With the ever evolving threat landscape, security operations teams require a new level of efficiency to protect their organizations. The latest release across Cortex products aims to solve a diverse set of challenges in security operations, all while improving the efficiency and overall analyst experience.
- XSIAM 2.3: Enhancing SecOps workflows and analyst experience.
- XDR 3.11: Preventing new and emerging threats with improved efficiency.
- Xpanse 2.6: Delivering new automations and active response enhancements.
- XSOAR 8.7: Simplifying automation in security operations.
XSIAM 2.3: Enhancing SecOps Workflows and Analyst Experience
The latest release of Cortex XSIAM enhances SecOps workflows and enriches the analyst experience by introducing higher levels of visibility and automation suited for the analyst’s individual preferences.
New Custom Incident Layout
One challenge analysts encounter is the inability to promote important data from alerts to the incident level, leading to difficulty in accessing the necessary information. Furthermore, without aggregated or enriched data from alerts at the incident level analysts will find it difficult to gain a comprehensive understanding of the situation.
But, the new Custom Incident Layout, available in XSIAM 2.3, enables analysts to customize the incident page layout. This streamlines the investigation process by enhancing the visibility of important incident-specific fields, data ingested from integrations, and playbooks that can be executed. Incident layouts are customizable by incident type (e.g., phishing, malware, etc.) or based on analyst preference.
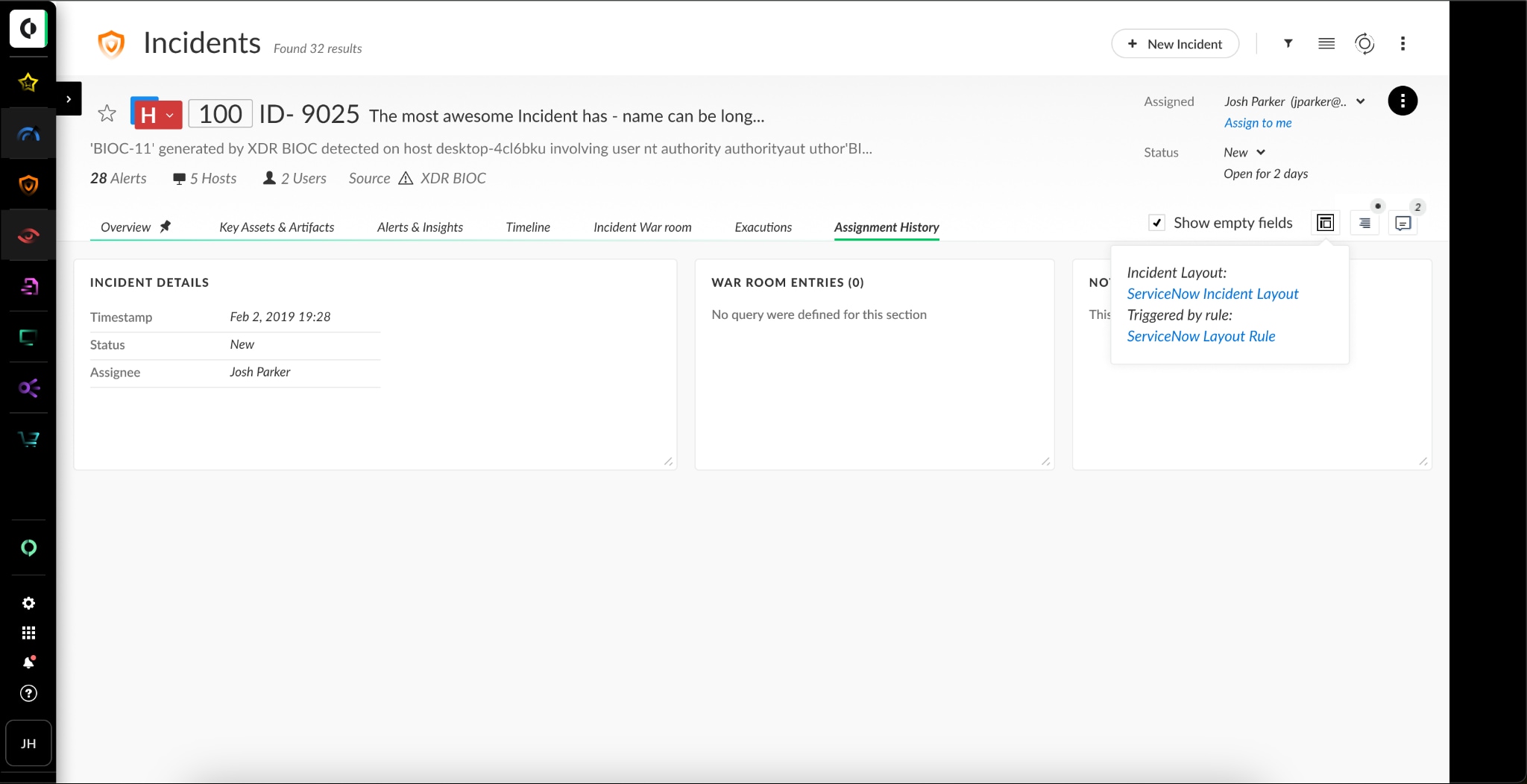
Incident SLAs
Analysts also face challenges in quantifying the impact of incident mitigation processes and identifying where delays or inefficiencies occur, which hinders the assessment and optimization of workflows. Addressing these challenges is crucial for enhancing incident response and customer satisfaction.
