Next-gen CASB
- Why is SaaS security important?
- What is SaaS security posture management (SSPM)?
- What are the layers of SaaS security?
- What is SaaS security architecture?
- What are the benefits of SaaS security?
- What are the primary SaaS security challenges?
- What are the common SaaS security risks and threats?
- How are cloud security and SaaS security related?
- Top 16 SaaS security best practices
- What SaaS security tools are available?
- 2025 SaaS security trends
- SaaS security FAQs
What Is SaaS Security? | Definition & Explanation
SaaS security is the protection of cloud-based software applications and data from unauthorized access and cyberthreats.
SaaS security involves implementing controls like authentication, encryption, and monitoring to preserve the integrity and confidentiality of data. Effective SaaS security also includes ensuring compliance and third-party service provider risk mitigation.
- Why is SaaS security important?
- What is SaaS security posture management (SSPM)?
- What are the layers of SaaS security?
- What is SaaS security architecture?
- What are the benefits of SaaS security?
- What are the primary SaaS security challenges?
- What are the common SaaS security risks and threats?
- How are cloud security and SaaS security related?
- Top 16 SaaS security best practices
- What SaaS security tools are available?
- 2025 SaaS security trends
- SaaS security FAQs
- 1. Why is SaaS security important?
- 2. What is SaaS security posture management (SSPM)?
- 3. What are the layers of SaaS security?
- 4. What is SaaS security architecture?
- 5. What are the benefits of SaaS security?
- 6. What are the primary SaaS security challenges?
- 7. What are the common SaaS security risks and threats?
- 8. How are cloud security and SaaS security related?
- 9. Top 16 SaaS security best practices
- 10. What SaaS security tools are available?
- 11. 2025 SaaS security trends
- 12. SaaS security FAQs
Without the right SaaS security measures, businesses can fall victim to data breaches, ransomware, or other cyber threats. As we all know, these incidents can cause major damage, ranging from financial losses to reputational damage.
What is SaaS security posture management (SSPM)?
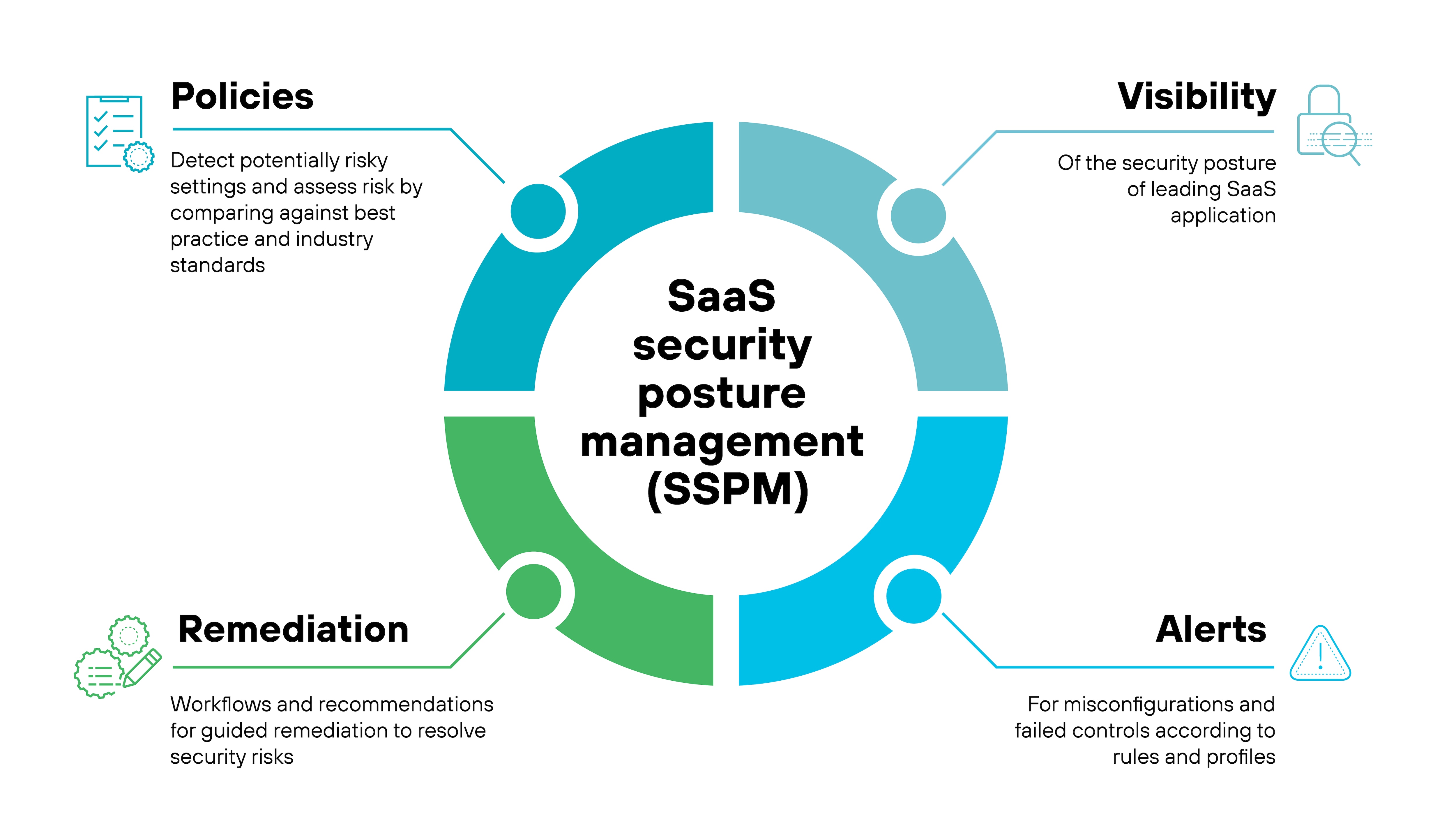
SaaS security posture management (SSPM) is a specialized toolset or approach within SaaS security that continuously monitors and assesses the configurations of SaaS applications to identify and address security risks.
SSPM focuses on ensuring proper application configuration to meet security policies and compliance standards. SSPM tools are designed to automatically detect misconfigurations, over-privileged user accounts, and other vulnerabilities. The objective is to reduce the manual effort needed to maintain secure SaaS environments.
Ultimately, by providing real-time visibility and automatic remediation, SSPM helps organizations minimize security risks and maintain regulatory compliance.
What are the components of SaaS security?
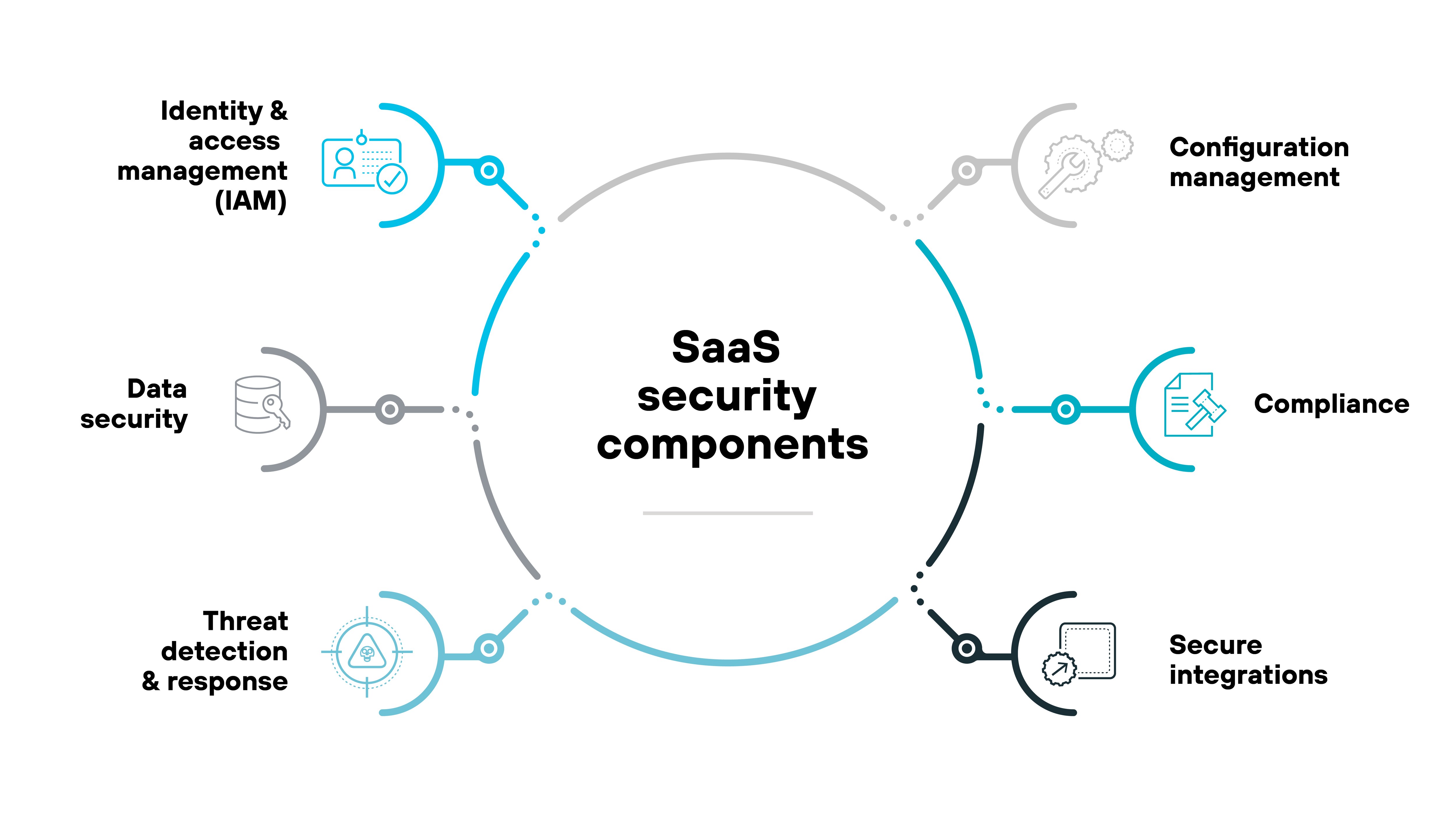
Securing SaaS applications involves addressing several key components that make up the overall security framework of SaaS applications. SaaS security components work together to protect data, compliance, and overall system integrity.
Each SaaS security component listed here plays a key role in reducing security risks and maintaining a secure environment for both organizations and users:
- Data security
- Identity and access management (IAM)
- Compliance
- Threat detection and response
- Configuration management
- Secure integrations
Data security
Data security is central to SaaS security. It focuses on protecting sensitive information using methods like encryption for data in transit and at rest.
Strong access controls and secure backup systems help prevent unauthorized access and mitigate the risk of data breaches. By securing data, organizations ensure the integrity and confidentiality of their critical assets.
Identity and access management (IAM)
IAM is essential for controlling user access to SaaS applications. It involves managing user identities and assigning appropriate access privileges.
Tools like multi-factor authentication and role-based access controls are key to reducing the risk of unauthorized access.
Overall, IAM helps ensure that only authorized users can interact with sensitive data, strengthening the security framework.
Compliance
As with all security practice areas, SaaS security includes compliance activities focused on making certain that SaaS applications meet regulatory requirements like GDPR or HIPAA.
Regular audits and enforcement of data handling policies help organizations mitigate compliance risks.
Threat detection and response
Detecting and responding to threats is a fundamental part of SaaS security. This involves using advanced threat detection tools, like AI-driven analytics, to identify unusual behavior or potential vulnerabilities.
Quick response mechanisms are critical to neutralizing threats before they lead to significant damage.
