- What Is a Cloud Service Provider?
-
Defining Organizational Cloud Security Responsibilities
- What Is Infrastructure as a Service?
- Top 3 Cloud Security Considerations
-
Why You Need Cloud Security
-
17 Tips to Securely Deploy Cloud Environments
-
Four Ways to Improve Cloud Security and Compliance
- Cloud Security Glossary & FAQs
- How to Assess Risk in the Cloud
- Cloud Security Is a Shared Responsibility
-
ASPM Best Practices for Enhancing Your Security Posture
- ASPM Foundations and Strategic Benefits in Cloud Environments
- Establishing Centralized Visibility and Data Organization for Continuous Monitoring
- DevSecOps Culture Integration and Shift-Left Security Practices
- KPI Alignment and Remediation Workflows for Vulnerability Management
- Advanced ASPM Optimization and Proactive Risk Management
- ASPM FAQs
What Is Cloud Security?
Cloud security, or cloud computing security, is all about safeguarding the measures, technologies, processes, and policies designed to protect cloud computing systems, data, and infrastructure from cyberthreats. It ensures your data stored and processed in the cloud remains confidential, integral, and available, keeping users and organizations safe from unauthorized access, breaches, and data loss.
While cybersecurity encompasses a broad range of protective measures for information systems, cloud security zeroes in on defending assets hosted on third-party service providers' infrastructure.
Why Is Cloud Security Important?
Cloud security protects sensitive data, applications, and infrastructure hosted in the cloud. As organizations increasingly use cloud computing and third-party cloud service providers (CSPs), they face unique security challenges, including data breaches, unauthorized access, and regulatory compliance.
- Data Protection: Cloud environments often store sensitive personal, financial, and intellectual property data. Cloud security measures safeguard this data from theft, loss, and unauthorized access.
- Regulatory Compliance: Compliance standards like GDPR, HIPAA, and PCI DSS govern many industries. Cloud security helps organizations meet these requirements, avoiding legal consequences and financial penalties.
- Mitigation of Cyberthreats: Cloud environments are frequent targets of cyberattacks, including phishing, ransomware, and DDoS attacks. Effective cloud security solutions protect against these threats, ensuring business continuity.
- Shared Responsibility Model: In cloud computing, security is a shared responsibility between the service provider and the customer. Cloud security tools and practices enable organizations to participate in this partnership.
- Secure Remote Access: With the rise of remote work, employees often access cloud-based systems from various locations and devices. VPNs (virtual private networks), Zero Trust network access (ZTNA), and secure gateways ensure access remains safe without compromising the organization’s data.
- Maintaining Customer Trust: Data breaches or security failures can damage a company's reputation and erode customer trust. Strong cloud security measures help maintain customer confidence and loyalty.
- Cost Efficiency: Proactive cloud security prevents expensive data breaches and downtime, reducing long-term costs associated with incident recovery and compliance violations.
Determine the best option for your organization: CSP-Built Security Vs. Third-Party Cloud-Native Security.
Essential Elements of a Cloud Security Strategy
To grasp cloud security, you must focus on the core tenets of a strategic cloud security plan, one that involves strategies and technology to protect data, applications, and infrastructure. Key areas include:
- Data Protection: Safeguarding data at rest, in transit, and during processing through encryption and access controls.
- Identity and Access Management (IAM): Ensuring only authorized users and devices can access cloud resources.
- Compliance and Governance: Adhering to legal and regulatory requirements, such as GDPR, HIPAA, or CCPA.
- Visibility: Monitoring cloud activity to identify potential security threats through logging, auditing, and analytics tools.
- Network Security: Protecting communication and connectivity within and between cloud environments using firewalls, intrusion detection systems (IDS), and other tools.
- Threat Detection and Prevention: Identifying and mitigating vulnerabilities and risks through automated tools, machine learning, and threat intelligence.
- Incident Response: Establishing procedures to address security breaches or cyberattacks effectively.
- Application Security: Securing applications hosted in the cloud from vulnerabilities or misconfigurations.
The Three Pillars of Cloud Security
The three pillars of cloud security — confidentiality, integrity, and availability — provide a foundational framework for securing cloud environments. These principles, often called the CIA triad, form the backbone of cloud security and overall cybersecurity principles.
