-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
Dark Web Leak Sites: Key Insights for Security Decision Makers
- Dark Web Leak Sites Explained
- Evolving Extortion Tactics
- The Role of Leak Sites in Ransomware Double Extortion
- Critical Risks Exposed by Data Leak Sites
- Anatomy of a Dark Web Leak Site
- Proactive Defense: How Organizations Can Mitigate Dark Web Leaks
- Dark Web Leak Site FAQs
- What to Do If Your Organization Appears on a Dark Web Leak Site
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- What Is Password Spraying?
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What is Spear Phishing?
Spear phishing is a targeted form of phishing where attackers use social engineering tactics to trick individuals or organizations into divulging sensitive information, such as login credentials or financial information. Unlike other kinds of phishing scams, which are usually sent to large groups of people, spear phishing messages target specific individuals. They are personalized to appear as if they are from a trusted source, like a colleague or a reputable organization.
Spear Phishing Email Tactics
Spear phishing emails often use persuasive language and formatting to appear legitimate. Some common tactics used in spear phishing emails include the below examples.
Urgent or Threatening Language
Spear phishing emails often create a sense of urgency or threat, encouraging the recipient to take immediate action without taking the time to verify the authenticity of the request. For example, the email might claim that there has been a security breach and that the recipient needs to verify their credentials in the attached link to avoid further damage.
Suspicious Sender Information
Spear phishing emails often come from suspicious or unfamiliar email addresses, or they may spoof the email address of a trusted individual or organization. Sometimes, threat actors might deliberately misspell the sender's information or contain other subtle variations to deceive the recipient.
Incorrect Grammar or Spelling
Spear phishing messages may contain grammar or spelling mistakes, which can be a red flag indicating that the email is not legitimate. However, advancements in AI and machine learning (ML) have enabled attackers to craft increasingly sophisticated emails with excellent grammar and spelling, making them harder to detect.
Suspicious Attachments or Links
Spear phishing emails may contain suspicious attachments or links that, when clicked or downloaded, can install malware or direct the recipient to a fake website where threat actors can steal their personally identifiable information (PII). The attachments or links may be disguised as legitimate documents or webpages to deceive the recipient.
Unusual Requests for Information
Spear phishing emails may make unusual requests for personal or sensitive information, such as passwords, Social Security numbers, or financial account information. The email may also ask the recipient to perform a task or take an action that is not typical of their job responsibilities or usual behavior.
How Does Spear Phishing Work?
Spear phishing uses email to exploit emotions, such as trust, fear, and curiosity, to extract high-value and sensitive data or other confidential information. Attackers typically research their targets in advance through social media or additional publicly available information to craft a personalized phishing email that is likely to trick their target. They may pose as a representative from a reputable organization or even a colleague, manager, or executive within the target organization.
The phishing attempt will contain a call to action like one of the following: clicking on a link, downloading an attachment, providing login credentials or sending real-time payments. Understanding attackers' preparation process for and executing a spear phishing attempt can help prime security teams and employees for this popular attack method.
Gathering Information
Spear phishers typically gather information about their targets through various methods, including:
- Social media: Attackers may use social media platforms such as Facebook, LinkedIn, or Twitter to learn more about their targets' personal and professional lives.
- Online research: Threat actors may conduct online research to find out information about their targets' job titles, responsibilities, and the companies they work for.
- Email lists: Attackers may obtain email lists from data breaches, dark web marketplaces or other sources to target specific individuals or organizations.
Crafting the Email
Once the spear phisher has gathered enough information about their target, they will craft an email that appears legitimate and trustworthy. This can involve any of the methods discussed above.
The email is designed to look as authentic as possible, often replicating the style, tone, and signature of the impersonated individual or organization. The email will typically include a request or some urgency for encouraging the target to act quickly, which might involve clicking a link, downloading an attachment or providing sensitive information.