The solution to this is Incident SLAs, which allows analysts to effectively monitor and assess key performance indicators (KPIs) by setting SLAs at the incident level. This provides a quantifiable and efficient approach to tracking KPIs, obtaining real-time insights into operational performance, and ensuring alignment with established objectives. By doing so, organizations can effectively meet critical goals and foster accountability and efficiency across operations.
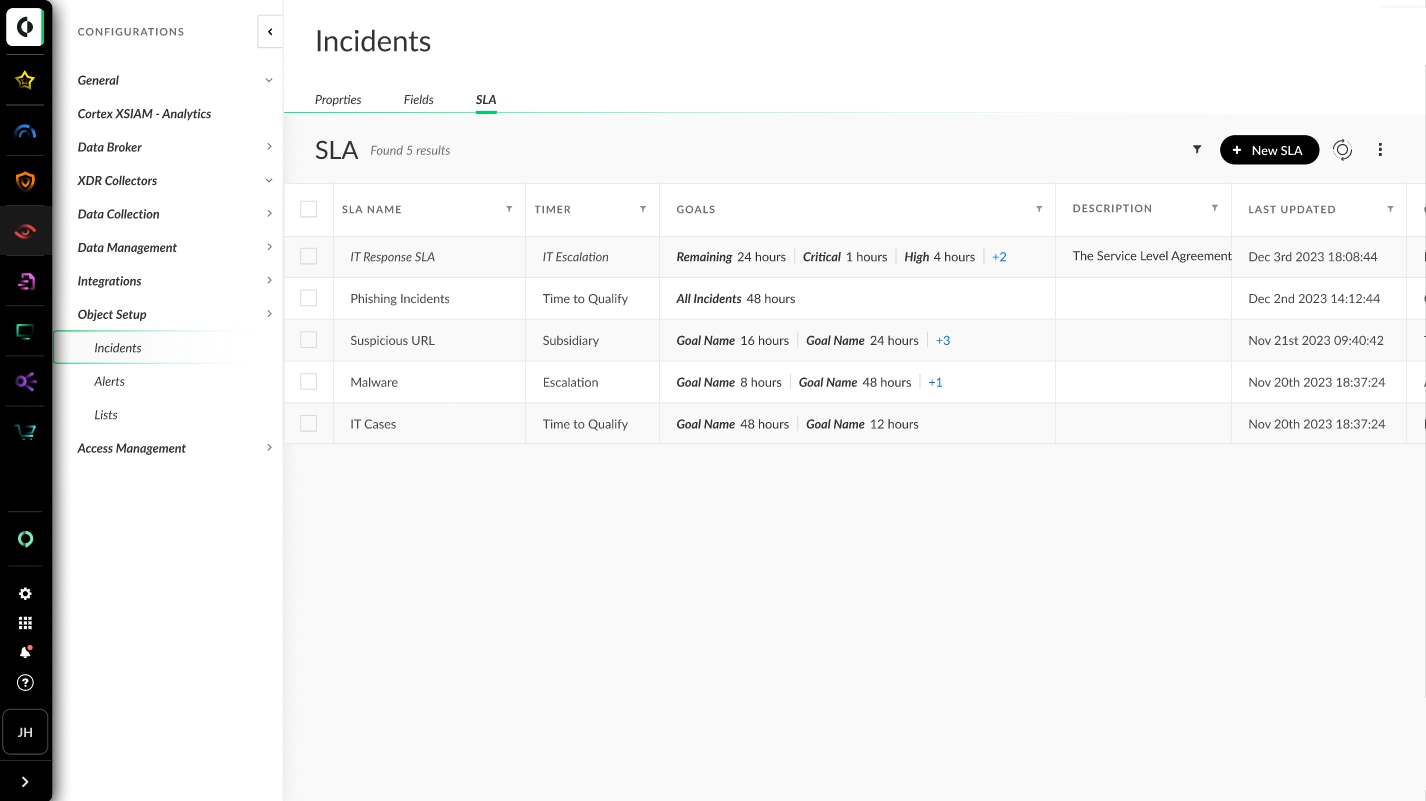
Playbook Dev-Prod Capabilities
Many analysts require separate environments for testing, which can often result in a large overhead of maintaining test data, and other challenges. For example, users migrating from XSOAR to XSIAM miss the ability to write all content, integrations, playbooks, and scripts in one environment and push them in a managed manner to their production environment. Additionally, there is a lack of tools to create and test datasets and playbooks before pushing them to the production environment, and difficulty in maintaining change management, as each update necessitates users to complete changes from start to finish in one go. Addressing these challenges would improve efficiency and streamline the development and deployment processes.
The new Playbook Dev-Prod Capabilities in XSIAM ensure efficient creation, deployment, and testing of automation playbooks. XSIAM now provides a pre-configured development repository for creating automation playbooks, utilizing data ingested from an organization's production tenants, and providing SecOps engineers with Dev-Prod capabilities. The Dev-Prod repository enables engineers to write, test, and revise playbooks in an isolated setting before deploying them to production.
