-
- How does a secure web gateway work?
- Why are secure web gateways necessary for network security?
- What are the benefits of secure web gateways?
- What are the features of secure web gateways?
- What are the most common secure web gateway deployment challenges?
- How do secure web gateways enforce acceptable use policies?
- How do secure web gateways secure remote workforces and branch offices?
- What is the role of secure web gateways in SASE?
- How do secure web gateways relate to compliance?
- Comparing secure web gateways with other security technologies
- What is the history of secure web gateways?
- How are secure web gateways evolving for the future?
- How to choose the right secure web gateway for your business
- Secure web gateways FAQs
Table of Contents
- What Is a Cloud Secure Web Gateway?
- Secure Web Gateway vs. CASB: What Is the Difference?
- Secure Web Gateway vs. Firewall: What Is the Difference?
- What Are Secure Web Gateway Use Cases?
-
Secure Web Gateway vs. Proxy Server: What Is the Difference?
- What Is an SWG?
- What Is a Proxy Server?
- Is a Proxy and Secure Web Gateway the Same?
- What Are the Differences Between SWGs and Proxy Servers?
- What Are the Similarities Between SWGs and Proxy Servers?
- How to Choose Between SWG vs. Proxy Server
- The Roles of SWGs and Proxy Servers in SASE
- SWG vs. Proxy Server FAQs
- SASE and Secure Web Gateway: How Are They Related?
- Secure Web Gateway vs. WAF: What Is the Difference?
- What Is a Next-Generation Secure Web Gateway (SWG)?
What Is a Secure Web Gateway (SWG)? | A Comprehensive Guide
7 min. read
Table of Contents
A secure web gateway (SWG) is an on-premises or cloud-delivered network security technology that filters internet traffic and enforces corporate and regulatory policy compliance. It sits between users and the internet, inspecting web requests to block access to malicious or non-compliant websites and applications.
SWGs also help prevent data breaches by enforcing acceptable use policies and applying controls such as URL filtering, anti-malware scanning, and data loss prevention (DLP).
How does a secure web gateway work?
A secure web gateway (SWG) sits between users and the internet. It filters traffic and enforces security policies before allowing access to web resources.
Here’s how it works:
When a user tries to visit a website, their request is first sent to the SWG. The SWG checks the request against defined policies. It looks at the destination URL, the user’s identity, and the type of content being accessed. If the request is safe and allowed, the SWG forwards it to the internet. If not, the request is blocked.

The same happens in reverse. Responses from the internet are inspected by the SWG before they reach the user. This prevents malware, phishing pages, or other malicious content from making it through.
In other words:
The SWG becomes a checkpoint for both outgoing and incoming web traffic.
It does this using key security functions such as:
URL filtering
Anti-malware scanning
Application control
Some solutions also include data loss prevention (DLP), HTTPS inspection, and other controls.
SWGs can be deployed in several ways. That includes physical appliances, cloud-based services, or software running on virtual machines. The deployment model depends on the organization's network architecture and remote access needs.
Because the SWG's position in the traffic flow makes it a central enforcement point. It ensures internet access is both safe and compliant with policy.
Why are secure web gateways necessary for network security?
Secure web gateways help address a fundamental gap in enterprise security: unmanaged internet access.
Here's why that matters:
Most organizations rely on the internet to support daily work. But internet traffic is inherently untrusted—and often outside the visibility of traditional security tools. Without an intermediary, users can unknowingly introduce risks just by browsing the web, clicking links, or accessing cloud services.
- Nearly half of the security incidents (44%) we investigated involved a web browser, including phishing attacks, malicious redirects and malware downloads.
- In nearly one in five cases, data exfiltration took place within the first hour of compromise.
- 70% of the incidents Unit 42 responded to happened on three or more fronts, underscoring the need to protect endpoints, networks, cloud environments and the human factor in tandem.
Web threats have also grown more evasive. Many use encrypted channels, impersonation techniques, or compromised legitimate sites to bypass basic defenses. Without safeguards in place, these threats can slip into the network undetected.
It's not just about blocking attacks. SWGs also help organizations regain control over how internet resources are used. That includes enforcing appropriate access, limiting risky behaviors, and preventing data from being mishandled or exfiltrated.
In other words:
A secure web gateway is necessary because unmanaged internet access is no longer safe by default—and businesses need a reliable way to reduce that risk.
| Further reading: What Are Secure Web Gateway Use Cases?
What are the benefits of secure web gateways?

