How Do I Implement MITRE ATT&CK Techniques? | Palo Alto Networks
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a comprehensive matrix of tactics and techniques threat actors use in cyber attacks. Implementing MITRE ATT&CK techniques involves understanding and utilizing the framework for various cybersecurity purposes, such as threat modeling, security assessment, and defense strategies.
Using MITRE ATT&CK techniques effectively requires a strategic approach tailored to your organization's needs and security posture. Using MITRE ATT&CK techniques is not just about defending against attacks; it's also about understanding the evolving landscape of cyber threats and continuously adapting your security posture. It's important to remember that these techniques should be part of an overall cybersecurity strategy and not the sole focus.
Key Elements of the MITRE ATT&CK Framework
The MITRE ATT&CK framework is a comprehensive matrix of tactics and techniques representing a cyber attack's various phases and methods. The framework is constantly updated to reflect the evolving nature of cyber threats.
Here's an overview of the key components, primarily for Enterprises:
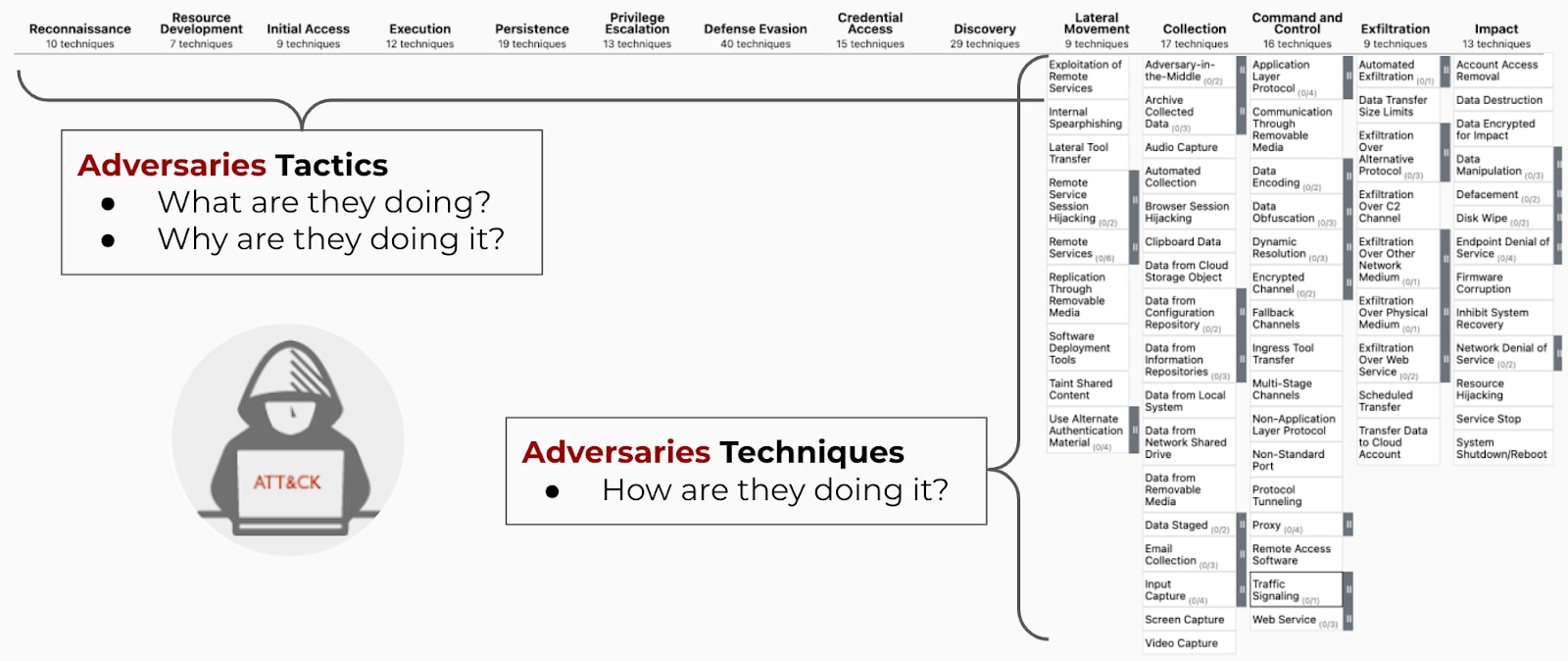
- Tactics: Tactics represent the "why" of an ATT&CK technique or sub-technique. It is the adversary's tactical goal: the reason for performing an action. For example, an adversary may want to achieve credential access.
- Techniques: Techniques represent 'how' an adversary achieves a tactical goal by performing an action. For example, an adversary may dump credentials to achieve credential access.
- Sub-techniques: These provide a more detailed breakdown of the techniques, offering a deeper understanding of how a specific technique is executed. For example, under the technique "Phishing," sub-techniques might include Spear Phishing via Email, Spear Phishing via Service, or Spear Phishing via SMS.