Confidentiality
Confidentiality ensures that only authorized individuals and systems can access sensitive data. This is achieved through encrypting data, using strong access controls like multifactor authentication (MFA) and role-based access control (RBAC), and securing APIs while applying the principle of least privilege. By safeguarding confidentiality, organizations can protect their operations and user trust.
Integrity
Integrity ensures data and systems remain accurate, reliable, and tampering-free. Organizations verify data with techniques like hashing and checksums, implement version control and backups to protect against changes, and adopt secure DevOps (DevSecOps) practices to ensure application security.
Availability
Availability ensures that cloud services, applications, and data are accessible when needed. Organizations achieve this through redundancy and failover mechanisms, implementing distributed denial-of-service (DDoS) protection, and performing regular system updates and patches to mitigate vulnerabilities that could cause downtime.
How Does Cloud Security Work?
Cloud security functions across three primary environments: public, private, and hybrid.
Public Cloud
The public cloud delivers IT services over the internet. A third-party provider owns and operates the underlying infrastructure. Organizations use public cloud services for various applications, including web-based solutions and data storage. These services are billed annually or based on actual usage, with costs tied to resource consumption and data traffic.
In a public cloud environment, organizations share the infrastructure with other users but manage their resources through individual accounts. The public cloud offers rapid deployment of scalable applications accessible globally, eliminating the need for substantial upfront investments.
Private Cloud
A private cloud is used exclusively by a single business or organization. It can be owned, managed, and operated by the company, a third-party service provider, or both, and can be located on-premises or off-site.
Private clouds offer the same benefits as public clouds, like elastic scalability and cost savings, resource availability, total control, privacy, and regulatory compliance. They’re ideal for organizations with strict compliance requirements or those that demand absolute data control, such as government agencies and financial institutions.
Hybrid Cloud
A hybrid cloud combines on-premises, private, and public environments while keeping them orchestrated and distinct. Data and applications can move between these environments, offering greater flexibility. Hybrid clouds are suitable for organizations extending their on-premises infrastructure with specific cloud use cases.
