- 1. Cyber Threat Intelligence Explained
- 2. Threat Intelligence: Why It Matters
- 3. The Benefits of Cyber Threat Intelligence
- 4. The Challenges of Cyber Threat Intelligence
- 5. Types of Cyber Threat Intelligence
- 6. What Data Is Considered Threat Intelligence?
- 7. Sources of Threat Intelligence
- 8. Tools and Services in Threat Intelligence
- 9. Practical Implementation of Threat Intelligence
- 10. The Threat Intelligence Lifecycle: An Overview
- 11. Building an Effective Threat Intelligence Program
- 12. Threat Intelligence FAQs
- Cyber Threat Intelligence Explained
- Threat Intelligence: Why It Matters
- The Benefits of Cyber Threat Intelligence
- The Challenges of Cyber Threat Intelligence
- Types of Cyber Threat Intelligence
- What Data Is Considered Threat Intelligence?
- Sources of Threat Intelligence
- Tools and Services in Threat Intelligence
- Practical Implementation of Threat Intelligence
- The Threat Intelligence Lifecycle: An Overview
- Building an Effective Threat Intelligence Program
- Threat Intelligence FAQs
What Is Cyber Threat Intelligence (CTI)?
- Cyber Threat Intelligence Explained
- Threat Intelligence: Why It Matters
- The Benefits of Cyber Threat Intelligence
- The Challenges of Cyber Threat Intelligence
- Types of Cyber Threat Intelligence
- What Data Is Considered Threat Intelligence?
- Sources of Threat Intelligence
- Tools and Services in Threat Intelligence
- Practical Implementation of Threat Intelligence
- The Threat Intelligence Lifecycle: An Overview
- Building an Effective Threat Intelligence Program
- Threat Intelligence FAQs
Cyber threat intelligence (CTI) is the process of collecting, analyzing, and applying data on cyber threats, adversaries, and attack methodologies to enhance an organization's security posture. It involves taking raw threat data from various sources and transforming it into actionable insights that enable organizations to anticipate, detect, and respond to cyber risks. Threat intelligence can be categorized into strategic intelligence, operational intelligence, and tactical intelligence, all of which offer strategic advantage against cybercriminals, nation-state actors, and insider threats. Properly informed and equipped, organizations can move beyond reactive defense and adopt a proactive security approach to mitigate risks before they materialize.
Cyber Threat Intelligence Explained
In a world where virtually every industry, organization, and individual increasingly relies on digital systems, identifying and mitigating the risk of cyberattacks is a crucial proactive security measure.
Cyber threat intelligence (CTI) represents the information an organization gathers and analyzes about potential and ongoing threats to cybersecurity and infrastructure.
Threat intelligence gives chief information security officers (CISOs) and security teams valuable insights about potential cyberthreat actors’ motivations and methods to help security teams anticipate threats, enhance cyber defense programs, improve incident response, decrease cyber vulnerability, and reduce potential damages caused by cyberattacks.
Threat Intelligence: Why It Matters
Cyber threat intelligence is an essential component of an organization's cyber resiliency, which includes “the ability to anticipate, withstand, recover from, and adapt” to threats, attacks, or compromises on systems, according to NIST.
Threat Intelligence fuels cybersecurity programs by providing powerful tactical information that organizations can use to better identify and respond to cyberattacks. The process of gathering this information also supports risk management by uncovering vulnerabilities in cybersecurity systems. Security teams are then able to allocate resources better to meet the most relevant cyber threats to their industry and protect valuable data, assets, and intellectual property.
The Benefits of Cyber Threat Intelligence
Threat intelligence is pivotal in enhancing an organization’s cybersecurity posture, providing numerous benefits spanning proactive defense to informed decision-making. One of the most critical advantages is the enhancement of incident response capabilities. With relevant threat intelligence, incident response teams can detect, investigate, and mitigate security incidents more rapidly and effectively. Being informed about adversaries’ TTPs ensures that response teams can tailor their strategies to the specific threats they face, leading to more efficient containment and recovery.
