Threat Intelligence Use Cases and Examples
Threat intelligence provides organizations with valuable information about potential cyberthreats and vulnerabilities. The ability to survey the entire threat landscape is essential, requiring organizations to prioritize threat intelligence.
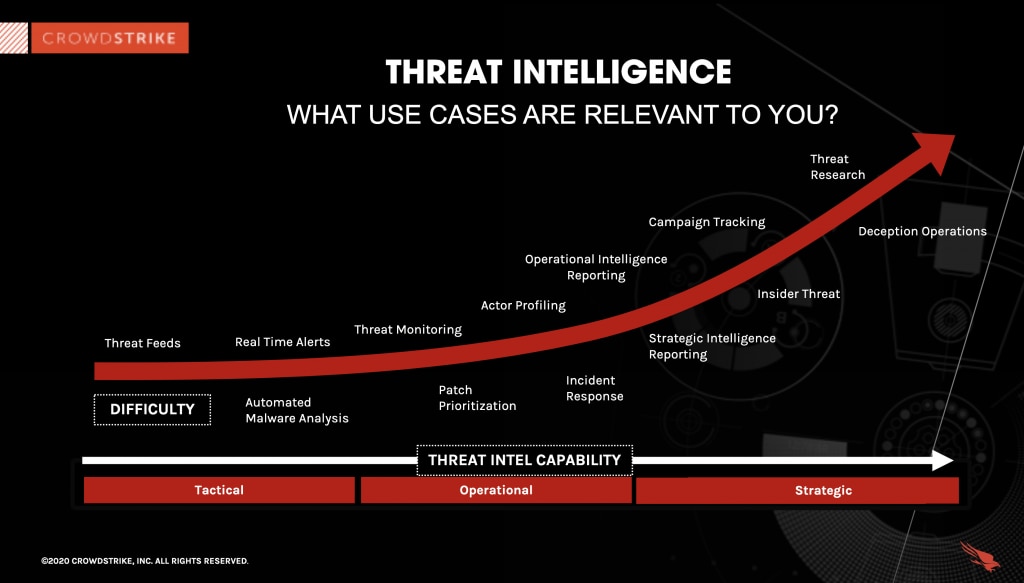
Threat intelligence use cases encompass a wide range of activities and strategies aimed at identifying, mitigating, and responding to cyberthreats. The specific use cases that are most relevant to an organization depend on its industry, size, and unique cybersecurity needs. As a rule, the more an organization relies on applications, digital tools, and technology-driven workflows for its business operations, the more use cases it identifies for threat intelligence.
What are the 4 Types of Threat Intelligence?
Understanding the various types of threat intelligence is a cornerstone of effective cybersecurity. The landscape of cyberthreats is complex and dynamic, demanding a nuanced approach to defense. In this exploration, the focus is on the different categories of threat intelligence - tactical, operational, strategic, and technical - each serving a distinct purpose. These types are dissected to reveal their unique roles in helping organizations anticipate, identify, and respond to cyberthreats, providing a comprehensive view of how they collectively fortify cybersecurity measures.
Strategic Threat Intelligence
Strategic threat intelligence refers to the broad analysis of the cyberthreat landscape with an emphasis on long-term trends. Its core purpose is to inform decision-makers about the overarching cyber risks that could impact an organization's future. Strategic threat intelligence is the starting point of an enterprise-wide cybersecurity intelligence program.
Unlike its more immediate counterparts, strategic intelligence deals less with the technical specifics of daily threats and more with the analysis of potential future risks, emerging threat patterns, geopolitical developments, and the implications of new technologies and laws on cybersecurity.
Tactical Threat Intelligence
Tactical threat intelligence provides detailed information on the tactics, techniques, and procedures (TTPs) employed by cyberthreat actors. Its purpose is to give IT security teams the insights formed from comprehensive data collection to strengthen defenses and respond to threats in real time. Tactical intelligence often includes specifics such as malware signatures, indicators of compromise (IoCs), and analysis of threat actor behavior.
This type of intelligence focuses on the current methods attackers use, offering insights into the latest cyberthreats. Security teams use this information to update firewalls, enhance security protocols, and train personnel to recognize and mitigate these risks. Tactical intelligence keeps pace with the rapidly changing threat landscape, enabling security measures to be as current as possible.
Operational Threat Intelligence
Operational threat intelligence pertains to the specifics of individual cyberthreats and campaigns. It provides insights into the motivations, targets, and methods of attackers, often in real time. This intelligence is crucial for incident response teams who need to understand the context of an attack to effectively counteract it.
Technical Threat Intelligence
Technical threat intelligence allows teams to conduct proactive threat hunting, analyze security incidents in depth, and locate forensic evidence, which is critical for defending against and mitigating the impact of cyberattacks. It also provides a foundation for enhancing security measures, keeping systems updated against known threats, and improving an organization’s resilience.
Top 4 Use Cases for a Threat Intel Platform (TIP)
A threat intelligence platform (TIP)’s primary goal is to help organizations proactively defend against cyberthreats by providing timely and relevant information about intent and capabilities of relevant threat actors. The platform plays an important role in cybersecurity strategy, enabling organizations to enhance their threat detection, response, and mitigation capabilities.
There are many use cases where cybersecurity threat intelligence plays a critical role in the digital health of an organization, its people, and its assets. These use cases fall into several broad categories, including:
- Threat Identification
- Threat Prevention
- Threat Remediation
1. Incident Enrichment Using Threat Intel Data
Problem: Most tools that security operations centers (SOCs) and incident response (IR) teams use to respond to alerts are very generic. There is not much correlation between network data and understanding of threats and attacker movements.
Many times there is a dump of information including bad IP addresses or domains and someone has to be assigned to resolve them and figure out false positives manually. In addition, there is a lack of understanding of malicious families, hacking tools and their patterns of attacks.
