This post is also available in: 日本語 (Japanese)
On July 24th, 2023, Ivanti Endpoint Manager Mobile (EPMM), previously known as MobileIron Core, publicly disclosed CVE-2023-35078. This vulnerability allows unauthenticated users full API access through specific API endpoints whereby malicious actors can extract personally identifiable information (PII) and perform administrative actions, like creating new accounts and making configuration changes, without needing any credentials.
Norwegian authorities confirmed on July 25th, 2023 that a dozen of its government ministries had been targeted in a cyberattack exploiting this vulnerability. According to Cortex Xpanse researchers, over 5,500 Ivanti Endpoint Manager Mobile servers were exposed at the time of this post, with the highest number of exposures found in Germany, the United States and the United Kingdom.
Given the global reach of this incident and the fact that the vulnerability has already been exploited in the wild, organizations should investigate exposures on their network and remediate as quickly as possible.
To help security teams respond to internet emergencies like this, Cortex Xpanse detects impacted devices on an organization's network and alerts you to those through an in-product policy module. Cortex Xpanse is able to provide increased coverage due to its extensive searching across multiple fields in an HTTP response, such as specific strings in the HTTP body, various HTTP headers, and other key indicators that other tools on the market might miss.
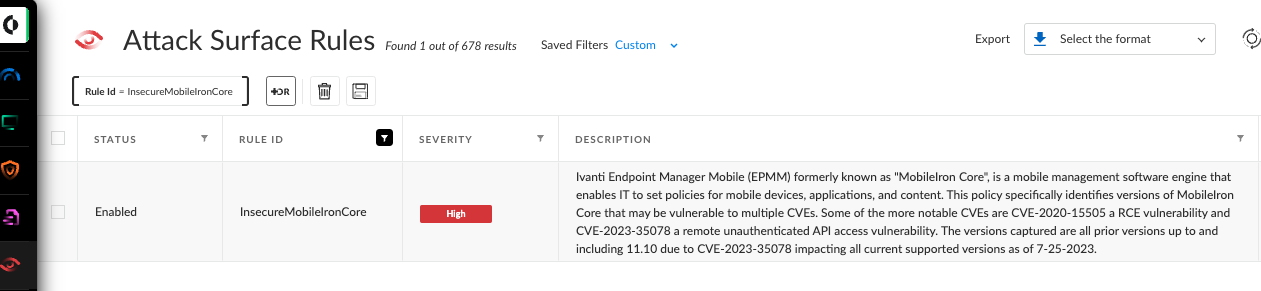
Within Cortex Xpanse’s Threat Response Center, organizations can also find curated threat intel summaries, exploit consequences, previous exploit activity, and links to other sources for additional information. This empowers you to see how risk is distributed across your organization and build a remediation plan based on the guidance provided. Cortex Xpanse identifies service owners automatically, so organizations can easily assign a ticket to the right person.
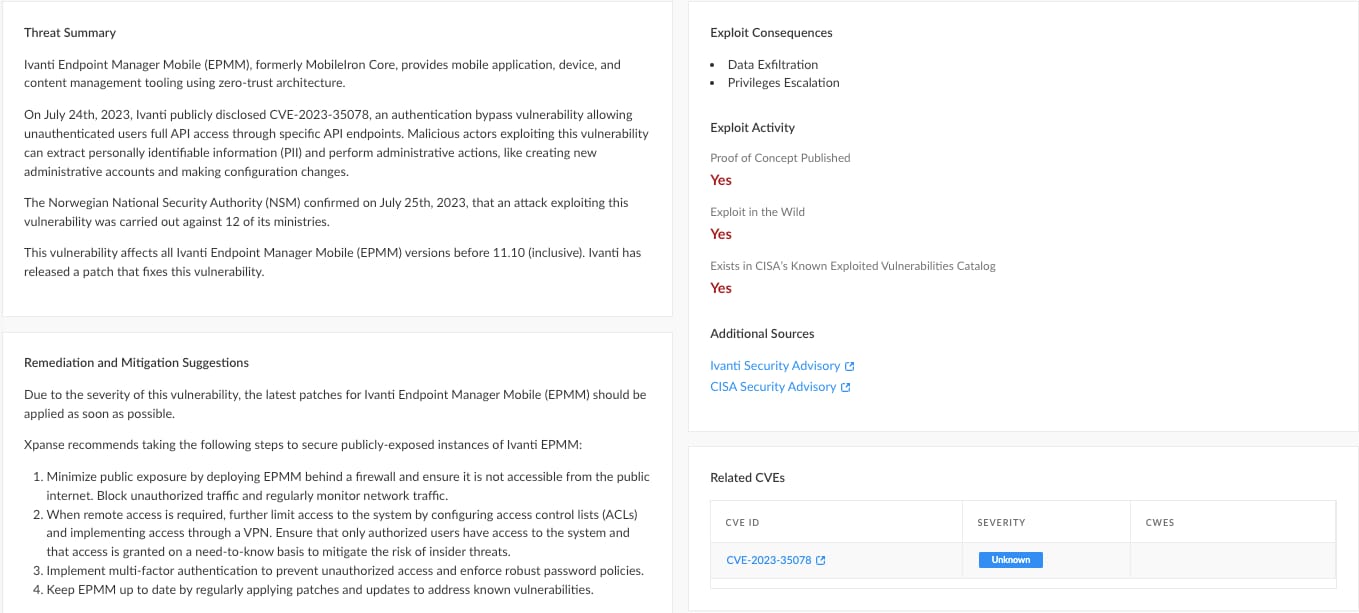
The exploitation of the Ivanti Endpoint Manager Mobile vulnerability calls for immediate examination to uncover vulnerabilities on your attack surface. If left unpatched, organizations are at risk of a major security breach. The Threat Response Center will continue to be updated dynamically as additional information becomes available.
To learn more about the Threat Response Center in Cortex Xpanse, read our datasheet.