Configuration management
Proper configuration management is about making sure that SaaS applications are securely set up and maintained. Which means establishing secure baseline configurations and continuously monitoring for misconfigurations.
When you address misconfigurations early, you avoid vulnerabilities that attackers can exploit.
Secure integrations
Today, SaaS applications integrate with third-party software more often than not. And that can introduce security risks.
Securing integrations is essential to avoid creating new vulnerabilities. Continuously verifying that data transfers and communications between systems are secure helps maintain the overall security posture of the SaaS environment.
What are the layers of SaaS security?
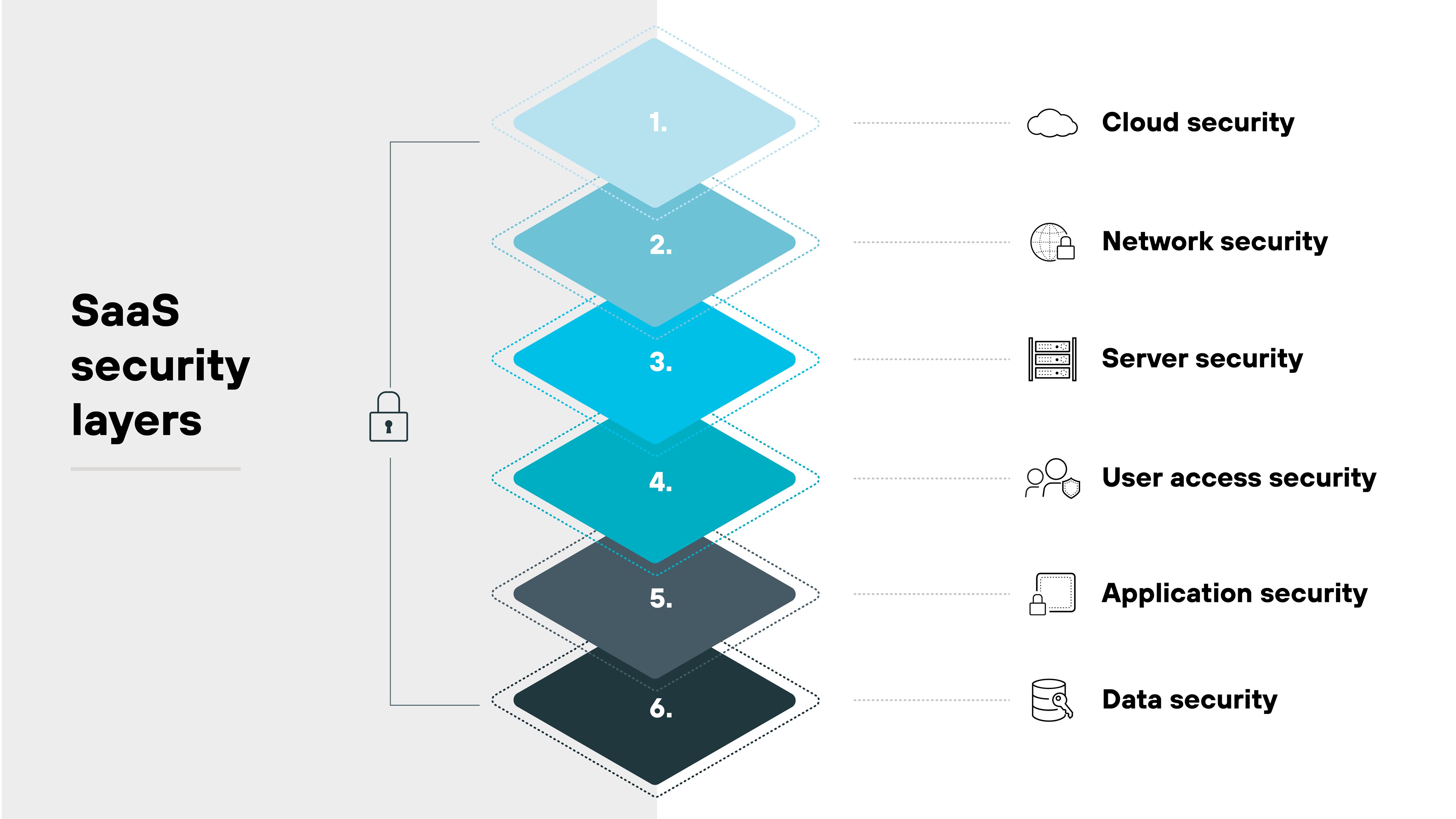
SaaS security applies different security measures which work together to provide defense at various levels, ensuring the protection of the applications and the data they process.
Each layer addresses a specific aspect of security, creating a robust defense system to prevent breaches and ensure compliance.
Here’s a breakdown of the key layers, which include:
- Cloud security
- Network security
- Server security
- User access security
- Application security
- Data security
Cloud security
The foundation of SaaS security begins with cloud security.
This layer includes securing the physical infrastructure of data centers through measures such as access controls, surveillance, and environmental protections. It also involves adhering to compliance regulations to ensure the provider meets legal requirements.
Cloud security matters because any vulnerabilities here could compromise the entire security structure of the SaaS environment.
Network security
Network security is critical in protecting communication between users and SaaS applications. It prevents unauthorized access and secures data transfers using a combination of firewalls, encryption protocols, and IDSes to filter out harmful traffic.
Plus, applying a zero-trust model strengthens security by continuously verifying users and devices before granting access. In other words: It ensures only trusted entities can communicate with the SaaS environment.
By monitoring and controlling network traffic, network security reduces the risk of threats from inside or outside the network.
Server security
Proper server security helps ensure the safe hosting of critical SaaS components. Servers, which host both SaaS applications and sensitive data, require specific security measures.
These include: hardening operating systems, limiting user access, and keeping software up-to-date with patch management.
Additional tools like antivirus software and intrusion detection systems provide further protection against both external and internal threats.
User access security
User access security focuses on managing who can access the SaaS application and its data.
It involves implementing multi-factor authentication (MFA), role-based access controls (RBAC), and regularly reviewing user permissions.
By limiting access to only authorized individuals and regularly educating users about security best practices, organizations reduce the risk of unauthorized access or insider threats.
Application security
This layer focuses on securing the SaaS applications themselves.
Secure coding practices, like input validation and output encoding, help prevent attacks like cross-site scripting (XSS).
Error handling mechanisms also protect sensitive information from exposure. Protecting the application’s code is essential to maintaining the integrity and functionality of the software while minimizing vulnerabilities.
Data security
As mentioned, data security ensures the confidentiality, integrity, and availability of data within SaaS applications. Encryption, data backup systems, and secure decommissioning procedures help protect data from unauthorized access and loss.
Plus: Maintaining a chain of custody ensures the organization is securely handling data and properly disposing of it when no longer needed.
Data security is a crucial layer that guarantees sensitive information stays safe throughout its lifecycle.
What is SaaS security architecture?
SaaS security architecture is the structural framework designed to ensure the security of SaaS applications and data. It incorporates multiple layers, techniques, and practices to prevent security threats and ensure compliance.
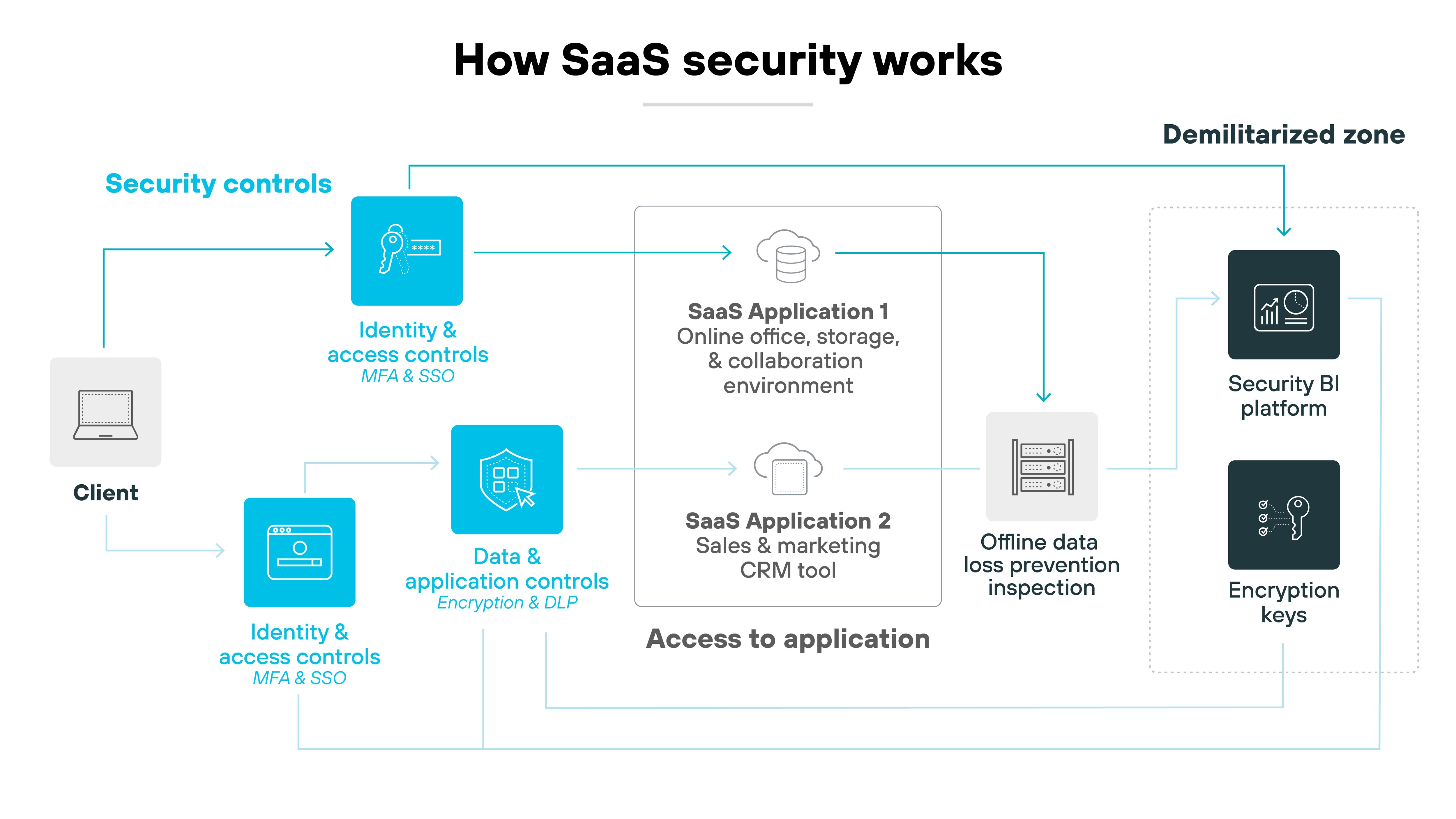
Here’s a breakdown of the core components of SaaS security architecture, including:
- Separation between tenants
- Security observation and data analysis
- Coordination with external services
- Conformity and oversight
- Recovery from disasters and ongoing business operations
Separation between tenants
In a multi-tenant SaaS environment, where multiple clients share the same application, tenant isolation is crucial. Each tenant's data and activities need to be completely separate from others.
SaaS providers typically accomplish Isolation by using separate databases for each tenant or applying encryption and access control measures to protect customer data.
Security observation and data analysis
Continuous monitoring and analysis are fundamental to maintaining SaaS security. Taking a proactive approach allows security teams to detect malicious actions and respond to any incidents quickly.
By using tools like security information and event management (SIEM) platforms, organizations can observe user behavior, detect anomalies, and identify potential security risks.
Coordination with external services
As discussed, SaaS applications integrate with external services via APIs. And API integration can introduce potential security risks.