The ATT&CK framework is used for various purposes, such as threat intelligence, security assessment, training, and improving cybersecurity defenses. It's a living document continually updated by MITRE Corporation, based on real-world observations of cyber attacks.

The MITRE ATT&CK framework: Turla. Explore in ATT&CK Navigator. Note: The items in blue are the techniques in the MITRE ATT&CK Enterprise framework that were emulated.
How to Implement MITRE ATT&CK Techniques
In the dynamic and ever-evolving landscape of cybersecurity, the implementation of MITRE ATT&CK techniques stands as a pivotal strategy for enhancing organizational defense mechanisms against cyber threats. This comprehensive approach, which pivots around the MITRE ATT&CK framework, is a crucial roadmap for organizations seeking to bolster their cybersecurity posture.
By meticulously understanding, identifying, and adapting these techniques, organizations can fortify their defenses against potential cyber attacks and develop a more proactive and informed stance in their security strategy.
Understand the Framework
Familiarize yourself with the MITRE ATT&CK matrix, which categorizes various tactics (what an attacker is trying to achieve) and techniques (how they achieve it). The framework is available on the MITRE ATT&CK website.
Understanding the MITRE ATT&CK framework
Identify Relevant Tactics and Techniques
Identify the most relevant tactics and techniques based on your organization's environment and threat landscape. This might involve understanding the common threats in your industry or the specific vulnerabilities of your systems.
Threat Modeling
Use the framework to model potential threats against your organization. This involves thinking like an attacker and identifying which tactics and techniques they might use to compromise your systems.
Gap Analysis
Assess your current security posture against the techniques identified in the MITRE ATT&CK framework. This will help you identify gaps in your defenses.
Enhance Security Measures
Based on the gap analysis, improve your security measures. This could involve implementing new security controls, enhancing existing ones, or changing processes and policies.
Training and Awareness
Educate your security team and relevant staff about the MITRE ATT&CK techniques and how to recognize and respond to them. This training should be part of an ongoing security awareness program.
Incident Response Planning
Incorporate knowledge of these techniques into your incident response planning. Ensure that your response plans include steps to detect, investigate, and mitigate attackers' tactics and techniques.
Continuous Monitoring and Improvement
Regularly monitor your security systems for signs of these techniques. Use threat intelligence to stay updated on emerging tactics and techniques and continuously improve your defenses.
Community Engagement
Engage with the cybersecurity community to share insights and learn from the experiences of others using the MITRE ATT&CK framework.
Leverage Tools and Technologies
Utilize security tools and technologies to detect and mitigate the techniques listed in the MITRE ATT&CK framework. Many modern security solutions are designed with this framework in mind.
How to Use MITRE ATT&CK Techniques Effectively
Using MITRE ATT&CK techniques effectively requires a strategic approach tailored to your organization's needs and security posture. Here's a step-by-step guide on how to use these techniques:
- Familiarize with the Framework: Begin by thoroughly understanding the MITRE ATT&CK framework. It's a comprehensive matrix that categorizes various cyberattack tactics (the objectives behind an attack) and techniques (the methods used to achieve these objectives).
- Identify Applicable Techniques: Depending on your organization's size, industry, and specific threats, identify which techniques are most relevant. Not all techniques will be applicable, so focus on those that align with your risk profile.
- Conduct Threat Modeling: Use the framework to simulate potential attack scenarios. This involves identifying potential threats and vulnerabilities in your system and understanding how an attacker might exploit them using techniques from the framework.
- Implement Security Measures: Based on your assessment, implement or enhance security measures to defend against the identified techniques. This might involve updating software, hardening systems, implementing new security tools, or changing operational procedures.
- Training and Awareness: Educate your IT and security teams about the ATT&CK framework. Ensure they understand the tactics and techniques attackers use and how to detect and respond to them.
- Improve Incident Response: Integrate the ATT&CK framework into your incident response plan. This includes preparing to detect, respond to, and recover from attacks using identified techniques.
- Use in Red Teaming/Blue Teaming Exercises: Utilize the framework in your red team (offensive) and blue team (defensive) exercises. This helps simulate real-world attack scenarios and test how well your team can defend against them.
- Continuous Monitoring and Updating: Cyber threats are constantly evolving, so, monitor your systems for signs of attack techniques and regularly update your security strategies. Leverage threat intelligence to stay informed about new and emerging tactics and techniques.
- Leverage Automation and Tools: Employ security tools and solutions that can detect, analyze, and mitigate the techniques outlined in the ATT&CK framework. Many modern cybersecurity tools are designed to be compatible with this framework.
- Collaborate and Share Knowledge: Engage with the cybersecurity community to share insights and learn from others' experiences. Collaboration can provide valuable insights into how other organizations are using the ATT&CK framework.