Multi-Tenant Unified Incident View
Managing incidents across multiple environments poses a significant challenge, particularly in terms of workload management, tracking the status of incidents, and prioritizing events effectively. There is a pressing need for solutions that offer the capability to take action, as the current read-only solutions are limited in addressing incidents promptly and effectively.
Multi-Tenant Unified Incident View empowers managed security service providers (MSSP) and multi-tenant administrators to centralize security operations across distributed environments with a consolidated view of all incidents within each child tenant. This enables administrators to take action, such as updating incident status, severity, and assignee across child tenants. This feature is also available in Cortex XDR 3.11.
XDR 3.11: Prevent New and Emerging Threats with Improved Efficiency
In the 2024 Forrester Wave™ for Extended Detection and Response Platforms, Cortex XDR was named a Leader in the industry, acknowledged for our commitment to disruption, ability to empower analysts to detect and respond effectively, as well as the enhancements enabling more platform features and analytics for identity and cloud. Our latest Cortex XDR 3.11 release builds on our leading extended detection and response capabilities with the introduction of new and updated protection modules to defend and prevent the latest threat techniques. These new features are also available in XSIAM 2.3.
New Protection Modules
When dealing with evolving and evasive cyberattacks, one of the more challenging aspects for defenders is detecting and preventing the unknown. When developing new features in our products, the Cortex research and development teams actively seek out the latest and greatest new tactics, techniques, and procedures (TTPs) that threat actors are using.