Securing API connections is vital to prevent vulnerabilities from insecure links or data transfers. Implementing strong authentication and encryption for third-party connections reduces the risk of exposing sensitive data through insecure integrations.
Conformity and oversight
SaaS security architecture must align with regulatory requirements. Regular compliance checks and audits are necessary so you know for sure that SaaS providers are following the necessary security protocols and providing a sound environment for users.
Recovery from disasters and ongoing business operations
A resilient SaaS architecture also incorporates strategies for disaster recovery and business continuity.
This includes: Regular backups, redundant systems, and predefined recovery methods. It’s essential to be certain the SaaS service can quickly recover from unexpected events or failures.
Not to mention: DR and business continuity efforts help maintain operations and minimize downtime in case of a security breach or system failure.
What are the benefits of SaaS security?

While implementing a strong SaaS security framework isn’t a choice, doing so does offer numerous advantages to organizations.
These benefits help ensure sensitive data is protected, compliance requirements are met, and business operations remain efficient and secure.
Let’s break down the key benefits of SaaS security:
- Enhanced visibility and control
- Data protection and integrity
- Reduced threat exposure
- Operational efficiency with automation
- Business continuity and resilience
- Cost savings
Enhanced visibility and control
SaaS security solutions provide centralized visibility into applications, user activities, and data flows.
Which makes it possible to monitor access, detect unauthorized use, and ensure compliance with security policies. And that makes it way easier to manage and control SaaS environments—and reduce potential security risks.
Data protection and integrity
Data protection is one of the core benefits of SaaS security.
By ensuring the confidentiality and accuracy of sensitive data, SaaS security frameworks minimize the risk of data breaches and unauthorized modifications. This not only helps safeguard critical assets but also fosters trust among customers, stakeholders, and partners.
Reduced threat exposure
SaaS security incorporates dynamic threat detection and behavior analytics to identify and mitigate risks from phishing, malware, and other cyber threats.
By staying ahead of evolving attack vectors, SaaS security helps reduce the likelihood of successful attacks. Proactively addressing threats ensures a stronger, more resilient security posture for businesses.
Operational efficiency with automation
Automation plays a significant role in SaaS security. Tasks like access management, compliance monitoring, and incident response can be automated, saving time and resources.
This reduces the manual effort required to maintain a strong security posture while ensuring consistency and accuracy across processes.
Business continuity and resilience
SaaS security ensures that organizations can maintain operations even during cyber incidents.
With strategies like disaster recovery plans, secure data backups, and quick incident response capabilities, businesses can minimize downtime. Which leads to business continuity and resilience—allowing companies to recover swiftly from unexpected events.
Cost savings
By preventing data breaches, reducing shadow SaaS use, and optimizing application usage, SaaS security helps organizations save money.
Savings can be reinvested into growth and innovation, rather than things like recovery efforts, fines, or fixing security flaws. Investing in SaaS security can ultimately lead to long-term financial benefits.
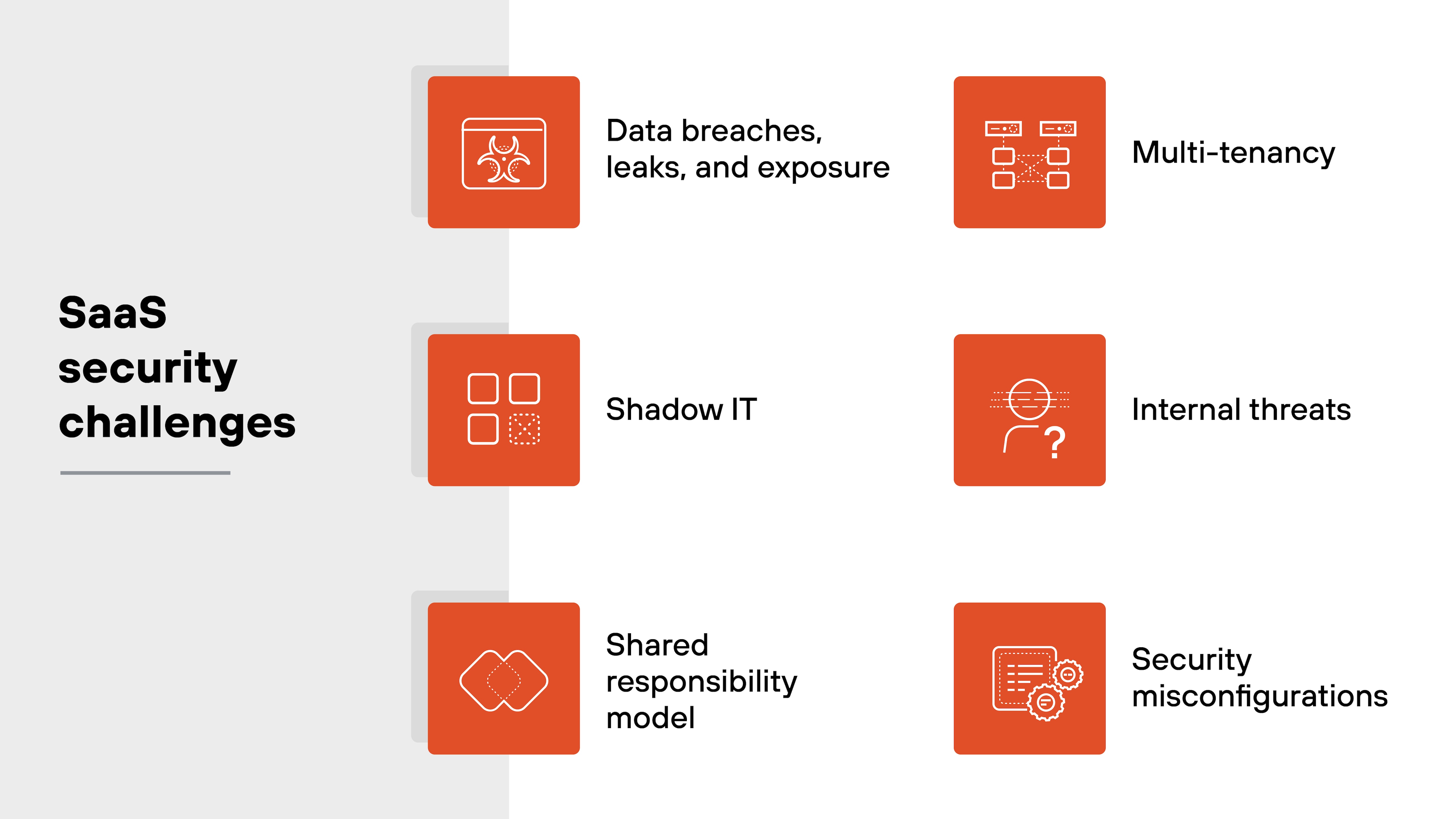
Securing SaaS applications does come with several hurdles that organizations have to address.
The most common SaaS security challenges organizations tend to encounter include:
- Data breaches, leaks, and exposure
- Shadow IT
- Shared responsibility model
- Multi-tenancy
- Internal threats
- Security misconfigurations
Let’s explore some of the primary security challenges businesses face when adopting SaaS solutions.
Data breaches, leaks, and exposure
Data breaches happen when unauthorized users access sensitive information stored in SaaS applications.
Because of the nature of cloud-based environments, SaaS providers are prime targets for attackers.
Data leaks and exposure can result from misconfigurations, weak access controls, or inadequate encryption, making SaaS platforms vulnerable to significant data compromises—and by extension, potentially their customers.
Shadow IT
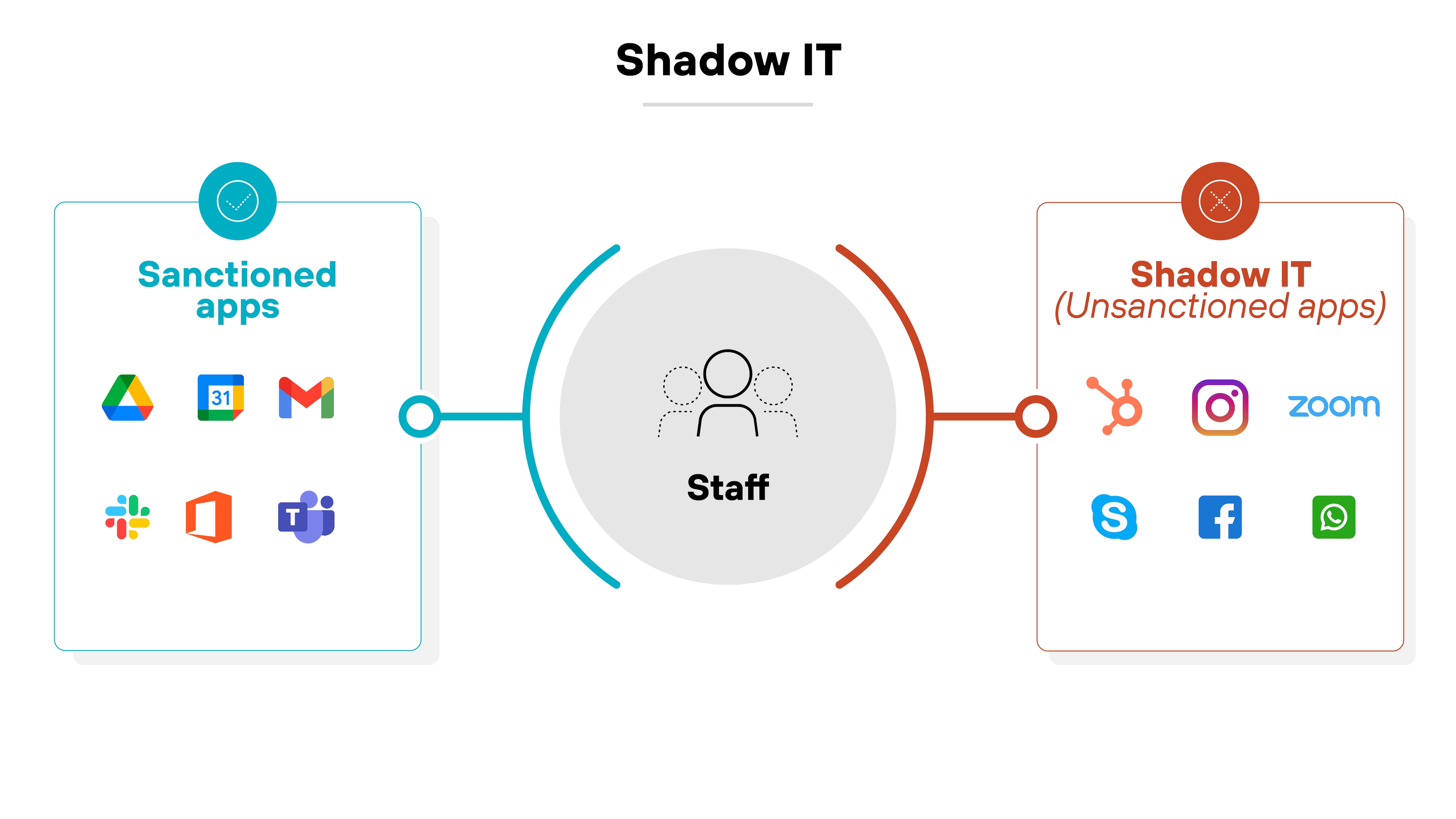
Shadow IT is perhaps one of the most frustrating and well-known challenges when it comes to Saas security. And as we all know, it refers to the use of unauthorized SaaS applications by employees without the knowledge or approval of the IT or security teams.
These applications often bypass organizational security policies and can expose sensitive data. So it’s important to make sure that employees are using only approved applications and continuously monitor for unauthorized ones.