Executing the Attack
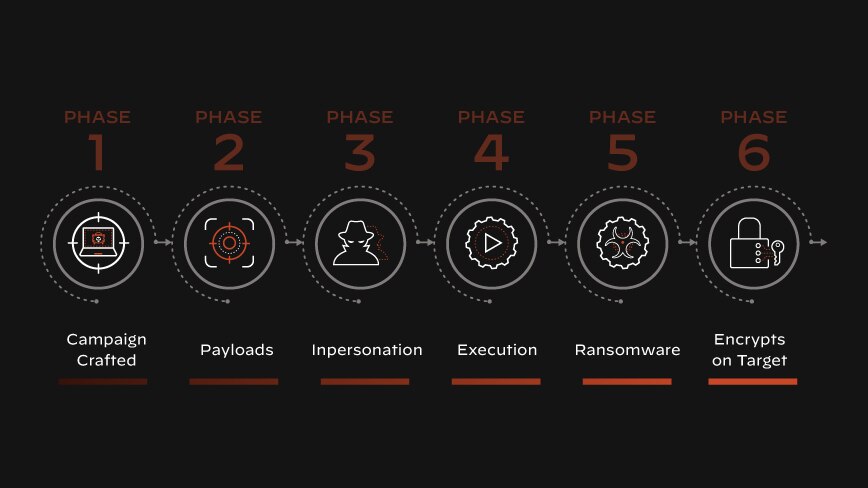
The email is sent to the target. Suppose the target falls for the scam and clicks the malicious link or downloads the attachment. In that case, they may inadvertently do any of the following: install malware on their device, provide sensitive information or grant the attacker access to secured systems or data.
Spear phishing attacks are designed to deceive targets into disclosing sensitive information or infecting their computer systems with malware. It's essential to be vigilant and carefully scrutinize all incoming emails, especially those that request sensitive information or appear suspicious.
Depending on the attacker's goal, they might use this access to steal sensitive information (such as financial data or personal identification information) or to install further malicious software. This can give them extended access, control over the system, or the ability to launch additional attacks.
Remember, spear phishing attacks are often highly sophisticated and can be difficult to spot. To protect yourself, it's important to be cautious about any emails requesting sensitive information, even if they appear to be from trusted sources.
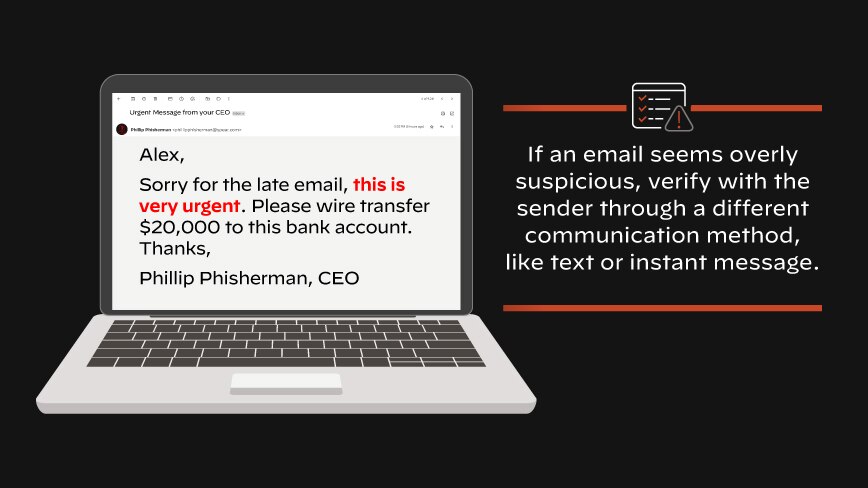
Double-check the email address, be wary of unsolicited attachments or links, and when in doubt, reach out to the alleged sender through a different communication channel to verify the request. Additionally, maintaining updated security software can help protect against some of the malicious actions these emails may attempt.
Types of Spear Phishing Attacks
Spear phishing attacks are usually delivered through suspicious emails or text messages, known as smishing. Here are a few tactics threat actors use to exfiltrate data from victims:
CEO Fraud
CEO fraud is where the attacker impersonates a high-ranking executive, like a CEO, or another person in a position of authority to trick the target into taking a specific action, such as making a wire transfer or providing sensitive information. In a typical CEO fraud attack, the attacker will send an email that appears to be from a CEO or other C-level executive, often using a spoofed email address that seems legitimate.
Email attempts may use tactics to make the request appear urgent and legitimate, like threatening consequences if the target does not comply. They might provide a plausible explanation for the request or even use social engineering techniques to take advantage of the target’s trust and the implied credibility of the position. Employees may not question such requests, especially if they appear to be coming from someone in a position of authority. As a result, CEO fraud attacks can be highly effective and result in significant financial losses for companies.