Experienced threat intelligence analyst can enhance cybersecurity and resiliency on several levels, including:
- Establishing proactive cyber defense: Contrary to traditional reactive cyber defense (responding to known threats), CTI empowers organizations to understand potential threat actors and anticipate potential attacks.
- Improving risk management plan: CTI provides actionable information about the motivations, means, and methods potential threat actors use. CISOs and SOCs can utilize these insights when evaluating risk profiles and allocating cybersecurity resources to maximize threat detection and protection.
- Improving incident response: In addition to supporting attack prevention, CTI provides insights that make an organization better prepared to respond to and recover from a cyberattack. A thorough understanding of the circumstances of a breach can dramatically reduce the impact of a breach.
- Increasing employee awareness: Organizations can utilize CTI to educate employees about cyber threats and establish security-focused operating procedures and training.
The Challenges of Cyber Threat Intelligence
Given the dynamic and complex nature of the cyber threat landscape, obtaining high-quality threat intelligence comes with several challenges, including:
- Information overload: In addition to collecting, processing, and analyzing immense volumes of data, CTI teams must differentiate between “normal” and “malicious” activity. Threats must also be evaluated to determine which information is most relevant to the organization’s industry, size, and risk profile, among other factors.
- Information updates: The effectiveness of a threat intelligence program relies on the timeliness of the information being analyzed. Decisions made based on outdated CTI can impede an organization’s threat detection and increase vulnerability to cyberattacks.
- Data Relevance: Not all threat intelligence is relevant to every organization. Determining which pieces of intelligence apply to a specific organization’s context and infrastructure can be challenging.
- Accuracy and False Positives: Low-quality or inaccurate threat intelligence can lead to false positives, causing security teams to waste resources on non-existent threats or overlook actual threats.
- Compliance: CTI often involves personally identifiable information (PII). Organizations must ensure that all cyber threat intelligence systems are in compliance with any applicable data protection regulations.
Types of Cyber Threat Intelligence
Threat intelligence, essential for proactive cybersecurity, covers a broad range of information and analysis and can be categorized into several standard types of threat intelligence based on content and use cases. It can, however, be separated into three general categories, according to information type and application. Among the most prevalent are strategic, tactical, operational, and technical threat intelligence. A well-rounded CTI program will contain varying levels of each type to meet the organization's unique cybersecurity needs.
Strategic Intelligence
Strategic threat intelligence (STI) comes from high-level analysis of broad cybersecurity trends and how they might affect an organization. It offers insights about threat actors' motives, capabilities, and targets, and helps executives and decision-makers outside of IT understand potential cyber threats. Typically less technical and incident-specific than other types of CTI, strategic threat intelligence is often used to formulate risk management strategies and programs to mitigate the impact of future cyberattacks.
Tactical Intelligence
As the name implies, tactical threat intelligence (TTI) focuses on threat actors’ tactics, techniques, and procedures (TTPs) and seeks to understand how a threat actor might attack an organization. Tactical threat intelligence also explores threat vulnerabilities using threat hunting, which proactively searches for initially undetected threats within an organization’s network. TTI is more technical than STI and is typically used by IT or SOC teams to enhance cybersecurity measures or improve incident response plans.
Operational Intelligence
More detailed, incident-specific, and immediate than STI and TTI, operational threat intelligence (OTI) is real-time data used to facilitate timely threat detection and incident response. CISOs, CIOs, and SOC members often utilize OTI to identify and thwart likely attacks.
What Data Is Considered Threat Intelligence?
Threat intelligence encompasses a wide range of information to provide organizations with insights into past, current, and potential future cyber threats. The data considered a part of threat intelligence includes:
Indicators of Compromise (IoCs): Observable data points that indicate a potential breach or malicious activity. Examples include:
- IP addresses associated with malicious activity.
- URLs or domain names of phishing sites.
- Malware hashes or file signatures.
- Email addresses or subjects linked to phishing campaigns.
Tactics, Techniques, and Procedures (TTPs): Descriptive details on threat actors’ operations, which can include:
- Specific methods used to gain initial access.