In doing so, we’ve taken these findings and have released new and updated protection modules in Cortex XDR 3.11 and Cortex XDR Agent 8.5 that protect against new attack techniques using in-memory shellcode, targeting the kernel, and stealing crypto wallets.
- Shellcode AI Protection Module: A new Precision AI™ machine learning module, specifically designed to tackle the evolving landscape of shellcode threats, offering Cortex customers enhanced shellcode prevention capabilities against new and unseen variations of shellcode, including in-memory shellcode attacks in Windows.
- Dynamic Kernel Protection Module: New protection module implemented at the kernel level, which loads during the boot process to protect against kernel-level threats like bootkits, rootkits, and susceptible drivers.
- Crypto Wallet BTP Support: An update to the behavioral threat protection (BTP) rules in the Financial Malware Protection module now prevents attackers trying to steal or manipulate cryptocurrency wallets stored on Windows and macOS hosts.
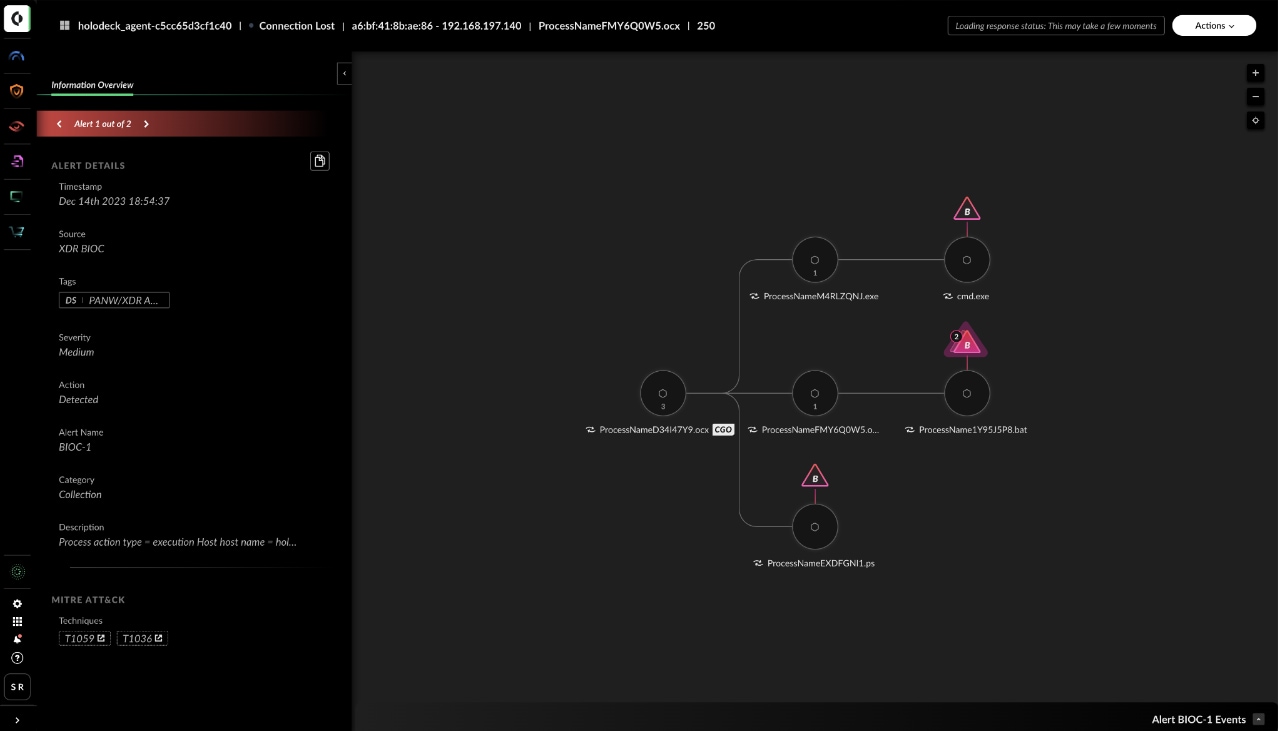
Revamped Causality Chain Interface
Today, the Cortex Causality Chain interface provides a useful but complex way to access information. To enable faster and more intuitive investigations, the alert Causality Chain interface has been revamped. The new Causality Chain Interface provides easier access to key information about an alert at each stage of the causality chain, enabling faster and more intuitive investigations, while also improving analyst workflows.