Whaling
Whaling is a type of spear phishing that targets high-level executives or individuals with access to sensitive information. Attackers target the organization's “big fish” — or “whales.” Whaling attacks often involve a high degree of sophistication and social engineering techniques to build trust and credibility with the target. For example, the attacker may conduct extensive research on the target's job responsibilities, work history, and personal life to create a highly personalized and convincing email.
Whaling attacks can be highly effective, as high-level executives may have access to large amounts of company funds and sensitive information. They may also be more susceptible to these attacks, as they are often targeted with a high volume of emails and may not have time to scrutinize each one carefully.
Business Email Compromise
Business email compromise (BEC) is a threat where actors use spear phishing tactics to access an organization's email system and carry out fraudulent activities. They typically involve compromising an employee's email account and using it to impersonate the employee, such as sending email messages from the employee's account to request fund transfers or other sensitive information.
BEC attacks can take several forms, including:
- CEO fraud
- Vendor email compromise: Impersonating a vendor or supplier of the business to request payments or financial information
- Account compromise: Compromising an employee's email account to gain access to sensitive information, such as financial statements or customer data
BEC attacks are highly effective cyberattacks that can result in substantial financial losses. The U.S. Federal Bureau of Investigation calls BEC the “$43 billion scam,” referring to statistics for incidents reported to the Internet Crime Complaint Center from 2016–2021. According to the 2025 Unit 42® Global Incident Response Report, Unit 42 observed that when threat actors gained access through phishing campaigns, the most common associated incident type was business email compromise, accounting for 76% of cases. In 2021, Unit 42 found that 89% of organizations that had been subject to BEC attacks had not turned on multifactor authentication (MFA) or followed email security best practices.
Brand Impersonation
Brand impersonation is a type of spear phishing attack where the attacker impersonates a well-known brand or organization to trick the target into providing sensitive information. Brand impersonation attacks often involve creating a fake website or email that appears to be from a legitimate source, using logos, branding, and other details to make the attack appear authentic.
Brand impersonation attacks can take several forms, including:
- Fake login pages: The attacker creates a fake login page that looks like the legitimate brand's website, often using similar colors, fonts, and logos to make it appear authentic. The target is thus tricked into entering their login credentials, which the attacker captures.
- Phishing emails: A phishing email that appears to be from a legitimate brand is sent to the victim, often using the brand's logo and other branding elements to make it appear authentic. The email may request the target click on a link or provide sensitive information, such as login credentials or financial data.
- Malicious apps: The attacker creates a malicious app or mobile website that appears to be from a legitimate brand, often using similar branding and design elements. The app or website may request access to sensitive information or may contain malware that steals information from the target's device.
Credential Harvesting
Threat actors trick users into divulging login credentials to gain access to their online accounts or sensitive information by posing as a reputable organization or service. In a credential harvesting attack, the attacker usually sends a fake email or creates a fake website that appears to be from a legitimate organization (such as a bank or social media platform). Then, he or she asks the user to provide their login credentials.
Credential harvesting attacks can take several forms, including phishing emails, fake websites, or malware. Learn more about credential-based attacks here.
Clone Phishing
Attackers create a copy of a legitimate email, modify it to include a malicious attachment or link, and resend it to the original recipient or others in their contact list. The goal is to trick them into revealing sensitive information, such as login credentials or financial data, by clicking on a link or downloading an attachment that contains malware or a request for sensitive information.
In a clone phishing attack, the attacker typically starts by obtaining a legitimate email sent to the target in the past, such as a marketing or promotional email from a trusted brand. The attacker then creates a near-identical copy of the email, often using the same branding and layout but with a few key differences. For example, the attacker may change the sender's email address, the links in the email, or the attachments, in an attempt to make the email appear more urgent or legitimate.
Malware Delivery
In some spear phishing attacks, malware can be delivered to gain unauthorized access to sensitive information or to cause damage to computer systems. Malware can take several forms, including ransomware, spyware, and botnets. Malware is often delivered through email attachments or malicious links on fake websites.
Examples of Spear Phishing Attacks
Unfortunately, spear phishing is a common and often effective attack. Here are a few real-life examples of spear phishing attacks.
The John Podesta Email Hack
The John Podesta email hack was a spear phishing attack that targeted John Podesta, the chairman of Hillary Clinton's 2016 presidential campaign. The attack resulted in the theft and release of thousands of confidential emails and documents, which WikiLeaks later published.
