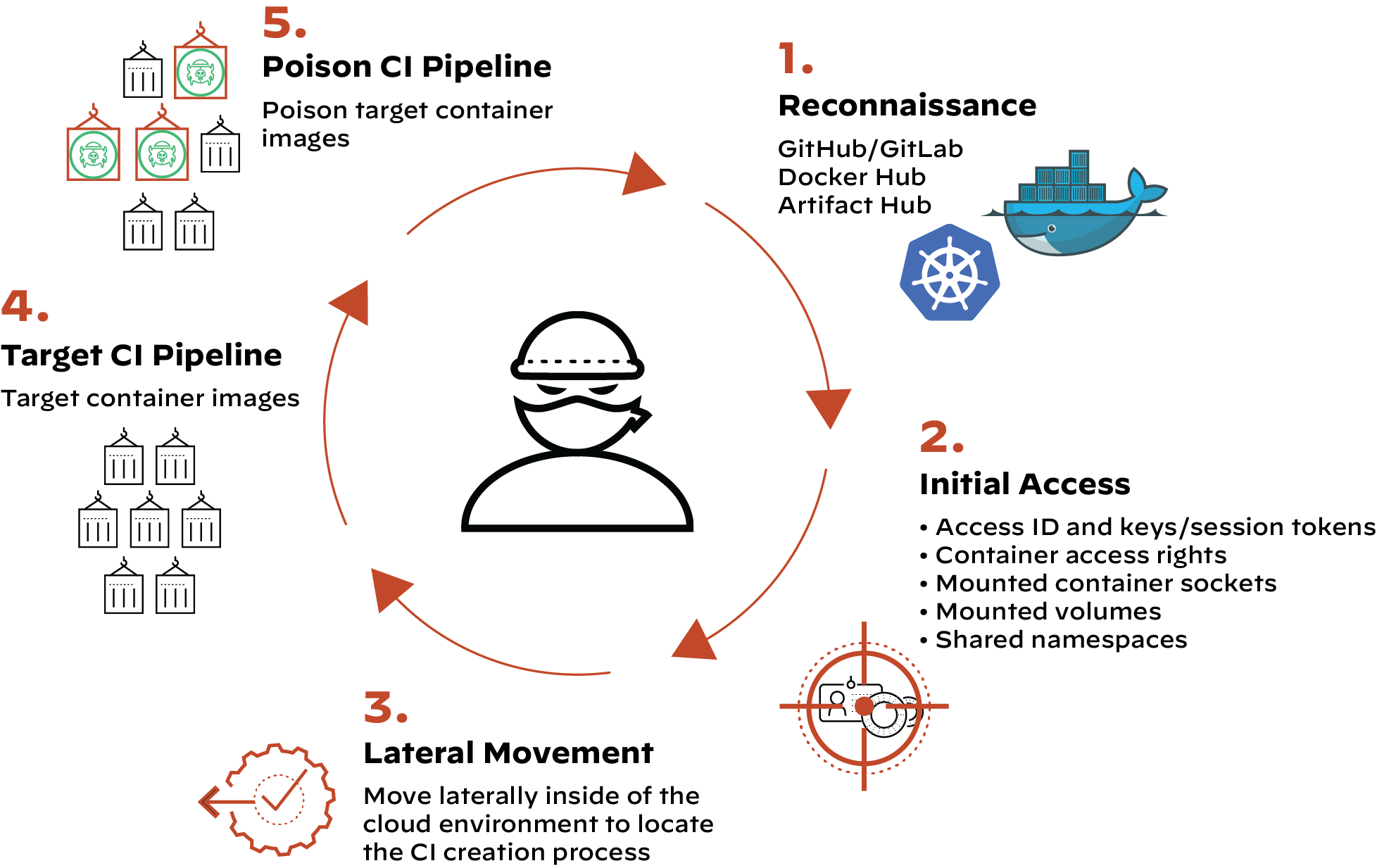
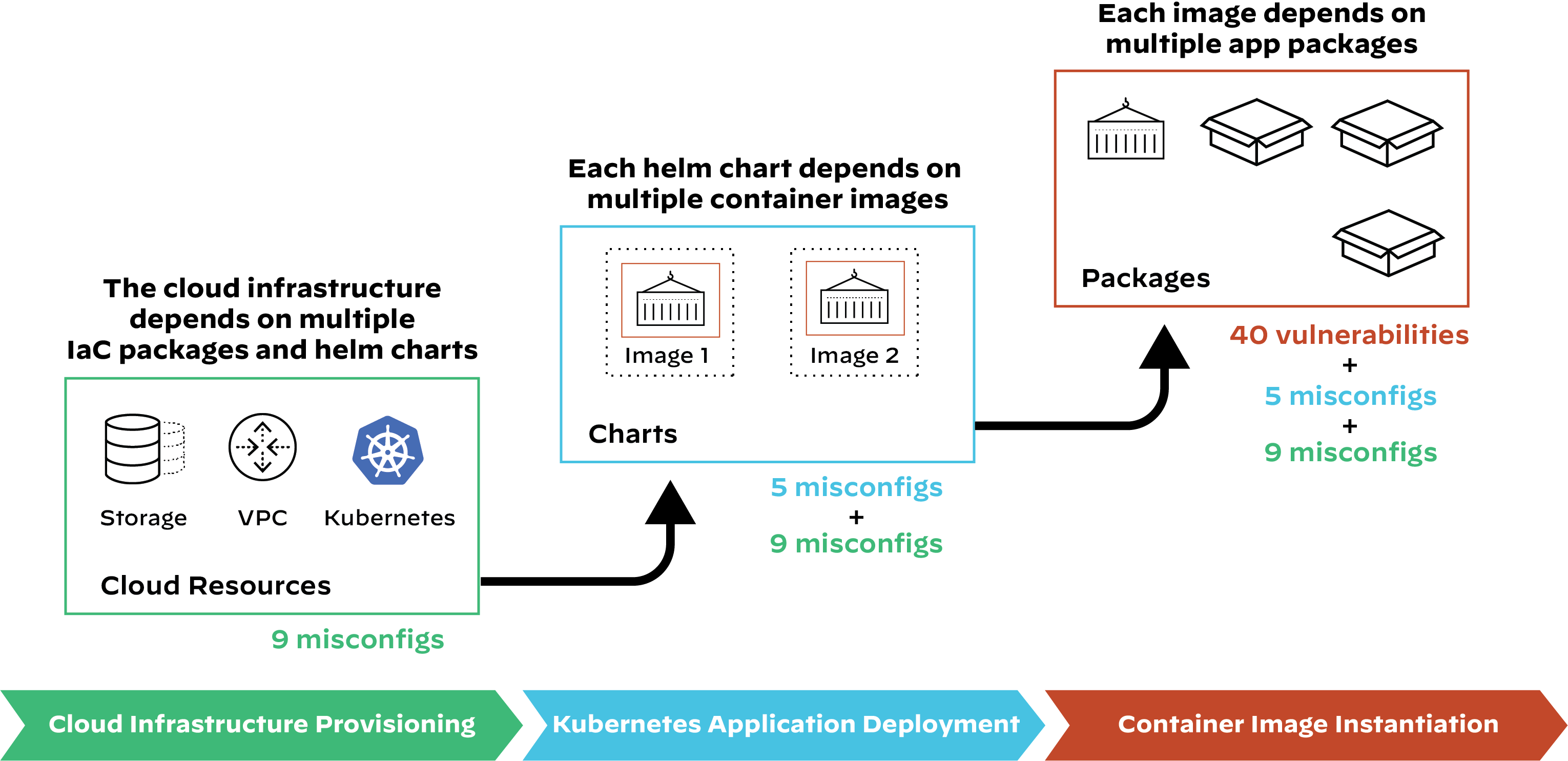
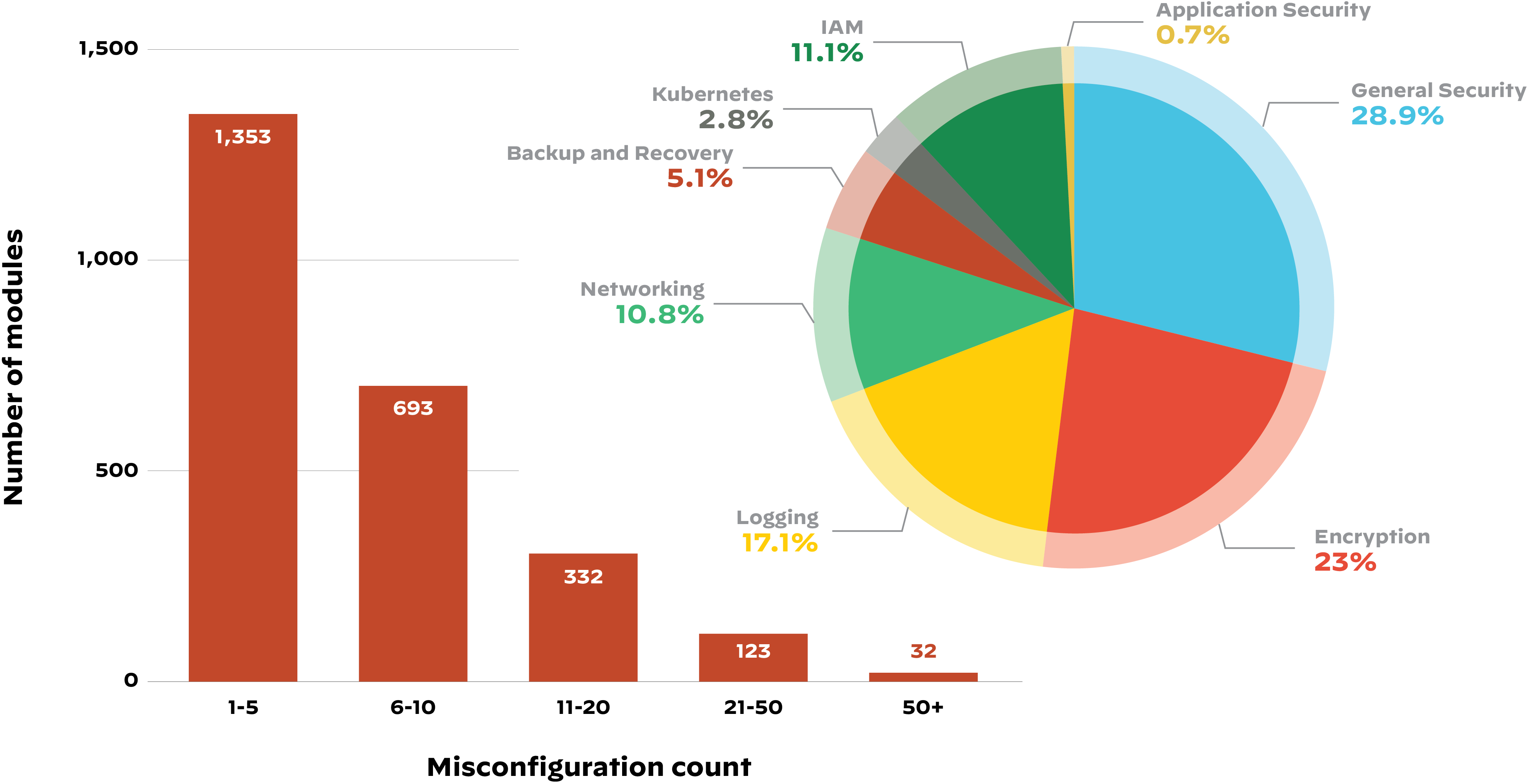
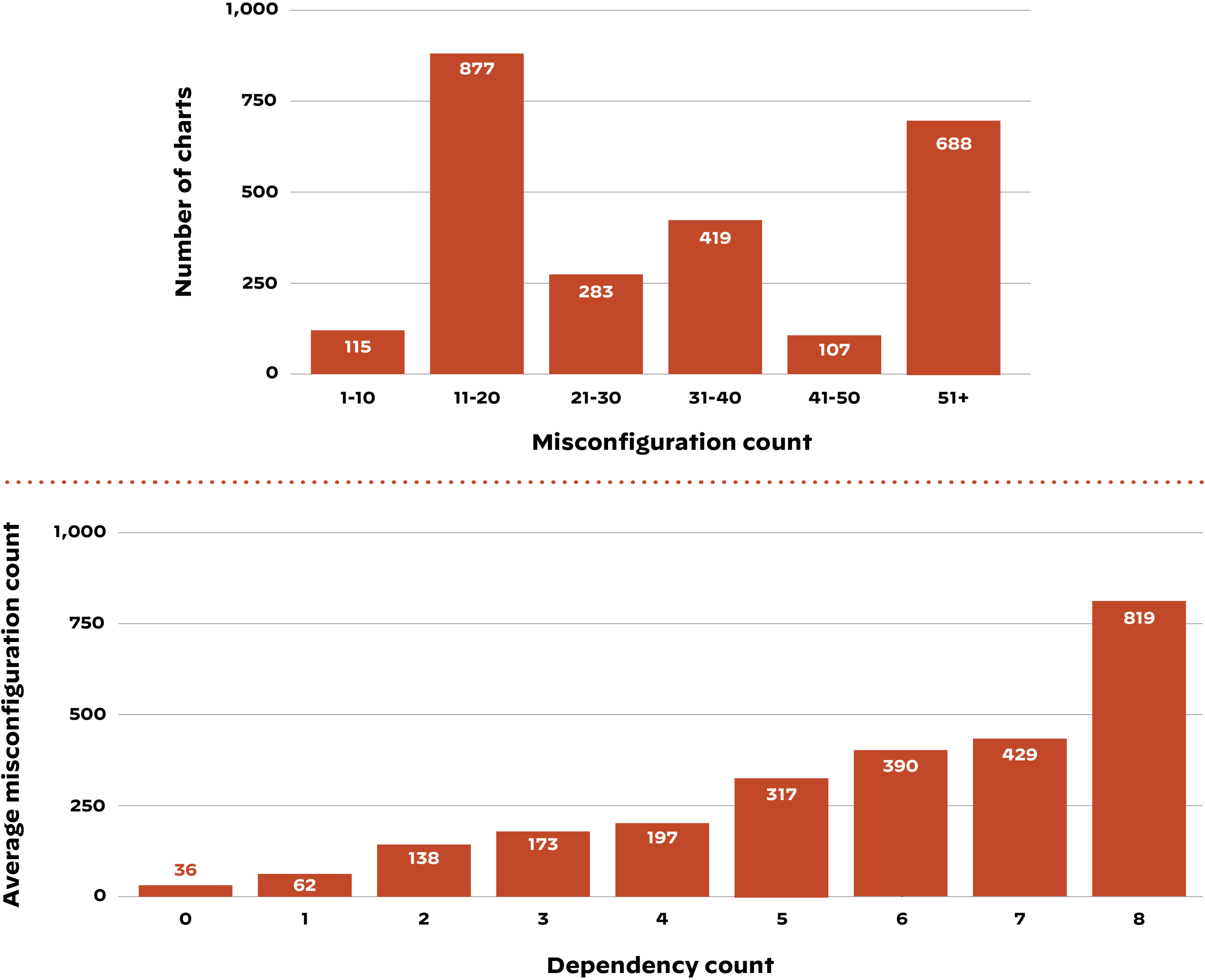
While the SolarWinds incident was the first major software supply chain attack to make international headlines, it wasn’t the first of its kind. Unit 42 researchers have been tracking significant attacks that have occurred to date, including some as early as 2015.
- September 2015 – XcodeGhost: An attacker distributed a version of Apple’s Xcode software (used to build iOS and macOS applications) that injected additional code into iOS apps built using it. This attack resulted in thousands of compromised apps identified in Apple’s App Store®.
- March 2016 – KeRanger: Transmission, a popular open-source BitTorrent client, was compromised through the injection of macOS ransomware into its installer. Users who downloaded and installed the program would be infected with malware that held their files for ransom. Attackers injected the ransomware by taking control of the servers used to distribute Transmission.
- June 2017 – NotPetya: Attackers compromised a Ukrainian software company and distributed a destructive payload with network-worm capabilities through an update to the “MeDoc” financial software. After infecting systems using the software, the malware spread to other hosts in the network and caused a worldwide disruption that affected thousands of organizations.
- September 2017 – CCleaner: Attackers compromised Avast’s CCleaner tool, used by millions to help keep their PCs working properly. The compromise was used to target large technology and telecommunications companies worldwide with a second-stage payload.
In each of these breaches, attackers compromised software development pipelines. They then used the trust placed in them to gain access to other networks.