Shared responsibility model
In a SaaS environment, the provider and the customer share security responsibilities. The cloud provider is responsible for securing the infrastructure, while the customer has to manage access control and protect their own data.
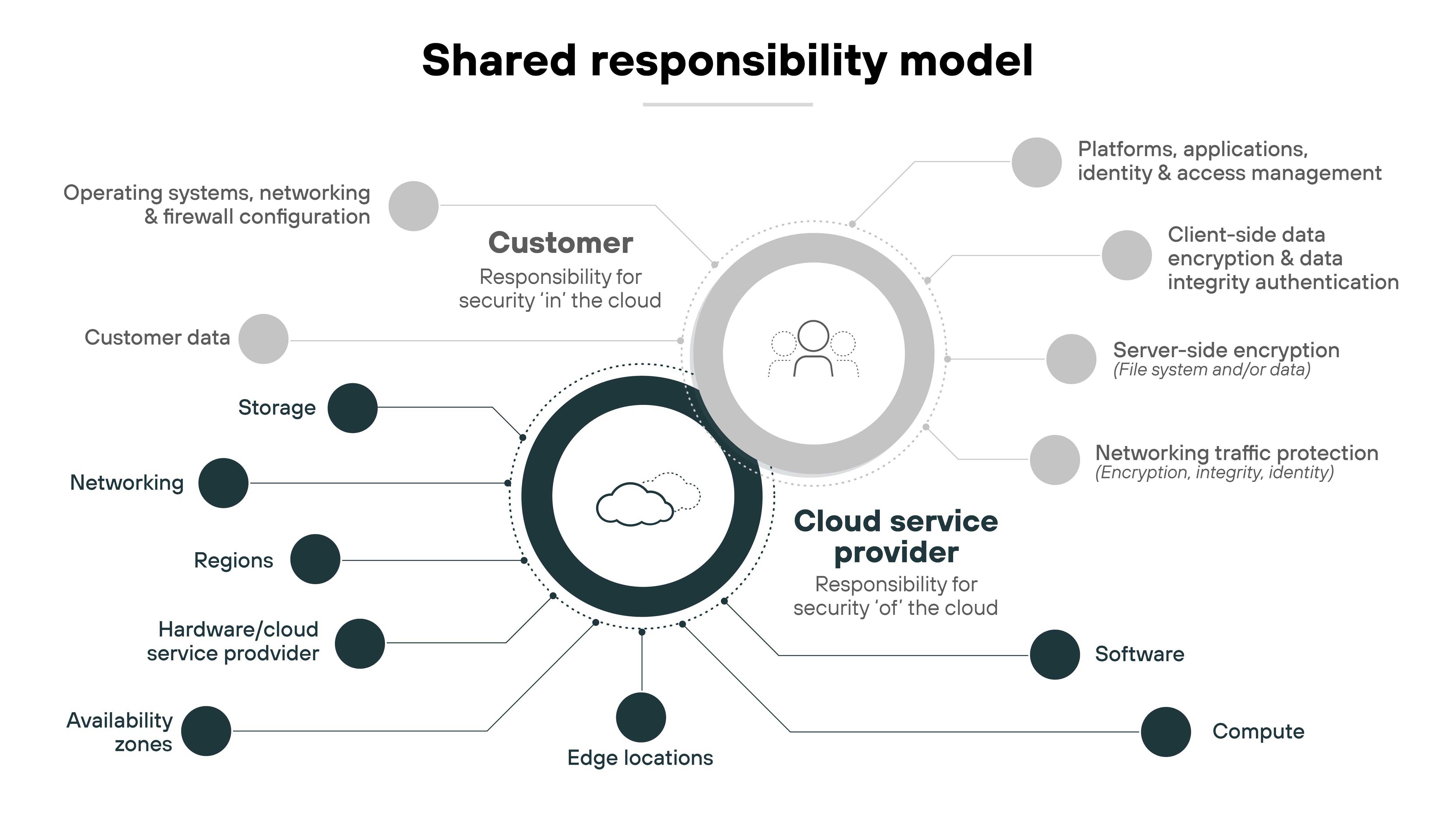
Shared responsibility can sometimes create confusion about who’s accountable for what. And that can lead to potential gaps.
Multi-tenancy
Most SaaS applications use a multi-tenant architecture, where multiple customers share the same resources.
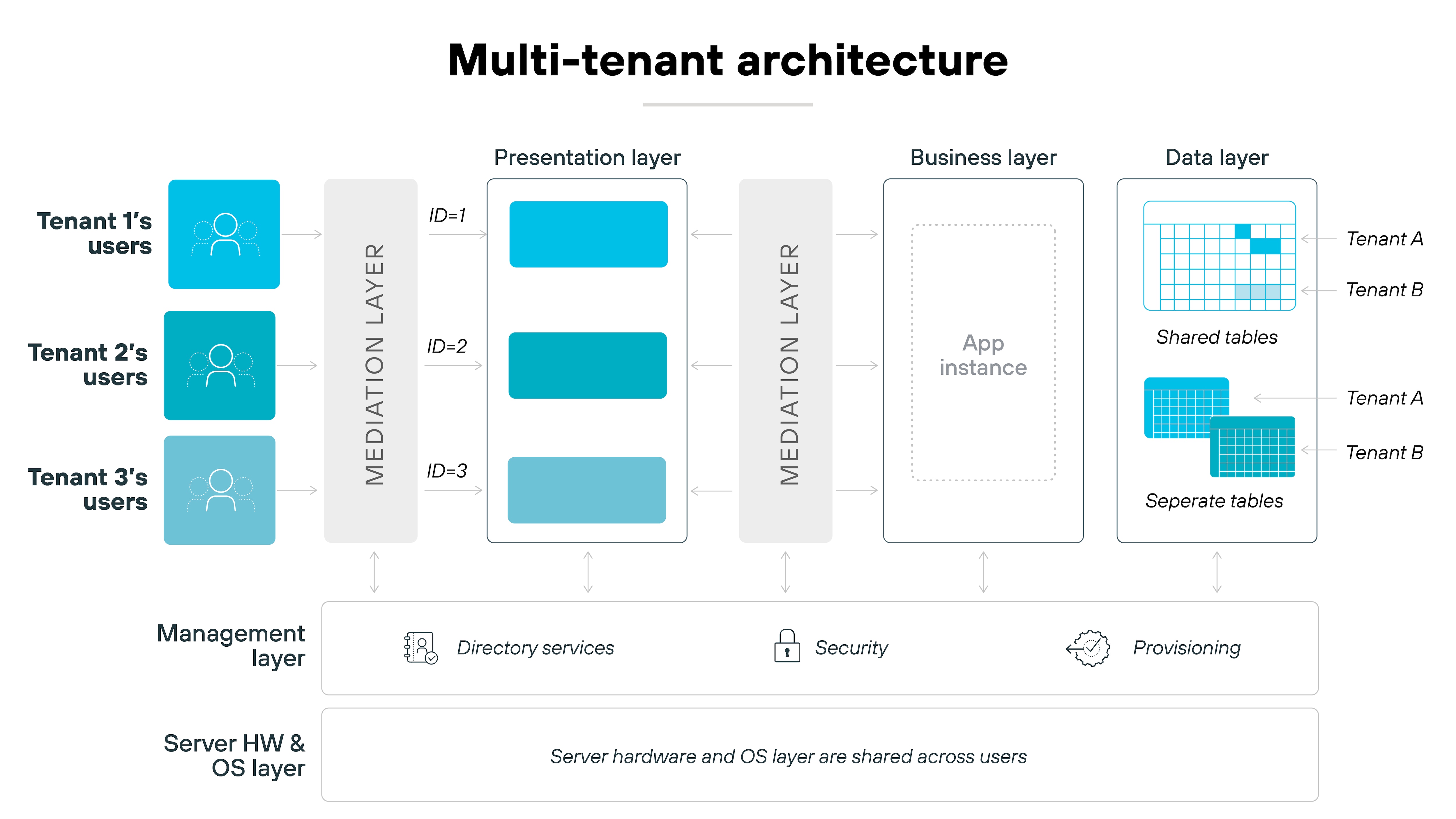
While this model is cost-effective, it can theoretically pose security risks if tenant data isn’t properly isolated. And inadequate isolation measures can then lead to data leaks or unauthorized access between tenants.
Internal threats
Security threats don’t always come from external actors. Employees, whether intentional or accidental, can pose a substantial security risk within SaaS applications.
With broad access permissions often granted to users, it can be tough to prevent or detect insider threats. Which makes access management and monitoring a key priority.
Security misconfigurations
Security misconfigurations happen when SaaS applications are improperly set up or maintained—usually because of default settings that don't meet security needs. One mistake, like an admin error, can expose sensitive data to the public internet.
What are the common SaaS security risks and threats?
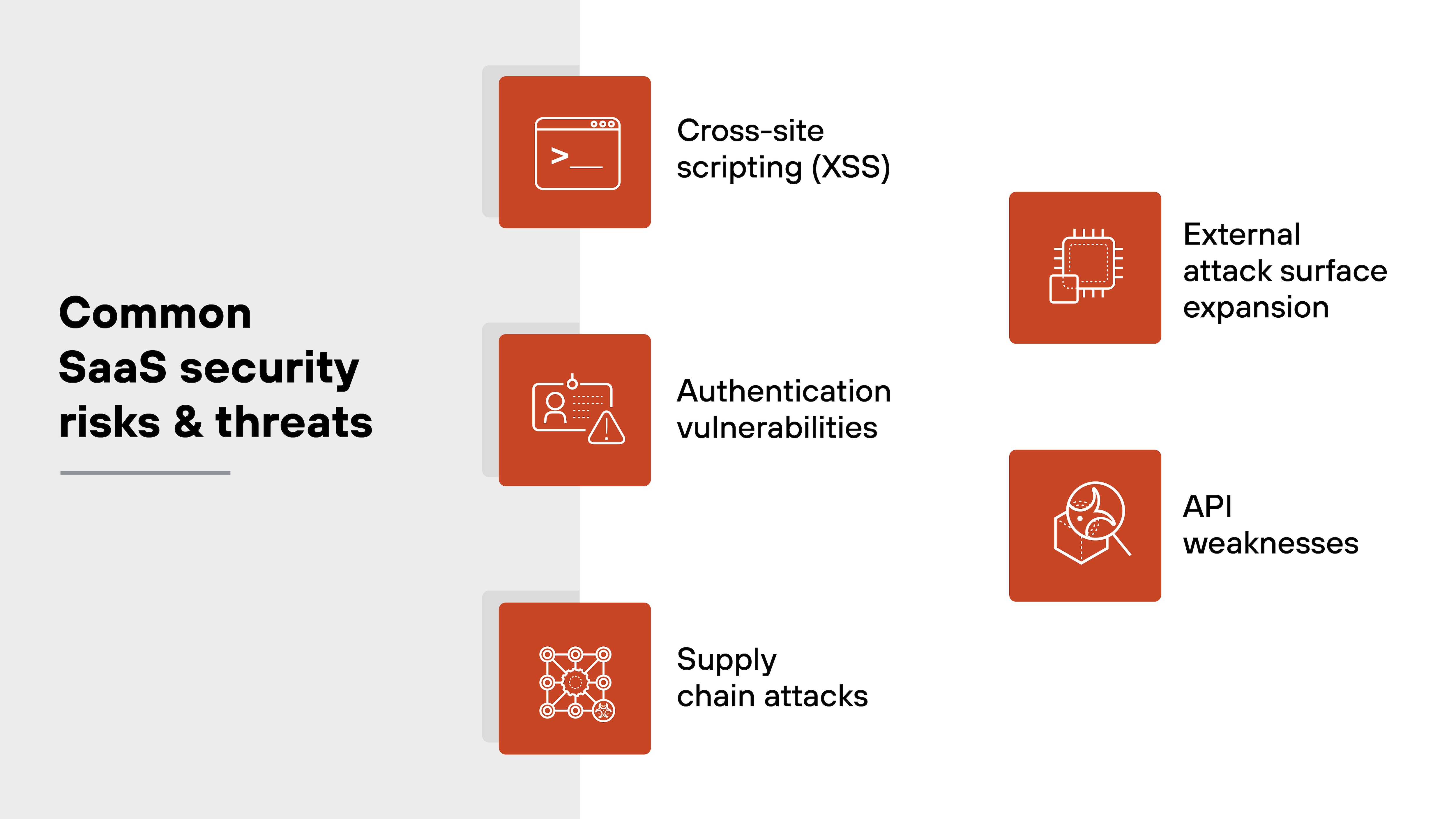
The need for SaaS security is precipitated by a number of cyber risks and threats that all organizations have to grapple with.