- Techniques for maintaining persistence.
- Ways they escalate privileges or move laterally within a network.
Security teams map TTPs to frameworks like MITRE ATT&CK to build threat models, improve detections, and enhance automated defenses. Tracking TTPs enables organizations to anticipate evolving adversary behavior and strengthen cloud security strategies.
Threat Actor Profiles: Information on groups or individuals responsible for cyberattacks, including:
- Their motivations (financial gain, espionage, activism, etc.).
- Capabilities and skill levels.
- Past campaigns or incidents attributed to them.
Vulnerability Information: Details about known weaknesses in software or hardware that can be exploited, such as:
- Vulnerability identifiers (e.g., CVE numbers).
- Affected systems or software.
- Potential impact and mitigation strategies.
Social Media and Dark Web Data: Information from online forums, social media platforms, or the dark web where threat actors might communicate, share tools, or sell stolen data.
Sources of Threat Intelligence
Sources for threat intelligence are almost as varied as the cybersecurity landscape itself. The more common sources for CTI include:
- Internal data: information an organization gathers from its own data, network logs, incident responses, etc.
- Open-source intelligence (OSINT): information from resources considered public domain.
- Closed-source services: information not available to the general public.
- Information sharing and analysis centers (ISACs): business sector-specific organizations that collect, analyze, and share actionable threat information with member organizations.
- Government advisories: information released by agencies like the FBI (USA), the National Cyber Security Centre (UK), or the European Union Agency for Cybersecurity (ENISA).
- Deep and dark web intelligence: encrypted and anonymous information that provides information regarding cybercrime and activity, early warnings of impending attacks, and insights about cybercriminals’ motives and methods.
Leveraging External and Internal Threat Intelligence
CTI from internal and external sources offers different, yet equally important, insights regarding an organization’s threat landscape.
Analysis of internal data creates “contextual CTI” that helps an organization identify and confirm the most relevant threats based on individual circumstances, business systems, products and services. Reviewing information from past incidents can reveal indicators of compromise (IOCs), detail the cause and effect of a breach, and provide opportunities to improve incident response plans. Internal CTI also creates a greater understanding of an organization’s vulnerabilities, allowing CISOs and SOCs to develop more tailored and targeted cybersecurity measures.
External CTI provides the insights needed to stay ahead of current and upcoming threat actors. From global TTPs to sector-specific intelligence from sources like ISACs and industry peer groups, external CTI increases threat awareness and improves an organization’s ability to create a more powerful cybersecurity program.
The Value of Intelligence-Driven Data in Threat Detection
A crucial element in any cyber threat detection and response program, intelligence-driven data fuels a proactive defense posture that helps organizations better understand their vulnerabilities, anticipate cyber threats, focus resources on the most significant threats, and develop an incident response plan that will minimize the impact of cyber attacks.
Intelligence-driven data can also provide a deeper understanding of risk management and compliance issues reducing potential financial and reputational damage resulting from a data breach.
Tools and Services in Threat Intelligence
You'll find a growing range of tools for generating cyber threat intelligence, each with unique forms and functions to fit an organization’s cybersecurity needs.
Combining the functions of several tools and threat intelligence platforms creates the most complete and thorough threat detection and prevention program.
An Overview of Threat Intelligence Tools and Their Functions
- Threat Intelligence Platforms (TIPs): automatically collect, aggregate, and analyze external threat data.
- Security Information and Event Management (SIEM) Systems: collect and analyze internal threat data composed of system logs, event data, and other contextual sources.
- Threat Intelligence Feeds: provide real-time streams of information related to current or ongoing cyber threats, often focused on a particular area of interest (IP addresses, domains, malware signatures, etc.).
- Sandboxing Tools: provide controlled environments in which organizations can analyze or open potentially dangerous files or programs without risk to the organization’s internal systems.
- Open-Source Intelligence (OSINT) Tools: gather data from public sources (social media, blogs, open discussion forums, etc.).
- Intrusion detection systems (IDS): monitor network traffic, identify threats, and provide intelligence for threat response.