Reduced risk from threats hidden in encrypted traffic
Secure web gateways can decrypt and inspect HTTPS traffic, which helps uncover malware, phishing sites, and other threats that would otherwise bypass security controls.Smaller external attack surface
By blocking access to known malicious or unauthorized sites, SWGs reduce the number of internet-based pathways that attackers can exploit.Consistent security for remote users
Organizations can maintain the same level of protection for users working outside the corporate network, supporting safer access to cloud and SaaS resources.Centralized and uniform policy enforcement
SWGs allow administrators to apply consistent web access policies across all users and locations, improving manageability and reducing the risk of policy gaps.Lower infrastructure and operational overhead
Cloud-delivered SWGs help eliminate the need for distributed hardware and reduce the complexity of maintaining on-premises appliances.Improved protection against accidental data loss
With built-in data controls, SWGs help prevent sensitive information from being uploaded or exposed through unsecured web channels.Stronger resilience for internet-connected systems
Systems that rely on continuous internet access—like servers or headless devices—can operate more securely with SWG protections in place.Better alignment with cloud and digital transformation goals
SWGs support scalable, internet-first architectures by helping organizations secure user access during cloud adoption and workforce changes.
What are the features of secure web gateways?

Secure web gateways (SWGs) include a combination of traffic inspection and access control technologies that help organizations enforce policy and reduce exposure to web-based threats.
URL filtering

URL filtering allows organizations to control access to websites based on content categories, risk levels, or user groups. It helps block access to known malicious domains and restricts browsing to acceptable content based on policy.
Threat prevention
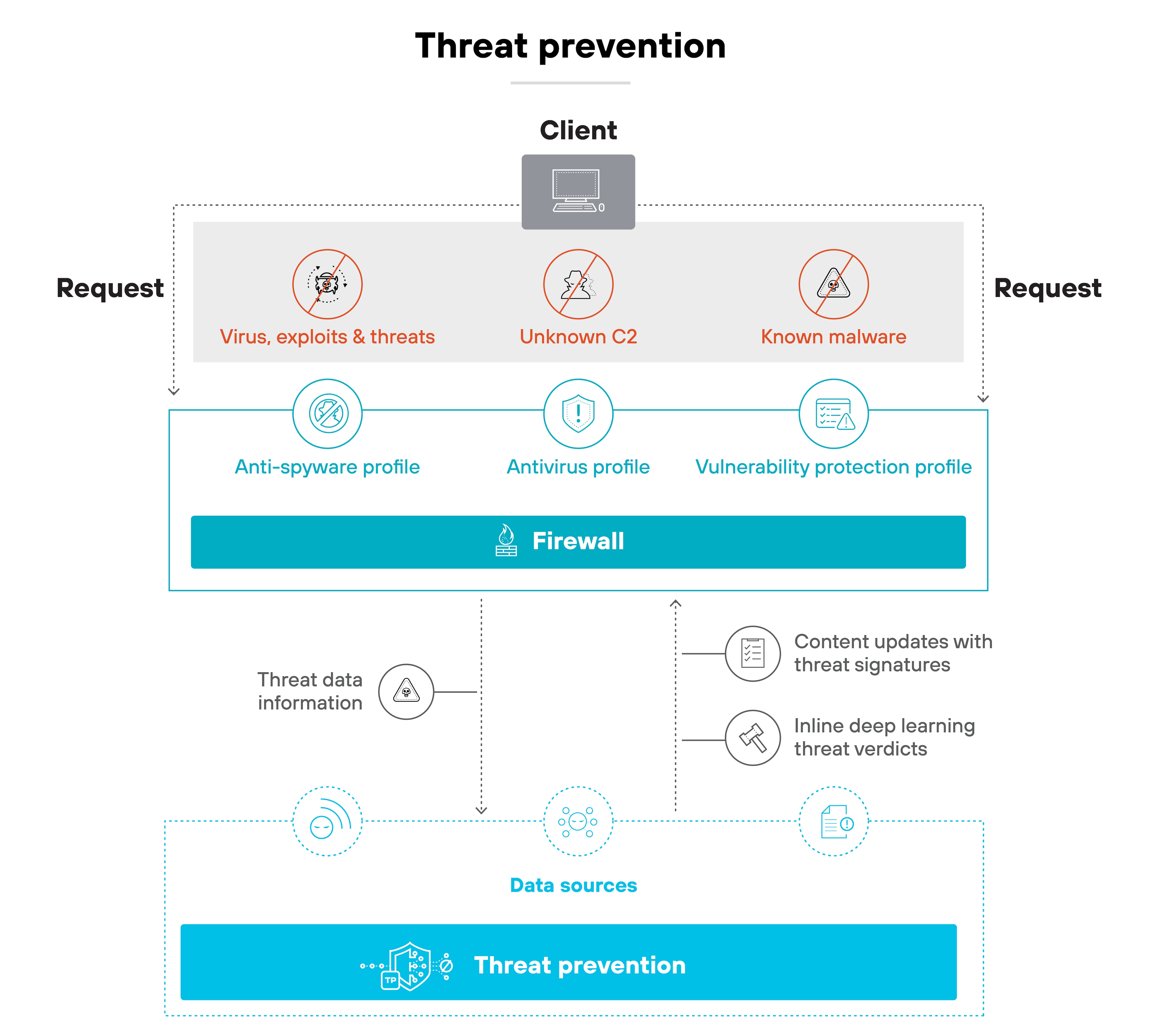
SWGs use threat prevention techniques to identify and block injection attacks, exploits, and malicious command-and-control (C2) activity. This includes detecting patterns that match known attack behavior and stopping traffic targeting vulnerable software or web applications.
Application control