Xpanse 2.6: New Automations and Active Response Enhancements
The next advancement of our industry-leading attack surface management solution, Xpanse 2.6, delivers enhancements to some of our most incredibly powerful capabilities yet. The new capabilities include enhancements to the Threat Response Center, new remediation use cases for our Active Response Module, such as automatic patching, and lastly, usability improvements to improve the analyst’s overall efficiency.
- Threat Response Center Enhancements: Expander's Threat Response Center, which is now available in XSIAM via the ASM module, is getting several UI/UX improvements and quality-of-life enhancements, including Scope-Based Access Control (SBAC) support.
- New Active Response Enhancements: Automatically patch OpenSSH via AWS System Manager with the Active Response Module.
New usability improvements include:
- Inventory Tag Rules: Automate the tagging of assets with Inventory tag rules (formerly called asset tag rules). Inventory tag rules enable you to define custom tags and custom rules for assigning tags automatically to IPv4 addresses, IPv4 ranges, domains, certificates, and Prisma Cloud resources.
- New Inventory Fields: Gain additional context for investigating assets with new fields that have been added to tables in the inventory, including domain registrant organization, domain admin organization, certificate expiry date, certificate hash.
- New Alerts Fields: Easily investigate and remediate alerts with remediation guidance and certificate subject organization.
- Cortex Xpanse API Updates: Create custom IPv4 ranges and reassign assets to different business units using new API improvements.
- Default Attack Surface Rules list: To provide timely visibility into critical risks, we will increase the list of default rules.
XSOAR 8.7: Simplify the Security Operations’ Automation Journey
Security automation is crucial to improving operational efficiency and driving faster and more complete security incident response. In 2023, we introduced Cortex XSOAR 8 SaaS solution that delivers greater performance, scalability, and reliability, and more recently, supports on-premises deployments.
Cortex XSOAR 8.7 focuses on providing immediate value out-of-the-box with automation workflows and an overall pleasant user experience for both our SaaS and on-premises customers.
- Manage notification distribution: Admin users can now manage notification distribution by adding or removing tenant stakeholder email addresses on the Server Settings page without the need to add them first on the tenant. This feature streamlines communication and simplifies administration.
- Indicator timeline preservation: In order to effectively investigate an incident and analyze associated indicators, it is crucial for the SOC analyst to have access to up-to-date data and a clear view of the most recent changes made to the relevant indicators, as well as the initial entries of indicator changes. In this release, the Indicator Timeline Table preserves the latest activity data, enabling timely threat detection and swift response actions.
- Reports in the time zone of choice: When generating a report, you can choose the time zone to ensure accurate and localized reporting for users working in multiple geographical locations.
- New XSOAR Content Packs and Integrations
- Cortex XDR Malicious Pod Response Playbook – This new playbook helps you quickly and effectively respond to malicious activity in pods. It includes a master playbook and a sub-playbook for agent and agentless environments. The playbook automates the creation of a Lambda function, handles container registry and image verification, and integrates threat intelligence and image scanning to provide comprehensive security measures.
- Zoom Mail integration – The new Zoom Mail integration allows for email creation and deletion, user management, and streamlining message handling with attachment extraction.
- Rapid7 InsightVM – The integration update now supports creating, updating, deleting, and retrieving tags and their associations with assets and groups. It also includes commands for managing site targets and groups.
- Generic Webhook – The integration has been enhanced to support the creation of multiple incidents in a single request.
The enhanced features and capabilities listed here are just the tip of the iceberg for what we’ve packed into this Cortex release across XSIAM, XDR, Xpanse and XSOAR. Learn more about the Cortex platform by visiting https://www.paloaltonetworks.com/cortex/.