data around suspiciously. The alert is received within Cortex XSOAR (triggered by Code42).
HISTORY MATTERS - Based on the alert and the type of files John appears to be moving, the security team constructs a full picture of all John’s historial file movements. It becomes clear that John has been moving company confidential files to an unsanctioned DropBox account - intent unknown.
INVESTIGATION POWERED BY FACTS DELIVER RIGHT-SIZED RESPONSE - Equipped with a complete forensic rundown of John’s file movement patterns, his manager has all the information required to have a corrective conversation with John. All of this was done in a matter of days, potentially saving QRST Inc millions of dollars in potential damages.
LEARN MORE ABOUT CODE42 + CORTEX XSOAR:
Joint Solution Brief: Link Pending (in review)
Joint Webinar: Palo Alto Networks + Code42: Managing Data Risks During WFH Workforce Changes