The attack began in March 2016 when Podesta received an email, which appeared to be from Google, asking him to change his email password. The email contained a link directing him to a fake Google login page, which prompted him to enter his credentials. Unbeknownst to Podesta, the page was actually a phishing site designed to steal his login credentials.
The attacker was believed to be a group affiliated with the Russian government. They used the stolen credentials to gain access to Podesta's email account as well as the email accounts of other campaign staffers. The attackers then downloaded and exfiltrated thousands of emails and documents, which were later leaked to the public.
The Mattel Payment Fraud Scam
The Mattel payment fraud scam was a spear phishing attack that targeted the finance department of the multinational toy company in 2015. The attack resulted in the theft of over $3 million from the company, which was sent to a bank account in China.
The attack began when a member of the finance department received an email that appeared to be from a new vendor who Mattel had recently started doing business with. The email contained a request to change the vendor's banking information, and the finance department employee followed the instructions, believing it to be legitimate.
However, the email was actually a spear phishing message sent by cybercriminals who had gained access to the vendor's email account and were posing as the vendor. The attackers used this access to send fraudulent payment requests to the finance department, which were approved and processed, resulting in the loss of over $3 million.
The Mattel payment fraud scam highlighted the risks of spear phishing attacks. It underscored the importance of implementing strong security measures, such as multifactor authentication and employee training, to prevent unauthorized access to sensitive information and financial accounts.
The Target Data Breach
The Target data breach was a massive cyberattack in late 2013. Cybercriminals stole the personal and financial information of millions of customers who had shopped at Target stores during the holiday season. The attack began with a spear phishing email sent to an HVAC contractor working for Target, which provided the attackers with access to the retailer's network.
Once inside Target's network, the attackers installed malware on point-of-sale (POS) systems in over 1,800 Target stores, allowing them to capture customers' credit and debit card information as they made purchases. The attackers also stole personal information, such as names, addresses, and phone numbers, of up to 70 million customers who had shopped at Target stores during the breach period.
At the time, the Target data breach was one of the most significant data breaches in history, and it significantly impacted Target's business, reputation, and customer trust. The breach also highlighted the risks of spear phishing attacks. Measures such as network segmentation, two-factor authentication, and regular employee training can prevent unauthorized access to sensitive information and systems.
How to Protect Yourself from Spear Phishing

There are several ways individuals and organizations can protect themselves from spear phishing attacks.
Employee Training and Awareness
Providing employees with security awareness training about the risks of spear phishing attacks and how to recognize and respond to suspicious emails is crucial. Training should cover:
- Best practices for verifying email senders.
- Identifying suspicious links and attachments.
- Reporting suspicious emails to IT or security personnel.
Implementing Security Best Practices
Solid security measures such as multifactor authentication, network segmentation, firewalls, and intrusion detection systems can help prevent unauthorized access to sensitive information and systems.
Using Anti-Phishing Software
Anti-phishing software can help detect and block suspicious emails, links, and attachments before reaching users' inboxes.
Regularly Backing Up Your Data
Regularly backing up critical data can help mitigate the impact of a successful spear phishing attack. In a breach or ransomware attack, having backups of critical information can help restore data.
Staying Up-to-Date with Security News
Keeping up to date with the latest security news and trends can help individuals and organizations stay informed about emerging threats and vulnerabilities. This information can be used to proactively implement security measures and protect against spear phishing attacks.
Stay ahead of cyberthreats with the latest threat intelligence from Unit 42’s Threat Research Center.
If You Fall Victim to Spear Phishing
If you fall victim to a spear phishing attack, it's essential to act quickly to minimize any damage. Here are some steps to take:
- Report the incident. Notify your IT and security operations teams immediately. They can help assess the extent of the damage and take appropriate steps to prevent further attacks.
- Change your passwords. If you have shared your login credentials with the attacker, change your passwords immediately for any accounts that may have been compromised.
- Notify other relevant parties. Inform anyone (other than IT) who may be affected by the cyber attack and data breach, preferably using methods other than the affected email account.
- Monitor your accounts. Check and continue monitoring your accounts for any suspicious activity or unauthorized access. If you find any, report it to the relevant service provider and take steps to secure your accounts.