Do you know if you have any exposure to the latest GitLab vulnerability? Cortex Xpanse does.
When companies decide to move their code repositories to the cloud, they often have concerns regarding the security of their code. Code repositories often contain third-party dependencies or libraries that can have security vulnerabilities. Cloud-based code repositories should have proper vulnerability management processes in place, including regular scanning, patching, and updating of software components to mitigate the risk of exploitation by attackers. Cortex Xpanse helps identify vulnerabilities in code repositories and even helps organizations take remedial actions.
On May 23, 2023, GitLab, a widely used web-based DevOps lifecycle tool, announced a critical security vulnerability known as CVE-2023-2825. This path traversal vulnerability allows malicious actors to access sensitive data on GitLab servers, such as proprietary software code, user credentials, tokens, and other confidential files, without authentication. This vulnerability has been assigned a maximum CVSS v3.1 score of 10.0 and has the potential to impact over 30 million registered GitLab users if exploited.
Xpanse helps you quickly assess the impact of this threat on your organization and, if needed, begin remediation through an automated incident response workflow.
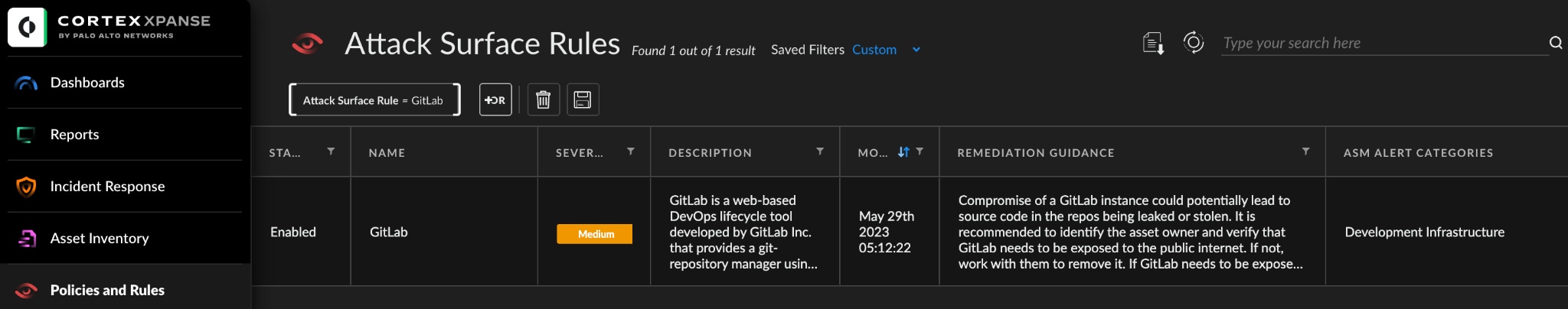
In the Expander console, you can see that an attack surface rule has been implemented to alert you to any exposed assets matching criteria of the CVE. With Xpanse’s real-time visibility and monitoring, you can expect continuous discovery and evaluation of security issues on your external attack surface.
Analysts can also navigate to the Threat Response Center and find a new threat event available for GitLab [CVE-2023-2825]. By clicking into the event, users can access alerts, incident reports, mitigation guidance, and a list of affected software versions. By understanding the severity and potential impact of the GitLab vulnerability, users can prioritize the most significant risks to their critical systems or sensitive code repositories, ensuring effective resource allocation for remediation.
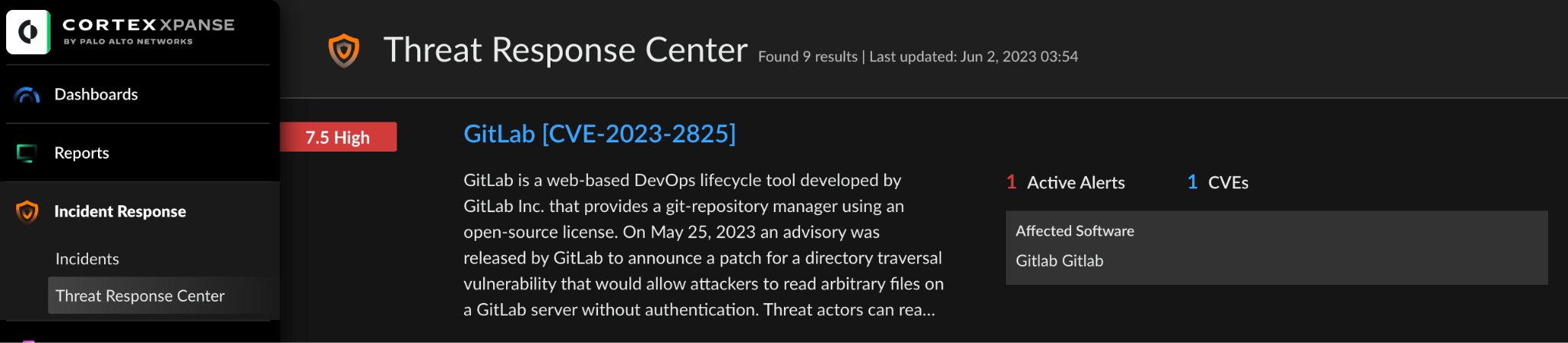
The centralized visibility Xpanse provides empowers organizations to quickly gain a clear understanding on the extent of exposure, as well as remediation guidance tailored to this specific vulnerability. Security teams are equipped to take the necessary steps to prevent exploitation - whether that be patching vulnerable instances or taking them offline - thereby streamlining the response process and minimizing the time required to mitigate the threat.