Application control enables policy enforcement on web-based applications. Administrators can allow, block, or restrict access to specific apps or app features to help manage risk and support acceptable use.
Data loss prevention (DLP)

DLP features help prevent the unauthorized transfer of sensitive data through web traffic. These controls support compliance efforts by monitoring content and enforcing rules that govern how data can be used or shared.
Antivirus and antimalware
Antivirus tools scan web traffic for known malware, including viruses, Trojans, and spyware. Antimalware features add behavioral analysis and sandboxing to detect unknown or evasive threats embedded in files or scripts.
DNS security

DNS security helps block domain-based threats. It detects suspicious or malicious DNS activity such as tunneling, domain generation algorithms (DGAs), or connections to attacker infrastructure.
HTTPS inspection

HTTPS inspection enables traffic analysis within encrypted sessions. The SWG decrypts, inspects, and re-encrypts web traffic to apply the same security controls to HTTPS as it would to unencrypted traffic.
What are the most common secure web gateway deployment challenges?

Secure web gateway (SWG) deployments can introduce operational and security challenges that impact usability, visibility, and effectiveness.
- Increased complexity in security stacks
Deploying SWGs as standalone point products can add to the overall complexity of a security environment. Without native integration into a broader security framework, they may require separate management and monitoring processes. - Negative impact on user experience
Traditional SWG architectures that backhaul traffic to centralized data centers can introduce latency. This may degrade application performance and lead users to bypass or disable security tools. - Difficulty adapting to modern cyberthreats
Legacy SWGs often rely on static indicators such as signatures or pre-crawled content. These approaches may be less effective against modern attack techniques that use dynamic, evasive methods to avoid detection.
How do secure web gateways enforce acceptable use policies?
Secure web gateways enforce acceptable use policies by identifying users and applying controls based on those identities.
This starts with authentication. The SWG can verify users through methods such as single sign-on or username and password. Once the user is identified, the system applies access rules that match their role or group.