This process is cumbersome, takes a lot of time, and is impractical. This is especially true in the present security scenario, where hundreds, if not thousands, of indicators are collected daily.
Solution: Accelerating incident response with TIP and alert enrichment using threat intelligence (TI) data.
Incident enrichment workflow in Cortex XSOAR Threat Intelligence Management (TIM) leverages TI from their very own high-fidelity centralized threat intelligence library.
Research data from Unit 42® to learn more about:
- Known malware campaigns or families
- IPs and domains with WHOIS data
- Passive DNS data
- Web categorization data
The video below provides you with a glimpse into our next release, TIM 3.0, and explores the enhancements and capabilities listed above, including how they can assist you in responding to incidents with confidence.
2. Proactive Blocking of Threats
Problem: The security team needs to leverage TI to block or alert on indicators of compromise (IoC) such as known bad domains, IPs, and hashes, using detection response tools and techniques. The indicators are being collected from many different sources that need to be normalized, scored, and analyzed before the customer can push to security devices such as SIEM and firewall for alerting. Detection tools can only handle limited amounts of TI data and must constantly re-prioritize indicators.
Solution: Proactive threat monitoring with playbook-driven automation.
With indicator prioritization, you can ingest alerts from email inboxes through integrations. Once an alert is ingested, a playbook is triggered and can have any combination of automated or manual actions that users desire. The playbooks can have filters and conditions that execute different branches depending on certain values.
Here is a demo of how TIM works with proactive blocking of threats.
3. Intelligence Reporting and Distribution
Problem: TI programs have a growing set of responsibilities. One key responsibility is producing and disseminating TI reports that keep employees updated on the latest threats targeting their industry.
Most intelligence is still shared via unstructured formats such as email and blogs. Sharing information about IOC is not enough. Additional context is required for the shared intelligence to have value.
Analysts go through hours of manual work to create reports by performing the following activities:
- Aggregating and digging for news of known malware families
- Curating news and threats related to the company or vertical for an industry
- Describing why the stories are relevant to the company
The analysts then need to send this report to a large audience to raise security awareness and alert other stakeholders so they can facilitate better-informed decisions in the future.
Solution: Workflows and a central repository for intelligence analysts to create, collaborate and share finished intelligence products with stakeholders via PDF reports. Intel analysts will be able to understand trends within TI using their local/curated intel and Unit 42 Threat Intelligence.
4. External Threat Landscape Modeling
Problem: TI teams need to understand details of attacks and how their organization may be vulnerable. The foundational element of understanding risk/impact to an organization begins when threat analysts begin profiling the attacks.
Solution: Threat modeling is employed to prevent or mitigate the impact of threats on the system. The threat intel team is responsible for contsructing profiles of threat actors, determining the existence of elated attacks, and identifying the techniques and tools used by the threat actor. Subsequently, this information is shared with key stakeholders, including security operations and leadership team.
See this demo to see how external threat landscaping is done in a real scenario.
Together, these use cases form the basis of a cybersecurity threat intelligence framework that acts as a guideline for using various threat intelligence sources to spot potential cyber problems before they have a substantial impact. Threat intelligence use cases typically align with one or more different types of threat intelligence.
Watch our video to see how external threat landscaping is done in a real scenario.
Specific Examples of Threat Intelligence Use Cases
MITRE ATT&CK as a Threat Intelligence Use Case
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a security framework threat hunters use. Organizations use MITRE ATT&CK to determine the tactics, techniques, and procedures (TTPs) used by cyber adversaries. TI teams and organizations can use MITRE ATT&CK in various ways to enhance their cybersecurity efforts.
Here are several ways MITRE ATT&CK can be used for TI:
- Security Operations: Security teams can use ATT&CK to match real-time events and behaviors to known attack patterns, enhancing detection and response capabilities.
- Threat Hunting: Threat hunters can leverage ATT&CK to search for new, or previously undetected, activities within an environment that aligns with known adversary behaviors.
- Red Teaming/Adversary Emulation: Teams can use ATT&CK to emulate an adversary's TTPs and test the effectiveness of security controls and incident response capabilities.
- Gap Analysis: ATT&CK can help organizations identify and prioritize the security gaps adversaries most likely exploit. It can show which tactics and techniques are not adequately covered by existing defenses.
- Security Assessment and Engineering: Engineers can use the ATT&CK framework to design and assess security architectures, ensuring that controls are in place to detect or mitigate specific adversary behaviors.
- Incident Response: Incident responders can use ATT&CK to categorize adversary behavior during an investigation, allowing them to determine the scope of an intrusion and develop effective remediation plans.
- Threat Intelligence: Analysts can compare external threat reports with the ATT&CK framework to understand adversaries' tactics and procedures and communicate about them using a common language.
- Education and Training: ATT&CK can serve as a training guide for new cybersecurity professionals to understand common adversary behaviors and the lifecycle of cyberattacks.
- Behavioral Analytics Development: Security teams can develop new analytics based on ATT&CK to detect adversarial behavior across different stages of the attack lifecycle.
- Risk Assessment: Risk management teams can use ATT&CK to better understand the risks associated with specific adversary behaviors and develop strategies to mitigate those risks.
Using MITRE ATT&CK involves integrating the framework into various cybersecurity practices to improve understanding, detection, and prevention of cyber threats. MITRE ATT&CK helps organizations understand who is targeting them and their industry, allowing for more informed threat response and proactive defense measures. It can also aid in sharing TI with the broader cybersecurity community.
While MITRE ATT&CK provides a valuable framework for understanding adversary behavior, it may not always lead to conclusive attribution on its own. Nonetheless, it is a critical tool for building a comprehensive understanding of the tactics and techniques used by threat actors, aiding in defense and response efforts.