Let's take a look at the most common SaaS security risks and threats, which include but aren’t limited to:
- Cross-site scripting (XSS)
- Authentication vulnerabilities
- Supply chain attacks
- External attack surface expansion
- API weaknesses
Cross-site scripting (XSS)
Cross-site scripting (XSS) occurs when attackers inject malicious scripts into web pages users are viewing. These scripts can steal data, compromise session integrity, or perform actions on behalf of the user.
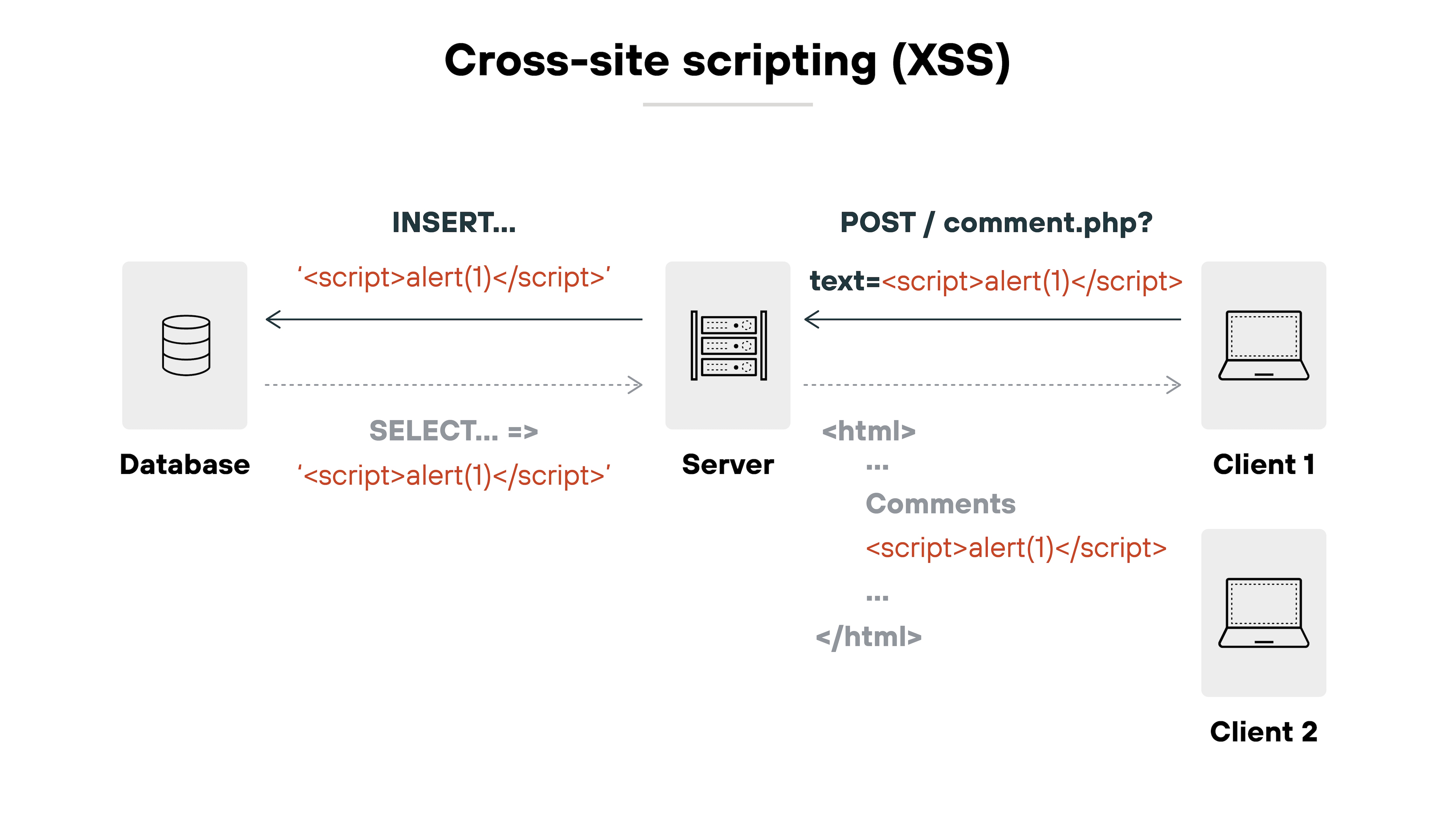
XSS vulnerabilities in SaaS applications can seriously jeopardize user security and lead to unauthorized access to sensitive information.
Authentication vulnerabilities
Authentication vulnerabilities are weaknesses in the mechanisms used to verify the identity of users. Inadequate authentication, like single-factor authentication, exposes SaaS applications to unauthorized access.
Authentication vulnerabilities are especially risky in cloud environments—where you really need strong access control to protect sensitive data and prevent unauthorized users from exploiting system weaknesses.
Supply chain attacks
Supply chain attacks target third-party SaaS providers or vendors to infiltrate their customers’ systems.
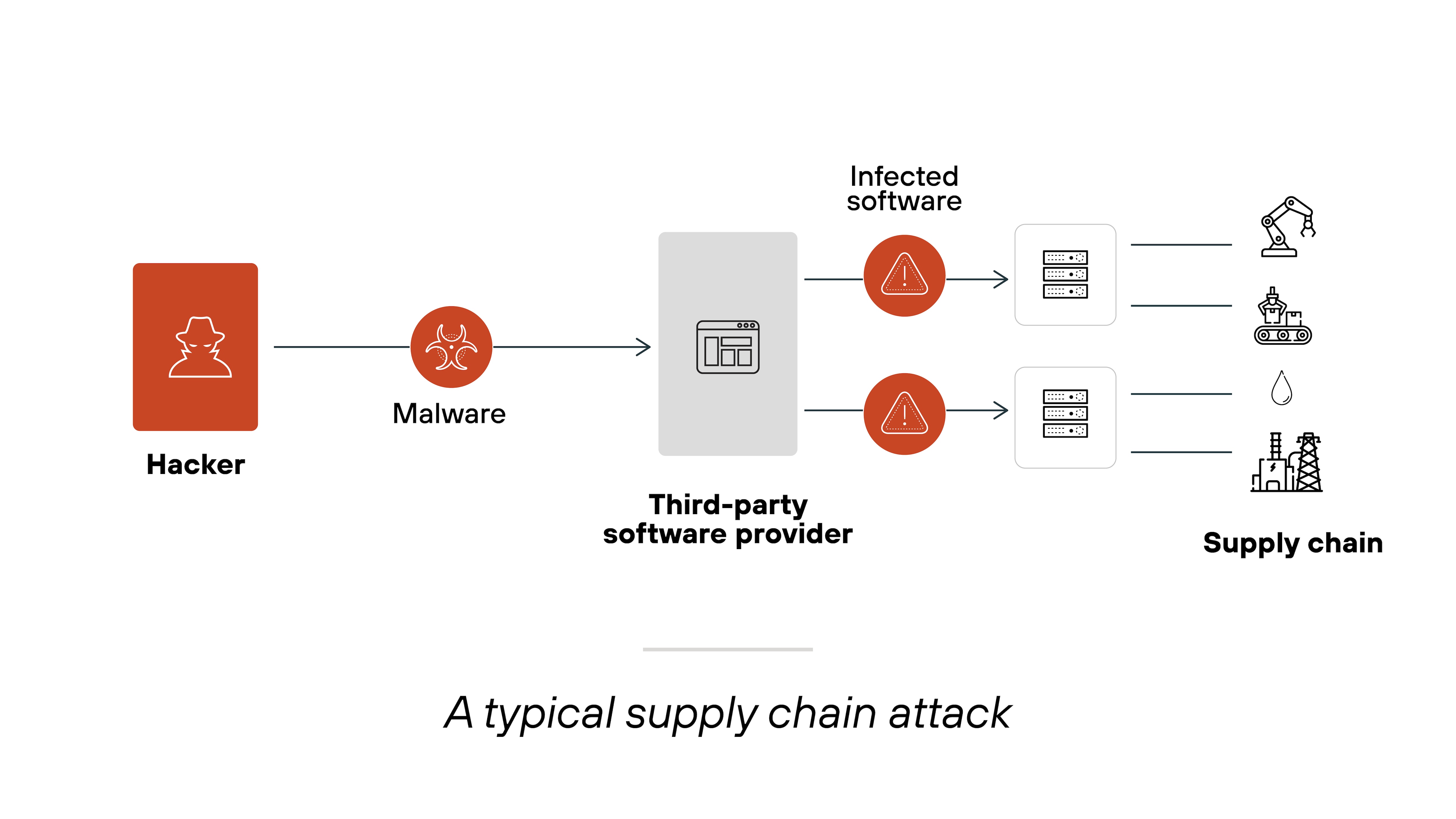
When a SaaS application integrates with external services, vulnerabilities in the provider’s security can lead to risks for the organization using the service. This can create an entry point for attackers to access the SaaS application’s sensitive data.
External attack surface expansion
Using SaaS applications automatically increases every organization's external attack surface beyond what’s directly controllable. Especially through APIs, subdomains, and integrations.
Unmonitored or misconfigured elements—like abandoned subdomains or unprotected APIs—can become targets for attackers to exploit.
API weaknesses
You need APIs for SaaS applications to communicate with other services, but they can become security vulnerabilities if they’re not properly secured.