For example:
An employee trying to visit a hacking-related website might be blocked. But someone in the security team could be allowed access for research purposes. The policy adapts based on who the user is and what they’re authorized to do.
Organizations use acceptable use policies to define what types of online content are allowed. These policies often block high-risk categories such as gambling, adult content, or known malicious sites.
In other words:
The SWG gives companies a way to enforce internet usage standards while aligning access with user roles and business needs.
How do secure web gateways secure remote workforces and branch offices?
Cloud-delivered secure web gateways (SWGs) help organizations protect users outside the traditional network perimeter. That includes remote workers and branch offices that no longer rely on a central data center.
Here’s how:

Cloud-based SWGs act as intermediaries between users and the internet. This allows remote traffic to be inspected and filtered without routing it back through a central location. It also gives users direct access to cloud and web resources while maintaining consistent security.
For branch offices without on-site infrastructure, this model avoids the need for backhauling traffic to a distant security stack. The result is lower latency and more scalable coverage.
It’s worth noting:
Earlier SWG deployments were typically on-premises appliances. Organizations often routed traffic through VPNs or IPsec tunnels back to headquarters. But that hub-and-spoke model was not built for today’s distributed environments. It introduced complexity and often degraded performance.
In contrast, cloud-delivered SWGs align better with hybrid work, cloud adoption, and decentralized IT architectures.
What is the role of secure web gateways in SASE?
Secure web gateways (SWGs) are a core part of secure access service edge (SASE) architecture. They provide the traffic inspection and policy enforcement needed to secure internet access across users, locations, and devices.

Within a SASE framework, the SWG function becomes part of a broader, cloud-delivered architecture that combines networking and security into a single service.
This integration helps eliminate the limitations of standalone SWG deployments. When SWG capabilities are built into SASE, they work alongside other controls to support consistent policy enforcement and reduce operational complexity. It also enables direct-to-internet access with unified inspection, which can help improve both security outcomes and user experience.
| Further reading: SASE and Secure Web Gateway: How Are They Related?
How do secure web gateways relate to compliance?
Secure web gateways (SWGs) help organizations meet regulatory requirements by monitoring and controlling how data moves across the internet.
This is especially relevant in sectors like healthcare or finance, where regulations often require strict oversight of sensitive information.
Here's how:
SWGs inspect web traffic to detect and block potential data leaks.
When combined with data loss prevention (DLP), this inspection helps prevent unauthorized sharing of personal or regulated data. For example, organizations subject to GDPR can use SWGs to enforce region-specific rules around data access and transfer.
SWGs also provide visibility into user activity through logging and reporting.
These records support audit requirements by showing what data was accessed, where it went, and whether any policy violations occurred. In highly regulated environments, this level of detail is often necessary.
Another benefit is customizability.
SWGs can be configured to meet different compliance needs based on region, industry, or internal policy. And as regulations evolve, updating SWG rules and capabilities helps organizations stay aligned with changing requirements.
Comparing secure web gateways with other security technologies
Secure web gateways (SWGs) are just one piece of the broader enterprise security architecture.
To understand where they fit—and where they don't—it helps to compare them against other technologies with overlapping or adjacent capabilities.
This table provides a side-by-side breakdown of SWGs, CASBs, firewalls (including NGFWs), proxy servers, and web application firewalls (WAFs). The goal isn't to suggest one replaces another—but to highlight how each contributes to different layers of protection, especially in modern cloud and hybrid environments.
| Parameter | Secure web gateway (SWG) | Cloud access security broker (CASB) | Firewall (including NGFW) | Proxy server | Web application firewall (WAF) |
|---|---|---|---|---|---|
| Primary function | Filters and controls web traffic to enforce security and usage policies | Secures access to and usage of cloud applications and services | Controls network traffic based on IP, ports, and protocol rules | Acts as an intermediary between users and internet destinations | Protects web apps by filtering and monitoring HTTP/S traffic |
| Traffic scope | Internet-bound traffic | SaaS, PaaS, and IaaS environments | All network traffic (not just web or cloud) | Web-based traffic only | Inbound HTTP/S traffic to web applications |
| Deployment options | On-premises appliances, cloud services, or software | Cloud-hosted software, API-based, or on-premises | Hardware appliances, virtual appliances, or cloud-native | Standalone servers or software | Software, hardware appliances, or cloud-delivered service |
| Policy enforcement | Applies web usage policies and acceptable use controls | Applies policies to cloud data and services usage | Enforces security rules across the network stack | Basic content filtering and access control | Applies security policies to protect web apps from attack |
| Threat protection | Blocks malware, phishing, and web-based threats | Protects against cloud-native threats, account compromise, and misuse | Prevents threats using packet inspection and connection tracking | Basic IP masking; no built-in threat protection | Blocks application-layer threats like XSS, SQLi, and cookie poisoning |
| Data loss prevention (DLP) | Included; used to prevent sensitive data exposure via the internet | Included; used for cloud data classification and enforcement | May include DLP depending on the solution | Not included | Not typically included |
| Encrypted traffic inspection | Decrypts and inspects HTTPS traffic | May include encrypted traffic inspection for cloud data access | Can inspect encrypted traffic across protocols | May support HTTPS proxying but lacks full inspection | Inspects HTTP/S traffic for malicious content |
| Application-layer focus | Yes | Yes | Partially; some NGFWs include application-layer inspection | No | Yes; specific to application-layer threats |
| Cloud service security | No | Yes | No | No | No |
| Web traffic control | Yes | Limited to cloud services | No | Yes | No |
| Granular access controls | Yes; based on user, device, and location | Yes; with detailed contextual controls | Limited; often lacks user/device-level policy depth | No | No |
| Use in SASE | Yes; core SASE component | Yes; extends SASE to cloud service access | Yes; included as FWaaS in SASE | Not a core SASE function; sometimes integrated | Not a core SASE component but can complement SASE |
| Further reading:
- Secure Web Gateway vs. CASB: What Is the Difference?
- Secure Web Gateway vs. Firewall: What Is the Difference?
- Secure Web Gateway vs. Proxy Server: What Is the Difference?
- Secure Web Gateway vs. WAF: What Is the Difference?
What is the history of secure web gateways?

