“Attack Surface Management” sounds like it could be the name of a heavy metal rock band. While ASM isn’t something you’ll see at Riot Fest, it should be something you find in your SOC, especially given what it provides. With ASM, you get an attacker’s “outside-in” view of your organization's attack surface.
That’s right, an attack surface management (ASM) solution can provide a continuous discovery, monitoring, and assessment of an organization’s external, internet-facing attack surface that could be at risk from threat actors who are scanning it for weaknesses at seemingly breakneck speeds.
And scan they will—ad nauseum, as we discovered. Attackers can scan the entire internet in under an hour to find exposed assets, and what they find is troubling.
In our report, 2022 Cortex Xpanse Attack Surface Threat Report: Lessons in Attack Surface Management Based on Observable Data, we outlined some key findings from our research of the public-facing internet attack surfaces of some of the world’s largest businesses:
- Low-Hanging Fruit Continues to Hang. Nearly one out of every four issues we found on the attack surface was related to exposed RDP servers, a key vector for ransomware attacks. Even looking at the next most common issues, the end result was often an exposed administration login portal.
- End-of-Life Software Means End-of-Life for Your Security. When looking at fundamental issues of poor security, we discovered a troubling amount of exposures in administrative login pages as well as in internet-facing end-of-life (EOL) software. Across the following applications below, we saw, on average, around 30% of organizations were running EOL software versions:
- Apache Web Server: ~32% running EOL versions
- Microsoft Exchange Server: 29% running EOL/unsupported versions
- The Unmanaged Attack Surface Is Growing. EOL software is often an indicator of an unmanaged asset. But risks and exposures are persistent not only because of asset leak leading to unmanaged assets, but because modern attack surfaces are inherently dynamic, constantly shifting, moving, and growing. This means that as attack surfaces grow, so too does the number of unmanaged assets on those surfaces.
The Urgency is Real and Increasing
Let’s face it, perimeter-centric strategies for network security don’t work anymore. Location of security infrastructure and systems extend beyond the traditional internet perimeter to the cloud, an increasingly remote and mobile workforce, and every connected device or endpoint—each requiring some level of visibility and control to prevent compromise. The modern threat landscape has become an environment that knows no bounds in our hyper-connected digital world.
As companies migrate more and more data resources and applications to the cloud, and it becomes easier for any employee with a credit card to create a new cloud instance outside of security controls, asset leak becomes inevitable. If companies don’t know what they have, that lack of visibility leads to a multitude of issues, including an inability to maintain regulatory compliance, cloud app data theft, and inability to monitor data to and from cloud apps.
And while cybersecurity pros take advantage of cool new tools to combat these challenges, advancements in scanning technologies allow threat actors to locate attack vectors quickly and easily, revealing abandoned, rogue, or misconfigured assets that can become backdoors for compromise.
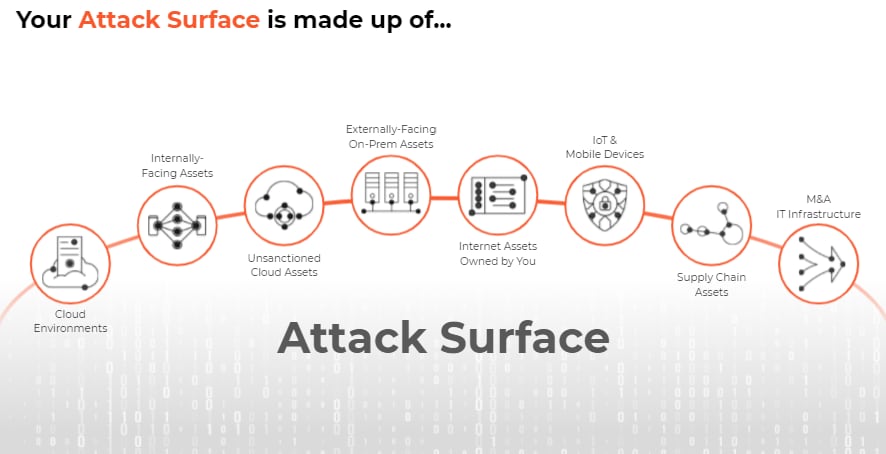
A critical step to informing any risk management function is to have a clear understanding of one’s attack surface—you can’t protect what you can’t see.
In ESG’s new whitepaper, Value Drivers for an Attack Surface Management (ASM) Program, they outline proof-points for organizations, providing a high-level overview of the value that Attack Surface Management brings to increasing security maturity and reducing risk.
In a no-nonsense approach, Jon Oltsik, ESG Senior Principal Analyst and Fellow, describes why current ASM is inadequate, continuing to lag, handicapped by manual processes, inconsistent discovery cycles, and incomplete or partial monitoring of an attack surface.
"69% of organizations surveyed report that they've experienced a cyber-incident resulting from an unknown, unmanaged, or poorly managed internet-facing device.1"
What’s it Going to Cost?
As with reviewing any new security solution, determining the benefit-to-cost ratio may help determine if and when a solution is implemented and deployed. In the case of ASM, the ESG paper makes a clear case of the absence of an ASM program coming at a cost.
When ASM best practices are neglected, traditional manual processes cannot keep up with modern ever-changing attack surfaces, leading to increased risks, breach-related costs, and even higher cyber insurance premiums.
As stated in the paper:
ESG research reveals that organizations have discovered an assortment of vulnerable assets like sensitive data in a previously unknown location, websites with a direct or indirect path to their organizations, employee credentials (that may be misconfigured), previously unknown SaaS applications, and applications with zero users.
In fact, unknown attack surface assets tend to be the rule rather than the exception. ESG has seen that when organizations use automated attack surface management discovery tools, security teams regularly find that their attack surface is at least 40% greater than they perceived. These exposures represent easy targets for cyber-adversaries and create significant risks for organizations.
It is these types of revelations that should be a wake-up call for security practitioners who are even remotely concerned of missing one iota of attack surface coverage during discovery. Any potential exposure can become an easy target for threat actors to gain a foothold, move laterally, and create significant compromises and/or full breaches.
Show Me the Money! How to Allocate Budget for ASM
According to ESG, 80% of organizations will increase security hygiene and posture management overall in 2022, and that includes direct investments in attack surface management2. However, finding budget can be a creative exercise in knowing how to position a request. In Value Drivers for an Attack Surface Management (ASM) Program, ESG shares strategies organizations are implementing to do just that including:
- Creating discretionary budgets.
- Rerouting point-in-time ASM analysis budgets.
- Establishing a preventative security budget.
- Justifying ASM spending to lower cyber-insurance premiums.
- Turning ASM spending from capital expenditure to operational expenditure.
- Sharing the cost of ownership across multiple teams
“Moving forward, ASM should be considered a critical security safeguard deserving a dedicated budget.” -Enterprise Strategy Group (ESG)
Suffice it to say, advocating for and adopting a sound ASM strategy should be a part of security hygiene best practices. And if it’s not, it should be on your shortlist of solutions to explore and consider.
Learn more about the benefits to security and budgets offered by ASM by downloading Value Drivers for an Attack Surface Management (ASM) Program by ESG.
1 Source: ESG Research Report, Security Hygiene and Posture Management, January 2022. All ESG research references and charts in this white paper have been taken from this research report, unless otherwise indicated.
2 Source: ESG Complete Survey Results, Security Hygiene and Posture Management, January 2022.