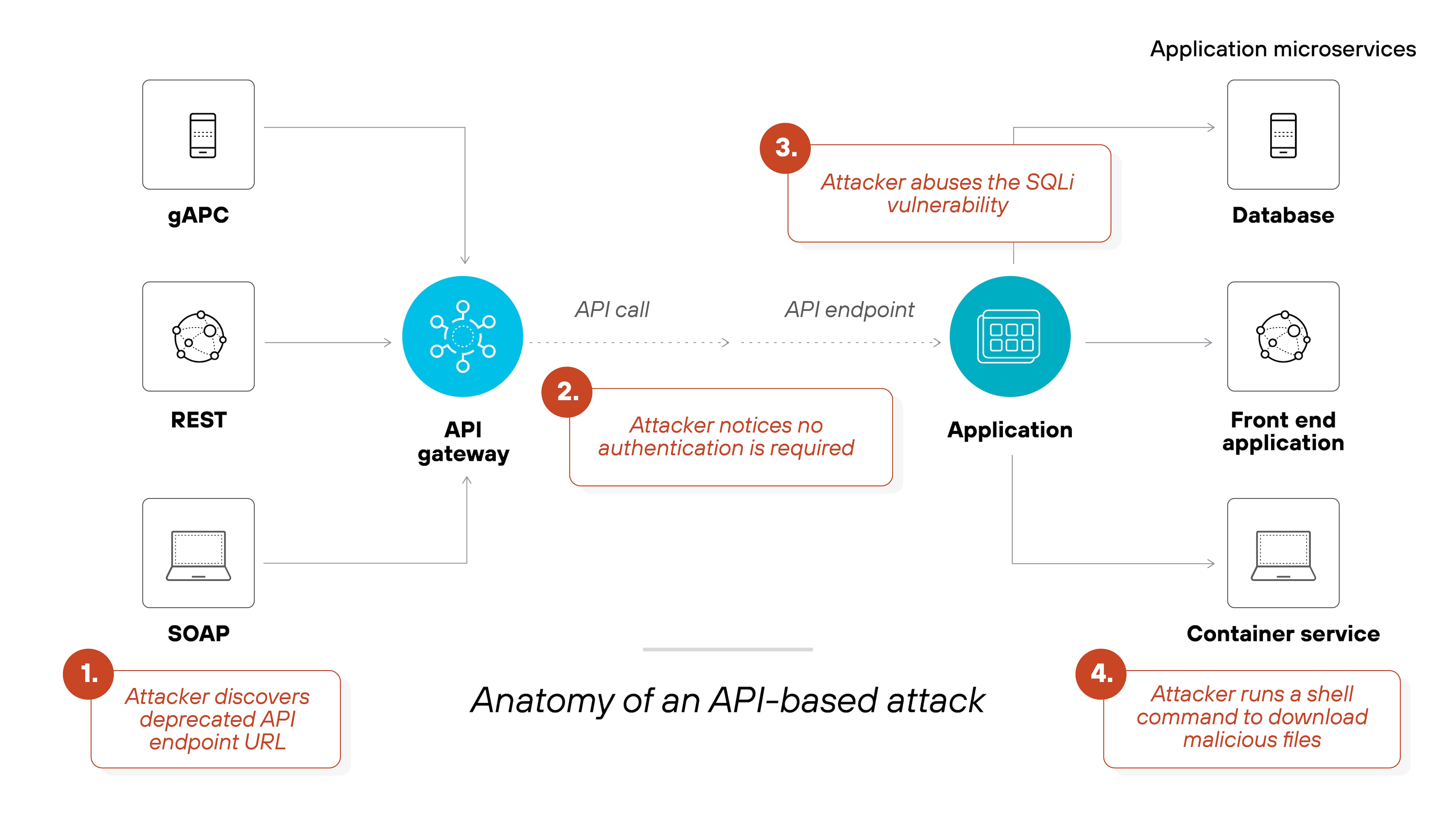
Weak API security can quickly lead to unauthorized data access, data loss, or manipulation. These vulnerabilities usually arise from bad authentication methods, insecure endpoints, or improper configurations in SaaS integrations.
How are cloud security and SaaS security related?
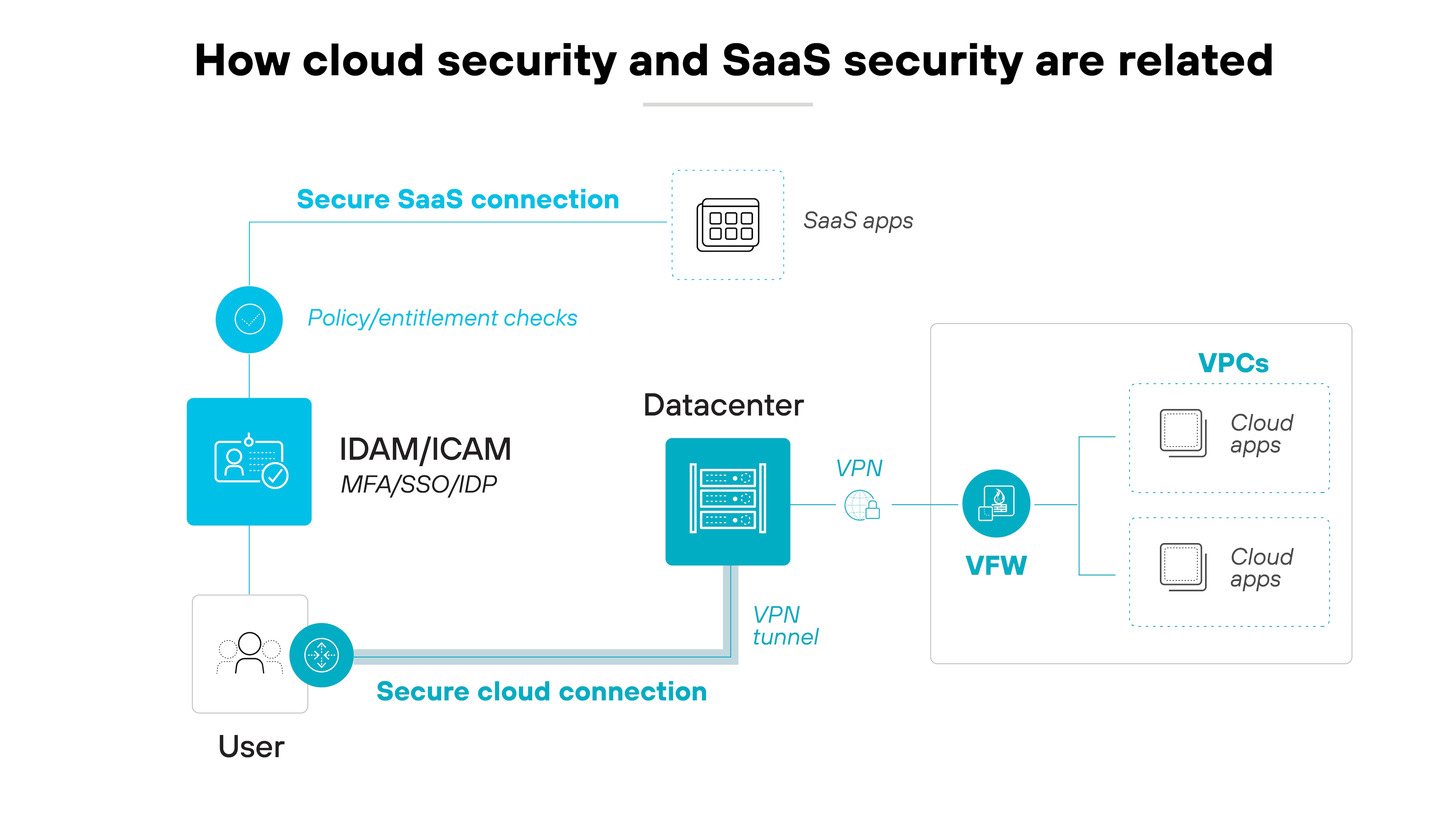
Cloud security and SaaS security are related in that cloud security protects the underlying infrastructure, while SaaS security focuses on securing the applications delivered through the cloud.
More specifically:
Cloud security secures the infrastructure, platforms, and data across all cloud services, like IaaS, PaaS, and SaaS. It protects physical servers, networks, and databases.
SaaS security, on the other hand, focuses on the applications delivered through the cloud. It ensures applications are safe, manages access controls, and secures data.
Cloud and SaaS security work together, with cloud security providing the foundation and SaaS security protecting the applications and data.
Top 16 SaaS security best practices
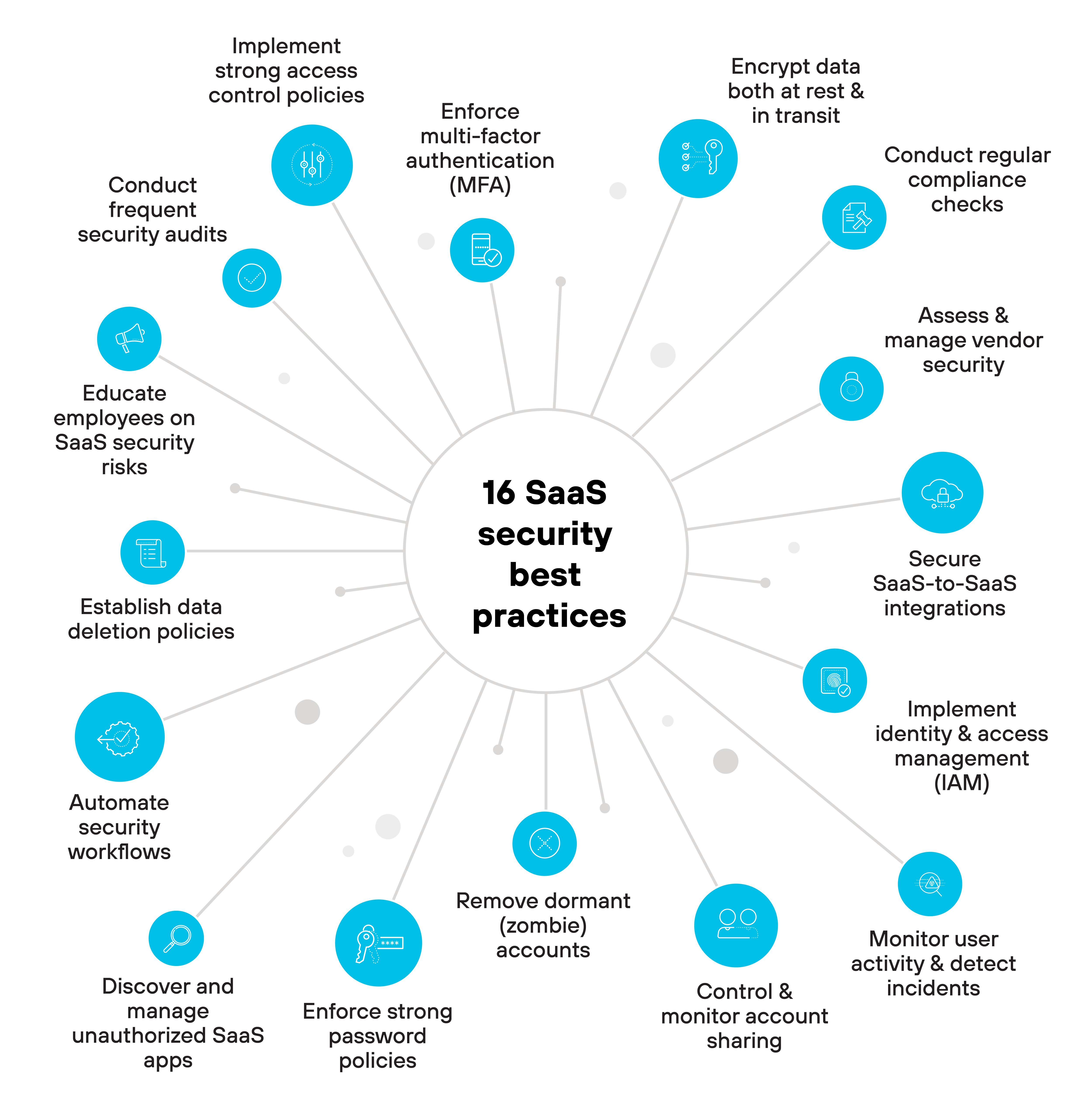
1. Conduct frequent security audits
Perform regular security audits to assess user permissions, access logs, and configurations. Regularly evaluate your SaaS apps to identify vulnerabilities and keep security up to date.
2. Implement strong access control policies
Adopt the principle of least privilege for access management. Grant users only the permissions they need to perform their duties and regularly review and update access controls to prevent unauthorized access.
3. Enforce multi-factor authentication (MFA)
Require multi-factor authentication (MFA) for all users accessing your SaaS apps. Implement MFA to add an additional layer of security. That way users are verified through multiple forms of identification.
4. Encrypt data both at rest and in transit
Make sure you’re encrypting all sensitive data during storage and transmission.
Use encryption protocols like SSL/TLS for data in transit and strong encryption methods for data at rest to safeguard it from unauthorized access.
5. Conduct regular compliance checks
Regularly review your SaaS apps to verify that they comply with regulations like GDPR, HIPAA, or SOC 2.