- Intrusion prevention systems (IPS): analyze threats, block attacks in real time, and enhance threat intelligence.
- Cloud Detection and Response (CDR): analyzes threats in the cloud environment, providing real-time intelligence and automated mitigation.
Threat Intelligence Services: How They Enhance Cybersecurity
Threat intelligence services support organizations’ cybersecurity efforts by providing CISOs and SOCs the tools to develop and optimize cyber threat analysis, prevention, and recovery programs. Effective CTI support increases overall threat awareness, enables proactive defense measures, enhances incident response plans, and improves decision-making and risk management.
The Role of Incident Response in a Threat Intelligence Program
An incident response plan (IRP) serves several purposes in a threat intelligence program. An IRP outlines how an organization will react to and recover from a cyber security incident. In addition to ensuring an organization’s preparedness for a cyber attack, a well-planned IRP will provide various types of threat intelligence that can be used to improve future cybersecurity measures.
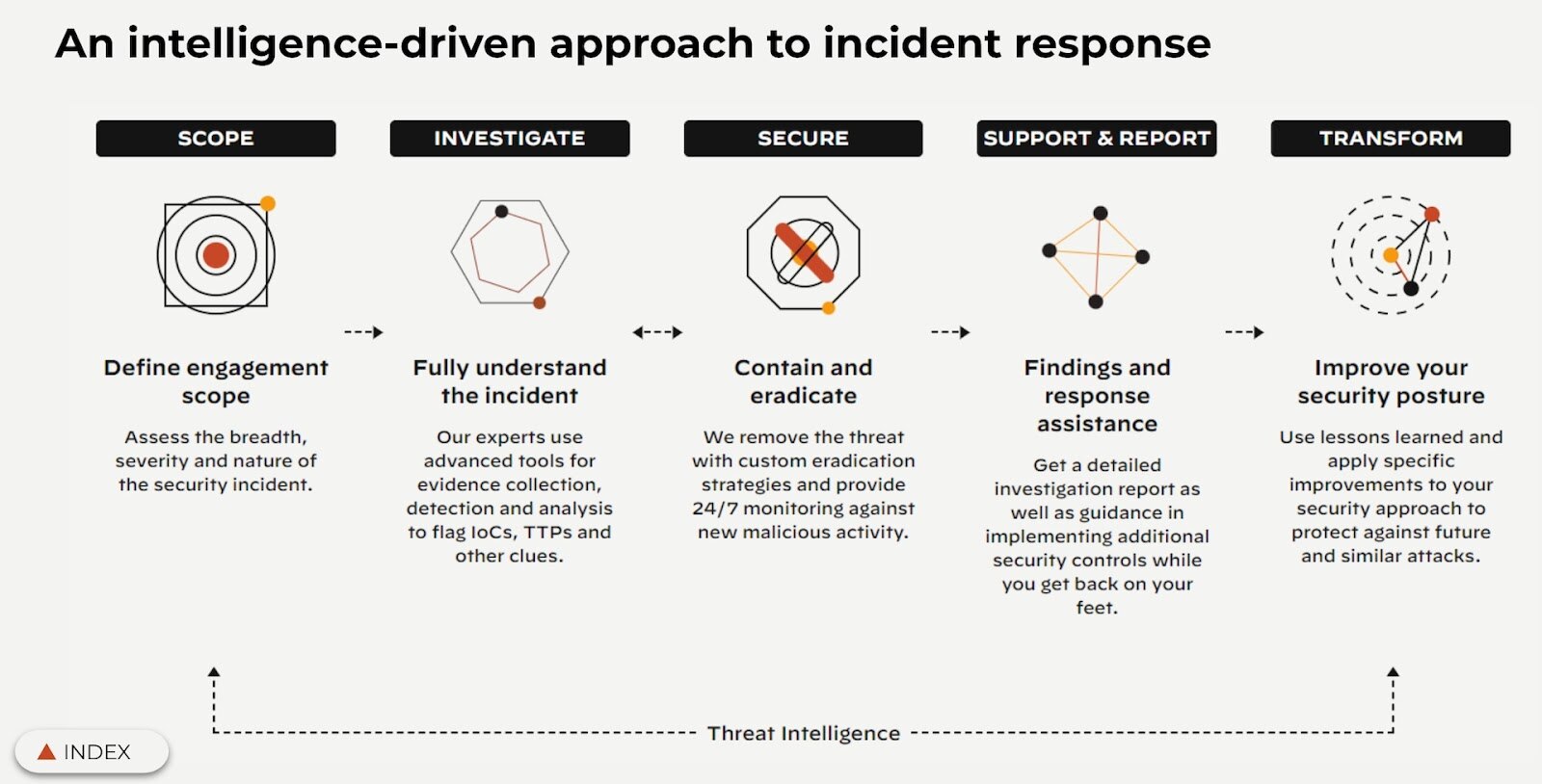
Figure 1: A graphic detailing the Unit 42® Incident Response Methodology
Practical Implementation of Threat Intelligence
The practical implementation of cyber threat intelligence begins with defining clear objectives and gathering relevant data from a variety of internal and external sources. Once analyzed, the data can be used to generate actionable intelligence designed to integrate into the existing cybersecurity program.
Integrating Threat Intelligence into Your Cybersecurity Strategy