Secure web gateways first emerged in the late 1990s and early 2000s. They were created to address the growing need for web filtering as internet usage increased and web-based threats became more common.
Over time, SWG functionality became part of a broader concept called security service edge (SSE). SSE brought together internet security, private application access, and identity-based access control. This included not just SWGs, but also technologies like Zero Trust Network Access (ZTNA) to replace traditional VPNs.
Later, SSE expanded to include other capabilities like cloud access security broker (CASB), data loss prevention (DLP), and firewall as a service (FWaaS). The goal was to consolidate security tools into one cohesive platform.
Eventually, networking functions like software-defined wide area networks (SD-WAN) were added. That combination—SSE plus SD-WAN—formed the basis for secure access service edge (SASE).
In other words:
SASE represents the latest stage in the evolution of SWGs. It reflects a shift toward converged security and networking architectures that simplify operations and enforce consistent policy across all users and locations.
How are secure web gateways evolving for the future?
Secure web gateways are moving toward cloud-delivered models. This shift supports scalability and improves cyber resilience as organizations prepare for evolving internet threats.

Originally, SWGs were built on on-premises proxy appliances. These proxies were deployed in data centers or large offices—at a time when most employees worked on-site. But with more users working remotely and relying on SaaS apps, backhauling traffic through those proxies started to slow things down.
To address this, many SWG providers now offer cloud-delivered proxies. These can support legacy proxy-based deployments or meet specific compliance needs. At the same time, many organizations have adopted cloud-native SSE platforms without relying on proxy functionality at all.
Here's what's changing now:
Artificial intelligence is becoming a key part of how SWGs detect and stop threats. AI can help analyze large volumes of traffic in real time and identify sophisticated threats—like spear phishing and evasive malware—that traditional methods might miss.
Looking ahead, upgrading an SWG isn't just about better threat detection. It's also about simplifying operations. That means choosing solutions with built-in integration, support for digital experience monitoring, and AIOps capabilities. The goal is clear: consistent, secure access to internet and SaaS apps—delivered with performance, scalability, and resilience.
| Further reading:
How to choose the right secure web gateway for your business