Conduct compliance checks to be certain that security measures align with industry standards and to avoid potential penalties.
6. Assess and manage vendor security
Evaluate third-party SaaS vendors before onboarding them.
Review their security practices, certifications, and compliance with security standards. Your security team should be assessing vendor security on a continuous basis.
7. Secure SaaS-to-SaaS integrations
Monitor and control integrations between your SaaS applications and third-party services. Enforce strict access controls and regularly audit these integrations to identify and address any security vulnerabilities.
8. Implement identity and access management (IAM)
Deploy a centralized identity and access management (IAM) system like IdP or SSO.
Use IAM to manage user authentication, enforce access policies, and maintain visibility over user activity within your SaaS applications.
9. Monitor user activity and detect incidents
Implement continuous monitoring of user activity across your SaaS applications. Set up alerts to detect unusual or unauthorized actions, such as failed login attempts, unauthorized configuration changes, or suspicious data access.
10. Control and monitor account sharing
Establish a policy to monitor and control account sharing within your SaaS applications. Confirm that shared accounts are properly secured, and that access is promptly revoked when an employee leaves or changes roles.
11. Remove dormant (zombie) accounts
Regularly identify and deactivate any dormant or unused accounts. Disable accounts that are no longer necessary to reduce the risk of exploitation by unauthorized users.
12. Enforce strong password policies
Mandate the use of strong passwords for all users accessing SaaS applications. Ensure passwords are complex, regularly updated, and not reused across multiple platforms. Encourage employees to use password managers to secure their credentials.
13. Discover and manage unauthorized SaaS apps
Implement tools to detect and monitor unauthorized SaaS applications (shadow IT) used within your organization. Regularly scan for non-approved applications and integrate them into your security framework.
14. Automate security workflows
Set up automated workflows for managing user access, detecting misconfigurations, and enforcing security policies. Automate routine security tasks to reduce human error and maintain consistent security practices across your SaaS environment.
15. Establish data deletion policies
Implement clear policies for securely deleting data from your SaaS applications once it’s no longer needed. Make sure the security is programmatically removing data from servers and logs once the retention period ends.
16. Educate employees on SaaS security risks
Provide regular training for employees on SaaS security best practices. Employees should be aware of the risks of phishing, the importance of strong passwords, and how to securely access and use SaaS applications.
What SaaS security tools are available?
Securing your SaaS applications requires the use of a variety of tools to address different aspects of security.
Below are some of the essential tools businesses rely on to ensure for SaaS security:
- Cloud access security brokers (CASBs)
- Identity and access management (IAM) solutions
- Data loss prevention (DLP) tools
- Security information and event management (SIEM) platforms
- Data encryption tools
- Vulnerability management tools
- Application programming interface (API) security tools
- Zero trust security tools
Cloud access security brokers (CASBs)
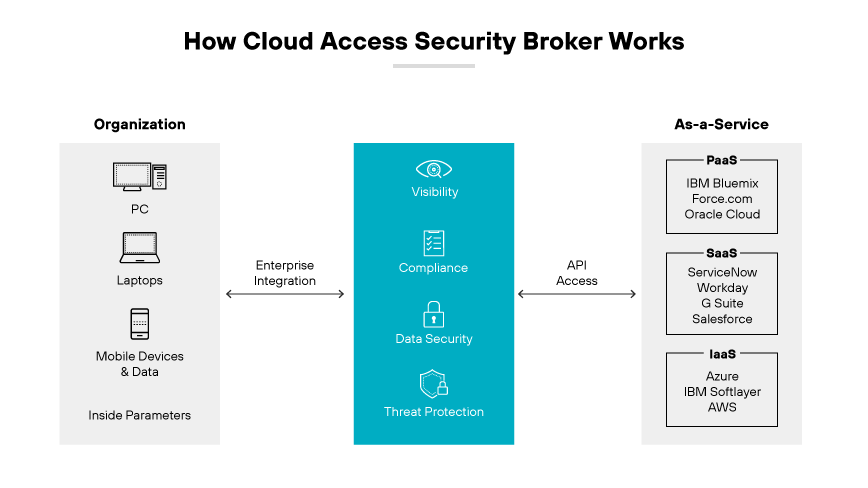
CASBs act as intermediaries between users and cloud services. They enforce security and compliance policies, providing visibility into cloud usage. CASBs can implement data loss prevention (DLP), detect threats, and ensure proper access control across cloud applications.
Identity and access management (IAM) solutions
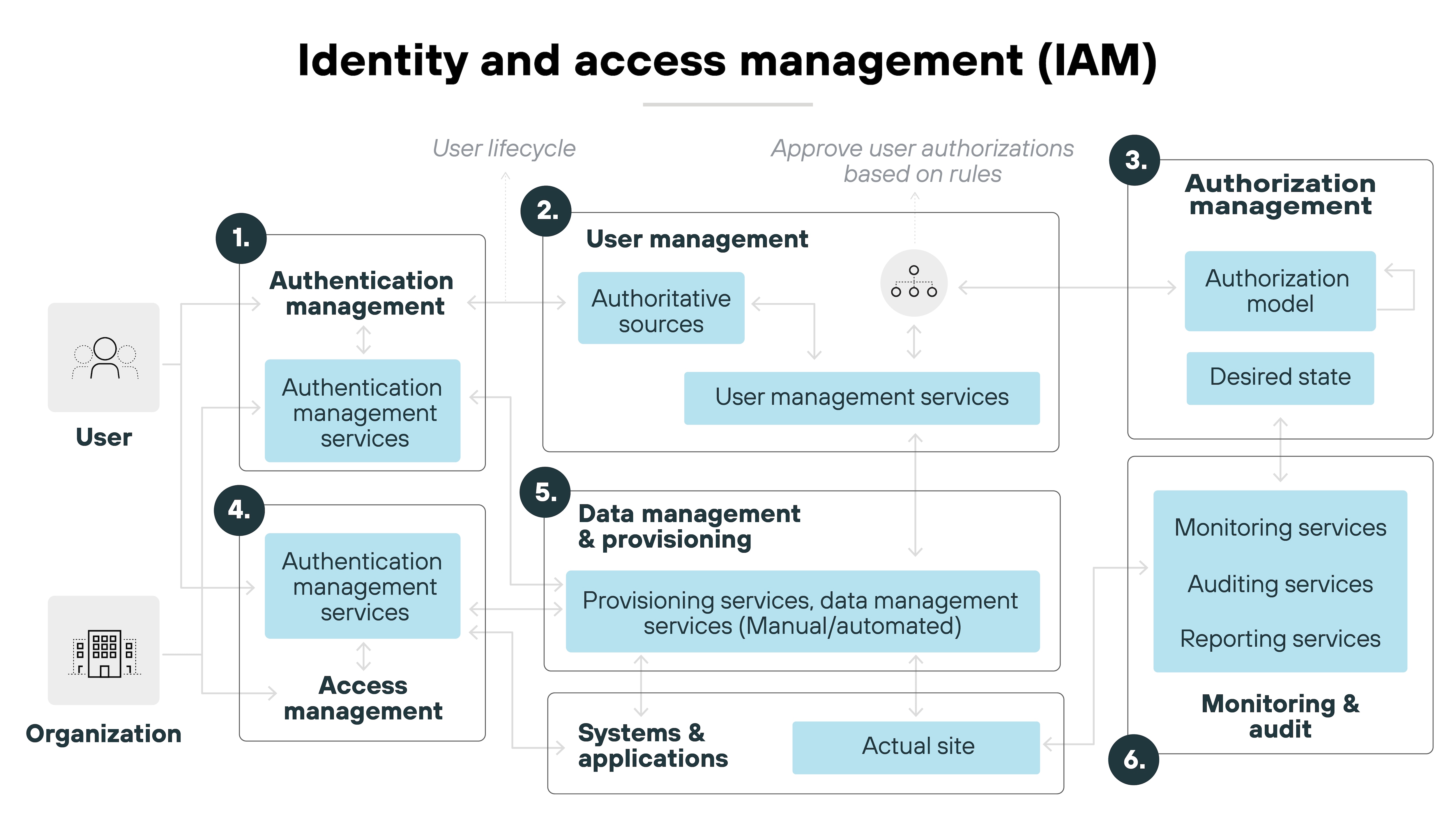
IAM solutions are critical for managing user identities, roles, and permissions within your SaaS environment. These tools help enforce least-privileged access, ensuring that only authorized users can access sensitive data. IAM systems also streamline user authentication through methods like single sign-on (SSO).
Data loss prevention (DLP) tools
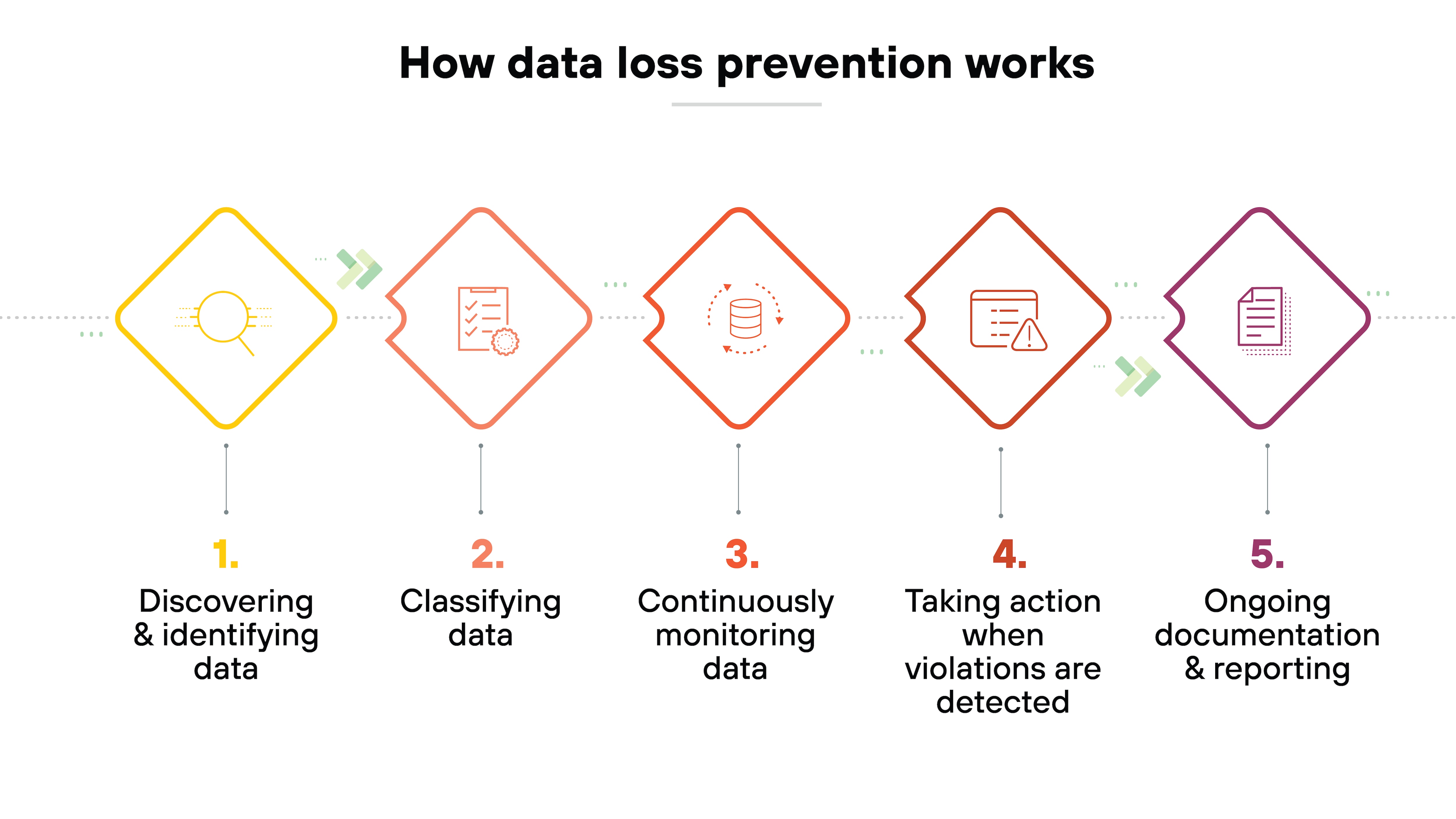
DLP tools protect sensitive information stored within SaaS applications. They monitor data usage and transfer, ensuring that data does not leave the organization improperly. These tools are essential for preventing data leaks and maintaining compliance with privacy regulations.