Applying the insights from your CTI program to your overall cybersecurity strategy will enhance threat awareness, attack prevention, and incident response. It is important to note that this integration may require adapting existing processes, adjusting control measures, updating plans, or modifying user training programs.
Threat Hunting: A Proactive Approach to Cybersecurity
Sophisticated hackers can infiltrate a network and remain undetected while searching for or collecting data, login credentials, or other sensitive materials. Threat hunting is the practice of proactively searching for previously undetected cyber threats on an internal network. Threat hunting is crucial for eliminating advanced persistent threats (APTs).
The Threat Intelligence Lifecycle: An Overview
The threat intelligence lifecycle is an outline of the process by which CISOs develop and implement cyber threat intelligence programs. It is a framework for continuously transforming raw threat data into actionable threat intelligence that can then be utilized to identify and avoid threats to an organization’s cybersecurity.
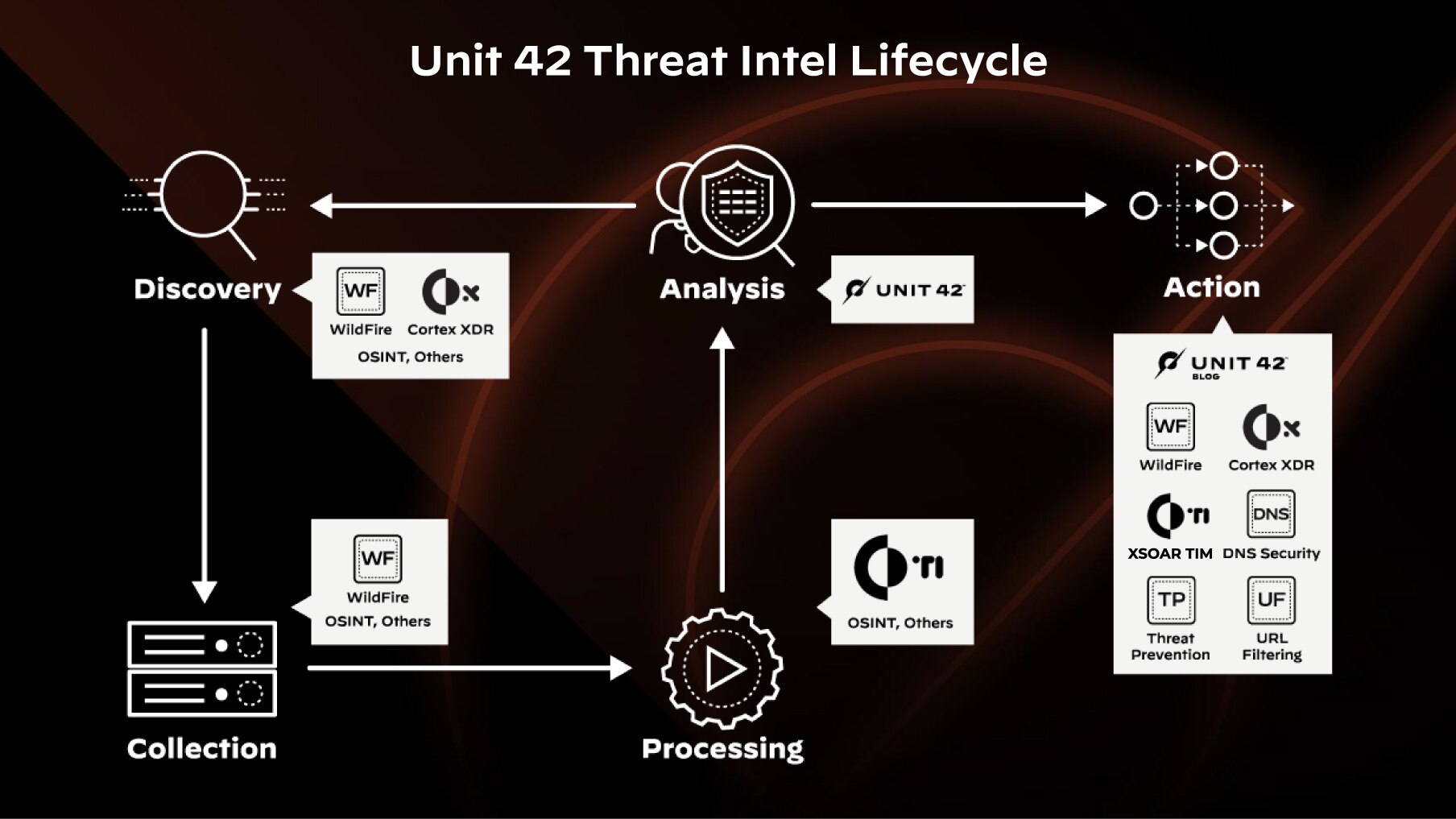
Figure 2. Unit 42 Threat Intel Lifecycle
Understanding the Stages of the Threat Intelligence Lifecycle
- Discovery: discover threat intelligence data (indicators, adversary tactics, tools, etc.) from various sources, which can include internal investigations and sources, threat intel feeds, partnerships, other open-source threat intelligence (OSINT).
- Collection: Once threat intelligence data is discovered, collect and store that data for additional processing and analysis.
- Processing: clean up data to remove duplicates, inconsistencies, and irrelevant information. Then transform raw data into a format suitable for analysis, and enhance with additional context and metadata.