For instance, public clouds can handle high-volume, lower-security needs like web-based applications, while private clouds manage sensitive, business-critical operations like financial reporting. Their adaptability makes hybrid clouds an attractive option for many enterprises.
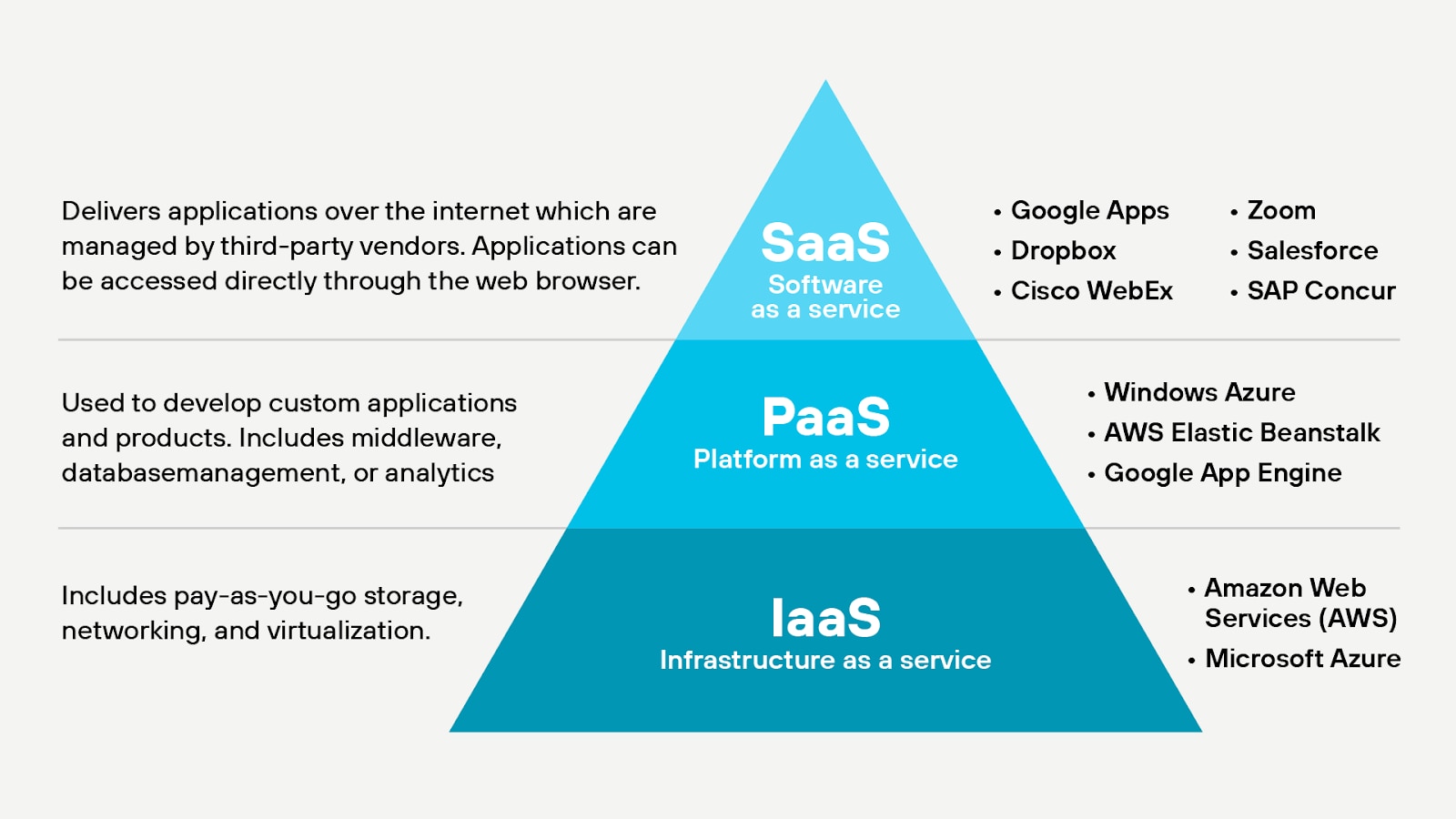
Three Categories of Cloud Service Models
Cloud security requires taking a strategic approach across your organization. Adding multiple security products to solve separate problems will cause issues in the long run. As you look for cloud solutions, consider these options:
- Software as a service (SaaS): Applications like Microsoft Office 365®, Box or Salesforce® allow users from anywhere to access and share data easily. SaaS applications save organizations operational time and costs.
- Platform as a service (PaaS): A service provider, such as AWS® or Azure®, provides the organization with the necessary infrastructure and applications. PaaS allows organizations to reduce hardware and mitigate connectivity issues they may have previously experienced.
- Infrastructure as a service (IaaS): Flexible cloud services allow organizations to pay a single fee based on the amount of data they need to have hosted. This is the most cost-effective way for organizations to get up and running in the cloud.
Organizations may use one or all three of these types of cloud services. You should look for offerings that have a similar security strategy to that of your organization, and that provide multiple security solutions in a single platform.
The Shared Responsibility Model
The shared responsibility model divides security responsibilities between a CSP and its customers. Organizations must align their security strategy with this model to protect their data, applications, and compliance status while leveraging cloud computing benefits. Understanding each party’s role reduces vulnerability risks.
CSP's Responsibilities
- Infrastructure Security: Securing the physical infrastructure, including servers, storage, and networking.
- Software Security: Ensuring the security of foundational services, including hypervisors and operating systems.
- Compliance: Maintaining certifications and compliance for their infrastructure to meet standards like SOC 2, ISO, GDPR, or HIPAA.
Customer's Responsibilities
- Data Security: Securing data stored in the cloud, including encryption and access controls.
- IAM: Managing user identities, roles, and permissions to ensure that only authorized individuals access resources.
- Application Security: Protecting applications, configurations, or workloads deployed in the cloud.
- Compliance: Ensuring usage aligns with organization-specific regulatory requirements.
Workload Responsibilities
Workload responsibilities vary based on the cloud service type:
- IaaS: CSP handles physical infrastructure and virtualization. The customer manages operating systems, applications, and data.