Security information and event management (SIEM) platforms
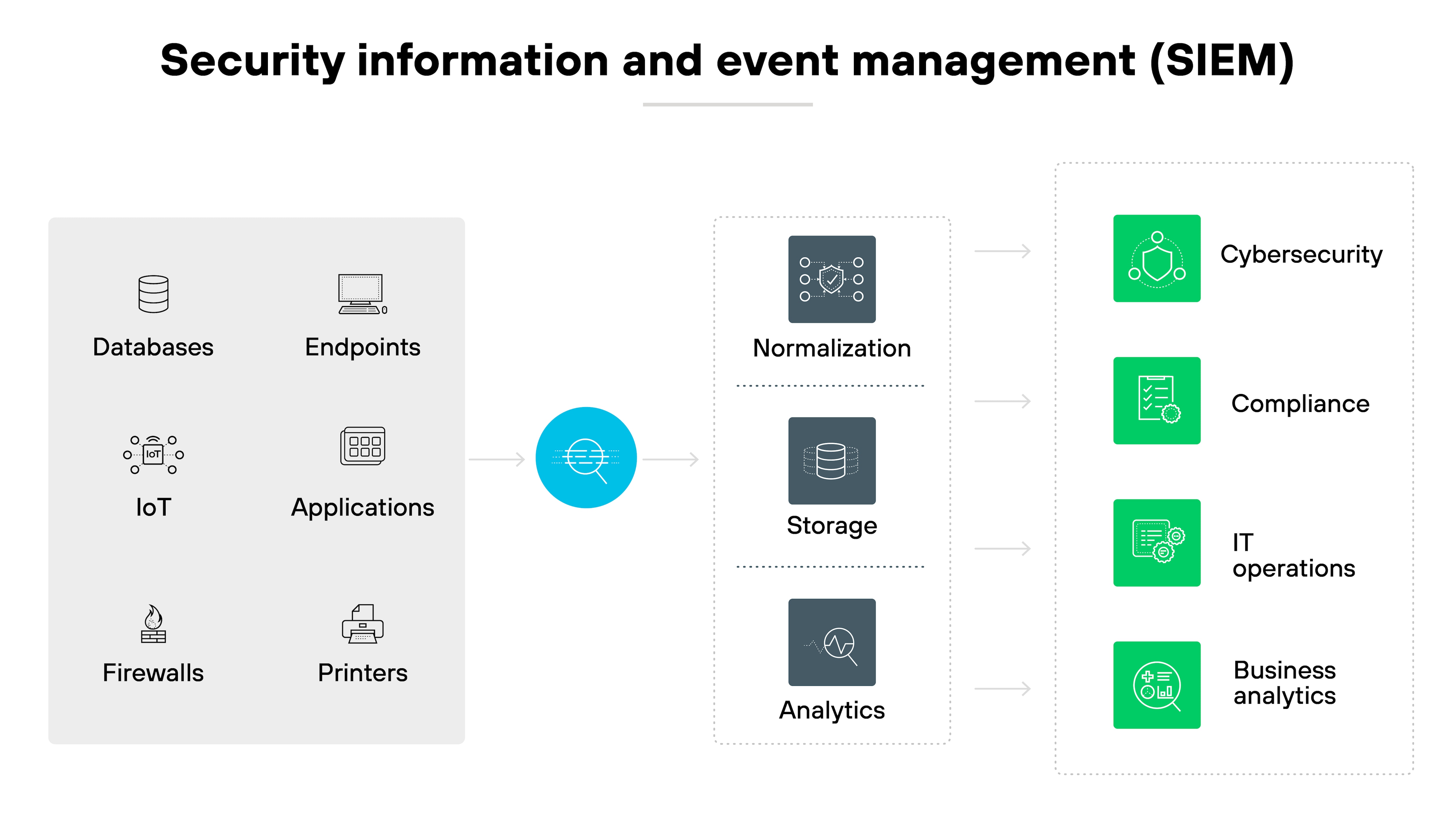
SIEM platforms collect and analyze data from various sources to detect security incidents. By monitoring activities and generating alerts, SIEM systems help identify potential threats before they escalate into breaches. They’re vital for organizations to manage logs, comply with regulations, and respond quickly to security events.
Data encryption tools
Encryption tools ensure that sensitive data remains secure both in transit and at rest. These tools convert data into unreadable formats that can only be decoded with the appropriate encryption keys. Encryption is a core defense mechanism for protecting SaaS data from unauthorized access.
Vulnerability management tools
Vulnerability management tools scan SaaS applications for weaknesses, misconfigurations, and security gaps. These tools help identify and fix vulnerabilities before attackers can exploit them, ensuring your applications stay secure and compliant with industry standards.
Application programming interface (API) security tools
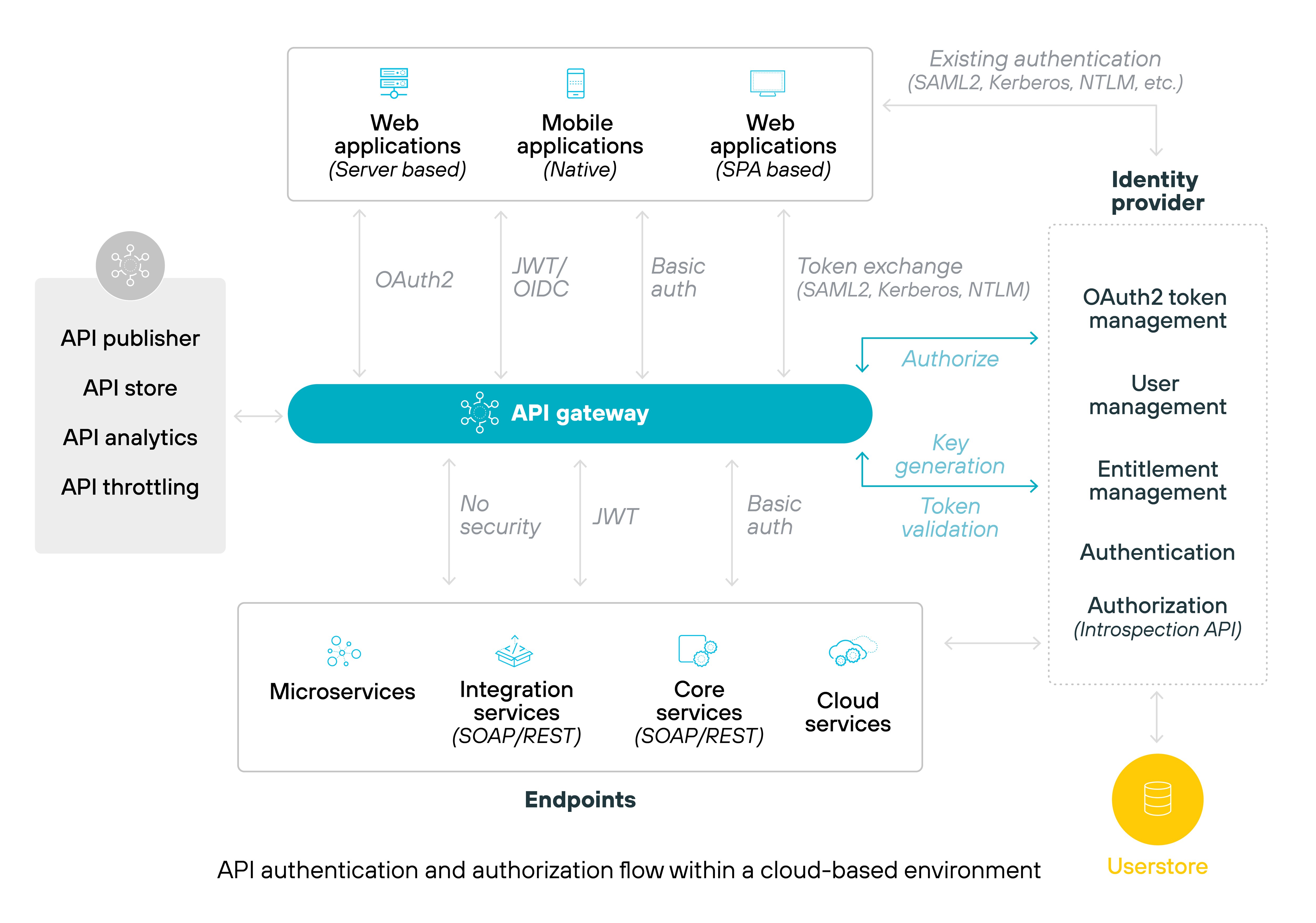
APIs are a common way for SaaS applications to exchange data with other systems. API security tools protect these integrations by monitoring and securing the data exchanged, preventing unauthorized access and ensuring secure connections between systems.
Zero trust security tools
Zero trust principles operate on the assumption that no one—inside or outside the organization—is trusted by default. Zero trust security tools enforce strict access control policies, using context-based authentication and continuous monitoring to ensure that only authorized users and devices can access the SaaS environment.
2025 SaaS security trends
In 2025, the landscape of SaaS security continues to evolve rapidly, driven by the increasing adoption of cloud-based services and the growing complexity of managing them.
One of the most prominent trends is the heightened focus on addressing the risks associated with SaaS sprawl. As more organizations turn to multiple SaaS applications for business operations, managing and securing this expanding ecosystem becomes increasingly difficult. The decentralized nature of SaaS applications, often spread across various business units, creates visibility gaps and complicates the enforcement of consistent security policies.
To tackle these challenges, many organizations are turning to SaaS security posture management (SSPM) tools, which provide centralized visibility and continuous monitoring of configurations, access controls, and potential misconfigurations across the SaaS environment.
Another key trend is the integration of generative AI (GenAI) tools into SaaS applications. While these tools offer significant benefits in terms of productivity and automation, they also introduce new security risks. GenAI tools often require extensive access to sensitive data within SaaS environments to function effectively, which increases the potential for data breaches and privacy violations. Plus: The rise of "shadow AI"—the unsanctioned use of AI tools within organizations—further exacerbates this issue, leaving security teams with limited oversight.
As a result, organizations are emphasizing stronger governance around the use of GenAI in SaaS, enforcing strict data access controls, and using automated solutions to monitor these integrations and mitigate risks.
A third trend is the growing importance of proactive security measures. Despite high levels of confidence in existing SaaS security programs, many organizations continue to experience security incidents due to gaps in their security practices.
This has led to a shift toward more automated and continuous monitoring strategies. Organizations are increasingly adopting tools that provide real-time risk assessment, compliance tracking, and identity management to ensure organizations can keep up with the pace of change and complexity in SaaS environments.
This trend reflects a broader push for a dedicated SaaS security program that integrates with other IT security frameworks to provide comprehensive protection against evolving threats.
As SaaS environments become more integral to business operations, organizations must adopt a holistic approach to SaaS security that encompasses robust monitoring, proactive risk management, and governance of third-party integrations.