- Analysis: conduct in-depth analysis of the processed data to identify patterns, trends, and potential threats, and employ various techniques to uncover hidden insights. Then evaluate the credibility and impact of identified threats.
- Action: prepare and distribute actionable intelligence to relevant stakeholders, including incident response teams, the SOCs, DevSecOps teams, and executives. Ensure to tailor the information to the specific needs of different audiences so it’s concise and clear.
- Feedback Loop: capture feedback from key stakeholders on the effectiveness and relevance of the provided threat intelligence. Then continuously refine and improve the collection, processing, analysis and processes based on feedback and lessons learned.
This lifecycle ensures organizations maintain proactive defense postures by continuously adapting intelligence to on-premises and cloud-native attack vectors and adversary behaviors.
Building an Effective Threat Intelligence Program
More than finding the right tools and searching for data, building an effective CTI program requires a strategy-driven plan, a team of specialists, well-organized processes, and an organization-wide commitment to continuous learning and improvement.
Key Steps in Setting Up a Threat Intelligence Program
- Defining goals and objectives.
- Allocating resources and appropriately skilled staff.
- Implementing processes for relevant data collection.
- Developing methodologies for data analysis and intelligence generation.
- Integrating and utilizing intelligence in cybersecurity programs.
- Defining formats for disseminating intelligence.
- Gathering and reviewing feedback.