- PaaS: CSP manages the platform, including infrastructure and runtime. The customer focuses on application development, configurations, and data.
- SaaS: CSP handles infrastructure, platforms, and software. The customer is responsible for user access and data security within the software.
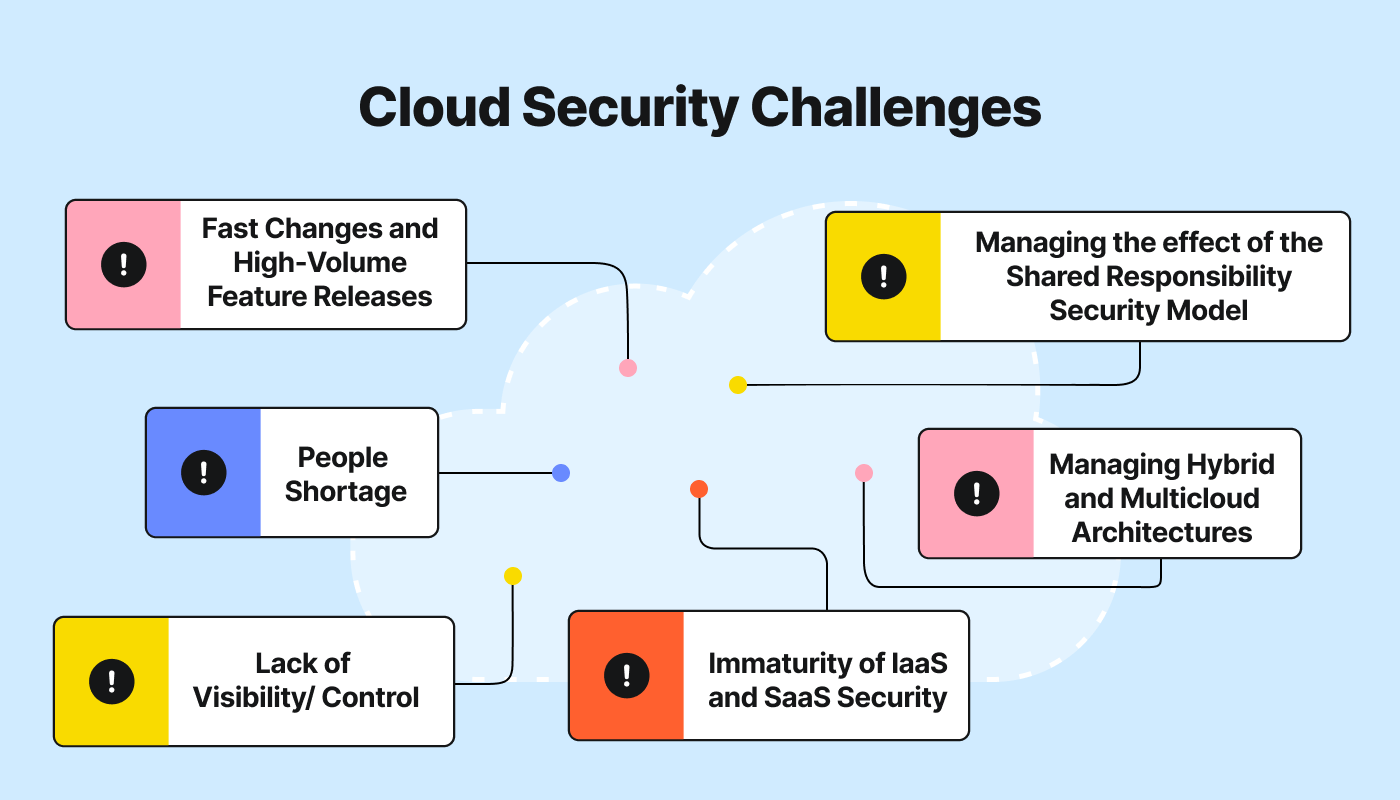
Top Cloud Security Risks and Challenges
Organizations face several cloud security challenges requiring strategic planning, proactive security measures, and diligent monitoring. Key challenges include:
- Sprawl: Cloud services are easy to launch but harder to manage and consolidate in a logical way. Fast-moving teams may find themselves spinning up VMs, databases, and the like haphazardly, with no centralized management strategy in place. By extension, systematically discovering and securing all of those workloads becomes challenging.