Using MITRE ATT&CK techniques is not just about defending against attacks; it's also about understanding the evolving landscape of cyber threats and continuously adapting your security posture. It's important to remember that these techniques should be part of an overall cybersecurity strategy and not the sole focus.
MITRE ATT&CK Techniques Used Often by Cyber Attackers
Cyber attackers frequently use the following MITRE ATT&CK techniques. However, it's important to note that the relevance of these techniques can change rapidly as attackers adapt their strategies and organizations improve their defenses. It is critical to stay informed about the latest trends and developments in cyber threats and MITRE ATT&CK techniques.
- Spear Phishing (T1566): A targeted approach to phishing where attackers tailor their messages to specific individuals or organizations to trick victims into revealing sensitive information or installing malware.
- Credential Dumping (T1003): Involves extracting sensitive credentials like usernames and passwords, often used for further lateral movement within a network.
- Privilege Escalation (T1068): Attackers gain higher-level permissions on a system or network, often by exploiting system vulnerabilities, to gain extensive environmental control.
- Lateral Movement (T lateral_movement): Technique where attackers move through a network, gaining access to multiple systems, often using legitimate credentials.
- Command and Control (C2) (T1071): Establishing a command and control channel allows attackers to maintain communication with compromised systems, often for data exfiltration or remote manipulation.
- Malware (T1065): Using malicious software to disrupt, damage, or gain unauthorized access to a computer system.
- Data Exfiltration (T1052): Unauthorized transfer of data from a computer, often the ultimate goal of a cyber attack.
- Supply Chain Compromise (T1195): Targeting less-secure elements in the supply chain to compromise the security of the final product or system.
- Phishing (T1566.001): The practice of sending fraudulent communications that appear to come from a reputable source, usually via email, to steal sensitive data or install malware on the victim's device.
Other commonly used techniques include:
- Command and Scripting Interpreter
- Exploit Public-Facing Application
- System Information Discovery
- Brute Force
Implementing MITRE ATT&CK Techniques FAQs
MITRE ATT&CK Techniques can indeed assist in predicting future cyber attacks to some extent. While they may not predict the specifics of individual attacks, they provide a framework for understanding adversary behaviors and methodologies. This knowledge can help organizations anticipate potential attack vectors and prepare defenses accordingly.
Here’s how:
- Behavior Patterns: By analyzing past incidents, ATT&CK helps identify patterns in adversary behaviors, which can be indicative of future actions.
- Trend Analysis: Security professionals can use ATT&CK to analyze trends in cyber threats and adapt their security measures to address emerging tactics.
- Threat Intelligence: ATT&CK’s comprehensive database supports threat intelligence efforts by providing context on how certain techniques have evolved and might be used in the future.
- Proactive Defense: With insights from ATT&CK, organizations can proactively strengthen their defenses against techniques that are becoming more prevalent1.
- Security Posture Assessment: ATT&CK enables organizations to assess their current security posture against known adversary techniques and make informed predictions about potential future attacks.
While ATT&CK is a powerful tool, it’s important to note that the cyber threat landscape is constantly evolving. Therefore, continuous monitoring, updating security practices, and integrating new intelligence are crucial for staying ahead of potential threats.
Organizations should implement MITRE ATT&CK Techniques in their security strategy by following a structured approach that aligns with their business objectives and security needs.
Here’s a step-by-step guide based on best practices:
- Understand Business Objectives: Begin by aligning the security strategy with the organization’s business goals. This ensures that the implementation of ATT&CK Techniques supports the overall mission of the company.
- Assess Current Security Posture: Evaluate the existing security measures and identify gaps where ATT&CK Techniques could provide improvements. This includes understanding the threat landscape specific to the organization.
- Prioritize Techniques: Not all ATT&CK Techniques will be relevant to every organization. Prioritize the techniques based on the most likely threats and the organization’s specific vulnerabilities.
- Educate and Train Staff: Ensure that the security team and relevant staff are educated about the ATT&CK framework and understand how to apply it in practice. This includes regular training and updates as the framework evolves.
- Integrate into Security Operations: Incorporate ATT&CK Techniques into daily security operations, including threat hunting, incident response, and continuous monitoring.
- Automate and Test: Use automation to test the effectiveness of security controls against ATT&CK Techniques and conduct regular audits to ensure they are functioning as intended.
- Collaborate and Share Information: Engage with the cybersecurity community to share insights and learn from others’ experiences in implementing ATT&CK Techniques.
- Continuously Improve: Cybersecurity is an ongoing process. Regularly review and update the implementation of ATT&CK Techniques to adapt to new threats and changes in the organization’s environment1.
By systematically implementing MITRE ATT&CK Techniques, organizations can enhance their ability to detect, prevent, and respond to cyber threats more effectively.