- Ensuring compliance and adherence to industry standards, regulations, and internal governance policies.
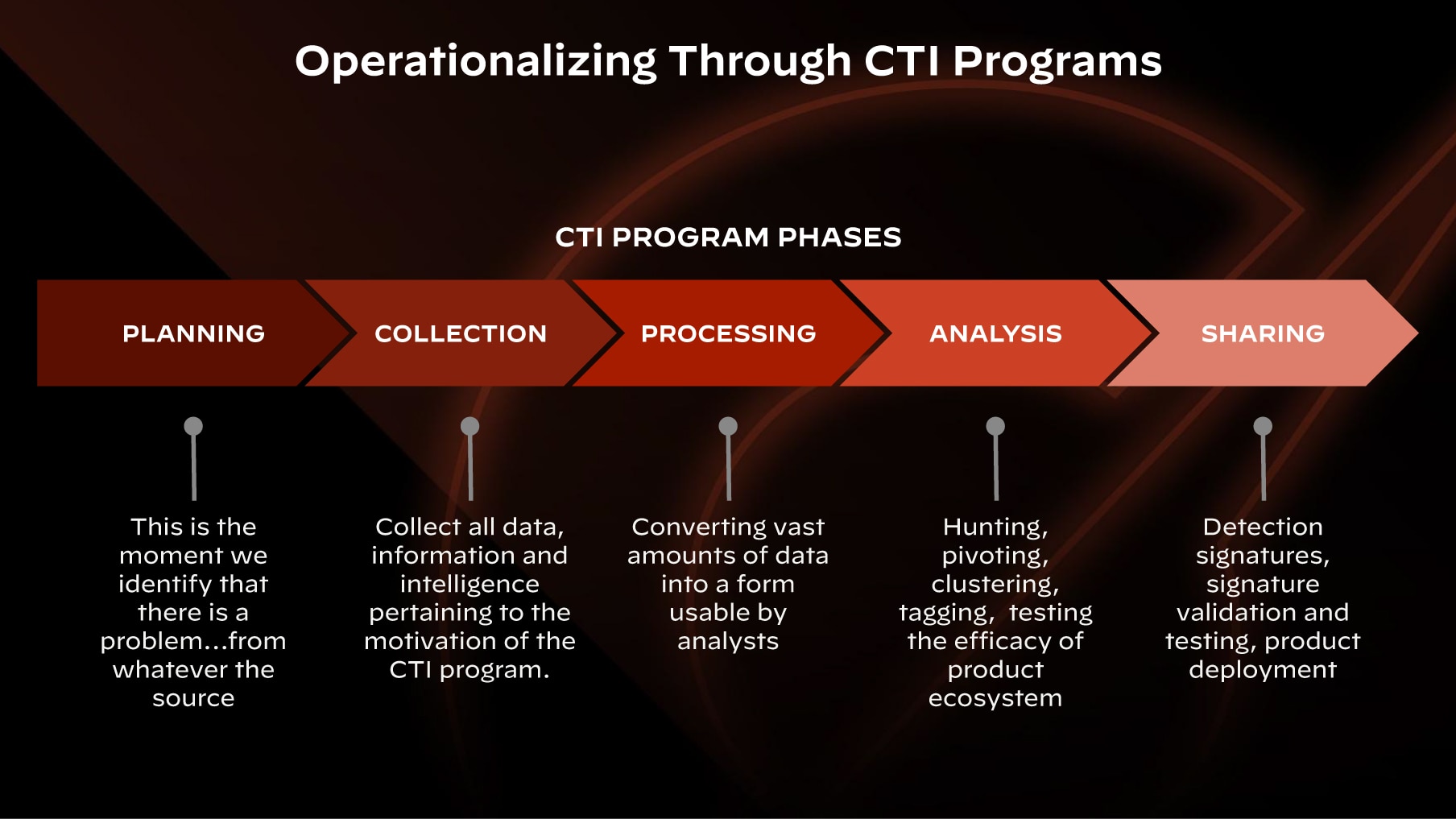
Figure 3. Unit 42 CTI Program Phases
The Importance of Continuous Learning and Adaptation in Threat Intelligence
The cyber threat landscape continuously changes as threat actors become more knowledgeable and sophisticated. An effective CTI program can only remain effective if it is as dynamic as the threats it is designed to thwart. Learning from previous incidents and threat intelligence feedback allows organizations to continuously adapt and enhance the elements of a CTI program, keeping it as relevant and effective as possible.