Choosing the right SWG involves more than checking off feature boxes. It's about finding a solution that fits your security goals, operational needs, and future plans. Here are the key factors to consider:
- Balance security and user experience
Strong protections are important. But so is giving users efficient, uninterrupted access to internet resources. - Simplify operations wherever possible
Too many products and interfaces can create risk. Fewer dashboards and vendors can make security easier to manage. - Consider broader platform integration
Look at how the SWG fits into your long-term strategy. It should serve as a step toward an integrated SSE or SASE architecture. - Prioritize centralized policy management
A solution that supports unified policy enforcement helps IT teams maintain consistent control across environments. - Evaluate vendor consolidation opportunities
A single SASE platform that includes SWG, FWaaS, CASB, ZTNA, and SD-WAN may offer operational advantages. Especially for teams trying to reduce tool sprawl. - Plan for scalability and future requirements
Choose an SWG that can adapt as your traffic volumes grow or your threat landscape changes. - Assess vendor reputation and support
Consider the vendor's track record. And be sure they offer the level of support your organization expects.
In other words:
The right SWG is not just about security. It's also about fit, flexibility, and long-term alignment with your IT and security strategy.
Secure web gateways FAQs
A virtual private network (VPN) primarily ensures a secure and encrypted connection between a user's device and a private network, allowing remote access as if the user were on that local network. A secure web gateway (SWG), on the other hand, is designed to filter and inspect web traffic, protecting users from malicious web content and ensuring compliance with corporate internet use policies. While both offer security features, the core function of a VPN is secure inbound access and connectivity, whereas an SWG focuses on outbound access to the internet with full security inspection.
Secure web gateways (SWGs) function as a shield for an organization's users against hazardous websites and unwanted content that resides beyond the organization's perimeter. On the other hand, web application firewalls (WAFs) serve as a protective measure for web-based applications that the organization hosts, warding off initiated attacks from external sources. In essence, the primary role of SWGs lies in safeguarding client-initiated web traffic, while the function of WAFs centers around the protection of web applications exposed to web traffic.
A secure web gateway ( SWG) is not a proxy. However, an SWG can be deployed as a proxy.
A secure web gateway ( SWG) is not a firewall, but there are overlapping capabilities. While both are security tools, they serve distinct purposes. A firewall acts as a barrier between networks, controlling and monitoring inbound and outbound traffic based on predefined security rules. In contrast, an SWG focuses on inspecting and filtering application-level web traffic, safeguarding users from malicious web content and ensuring policy compliance for internet use.
A secure web gateway (SWG) provides granular inspection of web traffic at the application level, ensuring that malicious or inappropriate web content is not accessed and that end users are protected from web threats like phishing, ransomware and malware. On the other hand, DNS security protects organizations by disrupting attacks that use DNS. These attacks can exploit DNS to establish command-and-control connections, attack hosts inside the corporate network from the internet, perform distributed denial-of-service (DDoS) attacks, and even take over domains completely. While SWGs focus on internet and SaaS security, DNS security primarily defends against DNS-layer attacks.
The objectives of a secure web gateway (SWG) are to filter internet traffic, enforce security and acceptable use policies, and protect users and organizations from online threats. SWGs scrutinize every outgoing web request from client devices, ensuring requests do not breach set policies and only permitting them if deemed safe. Similarly, incoming data is inspected before reaching users. By functioning as a web gateway, SWGs provide safe internet and SaaS access, prevent malware from reaching corporate networks and shield organizations from potential data breaches.
A secure web gateway (SWG) filters internet traffic and enforces security and acceptable use policies, safeguarding users and organizations from online threats associated with web browsing. In contrast, a secure email gateway (SEG) specifically focuses on inspecting and filtering inbound and outbound email traffic, protecting against email-borne threats, such as phishing, spam and malware. While both serve protective functions, the SWG targets broader web-based threats, while SEG addresses email-specific risks.
A secure web gateway helps enforce web usage policies, protect against internet-based threats, and prevent data loss. It filters web traffic, inspects encrypted connections, and provides user-level access controls to support compliance and secure internet use.
A firewall protects all network traffic by enforcing security rules at the network level. A secure web gateway focuses on filtering and securing web traffic specifically, with features like URL filtering, malware protection, and policy enforcement for internet access.
