How to Maintain AWS Compliance
Amazon Web Services (AWS) is certified in compliance such as ISO, and SOC 2. However, the way you store your data in AWS isn't always compliant.
As businesses continue to move to the cloud, data security and regulatory compliance are critical. Fortunately, Amazon Web Services (AWS®), an on-demand cloud computing platform, is certified compliant with regulations such as ISO, PCI DSS, and SOC 2. However, this does not mean the way data is stored within AWS is compliant. Just like security, compliance falls into the Shared Responsibility Model, which means AWS itself is responsible for compliance with regulations that apply to the host layer and physical infrastructure while AWS customers are responsible for compliance with regulations that apply to how they use services, consume applications and store data in the cloud.
Let’s take a step back to understand how managing compliance in an IT infrastructure traditionally looks: an organization’s compliance team takes inventory of all the organization’s IT resources. The team then reviews all resources that contain data bound by regulations and maps existing controls to corresponding regulatory requirements to prove compliance.
In AWS, however, manual compliance management falls short. Developers have the power to deploy new resources and rapidly make changes to the infrastructure – changes that often go unchecked by the security and compliance teams. To complicate matters further, even if an organization can prove compliance one day, that doesn’t mean it remains compliant two weeks – or even 24 hours – later. “Point in time” compliance quickly becomes irrelevant in the cloud.
Maintaining AWS compliance requires a new approach. Just as DevOps teams have made “continuous delivery” and “continuous innovation” parts of the everyday IT language, “continuous security” and “continuous compliance” need to be discussed just as frequently.
On the bright side, unlike managing compliance in traditional data centers, AWS infrastructure gives us a path to addressing security and compliance programmatically and automatically. The cloud provider APIs we have available now enable a whole new era of security automation. AWS Config allows an organization to use AWS APIs to access metadata about its infrastructure as well as continuously monitor and measure whether new changes introduce compliance issues.
Using AWS Config for Continuous Compliance
AWS Config allows for continuous monitoring of an environment for configuration changes and compliance with desired configuration rules, as well as viewing and management of resource relationships, all on a single dashboard (see Figure 1).
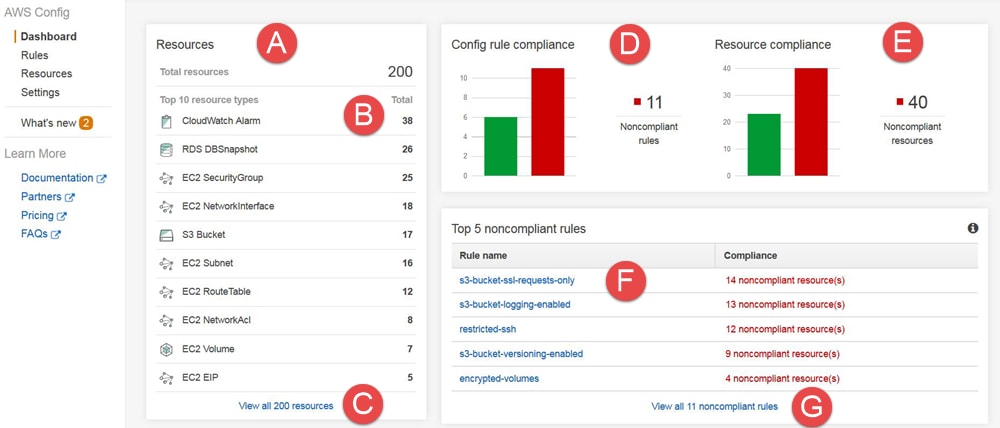
Figure 1: AWS management dashboard
There are two ways to use AWS Config for continuous compliance:
Option 1: Use Simple Notification Service for manual remediation. SNS will trigger an alert when something in the environment has changed and no longer complies with the organization’s rules. This allows for manual remediation of a problem as soon as it occurs.
Option 2: Use AWS Lambda for automated remediation. A change in the environment that results in noncompliance will trigger a Lambda function to auto-remediate. Example: A config rule states that VPC Flow logs must always be enabled. Someone turns off Flow logging, so Lambda uses API access to re-enable it.
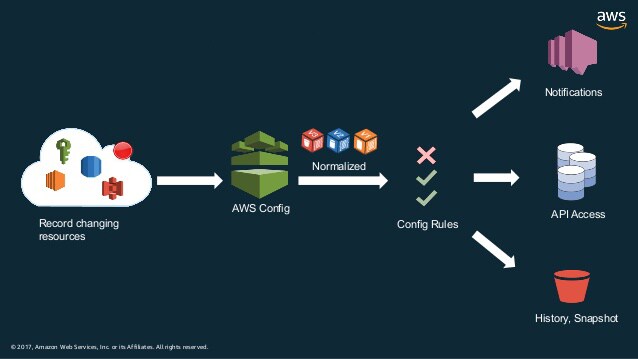
Figure 2: How AWS Config works
AWS Config provides customizable, predefined rules to administer through APIs. Administrators can also write team- and organization-specific config rules to build out more comprehensive compliance reporting. Click here for a curated community repository of custom AWS config rules.
Using AWS Services to Ensure Compliance
As mentioned previously, according to the Shared Responsibility Model, AWS is responsible for the security and compliance of the cloud infrastructure workloads run on, while customers are responsible for the compliance of the workloads themselves. However, AWS provides multiple tools to help ensure that compliance. For example:
PCI DSS Requirement 8 asks application owners to “identify and authenticate access to system components.” AWS Cognito, an authentication service that allows configuration of authentication and authorization for users and other AWS services, is commonly used to comply with this requirement.
PCI DSS Requirement 11 discusses the tracking and monitoring of all access to network resources and cardholder data. This can be done with monitoring tools such as CloudWatch and CloudTrail.
Get More Granular
As your cloud environment grows and your organization becomes more heavily regulated, you may want more granular AWS compliance reporting. For example, you may want to know how your AWS environment maps to specific compliance regulations or enable different compliance views for different teams and AWS accounts.
This is where third-party, API-based compliance tools can help. These tools are designed to allow you to continuously monitor cloud configurations for changes in real time and map these configurations to pre-built compliance templates for regulations such as ISO, SOC 2, HIPAA, PCI DSS, NIST, and GDPR. With the right compliance tool, you can easily generate compliance reports as well as demonstrate your compliance posture to auditors, customers and stakeholders with one click. For some guidelines on selecting the right tool, check out this blog post.
For more on these subjects, download the e-book Continuous Monitoring and Compliance in the Cloud.