Threat Intelligence FAQs
Cyberthreat intelligence trends will vary by industry, geography, and threat types. There are, however, several general trends that affect businesses and organizations of all kinds.
- Cyberattacks are increasing and becoming more expensive.
- Cybercriminals are working together and becoming specialized.
- Botnets and automated malware deployment tools are becoming more sophisticated.
- Collaboration between state-sponsored actors and cybercriminals is on the rise.
- Organizations of all sizes are in danger, especially small-to-medium businesses (SMBs).
The emergence of the internet created an unprecedented level of information sharing and connection. As the digital landscape expanded, so did the need to protect individuals and organizations from the growing threat of cyberattacks.
Rapidly growing threats gave rise to early cyber protection protocols like IP and URL blacklists and cyberthreat blocking systems like antivirus programs and firewalls.
Cybercrime increased into the 2000s with notable cyberattacks like the “ILOVEYOU” worm that caused upwards of $15 billion in damages. Spam, botnets, and trojans became more prevalent, and the need for more powerful and proactive cybersecurity measures became more clear. It was the advent of advanced persistent threats (APTs), however, that ignited the cyberthreat intelligence movement. Businesses and governments alike created cyberthreat intelligence teams, while cybersecurity firms began helping organizations better anticipate and prevent cyberthreats.
Since 2010, cyberattackers have become more sophisticated and damaging. Complex hacks, malware, and ransomware attacks led to a shift in CTI that focused on threat actors’ tactics, techniques, and procedures, now referred to as TTPs. These comprehensive analyses give organizations the insights and understanding needed to anticipate threats rather than simply reacting to them.
Modern cyberthreat intelligence is integral to any cybersecurity program, affecting resource allocation, threat analysis policies, and incident response plans.
Operational threat intelligence provides real-time, actionable insights into active cyber threats targeting an organization. It includes details on adversary TTPs, attack campaigns, and emerging vulnerabilities. Operational CTI enables SOCs, incident response teams, and DevSecOps engineers to anticipate and mitigate threats by implementing targeted detections, blocking malicious infrastructure, and enhancing automated defenses.
Unlike strategic intelligence, operational CTI focuses on immediate, short-term risks, often delivered through TIPs, security telemetry, and adversary tracking feeds.
The cyber kill chain is a model developed by Lockheed Martin that maps an attack's lifecycle in seven stages:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control
- Actions on Objectives
The cyber kill chain helps security teams detect and disrupt adversary campaigns early. While useful, the kill chain has limitations against modern threats like cloud-native attacks and APTs, which require frameworks like MITRE ATT&CK for more granular threat analysis.
Intrusion detection involves monitoring networks and systems for malicious activity using signature-based (known attack patterns) and behavioral-based (anomaly detection) techniques.
Intrusion detection systems (IDS) analyze logs, traffic, and system behavior to identify unauthorized access, malware infections, and policy violations. In cloud environments, intrusion detection extends to workload security, API monitoring, and identity-based anomaly detection. Advanced detection integrates AI and threat intelligence to detect evasive threats in real time.
APT groups are organized threat actors—often state-sponsored, criminal syndicates, or hacktivists—that conduct prolonged, sophisticated cyber operations. Groups like APT29 (Russia), APT41 (China), and Lazarus Group (North Korea) employ advanced malware, supply chain attacks, and cloud exploitation techniques. These groups use persistent footholds, leveraging stolen credentials and living-off-the-land (LOTL) techniques to evade detection.
Security teams track APTs using TTPs mapped to MITRE ATT&CK to strengthen defenses against cloud-based espionage, intellectual property theft, and geopolitical cyber threats.