- Shadow IT: Along similar lines, teams or individuals may launch shadow IT, or workloads only they know about and are not integrated with central IT management systems. These workloads are also difficult to detect and secure in a centralized fashion.
- Technical security debt: To innovate quickly, teams may overlook weak spots in their security postures in ways that increase the time and effort they need to spend finding and fixing vulnerabilities.
- Inadequate Incident Response: Cloud environments require specialized incident response strategies, and many organizations may lack the necessary expertise and tools to respond effectively to security incidents in the cloud.
- Third-Party Risks: Reliance on third-party vendors and services can introduce additional vulnerabilities and complicate the security landscape.
- Resource Limitations: Organizations may lack the budget, personnel, or expertise to effectively manage and secure their cloud environments, leading to gaps in their security posture.
- Securing Hybrid and Multicloud Environments: Consistent security across diverse environments can prove challenging and resource-intensive.
- Rapid Evolution of Cloud Technologies: It’s vital to keep pace with innovation in cloud services and security, as outdated practices increase vulnerability to threats.
Learn how to evaluate potential vulnerabilities and threats to your cloud infrastructure: How to Assess Risk in the Cloud.
Cloud Security Tools
A strong cloud security strategy involves adopting tools designed to secure cloud environments. Essential tools should provide:
- Visibility into cloud application activity.
- Detailed usage analytics to prevent data risk and compliance violations.
- Context-aware policy controls to enforce and remediate violations.
- Real-time threat intelligence to detect and prevent new malware.
Types of Cloud Security Tools
Cloud security tools protect cloud environments, applications, and data from threats, unauthorized access, and vulnerabilities. Key tools include:
- Cloud Access Security Brokers (CASBs): Monitor and manage access to cloud applications, enforce security policies, and provide visibility into cloud usage and compliance.
- Cloud Workload Protection Platforms (CWPPs): Secure workloads across multicloud environments, providing runtime protection and vulnerability management.
- IAM Tools: Ensure only authorized access to cloud resources, supporting SSO, MFA, and RBAC.
- Cloud Encryption Tools: Encrypt data at rest, in transit, or during processing with key management services.
- Cloud Security Posture Management (CSPM) Tools: Continuously monitor cloud environments for misconfigurations and compliance risks, offering automated remediation.
- Web Application Firewalls (WAFs): Protect cloud-hosted web applications from threats like SQL injection and DDoS attacks.
- Endpoint Protection Tools: Secure endpoints accessing cloud resources, detecting and responding to malware and other threats.
- Data Loss Prevention (DLP) Tools: Prevent unauthorized sharing or transferring of sensitive data.
- Intrusion Detection and Prevention Systems (IDPS): Detect and respond to suspicious activities within cloud environments.
- Cloud Monitoring and Analytics Tools: Provide visibility into cloud performance, usage, and security threats, enabling logging and incident analysis.
Cloud Security Best Practices
Protecting data, applications, and systems in the cloud involves following practical security practices. Checking off the following steps helps organizations stay ahead of cyberthreats and ensures smooth, compliant business operations:
- Understand shared responsibility.
- Secure the perimeter.
- Monitor for misconfigurations.
- Use IAM practices to enforce password, device, and access management.
- Enable security posture visibility.
- Implement policies to prevent unauthorized application access and secure data.
- Limit data access to necessary personnel to prevent leaks.
- Secure your containers.
- Conduct regular security audits, vulnerability scans, and timely security patches.
- Adopt a Zero Trust approach for updated security policies and remote access needs.
- Educate and train staff on current cloud security trends to identify suspicious behavior.
- Use log management and continuous monitoring.
- Conduct penetration testing.
- Encrypt data to keep it secure and accessible only to authorized users.
- Meet compliance requirements.
- Implement an incident response plan for handling security incidents.
- Secure all applications.
- Maintain a resilient data security posture.
- Consolidate cybersecurity solutions.
- Leverage a cloud detection and response (CDR).
With these human-centric guidelines and strategic focus points, organizations can efficiently manage and secure their cloud environments, ensuring protection against evolving cyberthreats and regulatory compliance.